CIS Control 11: Secure Configuration for Network Devices, such as Firewalls, Routers, and Switches
The focus of this control is to establish, implement, and actively manage (track, report on, correct) the security configuration of network infrastructure devices using a rigorous configuration management and change control process in order to prevent attackers from exploiting vulnerable services and settings.
The CIS states this Control is critical:
“As delivered from manufacturers and resellers, the default configurations for network infrastructure devices are geared for ease-of-deployment and ease-of-use – not security. Open services and ports, default accounts (including service accounts) or passwords, support for older (vulnerable) protocols, pre-installation of unneeded software; all can be exploitable in their default state. The management of the secure configurations for networking devices is not a one-time event, but a process that involves regularly re-evaluating not only the configuration items but also the allowed traffic flows. Attackers take advantage of network devices becoming less securely configured over time as users demand exceptions for specific business needs. Sometimes the exceptions are deployed and then left undone when they are no longer applicable to the business needs. In some cases, the security risk of the exception is neither properly analyzed nor measured against the associated business need and can change over time.
Attackers search for vulnerable default settings, gaps or inconsistencies in firewall rule sets, routers, and switches and use those holes to penetrate defenses. They exploit flaws in these devices to gain access to networks, redirect traffic on a network, and intercept information while in transmission. Through such actions, the attacker gains access to sensitive data, alters important information, or even uses a compromised machine to pose as another trusted system on the network.”
The journey of implementing the CIS Controls, continues with CIS Control 11: Secure Configuration for network devices, such as Firewalls, Routers, and Switches. Organizations are directed to review the configuration of all network devices against approved configurations. Organizations should record and mitigate any deviation. Organizations are also directed to establish a rigorous configuration management program and change control process in order to prevent attackers from exploiting network device vulnerabilities.
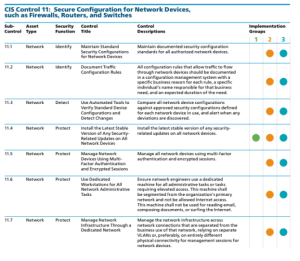
The specific sub-controls that are part of Implementation Group 1 (IG1) are:
For CIS Control 11, Tenable products allow the organization to actively and passively discover network devices and software. Using the same methods as discussed in Control 1 and Control 2, active scanning allows for network device mapping and software enumeration. Devices identified in Control 1 as network devices, firewalls, routers, and switches must be used as a reference for this control. Software versions that were enumerated in Control 2 are also required. Both of these efforts contribute greatly to this control.
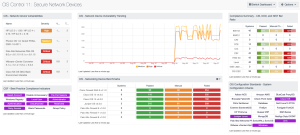
To further assist organizations with CIS Control 11: Secure Network Devices, the dashboard focuses on the compliance summary of network devices. Tenable Security Center is able to routinely scan the network for network devices and enumerate installed software, extracting software, vendor, and version information. Nessus scanners are capable of scanning internal and external assets to map out network devices. Tenable Security Center can also use passive detection to discover network devices that are not being scanned.