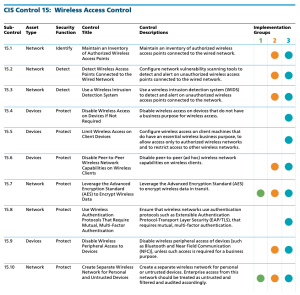
CIS Control 15: Wireless Access Control
The focus of this control is to ensure wireless access is configured to track and control access, prevent unauthorized access. If misconfigurations are found, the settings should be corrected. Wireless access has become a common and natural part of a majority of organizations network infrastructure. Wireless access is beneficial, but exposes networks to problems related to network boundaries, all of which come back to this basic series of questions:
- Who has access?
- What is being accessed?
- Why wireless access is required?
- Where from which locations is access required?
- When is access appropriate?
The CIS states this Control is critical:
“Major thefts of data have been initiated by attackers who have gained wireless access to organizations from outside the physical building, bypassing organizations’ security perimeters by connecting wirelessly to access points inside the organization. Wireless clients accompanying travelers are infected on a regular basis through remote exploitation while on public wireless networks found in airports and cafes. Such exploited systems are then used as backdoors when they are reconnected to the network of a target organization. Other organizations have reported the discovery of unauthorized wireless access points on their networks, planted and sometimes hidden for unrestricted access to an internal network. Because they do not require direct physical connections, wireless devices are a convenient vector for attackers to maintain long-term access into a target environment.”
The journey of implementing the CIS Controls continues with controlled use of wireless networking. Organizations are directed to verify that Advanced Encryption Standard (AES) is configured for all wireless technology. The sub-control that is part of Implementation Group 1 (IG1) is: