Preface on Sub-Controls 16.8, 16.9, and 16.11
Sub Controls 16.8 & 16.9
Sub-control 16.8 is not a technical control, as this requires a human to make the association between the role of the person and the account. However, Tenable Security Center is able to query systems and retrieve account names. Once the account names are collected, an organization can set up a manual process to review the accounts. There are plugins that can be used to look for accounts that are not active, and priority can be given to those systems. This process supports 16.9, as the dormant accounts may be identified during the review process. The “CSF - Account and Group Information” table located in the CIS Control 4/5 dashboard provides the query to use to get the information needed to support the account review process.
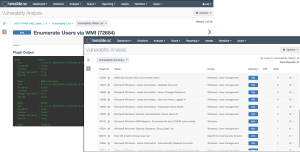
This table displays detections of account and group information, such as accounts that have never been logged into, disabled accounts, and group user lists. This information is obtained through Nessus credentialed scans. Most of these detections contain lists of accounts in the output. The "Obtains the Password Policy" detection contains the retrieved password policy in its output. Click on the Browse Component Data icon on the component to view the vulnerability analysis screen. Here, you can view the detections and investigate further. On the analysis screen, set the tool to Vulnerability Detail List to view the full details for each detection, including description and output.
Sub Control 16.11
This control focuses more on desktop computers, but can also affect applications, routers, switches and Linux servers. The configurations, however, are very different. As mentioned in the CIS Control 5 with baseline settings, Organizations should begin with CIS Benchmark. Tenable Security Center comes with audit files that are created based on the benchmarks, and this feature can be used to address this sub control. In the CIS Control 4/5 dashboard, the center column provides audit results for the benchmarks with various key words.
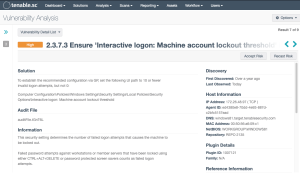
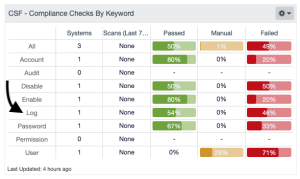
In the “CSF - Compliance Checks By Keyword” matrix, the “Log” row finds all audit checks with the word “Log” present. Each column provides a specific view into the queries with different tools and respective filters. The key to this control hover is illustrated in the “CIS Microsoft Windows Server 2019 Benchmark” setting index 2.3.7.3. In this setting, a Windows 2019 server is audited for the Interactive Logon setting. This is the key setting used to track this session timeout. The organization must review each benchmark and look for similar examples to find the exact matches. However, if the base work used in the setting is “log”, then this filter in this row returns the results. For Cisco routers, the search would be “exec-timeout”, which would not match. While Tenable can provide some keywords for searching, the organization is strongly encouraged to review the CIS Benchmark and select the correct terms.
-
CIS Microsoft Windows Server 2019 Benchmark
- https://workbench.cisecurity.org/files/2630
-
"2.3.7.3 Ensure 'Interactive logon: Machine inactivity limit' is set to '900 or fewer second(s), but not 0'"
-
CIS_DC_SERVER_2019_Level_1_v1.1.0.audit
-
Cisco IOS 15 Benchmark v4.0.1
-
https://workbench.cisecurity.org/files/2585
-
1.2.9 Set 'exec-timeout' to less than or equal to 10 minutes 'line vty'"
-
CIS_Cisco_IOS_15_v4.0.1_Level_1.audit
-
Below is a series of search terms and regular expressions to match:
REGEX: [iI]dle|[tT]imeout|[iI]nactive
Search Terms
-
Inactive
-
Timeout
-
Idle connections
-
Idle Timeout
-
user shell timeout
-
connection Timeout
-
SSH Idle Timeout
-
DCUI timeout
-
shell services timeout
-
terminate idle ESXi
-
exec-timeout