SSH Credentials
Use SSH credentials for host-based checks on Unix systems and supported network devices. Tenable Security Center uses these credentials to obtain local information from remote Unix systems for patch auditing or compliance checks. Tenable Security Center uses Secure Shell (SSH) protocol version 2 based programs (e.g., OpenSSH, Solaris SSH, etc.) for host-based checks.
Tenable Security Center encrypts the data
Note: Non-privileged users with local access on Linux systems can determine basic security issues, such as patch levels or entries in the /etc/passwd file. For more comprehensive information, such as system configuration data or file permissions across the entire system, an account with root privileges is required.
Note: You can add up to 1,000 SSH credentials in a single scan. For best performance, Tenable recommends adding no more than 10 SSH credentials per scan.
Configure the following options for SSH credentials, including options specific for your authentication method:
| General Option | Description |
|---|---|
|
Name |
(Required) A name for the credential. |
| Description | A description for the credential. |
|
Label |
A label for the credential. For more information, see |
Arcon Options
The following table describes the additional options to configure when using Arcon as the authentication method for SSH credentials.
| Option | Description |
|---|---|
| Arcon Host |
(Required) The Arcon IP address or DNS address. Note: If your Arcon installation is in a subdirectory, you must include the subdirectory path. For example, type IP address or hostname/subdirectory path. |
| Arcon Port | (Required) The port on which Arcon listens. By default, Tenable Security Center uses port 444. |
| API User | (Required) The API user provided by Arcon. |
| API Key | (Required) The API key provided by Arcon. |
| Authentication URL | (Required) The URL Tenable Security Center uses to access Arcon. |
| Password Engine URL |
(Required) The URL Tenable Security Center uses to access the passwords in Arcon. |
| Username | (Required) The username to log in to the hosts you want to scan. |
| Arcon Target Type | (Optional) The name of the target type. Depending on the Arcon PAM version you are using and the system type the SSH credential has been created with, this is set to linux by default. Refer to the Arcon PAM Specifications document (provided by Arcon) for target type/system type mapping for the correct target type value. |
| Checkout Duration |
(Required) The length of time, in hours, that you want to keep credentials checked out in Arcon. Configure the Checkout Duration to exceed the typical duration of your Tenable Security Center scans. If a password from a previous scan is still checked out when a new scan begins, the new scan fails. Tip: Configure the password change interval in Arcon so that password changes do not disrupt your Tenable Security Center scans. If Arcon changes a password during a scan, the scan fails. |
| Use SSL | When enabled, Tenable Security Center uses SSL through IIS for secure communications. You must configure SSL through IIS in Arcon before enabling this option. |
| Verify SSL Certificate | When enabled, Tenable Security Center validates the SSL certificate. You must configure SSL through IIS in Arcon before enabling this option. |
| Privilege Escalation | The privilege escalation method you want to use to increase users' privileges after initial authentication. Your Privilege Escalation selection determines the specific options you must configure. For more information, see Privilege Escalation. |
| Targets to Prioritize Credentials |
Specify IPs or CIDR blocks on which this credential is attempted before any other credential. To specify multiple IPs or CIDR blocks, use a comma or space-separated list. Using this setting can decrease scan times by prioritizing a credential that you know works against your selected targets. For example, if your scan specifies 100 credentials, and the successful credential is the 59th credential out of 100, the first 58 credentials have to fail before the 59th credential succeeds. If you use Targets To Prioritize Credentials, you configure the scan to use the successful credential first, which allows the scan to access the target faster. |
BeyondTrust Options
The following table describes the additional options to configure when using BeyondTrust as the authentication method for SSH credentials.
| Option | Description |
|---|---|
| Username | The username to log in to the hosts you want to scan. |
| BeyondTrust Host | The BeyondTrust IP address or DNS address. |
| BeyondTrust Port | The port BeyondTrust is listening on. |
| BeyondTrust API User | The API user provided by BeyondTrust. |
| BeyondTrust API Key | The API key provided by BeyondTrust. |
| Checkout Duration |
The length of time, in minutes, that you want to keep credentials checked out in BeyondTrust. Configure the Checkout duration to exceed the typical duration of your Tenable Security Center scans. If a password from a previous scan is still checked out when a new scan begins, the new scan fails. Tip: Configure the password change interval in BeyondTrust so that password changes do not disrupt your Tenable Security Center scans. If BeyondTrust changes a password during a scan, the scan fails. |
| Use SSL |
If enabled, Tenable Security Center uses SSL through IIS for secure communications. You must configure SSL through IIS in BeyondTrust before enabling this option. |
| Verify SSL Certificate |
If enabled, Tenable Security Center validates the SSL certificate. You must configure SSL through IIS in BeyondTrust before enabling this option. |
| Use Private Key | If enabled, Tenable Security Center uses key-based authentication for SSH connections instead of password authentication. |
| Use Privilege Escalations |
If enabled, Tenable Security Center uses BeyondTrust for privilege escalation. |
Centrify Options
The following table describes the additional options to configure when using Centrify as the authentication method for SSH credentials.
| Option | Description |
|---|---|
| Centrify Host |
(Required) The Centrify IP address or DNS address. Note: If your Centrify installation is in a subdirectory, you must include the subdirectory path. For example, type IP address or hostname/subdirectory path. |
| Centrify Port | (Required) The port on which Centrify listens. By default, |
| API User | (Required) The API user provided by Centrify. |
| API Key | (Required) The API key provided by Centrify. |
| Tenant | (Required) The Centrify tenant associated with the API. By default, |
| Authentication URL | (Required) The URL |
| Password Query URL | (Required) The URL |
| Password Engine URL |
(Required) The URL |
| Username | (Required) The username to log in to the hosts you want to scan. |
| Checkout Duration |
(Required) The length of time, in minutes, that you want to keep credentials checked out in Centrify. Configure the Checkout Duration to exceed the typical duration of your Tenable Security Center scans so that password changes do not disrupt your |
| Use SSL | When enabled, |
| Verify SSL Certificate | When enabled, |
Certificate Options
The following table describes the additional options to configure when using Certificate as the authentication method for SSH credentials.
| Option | Description |
|---|---|
| Username | (Required) The username for a user on the host system. |
| User Certificate |
(Required) The RSA, DSA, or ED25519 OpenSSH certificate file for the user. |
| Private Key |
(Required) The RSA, DSA, or ED25519 OpenSSH private key file for the user. |
| Passphrase | The passphrase for the private key, if required. |
| Privilege Escalation |
The privilege escalation method you want to use to increase users' privileges after initial authentication. Your Privilege Escalation selection determines the specific options you must configure. For more information, see Privilege Escalation. |
CyberArk SSH Auto-Discovery Options
The following table describes the additional options to configure when using CyberArk SSH Auto-Discovery as the authentication method for SSH credentials.
| Option | Description | Required |
|---|---|---|
|
CyberArk Host |
The IP address or FQDN name for the user’s CyberArk Instance. |
yes |
|
Port |
The port on which the CyberArk API communicates. By default, Tenable uses 443. |
yes |
|
AppID |
The Application ID associated with the CyberArk API connection. |
yes |
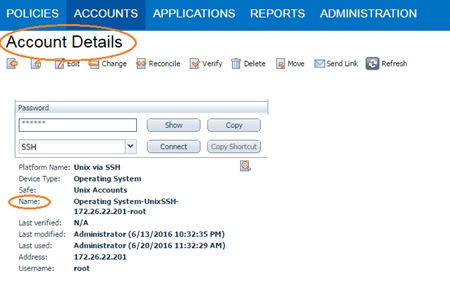
| Safe |
Users may optionally specify a Safe to gather account information and request passwords. |
no |
| AIM Web Service Authentication Type | There are two authentication methods established in the feature. IIS Basic Authentication and Certificate Authentication. Certificate Authentication can be either encrypted or unencrypted. |
yes |
|
Username |
(Appears if AIM Web Service Authentication Type is IIS Basic Authentication) The username for a user on the CyberArk server. |
no |
|
Password |
(Appears if AIM Web Service Authentication Type is IIS Basic Authentication) The password associated with the username you provided. |
no |
| Client Certificate |
(Appears if AIM Web Service Authentication Type is Certificate Authentication) The file that contains the PEM certificate used to communicate with the CyberArk host. |
no |
| Client Certificate Private Key |
(Appears if AIM Web Service Authentication Type is Certificate Authentication) The file that contains the PEM private key for the client certificate. |
yes, if private key is applied |
| Client Certificate Private Key Passphrase |
(Appears if AIM Web Service Authentication Type is Certificate Authentication) The passphrase for the private key, if required. |
yes, if private key is applied |
| CyberArk PVWA Web UI Login Name | Username to log in to CyberArk web console. This is used to authenticate to the PVWA REST API and gather bulk account information. |
yes |
| CyberArk PVWA Web UI Login Password | Password for the username to log in to CyberArk web console. This is used to authenticate to the PVWA REST API and gather bulk account information. |
yes |
| CyberArk Platform Search String |
String used in the PVWA REST API query parameters to gather bulk account information. For example, the user can enter UnixSSH Admin TestSafe, to gather all UnixSSH platform accounts containing a username Admin in a Safe called TestSafe. Note: This is a non-exact keyword search. A best practice would be to create a custom platform name in CyberArk and enter that value in this field to improve accuracy. |
yes |
|
Use SSL |
If enabled, the scanner uses SSL through IIS for secure communications. Enable this option if CyberArk is configured to support SSL through IIS. |
yes |
|
Verify SSL Certificate |
If enabled, the scanner validates the SSL certificate. Enable this option if CyberArk is configured to support SSL through IIS and you want to validate the certificate. |
no |
| Targets to Prioritize Credentials |
Specify IPs or CIDR blocks on which this credential is attempted before any other credential. To specify multiple IPs or CIDR blocks, use a comma or space-separated list. Using this setting can decrease scan times by prioritizing a credential that you know works against your selected targets. For example, if your scan specifies 100 credentials, and the successful credential is the 59th credential out of 100, the first 58 credentials have to fail before the 59th credential succeeds. If you use Targets To Prioritize Credentials, you configure the scan to use the successful credential first, which allows the scan to access the target faster. |
no |
| Privilege Escalation | The privilege escalation method you want to use to increase users' privileges after initial authentication. Your Privilege Escalation selection determines the specific options you must configure. For more information, see Privilege Escalation. | no |
CyberArk Vault Options
The following table describes the additional options to configure when using CyberArk Vault as the authentication method for SSH credentials.
| Option | Description | Required |
|---|---|---|
| CyberArk Elevate Privileges With |
The privilege escalation method you want to use to increase users' privileges after initial authentication. Your CyberArk Elevate Privileges With selection determines the specific options you must configure. For more information, see Privilege Escalation. |
no |
| Get credential by |
The method with which your CyberArk API credentials are retrieved. Can be Username, Identifier, Address, or Parameters. Note: The frequency of queries for Username is one query per target. The frequency of queries for Identifier is one query per chunk. This feature requires all targets have the same identifier. |
yes |
| Account Name | (If Get credential by is Identifier) The unique account name or identifier assigned to the CyberArk API credential. | no |
| Address |
(If Get credential by is Address |
no |
| Username |
(If Get credential by is Username |
no |
| Safe |
The CyberArk safe the credential should be retrieved from. |
no |
|
Use Target IP Address |
(If Get credential by is Parameters) When enabled, the integration appends the target address to the credential query, which limits the query to accounts matching the scan target’s address. This is ignored if Address is set. |
no |
|
Folder |
(If Get credential by is Parameters) The folder of the credential. |
no |
|
Database |
(If Get credential by is Parameters) The database of the credential. |
no |
|
Query |
(If Get credential by is Parameters) Specify a custom “free query” using account properties. When this method is specified, all other search criteria are ignored. |
no |
|
Query Format |
(If Get credential by is Parameters) Defines the query format. Allowed values are Exact and Regexp. The default is Exact. This value is ignored unless the Query option was specified. |
no |
|
CyberArk Host |
The IP address or FQDN name for the CyberArk AIM Web Service. |
yes |
|
Port |
The port on which the CyberArk API communicates. By default, Tenable uses 443. |
yes |
|
AppID |
The Application ID associated with the CyberArk API connection. |
yes |
| Client Certificate |
The file that contains the PEM certificate used to communicate with the CyberArk host. Note: Customers self-hosting CyberArk CCP on a Windows Server 2022 and above should follow the guidance found in Tenable’s Community post about CyberArk Client Certification Authentication Issue. |
no |
| Client Certificate Private Key | The file that contains the PEM private key for the client certificate. |
yes, if private key is applied |
| Client Certificate Private Key Passphrase | The passphrase for the private key, if required. |
yes, if private key is applied |
|
Kerberos Target Authentication |
If enabled, Kerberos authentication is used to log in to the specified Linux or Unix target. |
no |
|
Key Distribution Center (KDC) |
(Required if Kerberos Target Authentication is enabled) This host supplies the session tickets for the user. |
yes |
|
KDC Port |
|
|
|
KDC Transport |
|
|
|
Realm |
(Required if Kerberos Target Authentication is enabled) The Realm is the authentication domain, usually noted as the domain name of the target (for example, example.com). By default, Tenable Security Center uses 443. |
yes |
|
Use SSL |
If enabled, the scanner uses SSL through IIS for secure communications. Enable this option if CyberArk is configured to support SSL through IIS. |
no |
|
Verify SSL Certificate |
If enabled, the scanner validates the SSL certificate. Enable this option if CyberArk is configured to support SSL through IIS and you want to validate the certificate. |
no |
CyberArk Vault (Legacy) Options
The following table describes the additional options to configure when using CyberArk Vault (Legacy) as the authentication method for SSH credentials.
| Option | Description |
|---|---|
|
Username |
(Required) The username for the target system. |
| CyberArk elevate privileges with |
The privilege escalation method you want to use to increase users' privileges after initial authentication. Your CyberArk elevate privileges with selection determines the specific options you must configure. For more information, see Privilege Escalation. |
|
Central Credential Provider URL Host |
(Required) The CyberArk Central Credential Provider IP/DNS address. |
|
Central Credential Provider URL Port |
(Required) The port the CyberArk Central Credential Provider is listening on. |
| CyberArk Address | The domain for the CyberArk account. You must configure SSL through IIS in CyberArk Central Credential Provider before configuring this option. |
|
Vault Username |
The username for the vault, if the CyberArk Central Credential Provider is configured for basic authentication. |
|
Vault Password |
The password for the vault, if the CyberArk Central Credential Provider is configured for basic authentication. |
|
Safe |
(Required) The safe on the CyberArk Central Credential Provider server that contains the credentials you want to retrieve. |
| CyberArk Client Certificate | The file that contains the PEM certificate used to communicate with the CyberArk host. |
| CyberArk Client Certificate Private Key | The file that contains the PEM private key for the client certificate. |
| CyberArk Client Certificate Private Key Passphrase | The passphrase for the private key, if required. |
|
AppID |
(Required) The AppID with CyberArk Central Credential Provider permissions to retrieve the target password. |
|
Folder |
(Required) The folder on the CyberArk Central Credential Provider server that contains the credentials you want to retrieve. |
|
PolicyID |
The PolicyID assigned to the credentials you want to retrieve. |
|
Vault Use SSL |
When enabled, Tenable Security Center uses SSL through IIS for secure communications. You must configure SSL through IIS in CyberArk Central Credential Provider before enabling this option. |
|
Vault Verify SSL |
When enabled, Tenable Security Center validates the SSL certificate. You must configure SSL through IIS in CyberArk Central Credential Provider before enabling this option. |
| CyberArk Escalation Account Details Name |
The unique name of the credential you want to retrieve from CyberArk. |
| CyberArk AIM Service URL |
The URL for the CyberArk AIM web service. By default, Tenable Security Center uses /AIMWebservice/v1.1/AIM.asmx. |
Delinea Secret Server Options
The following table describes the additional options to configure when using Delinea Secret Server as the authentication method for SSH credentials.
| Option | Description | Required |
|---|---|---|
|
Delinea Secret |
The value of the secret on the Delinea server. The secret is labeled Secret Name on the Delinea server. |
yes |
|
Delinea Host |
The Delinea Secret Server host to pull the secrets from. |
yes |
|
Delinea Port |
The Delinea Secret Server Port for API requests. By default, Tenable uses 443. |
yes |
| Delinea Authentication Method | Indicates whether to use credentials or an API key for authentication. By default, Credentials is selected. | yes |
|
Delinea Login Name |
The username to authenticate to the Delinea server. |
yes |
|
Delinea Password |
The password to authenticate to the Delinea server. This is associated with the Delinea Login Name you provided. |
yes |
| Delinea API Key | The API key generated in the Secret Server user interface. |
yes |
|
Use Private Key |
If enabled, uses key-based authentication for SSH connections instead of password authentication. |
no |
|
Use SSL |
Enable if the Delinea Secret Server is configured to support SSL. |
no |
|
Verify SSL Certificate |
If enabled, verifies the SSL Certificate on the Delinea server. |
no |
|
Privilege Escalation |
The privilege escalation method you want to use to increase users' privileges after initial authentication. Multiple options for privilege escalation are supported, including su, su+sudo and sudo. Your selection determines the specific options you must configure. |
no |
| Custom password prompt | Some devices are configured to prompt for a password with a non-standard string (for example, "secret-passcode"). This setting allows recognition of these prompts. Leave this blank for most standard password prompts. |
no |
Delinea Secret Server Auto-Discovery Options
The following table describes the additional options to configure when using Delinea Secret Server Auto-Discovery as the authentication method for SSH credentials.
| Option | Description | Required |
|---|---|---|
|
Delinea Host |
The Delinea Secret Server host to pull the secrets from. |
Yes |
|
Delinea Port |
The Delinea Secret Server Port for API requests. By default, Tenable uses 443. |
Yes |
|
Delinea Authentication Method |
Indicates whether to use credentials or an API key for authentication. By default, Credentials is selected. |
Yes |
| Delinea Login Name |
The username to authenticate to the Delinea server. |
Yes |
| Delinea Password | The password to authenticate to the Delinea server. This is associated with the provided Delinea Login Name. |
Yes |
| Delinea API Key | The API key generated in the Secret Server user interface. This setting is required if the API Key authentication method is selected. |
Yes |
| Query Mode | Choose to query accounts using pre-set fields or by constructing a string of URL query parameters. By default, Simple is selected. |
Yes |
| Folder ID |
Query accounts with the given folder ID. This option is only available if query mode is set to Simple. |
No |
|
Search Text |
Query accounts matching the given search text. This option is only available if query mode is set to Simple. |
No |
|
Search Field |
The field to search using the given search text. If not specified, the query will search the name field. This option is only available if query mode is set to Simple. |
No |
| Exact Match | Perform an exact match against the search text. By default, this is unselected. This option is only available if query mode is set to Simple. |
No |
| Query String | Provide a string of URL query parameters. This option is only available if query mode is set to Advanced, and in that case it is required. |
Yes |
| Use Private Key | Use key-based authentication for SSH connections instead of password authentication. |
No |
| Use SSL | Use SSL for secure communications. |
Yes |
| Verify SSL Certificate | Verify the Delinea Secret Server SSL certificate. |
No |
|
Privilege Escalation |
The privilege escalation method to use to increase users' privileges after initial authentication. Multiple options for privilege escalation are supported, including su, su+sudo and sudo. Selecting a privilege escalation method provides options to configure an escalation query, similar to “query mode” and its related options. These fields must only be completed if using a separate account for escalation than initial login (for example, “su”). |
Yes |
| Custom Password Prompt | Some devices are configured to prompt for a password with a non-standard string (for example, "secret-passcode"). This setting allows recognition of these prompts. Leave this blank for most standard password prompts. | No |
Hashicorp Vault Options
The following table describes the additional options to configure when using Hashicorp Vault as the authentication method for SSH credentials.
| Option | Default Value | Required |
|---|---|---|
|
Hashicorp Host |
The Hashicorp Vault IP address or DNS address. Note: If your Hashicorp Vault installation is in a subdirectory, you must include the subdirectory path. For example, type IP address or hostname/subdirectory path. |
yes |
|
Hashicorp Port |
The port on which Hashicorp Vault listens. |
yes |
|
Authentication Type |
Specifies the authentication type for connecting to the instance: App Role or Certificates. If you select Certificates, additional options for Hashicorp Client Certificate (Required) and Hashicorp Client Certificate Private Key (Required) appear. Select the appropriate files for the client certificate and private key. |
yes |
|
Role ID |
The GUID provided by Hashicorp Vault when you configured your App Role. |
yes |
| Role Secret ID |
The GUID generated by Hashicorp Vault when you configured your App Role. |
yes |
| Authentication URL |
The path/subdirectory to the authentication endpoint. This is not the full URL. For example: /v1/auth/approle/login |
yes |
| Namespace | The name of a specified team in a multi-team environment. | no |
| Hashicorp Vault Type |
The type of Hashicorp Vault secrets engine:
|
yes |
|
KV1 Engine URL KV2 Engine URL AD Engine URL LDAP Engine URL |
The engine URL combines with the secret name to form the API request URL. For example, a secret name of creds and a KV v1 engine url of /v1/secret would result in a GET request to /v1/secret/creds (for KV v2, /v1/secret/data/creds). |
yes |
|
Username Source |
(Appears when Hashicorp Vault Type is KV1 or KV2) Specifies if the username is input manually or pulled from Hashicorp Vault. |
yes |
|
Username Key |
(Appears when Hashicorp Vault Type is KV1 or KV2) The name in Hashicorp Vault that usernames are stored under. |
yes |
| Password Key | (Appears when Hashicorp Vault Type is KV1 or KV2) The key in Hashicorp Vault that passwords are stored under. | yes |
| Secret Name | The key secret you want to retrieve values for. | yes |
|
Kerberos Target Authentication |
If enabled, Kerberos authentication is used to log in to the specified Linux or Unix target. |
no |
|
Key Distribution Center (KDC) |
(Required if Kerberos Target Authentication is enabled) This host supplies the session tickets for the user. |
yes |
|
KDC Port |
(Required if Kerberos Target Authentication is enabled) The port on which the Kerberos authentication API communicates. By default, Tenable uses 88. |
yes |
|
KDC Transport |
(Required if Kerberos Target Authentication is enabled) The KDC uses TCP by default in Linux implementations. For UDP, change this option. If you need to change the KDC Transport value, you may also need to change the port as the KDC UDP uses either port 88 or 750 by default, depending on the implementation. |
yes |
|
Realm |
(Required if Kerberos Target Authentication is enabled) The Realm is the authentication domain, usually noted as the domain name of the target (for example, example.com). By default, Tenable Security Center uses 443. |
yes |
| Use SSL | When enabled, Tenable Security Center uses SSL for secure communications. You must configure SSL in Hashicorp Vault before enabling this option. | no |
| Verify SSL | When enabled, Tenable Security Center validates the SSL certificate. You must configure SSL in Hashicorp Vault before enabling this option. | no |
| Targets to Prioritize Credentials |
Specify IPs or CIDR blocks on which this credential is attempted before any other credential. To specify multiple IPs or CIDR blocks, use a comma or space-separated list. Using this setting can decrease scan times by prioritizing a credential that you know works against your selected targets. For example, if your scan specifies 100 credentials, and the successful credential is the 59th credential out of 100, the first 58 credentials have to fail before the 59th credential succeeds. If you use Targets To Prioritize Credentials, you configure the scan to use the successful credential first, which allows the scan to access the target faster. |
no |
| Privilege Escalation | The privilege escalation method you want to use to increase users' privileges after initial authentication. Your Privilege Escalation selection determines the specific options you must configure. For more information, see Privilege Escalation. | no |
Kerberos Options
The following table describes the additional options to configure when using Kerberos as the authentication method for SSH credentials.
| Option | Description |
|---|---|
| Username | (Required) The username for a user on the target system. |
| Password | (Required) The password associated with the username you provided. |
| KDC Host | (Required) The host supplying the session tickets. |
| KDC Port | (Required) The port you want to use for the KDC connection. By default, Tenable Security Center uses port 88. |
| KDC Transport |
(Required) The method you want to use to connect to the KDC server. Note: If you select UDP, you may need to edit the KDC Port. The KDC UDP protocol uses either port 88 or port 750. |
| Realm | (Required) The authentication domain, typically the domain name of the target (e.g., example.com). |
| Privilege Escalation |
The privilege escalation method you want to use to increase users' privileges after initial authentication. Your Privilege Escalation selection determines the specific options you must configure. For more information, see Privilege Escalation. |
Lieberman Options
The following table describes the additional options to configure when using Lieberman as the authentication method for SSH credentials.
| Option | Description |
|---|---|
| Username | The username for a user on the database. |
| Lieberman Host |
The Lieberman IP address or DNS address. Note: If your Lieberman installation is in a subdirectory, you must include the subdirectory path. For example, type IP address or hostname/subdirectory path. |
| Lieberman Port | The port Lieberman is listening on. |
| Lieberman User |
The username for the Lieberman explicit user you want Tenable Security Center to use for authentication to the Lieberman Rapid Enterprise Defense (RED) API. |
| Lieberman Password |
The password for the Lieberman explicit user. |
| Use SSL |
When enabled, Tenable Security Centeruses SSL through IIS for secure communications. You must configure SSL through IIS in Lieberman before enabling this option. |
| Verify SSL Certificate |
When enabled, Tenable Security Center validates the SSL certificate. You must configure SSL through IIS in Lieberman before enabling this option. |
| System Name | The name for the database credentials in Lieberman. |
Password Options
The most effective credentialed scans are those with root privileges (enable privileges, for Cisco IOS). Since many sites do not permit a remote login as root for security reasons, a Nessus user account can invoke a variety of privilege escalation options including: su, sudo, su+sudo, DirectAuthorize (dzdo), PowerBroker (pbrun), k5login, and Cisco Enable.
The following table describes the additional options to configure when using Password as the authentication method for SSH credentials.
| Option | Description |
|---|---|
| Username | (Required) The username for a user on the target system. |
| Password |
(Required) The password associated with the username you provided. |
| Privilege Escalation |
The privilege escalation method you want to use to increase users' privileges after initial authentication. Your Privilege Escalation selection determines the specific options you must configure. For more information, see Privilege Escalation. |
Public Key Options
The following table describes the additional options to configure when using Public Key as the authentication method for SSH credentials.
| Option | Description |
|---|---|
|
Username |
(Required) The username for a user on the host system. |
|
Private Key |
(Required) The RSA, DSA, or ED25519 OpenSSH key file for the user. |
|
Passphrase |
The passphrase for the private key, if required. |
|
Privilege Escalation |
The privilege escalation method you want to use to increase users' privileges after initial authentication. Your Privilege Escalation selection determines the specific options you must configure. For more information, see Privilege Escalation. |
QiAnXin Options
The following table describes the additional options to configure when using QiAnXin as the authentication method for SSH credentials.
| Option | Description | Required |
|---|---|---|
|
QiAnXin Host |
The IP address or url for the QiAnXin host. |
yes |
|
QiAnXin Port |
The port on which the QiAnXin API communicates. By default, Tenable uses 443. |
yes |
|
QiAnXin API Client ID |
The Client ID for the embedded account application created in QiAnXin PAM. |
yes |
|
QiAnXin API Client Secret |
The Secret ID for the embedded account application created in QiAnXin PAM. |
yes |
|
|
The username to log in to the hosts you want to scan. | yes |
|
QiAnXin Asset Address |
Specify the host IP of the asset containing the account to use. If not specified, the scan target IP is used. | no |
|
|
Specify the platform (based on asset type) of the asset containing the account to use. If not specified, a default target is used based on credential type (for example, for Windows credentials, the default is WINDOWS). Possible values:
|
no |
|
|
Specify the region ID of the asset containing the account to use. | Only if using multiple regions |
|
Kerberos Target Authentication |
If enabled, Kerberos authentication is used to log in to the specified Linux or Unix target. |
no |
|
Key Distribution Center (KDC) |
(Required if Kerberos Target Authentication is enabled) This host supplies the session tickets for the user. |
yes |
|
KDC Port |
The port on which the Kerberos authentication API communicates. By default, Tenable uses 88. |
no |
|
KDC Transport |
The KDC uses TCP by default in Linux implementations. For UDP, change this option. If you need to change the KDC Transport value, you may also need to change the port as the KDC UDP uses either port 88 or 750 by default, depending on the implementation. |
no |
|
Realm |
(Required if Kerberos Target Authentication is enabled) The Realm is the authentication domain, usually noted as the domain name of the target. |
yes |
| Use SSL | When enabled, Tenable uses SSL for secure communication. This is enabled by default. |
no |
|
Verify SSL Certificate |
When enabled, Tenable verifies that the SSL Certificate on the server is signed by a trusted CA. |
no |
| Targets to Prioritize Credentials |
Specify IPs or CIDR blocks on which this credential is attempted before any other credential. To specify multiple IPs or CIDR blocks, use a comma or space-separated list. Using this setting can decrease scan times by prioritizing a credential that you know works against your selected targets. For example, if your scan specifies 100 credentials, and the successful credential is the 59th credential out of 100, the first 58 credentials have to fail before the 59th credential succeeds. If you use Targets To Prioritize Credentials, you configure the scan to use the successful credential first, which allows the scan to access the target faster. |
no |
| Privilege Escalation | The privilege escalation method you want to use to increase users' privileges after initial authentication. Your Privilege Escalation selection determines the specific options you must configure. For more information, see Privilege Escalation. | no |
Senhasegura Options
The following table describes the additional options to configure when using Senhasegura as the authentication method for SSH credentials.
| Option | Description | Required |
|---|---|---|
|
Senhasegura Host |
The IP address or url for the Senhasegura host. |
yes |
|
Senhasegura Port |
The port on which the Senhasegura API communicates. By default, Tenable uses 443. |
yes |
|
Senhasegura API Client ID |
The Client ID for the applicable Senhasegura A2A Application for Oauth 2.0 API authentication. |
yes |
| Senhasegura API |
The Secret ID for the applicable Senhasegura A2A Application for Oauth 2.0 API authentication. |
yes |
| Senhasegura Credential ID or Identifier | The credential ID or identifier for the credential that you are requesting to retrieve. |
yes |
| Use SSH Key for Target Authentication | The user can select this option to retrieve the SSH Key to authenticate to the target if configuration is applicable in Senhasegura. | Required if authenticating to target with SSH Key. |
|
Private Key File |
The Private Key used to decrypt encrypted sensitive data from A2A. Note: You can enable encryption of sensitive data in the A2A Application Authorizations. If enabled, you must provide a private key file in the scan credentials. This can be downloaded from the applicable A2A application in Senhasegura. |
Required if you have enabled encryption of sensitive data in A2A Application Authorizations. |
| Use SSL | When enabled, Tenable Security Center uses SSL for secure communications. This setting is enabled by default. | no |
|
Verify SSL Certificate |
When enabled, Tenable Security Center validates the SSL certificate. This setting is disabled by default. |
no |
| Privilege Escalation |
The Private Key used to decrypt encrypted sensitive data from A2A. Note: Tenable supports multiple options for privilege escalation, including su, su+sudo and sudo. For example, if you select sudo, more fields for sudo user, Escalation Account Name, and Location of su and sudo (directory) are provided and can be completed to support authentication and privilege escalation through Senhasegura. The Escalation Account Name field is then required to complete your privilege escalation. Note: For more information about supported privilege escalation types and their accompanying fields, see Privilege Escalation. |
no |
Thycotic Secret Server Options
The following table describes the additional options to configure when using Thycotic Secret Server as the authentication method for SSH credentials.
| Option | Description |
|---|---|
|
Username |
(Required) The username for a user on the target system. |
| Thycotic elevate privileges with |
The privilege escalation method you want to use to increase users' privileges after initial authentication. Your selection for this setting determines the specific options you must configure. For more information, see Privilege Escalation. |
| Thycotic Secret Name | The Secret Name value on the Thycotic server. |
| Thycotic Secret Server URL |
(Required) The value you want Tenable Security Center to use when setting the transfer method, target, and target directory for the scanner. Find the value on the Thycotic server, in Admin > Configuration > Application Settings > Secret Server URL. For example, if you type https://pw.mydomain.com/SecretServer, Tenable Security Center determines it is an SSL connection, that pw.mydomain.com is the target address, and that /SecretServer is the root directory. |
| Thycotic Login Name | (Required) The username for a user on the Thycotic server. |
| Thycotic Password | (Required) The password associated with the Thycotic Login Name you provided. |
| Thycotic Organization | In cloud instances of Thycotic, the value that identifies the organization you want Tenable Security Center to target. |
| Thycotic Domain | The domain, if set for the Thycotic server. |
| Verify SSL Certificate |
If enabled, Tenable Security Center verifies the SSL Certificate on the Thycotic server. For more information about using self-signed certificates, see the Nessus custom_CA.inc documentation. |
| Use Private Key | If enabled, Tenable Security Center uses key-based authentication for SSH connections instead of password authentication. |
WALLIX Bastion Options
The following table describes the additional options to configure when using WALLIX Bastion as the authentication method for SSH credentials.
| Option | Description | Required |
|---|---|---|
|
WALLIX Host |
The IP address for the WALLIX Bastion host. |
yes |
|
WALLIX Port |
The port on which the WALLIX Bastion API communicates. By default, Tenable uses 443. |
yes |
|
Authentication Type |
Basic authentication (with WALLIX Bastion user interface username and Password requirements) or API Key authentication (with username and WALLIX Bastion-generated API key requirements). |
no |
| WALLIX User |
Your WALLIX Bastion user interface login username. |
yes |
| WALLIX Password | Your WALLIX Bastion user interface login password. Used for Basic authentication to the API. | yes |
| WALLIX API Key | The API key generated in the WALLIX Bastion user interface. Used for API Key authentication to the API. | yes |
| Get Credential by Device Account Name |
The account name associated with a Device you want to log in to the target systems with. Note: If your device has more than one account you must enter the specific device name for the account you want to retrieve credentials for. Failure to do this may result in credentials for the wrong account returned by the system. |
Required only if you have a target and/or device with multiple accounts. |
|
HTTPS |
This is enabled by default. Caution: The integration fails if you disable HTTPS. |
yes |
|
Verify SSL Certificate |
This is disabled by default and is not supported in WALLIX Bastion PAM integrations. |
no |
|
Privilege Escalation |
This enables WALLIX Bastion Privileged Access Management (PAM). Use the drop-down menu to select the privilege elevation method. To bypass this function, leave this field set to Nothing. Caution: In your WALLIX Bastion account, the WALLIX Bastion super admin must have enabled "credential recovery" on your account for PAM to be enabled. Otherwise, your scan may not return any results. For more information, see your WALLIX Bastion documentation. Note: Multiple options for privilege escalation are supported, including su, su+sudo and sudo. For example, if you select sudo, more fields for sudo user, Escalation Account Name, and Location of su and sudo (directory) are provided and can be completed to support authentication and privilege escalation through WALLIX Bastion PAM. The Escalation Account Name field is then required to complete your privilege escalation. Note: For more information about supported privilege escalation types and their accompanying fields, see Privilege Escalation. |
Required if you wish to escalate privileges. |
| Targets to Prioritize Credentials |
Specify IPs or CIDR blocks on which this credential is attempted before any other credential. To specify multiple IPs or CIDR blocks, use a comma or space-separated list. Using this setting can decrease scan times by prioritizing a credential that you know works against your selected targets. For example, if your scan specifies 100 credentials, and the successful credential is the 59th credential out of 100, the first 58 credentials have to fail before the 59th credential succeeds. If you use Targets To Prioritize Credentials, you configure the scan to use the successful credential first, which allows the scan to access the target faster. |
no |