Preface on Sub-Control 9.4
The CIS recommends that to meet the requirements for IG1, organizations should at a minimum apply host-based firewalls or port-filtering tools on end systems, with a default-deny rule that drops all traffic except those services and ports that are explicitly allowed. For CIS Control 9, Tenable products allow security operations teams to use Tenable Security Center Continuous View to analyze endpoints and check firewall configurations, as well as track open ports and services.
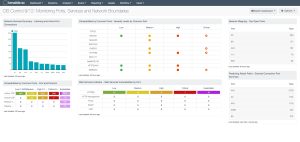
To further assist organizations the CIS Control 9/12, the "Monitoring Ports, Services and Network Boundaries" dashboard focuses on the tracking of active ports, services, and protocols. Tenable Security Center is able to routinely scan the network for open ports and services. Nessus scanners are capable of scanning internal and external assets on the network. Tenable Security Center can also use passive detection to find systems that are communicating with the internal network from external or untrusted devices.
For more information about the CIS Control 9 dashboard, see CIS Control 9/12: Monitoring Ports, Services and Network Boundaries.
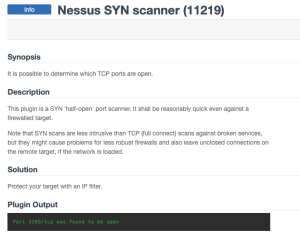
There are a variety of methods that can be employed to assist organizations with port filtering, or determining if host-based firewalls are in use. Nessus has a variety of scanning methods to detect open ports and services. The Nessus SYN scanner, plugin ID 11219, is less intrusive and behaves differently by simplifying the scanning process. The scanner sends packets and waits for a response, but does not initiate the full three-way handshake. It does not open sockets, but generates raw packets using low-level libraries.
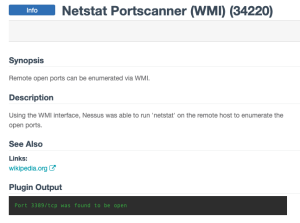
Organizations can benefit from also using the following plugins, such as plugin 34220, which uses the WMI interface to run ‘netstat’ on the remote host to enumerate the open ports.
Plugin 34252 Microsoft Remote Listeners Enumeration (WMI), can be used to obtain the names of processes listening on UDP and TCP ports.
As related to sub-control 9.4, there are several plugins available, such as plugin ID 45052 WMI Firewall enumeration, which allows Nessus to use WMI to enumerate third party firewall software installed on the host. Also, using plugin 20811, Microsoft Windows Software Enumeration and a vulnerability text of “Windows Firewall” can assist in determining if the application is installed on the target host.