CIS Control 17: Implement a Security Awareness and Training Program
The security awareness program is influenced by the maturity of an organization. For example a small company with 100 employees or less can have a very informal program, while a fortune 500 company on average has over 60,000 employees and must have a very formal program.
CIS Control 17 states:
“For all functional roles in the organization (prioritizing those mission-critical to the business and its security), identify the specific knowledge, skills, and abilities needed to support defense of the enterprise; develop and execute an integrated plan to assess, identify gaps, and remediate through policy, organizational planning, training, and awareness programs.
Why Is This CIS Control Critical?
It is tempting to think of cyber defense primarily as a technical challenge, but the actions of people also play a critical part in the success or failure of an enterprise. People fulfill important functions at every stage of system design, implementation, operation, use, and oversight. Examples include: system developers and programmers (who may not understand the opportunity to resolve root cause vulnerabilities early in the system life cycle); IT operations professionals (who may not recognize the security implications of IT artifacts and logs); end users (who may be susceptible to social engineering schemes such as phishing); security analysts (who struggle to keep up with an explosion of new information); and executives and system owners (who struggle to quantify the role that cybersecurity plays in overall operational/mission risk, and have no reasonable way to make relevant investment decisions).”
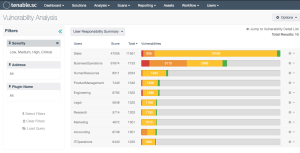
Tenable Security Center provides reports and other data display tools to help the security awareness team understand how risk mitigation efforts are progressing. As shown in the image below, we have created accounts for the executive team who organizationally, is responsible for assets. This visualization can be used to help provide awareness of the current state of the vulnerability management program. Other filters and queries can also be used to help illustrate risk management functions. As the organization matures and becomes more security aware, these types of reports can also serve as Key Performance Indicators (KPI).