Create Recast Rules from the Findings Page
On the Findings page, you can create rules which change the status of Vulnerabilities, Web Applications or Host Audits or hide them. You can also create rules from ![]() Recast, as described in Add Recast Rules.
Recast, as described in Add Recast Rules.
Tip: To learn more about when to create rules and how to manage them, see Recast .
Here are the rule types that you can add:
| Rule | Description |
|---|---|
| Recast | In the Vulnerabilities and Web Applications tabs, modify the severity findings based on query criteria. |
| Accept | In the Vulnerabilities, Host Audits and Web Applications tabs, accept the risk of vulnerability findings for Vulnerabilities and Web Applications or accept the Original Result of host audit findings and hide them from the Findings table. |
| Change Result | In the Host Audits tab, change the Original Result of host audit findings, for example, by changing Failed to Passed. |
Rule Evaluation: As new findings are imported, they are queued for evaluation against your recast rules. It is possible for a new finding to appear in the Explore > Findings view before your rule has been evaluated and applied to it.
View Caching: After a recast rule has been evaluated and the Revised Finding count is updated in the recast rules table, there is an additional cache period of up to 60 minutes for the Explore > Findings view to reflect this change.
Add a Recast or Accept Rule
To add a Recast or Accept rule from the Findings page:
-
In the left navigation, click
 Explore > Findings
Explore > FindingsThe Findings page appears.
-
Click on the Vulnerabilities or Web Applications tab.
-
In the table, in the row for the finding for which you want to create a rule, click the check box.
An action bar appears.
-
Click
 More.
More.A menu appears.
-
Click
 Recast.
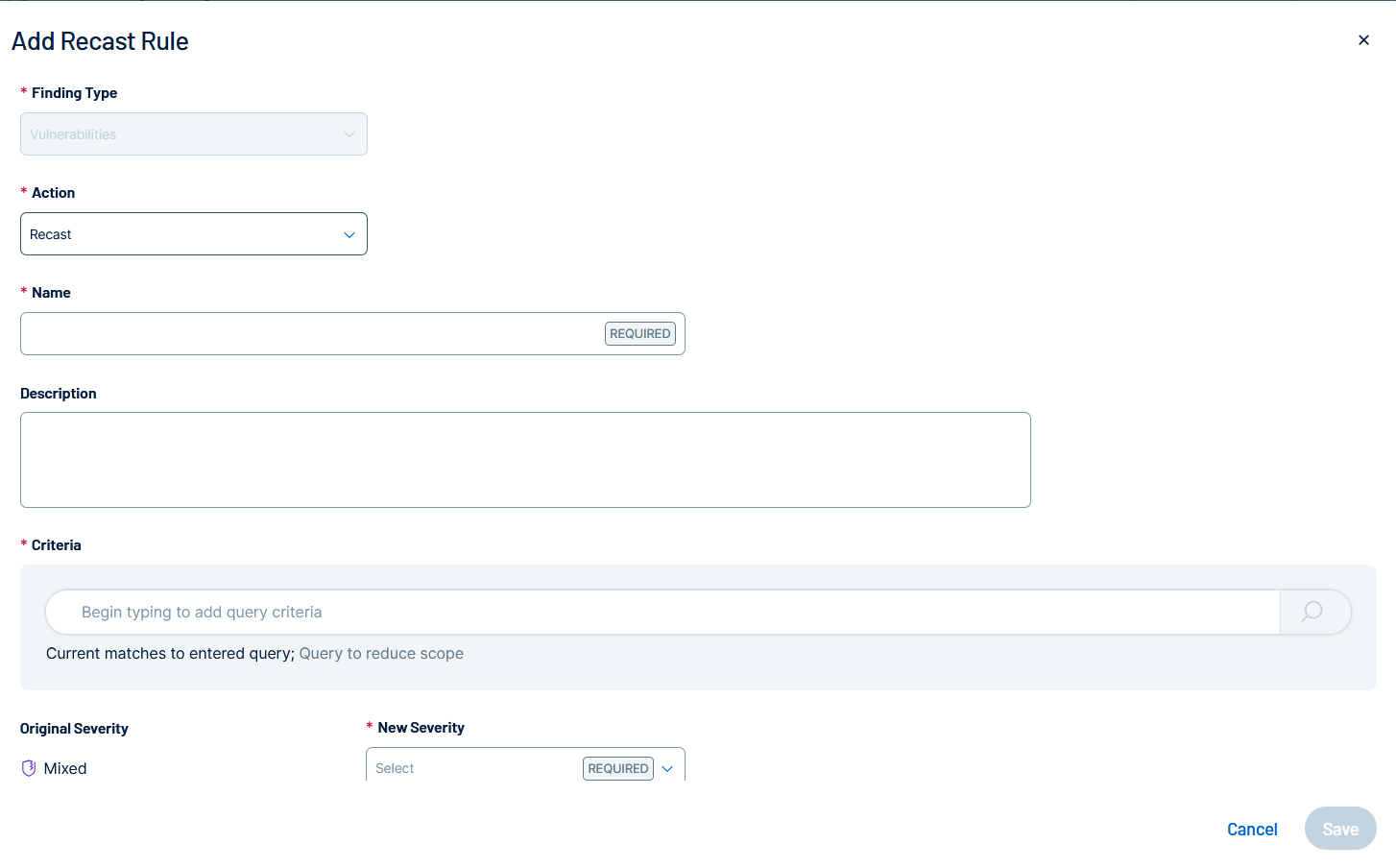
Recast.The Add Recast Rule window appears.
Note: The Criteria query bar auto populates with the rule for recasting the finding that you selected.
-
Configure the following options:
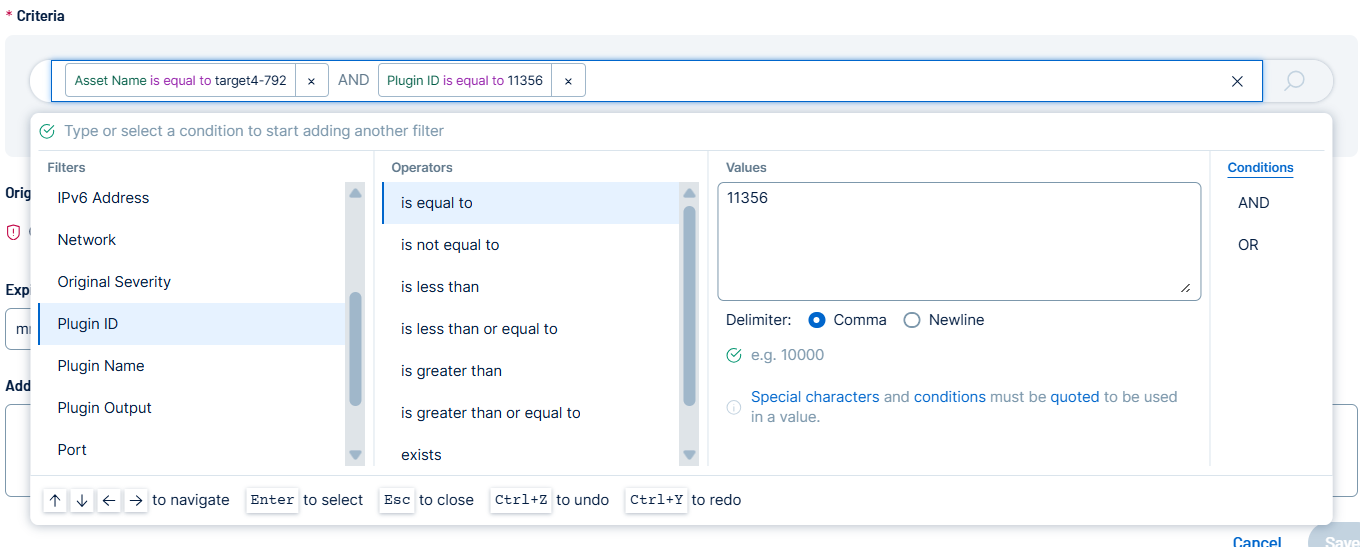
Option Description Action (required) Click Accept or Recast. To learn about these rule types, see About Recast and Accept Rules. Name (required) Type a name for this recast rule. Description Type a description for this recast rule. Criteria (required) Use this query bar to define the precise set of assets and/or findings to which this Recast rule will apply. You can construct a query using filters available in Recast Filters such as IPv4 Address, Plugin ID, FQDN, and Tags.
When you select a filter, you can select the desired Operator and Values for your query.
As you build your query, the system provides dynamic, real-time feedback by automatically displaying the exact number of Assets and Findings that match your specified criteria, allowing you to accurately scope your rule before final submission. These values appear in the Current matches to entered query below the Criteria query bar.
Tip: For more information on tags and how to create and manage them, see Tags.Tip: Use the AND / OR boolean operators to apply multiple filters to the rule.Original Severity Shows the original severity identified by Tenable Vulnerability Management. New Severity (Recast rules only) Select the severity you want to change the corresponding vulnerability to, for example Low. Expires Type a date when the rule will expire or click the  icon and select a date.
icon and select a date.Additional Comments Type comments to provide rule details. Report as false positive to Tenable (Accept rules only) Turn on this toggle when a plugin generates inaccurate findings and you want Tenable to review the results. -
Click Save.
The system processes the rule, which may take time if many findings are targeted. When complete, the rule appears in either the Vulnerabilities or Web Applications table in
 Recast and the system updates the Findings table.
Recast and the system updates the Findings table.
Create a Change Result or Accept Rule
Note: For best performance, the system supports a maximum of 5000 Change Result and Accept rules in each container, total.
To add a Change Result or Accept rule:
-
In the left navigation, click
 Explore > Findings.
Explore > Findings.The Findings page appears.
-
In the table, in the row for the finding for which you want to create a rule, click the check box.
An action bar appears.
-
Click
 More.
More.A menu appears
-
Click
 Recast.
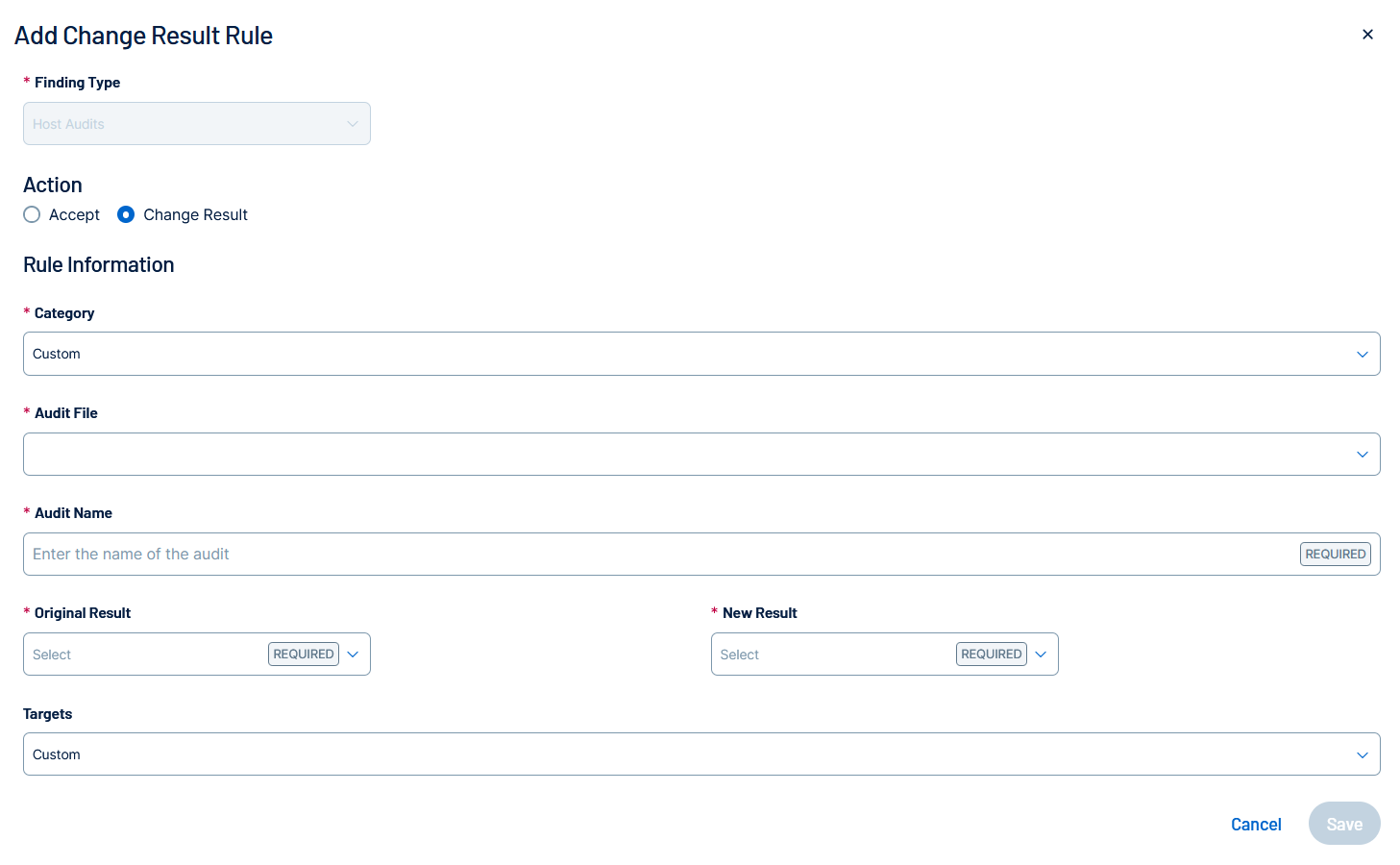
Recast.The Add Change Result Rule window appears.
-
Configure the following options:
Option Description Action Click Accept or Change Result. To learn about these rule types, see About Change Result and Accept Rules. Category Select a category for the new rule, for example, Windows. Audit File Select an audit file to run against your assets, for example, CIS_MS_Windows_11_Enterprise_Level_1_v1.0.0.audit.
Audit Name Type an audit name, for example, 9.3.1 Ensure 'Windows Firewall: Public: Firewall state' is set to 'On (recommended)'.
Original Result Select the original result of the host audit, for example, Failed.
New Result (Change Result rules only) Select the desired final status for the targeted host audit findings. This option is available only when creating a Change Result rule, which is used to override a scan's result when you have confirmed a mitigation is in place but the scanner cannot verify it. Your options are Passed, Failed, Warning. Targets (Optional) Select Custom. If the rule will override other rules, a warning appears. The newest rule takes precedence over all conflicting earlier rules. Target Hosts For Custom targets, type a comma-separated list of IPv4 or IPv6 addresses or ranges, Classless Inter-Domain Routing (CIDR) notation, or fully qualified domain names (FQDNs). The system supports up to 100 items.
Expires (Optional) Select After or Exact Date. Then, type a date when the rule expires or click the  icon and select a date.
icon and select a date.Comments Type comments to provide rule details. -
Click Save.
The system processes the rule, which may take time. When complete, the Findings page updates and the rule appears in
 Recast.
Recast.