Recast
Recast in Tenable Vulnerability Management is a powerful tool for customizing your risk management framework. It allows you to create rules that modify a vulnerability's severity or accept the risk, helping you focus remediation efforts on what's most critical. This is useful for addressing findings that are not relevant to your specific environment, such as a vulnerability on a decommissioned asset, or for adjusting the risk of a finding that is already mitigated by other means. Accept rules help you keep your dashboards clean by hiding findings you've accepted the risk for, while Change Result rules for host audits allow you to modify a failed audit check to a "passed" status when the issue has been addressed outside of the standard scan detection.
Rule Evaluation: As new findings are imported, they are queued for evaluation against your recast rules. It is possible for a new finding to appear in the Explore > Findings view before your rule has been evaluated and applied to it.
View Caching: After a recast rule has been evaluated and the Revised Finding count is updated in the recast rules table, there is an additional cache period of up to 60 minutes for the Explore > Findings view to reflect this change.
Example
Imagine you have an asset with a vulnerability on an FTP service. You no longer need FTP, so you shut down the service. Now, Tenable Vulnerability Management cannot verify the vulnerability as patched, so it continues to appear in your Findings list. You can use a recast or accept rule to ignore this vulnerability finding without needing to delete the asset and begin a fresh scan.
To access the Recast page:
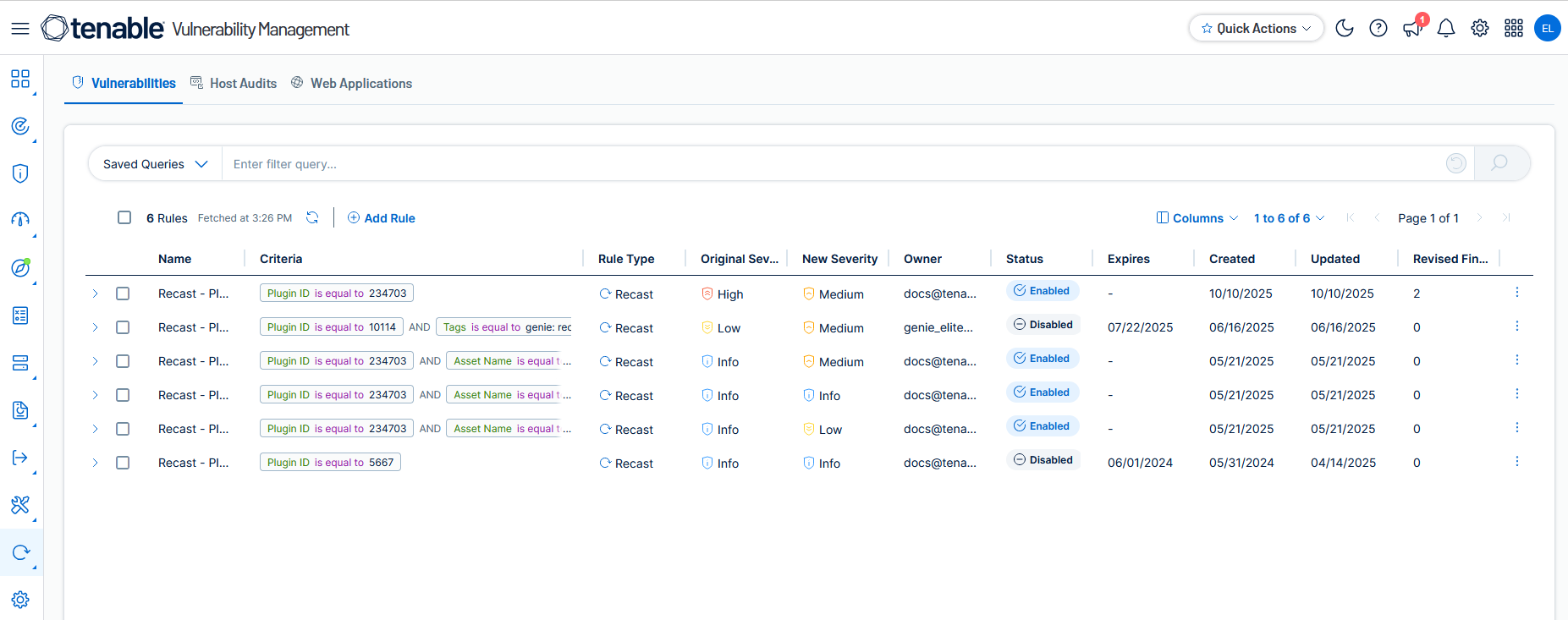
Here, you can view a table showing your current recast rules for each finding type: Vulnerabilities, Host Audits, and Web Applications.
This documentation explains how to add recast rules, what filters are available for building criteria queries, when to use them, and how to manage them. Also, you can view details about available recast columns for each finding type. For more information, see the following topics:
| In This Topic | Learn How To... |
|---|---|
| About Recast and Accept Rules | Know the how and why of recasting or accepting outcomes of vulnerability and web applications findings. |
| About Change Result and Accept Rules | Know the how and why of changing or accepting outcomes of host audits. |
| Recast Rule Details | Understand the details pane for each recast rule type. |
| Add Recast Rules | Understand how to add new recast rules for each finding type: Vulnerabilities, Host Audits, and Web Application Findings. |
| Manage Recast Rules | Learn how to manage recast rules. |
| Recast Columns | Understand the columns in the tables for each of Vulnerabilities, Host Audits, and Web Application Findings. |
| Recast Filters | Know the filters available for your criteria queries for each finding type. |