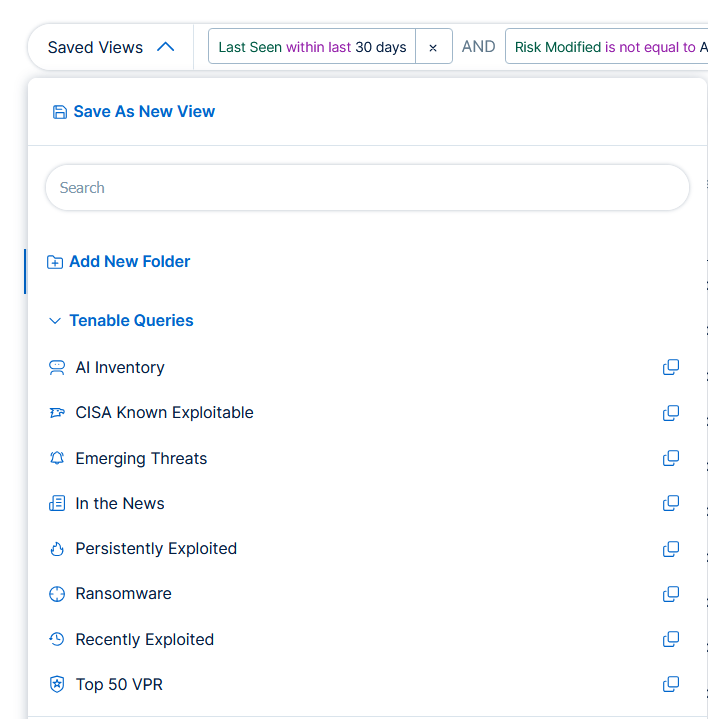
Tenable Queries
Tenable Queries are a set of pre-built, dynamically updating filters curated by Tenable Research to help you immediately focus on the most critical threats facing your organization.
Tenable Queries in Explore
The table below lists the Tenable Queries available in Explore -> Assets, by asset type. These queries help you segment your environment by specific asset characteristics.
| Tenable Query | Asset Types | Risk Focus | Criteria Applied |
|---|---|---|---|
| External Assets (ASM) | Host, Web Application | Assets or domains discovered by Tenable Attack Surface Management, integrated with the steps described in Manage Integrations in the Tenable Attack Surface Management User Guide. | Filter on assets integrated via the ASM process. |
| Network Devices | Host |
Assets identified as networking devices (e.g., routers, switches, firewalls, and SSL gateways). |
Asset type filter for network device classifications. |
The table below lists the Tenable Queries available in Explore->Findings, by findings type. These queries are driven by Tenable Research's threat intelligence to highlight vulnerabilities with the highest real-world risk, based primarily on the Vulnerability Priority Rating (VPR).
| Tenable Query | Findings Types | Risk Focus | Criteria Applied |
|---|---|---|---|
| AI Inventory | Vulnerabilities, Web Application Findings | AI-related Vulnerabilities and Web Application findings, including those identifying the presence of AI/LLM tools and services. | Filter on Tenable plugins related to AI/LLM detection. |
| CISA Known Exploitable | Vulnerabilities |
Vulnerabilities that appear in the CISA Known Exploited Vulnerabilities Catalog. |
The vulnerability's CVE appears in the CISA KEV Catalog. |
| Emerging Threats | Vulnerabilities |
Vulnerabilities being actively monitored by Tenable in three areas:
|
VPR Key Drivers such as Threat Source and Exploit Code Maturity. |
| In the News | Vulnerabilities | Vulnerabilities being widely reported in the press with notable public coverage over the past 30 days. | Based on VPR Key Driver: Threat Sources. |
| Ransomware | Vulnerabilities | Vulnerabilities used in current or historical ransomware attacks, as determined from evidence gathered by the Tenable Research team. | VPR Key Driver indicates association with ransomware. |
| Recently Exploited | Vulnerabilities | Vulnerabilities being leveraged by threat actors over an extended period of time in targeted attacks, ransomware, or malware campaigns. These vulnerabilities are curated by the Tenable Research team. | VPR Key Driver: Threat Sources and Threat Recency . |
| Persistently Exploited | Vulnerabilities | Vulnerabilities being leveraged by threat actors over an extended period of time in targeted attacks, ransomware, or malware campaigns. These vulnerabilities are curated by the Research team. | Curated by the Research team based on historical exploitation evidence. |
| Top 50 VPR | Vulnerabilities, Web Application Findings | The top 50 vulnerabilities by Vulnerability Priority Rating (VPR). | The 50 unique vulnerabilities with the highest VPR score in your environment. |
Accessing and Using Tenable Queries
Tenable Queries are available in the Saved Views dropdown menu in Explore. When you select a Tenable Query, the table shows only the matching vulnerabilities.
To show Tenable Queries:
 Explore > Assets or
Explore > Assets or