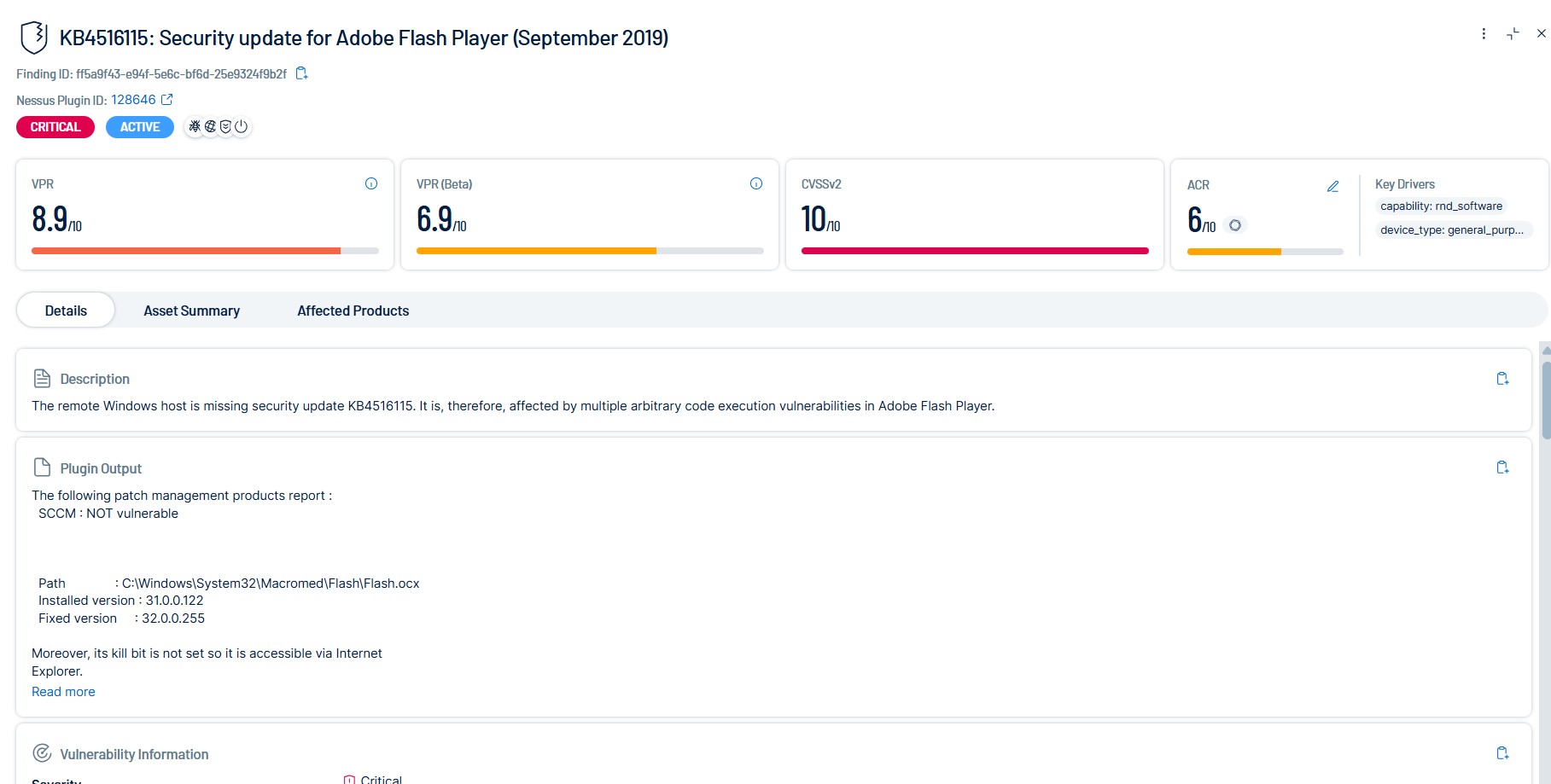
View Findings Details
On the Findings page, click a finding to open a pane of details. Then, click  to expand the pane.
to expand the pane.
The upper part of the Findings Details page contains the following information.
|
Attribute |
Description |
|---|---|
|
Finding Name |
The name of the finding, for example Microsoft Netlogon Elevation of Privilege (Zerologon) (Remote). |
|
Nessus Plugin ID |
If relevant, the unique identifier for the Tenable Nessus plugin that found the vulnerability. |
|
Severity |
The vulnerability's CVSS-based severity. For more information, see CVSS vs. VPR. |
| State |
The state of the vulnerability, for example Active. |
| Exploitability |
Icons indicating characteristics of the vulnerability that determine its potential exploitability; for example, Exploited By Malware or Remotely Exploitable. |
| VPR | The vulnerability's vulnerability priority rating. |
| VPR(Beta) |
The vulnerability's vulnerability priority rating using VPR (Beta) scoring. Tip: For more information, see the Scoring Explained Quick Reference Guide.
|
| CVSSv2 | The corresponding vulnerability's CVSSv2 base score. |
| ACR | (Requires Tenable One or Tenable Lumin license) The Tenable-defined Asset Criticality Rating (ACR). |
The lower part of the Findings Details page is divided into tabs. Not all information appears for all findings types.
Details
The Details tab breaks down information about a finding including its description and details for the corresponding vulnerability.
|
Section |
Description |
|---|---|
| Description | A description of the corresponding vulnerability. |
| Plugin Output | Output from the plugin that identified the vulnerability. |
|
Vulnerability Information |
Important information about the vulnerability, including the following attributes:
|
| Fixes |
If available, details about fixes for the vulnerability, including:
|
| Vulnerability Detection Timeline |
Information about when the vulnerability was detected, including:
|
| VPR Key Drivers |
Information about the key drivers Tenable uses to calculate a VPR for the vulnerability, including, but not limited to:
|
| VPR (Beta) Key Drivers |
Information about the key drivers Tenable uses to calculate a VPR (Beta) score for the vulnerability, including, but not limited to:
|
| Plugin Details |
Information about the plugin that detected the vulnerability, including:
|
| CVEs | Links to the CVEs corresponding to the finding. Click a link to open the the Vulnerability Profile page in the Vulnerability Intelligence section. |
| Risk Information |
Information about the vulnerability's risk profile, including:
|
| References | Industry resources that provide additional information about the vulnerability. |
Asset Summary
The Asset Summary tab contains details about the asset corresponding to the finding, along with when the asset was last seen by a scanner.
|
Section |
Description |
|---|---|
| Asset Summary |
Information about the affected asset, including:
|
| Tags | A panel containing tags assigned to the affected asset. Click |
| CPE |
The Common Platform Enumeration (CPE) numbers for vulnerabilities that the plugin identifies, using a standardized naming convention. To learn more, see the National Vulnerability Database website. |
|
Last Seen |
Information about when the affected asset was last identified on a scan, including:
|
Affected Products
A table of information about the products on the affected assets. This section only appears for Vulnerabilities and has the following columns.
|
Column |
Description |
|---|---|
| End of Life | If applicable, the end of life date for the affected product. |
| Path | The installation path of the product. |
|
Product |
The product name. |
| Product Type | The type of product, for example Operating System. |
| Vendor | The vendor who makes the product affected by the vulnerability, for example Microsoft. |
| Version | If relevant, the version number of the product. |