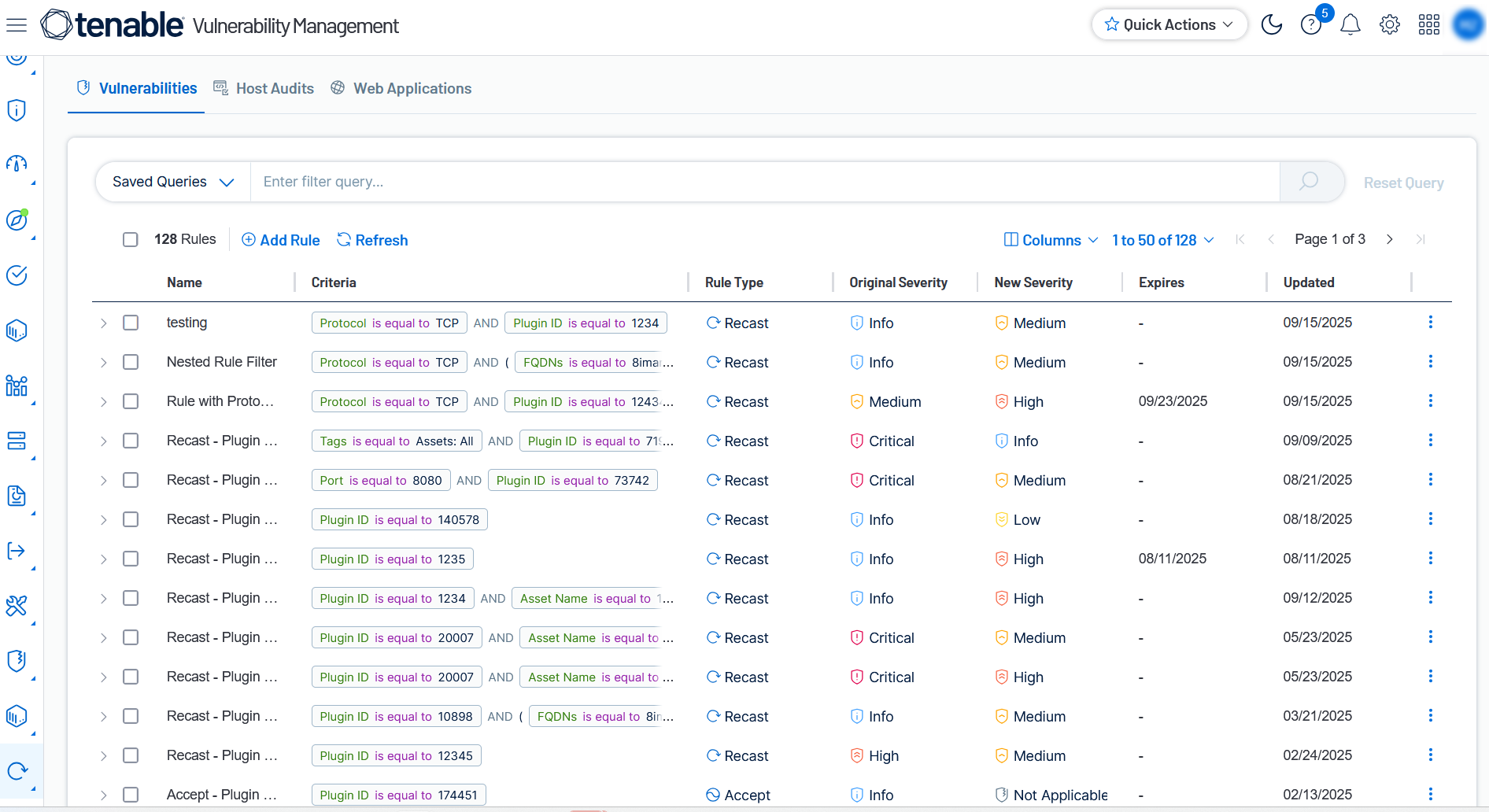
Recast Rules
In Tenable Vulnerability Management, you can customize Tenable's risk management framework to fit the needs of your organization. While Recast rules modify the severity of all findings that correspond to a Plugin ID, Accept rules hide the findings instead.
Example
Imagine you have an asset featuring an FTP with an open vulnerability. You no longer need FTP, so you shut down the service. Now, Tenable Vulnerability Management cannot verify the vulnerability as patched, so it continues to appear in your Findings list. You can use a recast or accept rule to ignore this vulnerability finding without needing to delete the asset and begin a fresh scan.
For more information on recast and change result rules, see Recast and Add Recast Rules.
To access the Recast page via Settings:
-
In the left navigation, click
 Settings.
Settings.The Settings page appears.
-
Click the
 Recast tile.
Recast tile.The Recast page appears.
To add Recast, Accept, or Change Result rules, see Add Recast Rules.
Here, you can view information about your recast rules including:
-
Rule Type — Indicates the type of rule, for example
 Recast,
Recast,  Accept, or
Accept, or  Change Result. Tip: To learn about these rule types, see About Recast and Accept Rules and About Change Result and Accept Rules.
Change Result. Tip: To learn about these rule types, see About Recast and Accept Rules and About Change Result and Accept Rules. -
Plugin ID — The plugin ID associated with the vulnerability.
-
Original Severity — The original severity of the vulnerability before the rule was applied.
-
New Severity — The new severity of the vulnerability after the rule was applied.
-
Tags — Where applicable, the tag filters applied to the rule.
Note: Tag filters can only be applied to rules created via the Findings page or the Quick Actions menu. These rules are view-only within the Settings > Recast section of the user interface. -
Owner — The Tenable Vulnerability Management user who created the rule.
-
Expires — The date and time on which the rule expires. If the rule does not expire, this column is blank.
-
Created — The date and time at which the rule was created.
-
Updated — The date and time at which the rule was last updated by a user.
-
Actions — Click the
 button to view actions you can take with the rule: Edit, Disable, Delete. For more information, see Manage Recast Rules.
button to view actions you can take with the rule: Edit, Disable, Delete. For more information, see Manage Recast Rules.
See Recast Columns for the full list of columns for each finding type.