Compliance Dashboard
Compliance to security frameworks such as NIS 2 Directive, ISO 27001 Controls are now mandatory for most of the critical infrastructure companies to clear audit checks.
Navigating compliance frameworks can be a complex process and require specialized knowledge. Use the Compliance dashboard to get a high-level understanding of all assets, vulnerabilities, and events that might affect your organization's critical business operations and also help answer these critical audit questions:
Which security policies do you have in place to detect suspicious activity?
How long does it take you to handle an incident?
Are the alerts integrated with SOC/SIEM as part of your Incident Response (IR) plan?
How many security events did you have on your critical assets in the last week or month?
The Compliance dashboard enables you to align key security measures with regulatory requirements, track your progress and improvements over time, and strengthen your security posture.
Using the dashboard data, you can identify areas where the organization is compliant and improve areas that impact the business from a risk perspective.
To view the compliance dashboard:
In the left navigation bar, click Dashboards > Compliance.
The Compliance dashboard appears.
In the left navigation bar, click Risks > Compliance.
The Compliance dashboard appears.
The dashboard includes the following widgets.
| Widget | Description |
|---|---|
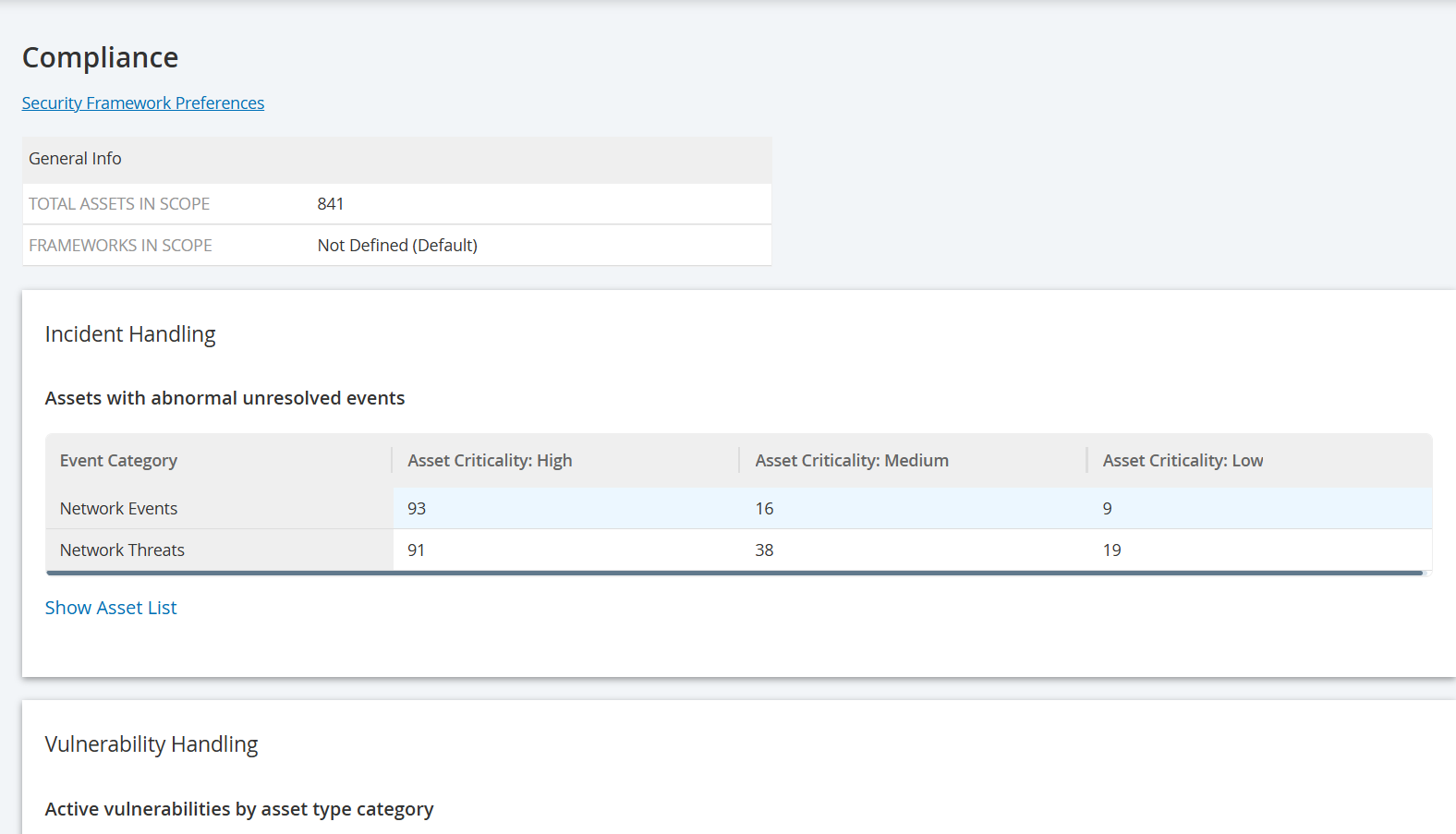
| Incident Handling | Provides an overview of the assets at risk by their asset criticality: High, Medium, or Low. You can use this data to respond to high-risk security incidents. Based on the resolution of high-critical events in the last 30 days, OT Security records the Event Mean Time to Respond (MTTR). This value helps you understand the mean time required to respond to each critical event. MTTR is a critical key performance indicator and a shorter MTTR value indicates a more efficient incident resolution process. Note: To view all high-risk assets with suspicious open events, click the Show Asset List link. To close the assets list, click Hide Asset List. |
| Vulnerability Handling | Provides an overview of all vulnerabilities by their severity and the affected asset types. This widget allows you to identify, assess, report, and remediate OT, network, and IoT vulnerabilities on an ongoing basis. Based on the vulnerabilities fixed in the last 90 days, OT Security records the Mean Time to Respond (MTTR). MTTR and Service Level Agreement (SLA) parameters help understand the mean time required to respond for each critical vulnerability and track the progress of the team in mitigating the vulnerabilities based on the defined SLAs. A shorter MTTR value indicates a more efficient incident resolution process. Note: To view all high-risk assets with active critical vulnerabilities, click Show Asset List. To close the assets list, click Hide Asset List. |
| Configuration & Change Management | Provides an overview of all assets with unresolved configuration events such as changes made after setting a baseline and critical controller status activities such as the stopping of the device. The data in this widget helps you detect unauthorized modifications and critical events thereby ensuring operational continuity and quick recovery during service disruptions. Note: To view high-risk asset with configuration change events, click the Show Asset List link. To close the assets list, click Hide Asset List. |
| External Exposure Risk | Provides an overview of external connections to Industrial Control Systems (ICS) networks. You can use the data in this widget to help identify, evaluate, and mitigate OT, network, and IoT assets from unexpected external communication. This data also ensures compliance with supply chain security where ICS equipment and machine builder vendors use hybrid models and move their portal and engineering stations to the cloud, where there is a possibility of external exposure. |
| Insecure Cryptography | Provides an overview of insecure cryptographic events, such as unsecured logins and unencrypted credentials. This data can help monitor and detect insecure cryptographic events, and in turn prevent the compromise of sensitive information and service disruption. Note: To view all high-risk assets with insecure authentication events, click Show Asset List. To close the assets list, click Hide Asset List. |
| Insecure Communication Monitoring | Provides an overview of high-risk assets with unsecured communication events and unauthorized access. This data can help avoid any insecure communication and suspicious unauthenticated access that may leave sensitive information or critical assets vulnerable to attackers. Note: To view all high-risk assets with insecure authentication events, click Show Asset List. To close the assets list, click Hide Asset List. |
| Risk Assessment | Provides an overview of assets at risk by their criticality. This data helps you assess and manage risks associated with OT, network, and IoT assets and proactively identify and mitigate potential threats. Note: To view all assets that are at high risk, click the Show Asset list link. To close the assets list, click Hide Asset List. |