Asset Discovery and Assessment
Organizations need to identify the existence and location of critical assets to ensure that said assets are monitored and protected based on each asset’s business risk rating. Discovering assets enables organizations to establish an inventory, which can be used to assess and mitigate associated risks to the organization. An asset inventory enables organizations to configure scans to probe for common weaknesses in the platform or application.
Asset Discovery
Tenable Vulnerability Management supports the discovery of assets without scanning the assets for vulnerabilities. Tenable Vulnerability Management provides scan templates for discovery scanning and passive detection using Tenable Network Monitor in discovery mode. Tenable Vulnerability Management also supports connectors from third parties such as ServiceNow or API calls to manually enter the assets. Assets that have not been scanned for vulnerabilities do not count towards the organization's asset license limit. After assets are discovered in this manner, a strategy can be developed to categorize and scan assets for vulnerabilities. Importing assets via the API or third party integration, such as ServiceNow, increases scanning capabilities by leveraging the extensive ServiceNow Configuration Management Database (CMDB) to accurately track assets. For more information on reconciling assets between ServiceNow and Tenable Vulnerability Management , please refer to the Tenable and ServiceNow Integration Guide.
For more information on Container Security Connectors please refer to the Configure Container Security Connectors to Import and Scan Images page.
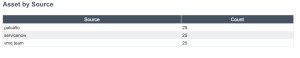
Assets by Source
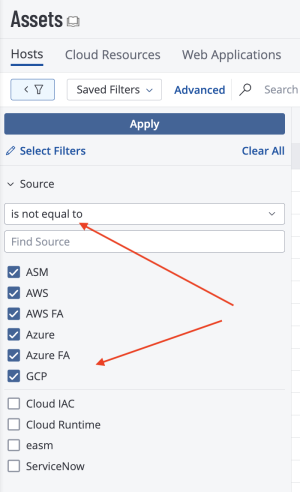
The Asset by Source widget displays discovered third party assets that are not licensed, and have not been assessed for vulnerabilities. This query is accomplished by setting the source filter to ”is not equal to” and selecting the following values: GCP, AWS, SSM, AZURE, AZURE_FA, WAS, INDUSTRIAL_SECURITY, ASM, NNM, NESSUS_SCAN, or NESSUS_AGENT. The widget provides a count of assets by collection method. Assets listed have not been scanned for vulnerabilities or by other Tenable sensors. The ability to import assets from external sources into Tenable Vulnerability Management reduces the number of blind spots, and increases the likelihood of complete scan coverage.
To recreate the results from this widget,, navigate to the Explore Overview → Assets page in Tenable Vulnerability Management as shown below. Select Source as a filter option, choose “is not equal to” from the drop down menu, and check the boxes for the appropriate options. Click Apply to apply the filter to the results.
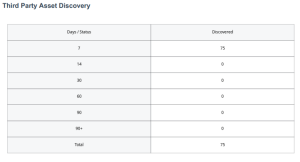
Third Party Asset Discovery
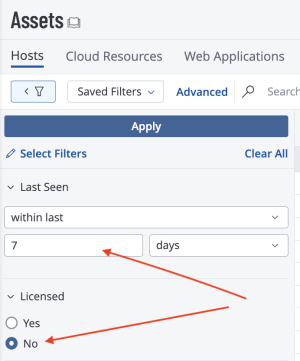
The Third Party Asset Discovery widget displays the count of assets that have been imported and considered discovered but not scanned, grouped by time ranges from when the last import occurred. The data is organized over time periods for 7,14, 30, 60, 90, and 90+ days using the Last Seen filter. As with the “Asset By Source” widget, the source filter is set to remove any asset that is discovered by Tenable sensors. Once a third party asset is scanned, the asset becomes licensed and will be removed from this widget. This widget is a useful gauge to determine the maturity of the vulnerability management program, since it demonstrates whether or not assets are scanned on a regular basis as they are added to the network. For example, organizations may scan the network weekly, or even daily. If there are gaps in scanning activity there may be higher counts in the longer timeframes.
The queries in the Third Party Asset Discovery widget can be created manually via the Explore Overview → Assets page in Tenable Vulnerability Management as shown below. Select Last Seen as a filter option and choose a time frame. Then add a second filter for Licensed and select No to display only the assets that have not been scanned for vulnerabilities. Click Apply to apply the filter to the results.
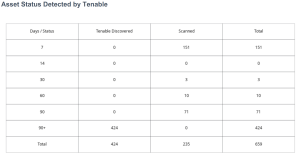
Asset Status Detected by Tenable
The Asset Status Detected by Tenable widget provides an overview of assets that have been recently discovered or scanned with or without credentials. The timeframe displayed shows key time periods for 7,14,30, 60, 90, and 90+ days using the Last Seen filter to help determine what new devices are entering the environment. New devices that have not been evaluated introduce unknown risk. Assets that are scanned or discovered are only counted towards the license limit if that asset has been assessed for vulnerabilities.
The Days/Status column contains static rows displaying time ranges from 7 to 90+ days. Each row utilizes the last_observed filter to display information for the specified time range. These rows are the primary focal point for the other columns.
The Tenable Discovered column displays assets that have been discovered with host discovery plugins. A healthy environment will have low numbers in the Tenable Discovered column, with those numbers increasing as they progress downwards in the matrix. This is a clear indication that no new devices have been recently discovered. The “Is Licensed is equal to False” filter is used for this column.
The Scanned column displays assets that have been scanned using credentials. Organizations with good security practices will have the largest numbers at the top with lowest numbers at the bottom (the reverse of the Tenable Discovered column), indicating that devices are being scanned on a regular and frequent basis. The “Is Licensed is equal to True” filter is used for this column.
The Total column and row displays the total number of assets for each row or column.
Assets that have been scanned using a Host Discovery template, as shown below, scanned with discovery-only plugins, or have been imported and do not contain vulnerability data (such as ServiceNow data) are not associated with any risk-based vulnerabilities.
Data from Tenable Network Monitor running in discovery mode will also not count towards the license limit. Scanned assets with risk-based vulnerability data count against the license, regardless of the source (Nessus Agent or Tenable Vulnerability Management). These vulnerability records indicate some level of a risk assessment has been performed. Organizations with a robust vulnerability management program will continuously close the loop between those assets which are discovered and assets which are assessed within an acceptable period of time.
In addition to IP addresses, Tenable Vulnerability Management uses asset attributes to identify an asset. When an asset is first discovered, information is gathered that may include a BIOS UUID, MAC Address, NetBIOS name, FQDN, and other attributes that can be used to reliably identify an asset. Additionally, authenticated scanning and Nessus agents assign a Tenable UUID to the device. When an asset is subsequently scanned, the information is compared to previously discovered assets. If the information does not match a previously discovered asset, the new device is added to the asset inventory. Tenable Vulnerability Management leverages a variety of methods and proprietary algorithms to avoid double counting the same asset. This process increases the accuracy of tracking and identifying assets across the network.
More details on how Tenable Vulnerability Management can be leveraged to identify assets can be found on the Mapping, Classification, and Categorization of Assets and the Key Asset Attributes pages. For more information related to networks, please refer to the Networks section of the documentation.
Asset Assessment
Vulnerability assessments are excellent for testing visible network services and finding vulnerabilities or misconfigurations that may expose sensitive information. The health of an organization’s scanning program is based on the level of access the scanner is assigned during the vulnerability scan. When organizations scan with invalid or unprivileged credentials, proper and thorough assessments are not completed, and lead to false sense of security or in accurate risk assessments.
Credentialed scans provide more detailed results that can help to detect outdated software, vulnerabilities, and compliance issues. Credentials enable the scanner to login to the asset as an authorized user and view configuration and other data that the provided credentials are permitted to see. Credentials from a privileged user, such as the administrator or root, provide the most accurate information, enabling organizations to have a more comprehensive view of cyber risk for that asset.
Tenable provides several plugins to assist with common scan problems, such as determining if scans are incomplete, have errors, or credentials are bad or missing. Organizations with good scan health leverage this information to ensure scans are configured to use the appropriate plugins and settings for the devices being scanned. In addition to reporting on complete scans, the Scan Health widget identifies the most common scan issues, such as no credentials, bad credentials, incomplete scans, and scan errors. This information can be used to demonstrate that organizations are using appropriate authentication for scanning. Tenable recommends scanning at least twice per week with all plugins to achieve the most complete scan and vulnerability data.
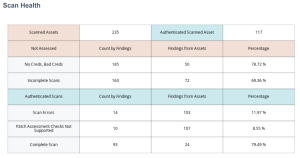
Scan Health
The Scan Health widget is separated into two sets of data points: assets scanned with authentication; and assets scanned without authentication. The rose colored cells indicate errors from scans where authentication was not configured or failed. The teal colored cells indicate a degree of authentication was successful. All data points within this widget are dependent on the level of authentication. If a majority of the assets are scanned without credentials, the vulnerability counts could potentially be much lower. The vulnerability counts could also be lower for assets that are scanned with credentials that do not provide administrative access.
Note: Assets where the scanner has the highest privileged credentialed access will have the best data on the risk exposure to the asset.
Each of the rows of the Scan Health widget are defined below:
No Creds, Bad Creds – This row provides the asset count for each scan result with plugin No Credentials (110723), Failure for Provided Credentials (104410), or OS Security Patch Assessment Not Available (117886) detected. The results indicate that either no credentials were used in the scan or the credentials used were not valid for the asset. These results are compared against the overall scanned assets, for a percentage of assets where a successful vulnerability scan was not completed.
Incomplete Scans – This row provides the asset count for each scan result with Windows SMB Registry Not Fully Accessible (10428), OS Security Patch Assessment Failed (21745), or SSH Commands Require Privilege Escalation (102094) plugins. The results indicate that successful authentication was not fully achieved, the patch assessment failed to execute or there was some other related login problem. These scans may have used valid credentials but some other problem occurred and the scan was aborted. These results are compared against the overall scanned assets, for a percentage of assets where a successful vulnerability scan was not completed.
Scan Errors – This row provides the asset count for each scan result with Insufficient Privilege (110385) or Patch Assessment Checks Not Supported (110695). These assets had successful authentication, and therefore are compared against the Authenticated Scan result column. However, an error was detected by a plugin or scan results for the operating systems were not available.
Complete Scan – This row provides the asset count for each scan result with the OS Security Patch Assessment Available (117887) plugin present. These assets have local checks enabled and the most complete scan possible was achieved at that time. These assets had successful authentication, and therefore are compared against the Authenticated Scan result column. Having a majority of assets present in this row demonstrates organizations with a healthy vulnerability management program.
Authenticated Scanning
Understanding the differences between an authenticated scan, and a non-authenticated scan is critical. A non-authenticated scan, discovery scan, or default scan is a remote test performed without authentication. Non-authenticated scans probe the target with various packets. This external view of the target can often determine the type of the device, what ports are open, and what services are running on those ports. However, scanning without credentials does not provide much detail on missing OS or third-party patches or compliance with industry benchmarks and frameworks, such as the CIS Benchmarks or the NIST Cybersecurity Framework (CSF).
When a scan is initiated, Nessus probes the target to determine which ports can be used to login to the target. If credentials have been provided, Nessus will use the credentials to login to the asset, and attempt to perform a more thorough assessment. Privileged access to the asset is necessary during an authenticated scan to determine information such as installed software, including the version, anti-virus software configuration, password policies, missing patches, and misconfigurations. If no credentials are provided, or the credentials are invalid, Nessus will continue to probe the device externally.
The quantity of vulnerabilities reported between an authenticated and unauthenticated scan can often be 10 times greater when scan use privileged credentials. Tenable Vulnerability Management customers can use Predictive Prioritization and Vulnerability Priority Rating (VPR) to help manage this vulnerability overload. These vulnerabilities always existed; authenticated assessments provide visibility that an unauthenticated one cannot. In general, fully credentialed scans are preferred, as they create less network overhead and up to ten times more information is returned to help with risk identification and prioritization. The integrity of the vulnerability scan results are based on the level of access provided to the scanner, for complete vulnerability assessment, Tenable recommends using credentials or agent based scans. Reference the Credentials in Vulnerability Management Scans document for more information on scan credentials configuration.