SLAs and Remediation
Vulnerability Management Service Level Agreements (SLAs) often change from one organization to the next, however meeting these SLAs is a common issue among organizations industry wide. SLAs define an expected level of service by which measurements, metrics, or penalties can be established. SLA compliance is a critical component of a vulnerability management program.
There is no set timetable to resolve vulnerabilities that fits every situation. SLAs can vary from organization to organization, and even vary between business units within the organization. Tenable recommends aligning SLAs with technology or business objectives, starting with the most important assets. The Department of Homeland Security has made available 10 resource guides to help organizations implement business practices to reduce cyber risk. Volume 4: Vulnerability Management provides guidance for organizations to work with stakeholders to develop remediation timeframes that align with business goals.
As vulnerabilities are identified, remediation must be prioritized and tracked. Reviewing remediated vulnerabilities and the remediation time frame provides valuable information to the organization on the success of the risk remediation program.
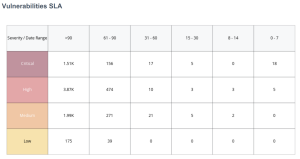
Vulnerability SLA Widget
The Vulnerability SLA widget enables organizations to track and report on their remediation efforts over time and severity. Vulnerabilities are displayed by severity and time to remediate from less than 7 days to over 90 days. Tenable recommends prioritizing remediation of exposures that pose the greatest risk to the organization. This widget enables organizations to identify the vulnerabilities that are not being remediated quickly, or outside of established timeframes. Organizations with an effective vulnerability management program will have critical vulnerabilities displayed in the far right three columns, representing remediations occurring within 30 days or less. Vulnerabilities that pose less risk exposure could have higher counts in the middle of the matrix in the 30-90 day time period. Numbers in the far left of the matrix depict vulnerabilities that are remediated after 90 days have passed.
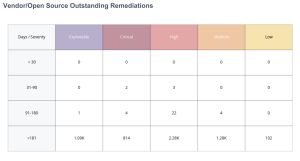
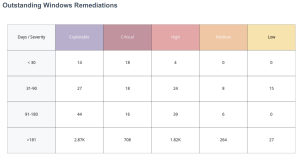
Outstanding Remediations
The time between when a vulnerability is discovered and when the vulnerability is typically exploited; called the ‘time to exploit’ is rapidly decreasing. The CISA INSIGHTS report titled Remediate Vulnerabilities for Internet-Accessible Systems notes that adversaries are able to exploit a vulnerability within 15 days, on average. This is down from a previous average of over 30 days the previous year. For organizations this means that patching must be a priority to reduce threat as unpatched vulnerabilities over 15 days old begin to present a significant risk.
The Outstanding Windows Remediations and the Vendor/Open Source Outstanding Remediations widgets use plugin families along with patch publication date filters to communicate the presence of vulnerabilities in the network. The time frame shown are the days since a patch or other mitigation was offered by the software vendor, and not the time the vulnerability has affected the asset. The exploitable column denotes the vulnerability counts in combination with CVSSv3 rating, while the severity based column focuses on the CVSSv3 score only. This distinction is important as not all vulnerabilities are known to be exploitable.
Unpatched assets expose organizations to vulnerabilities that could be exploited. As new assets are added to the network, and scanned for the first time, the system shows counts for vulnerabilities with known patches available. As new assets are detected, any related vulnerabilities have not been present in the network for a long time, but a patch has been available that has not been applied yet. Organizations with a mature vulnerability management process will address these concerns during the initial build process.
Assets with the largest number of missing patches typically represent a higher level of remediation effort and may be the most time-consuming to address. Vulnerability severity, exploitability, and time since patch availability age are displayed as the key points of vulnerability management. Organizations with an effective vulnerability management program will typically patch within 90 days of the date the patch is made available, and usually will have lower counts in the last two rows of these matrices. These organizations will most likely only have data presented in the first row (under 30 days), especially for the highest severity vulnerabilities.
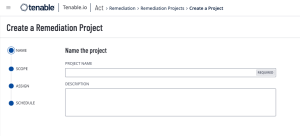
Assets that are exploitable or have a higher severity rating represent a fast lane for attackers. Prioritizing remediation of these vulnerabilities is an effective strategy to reduce risk. Tenable has provided a method to create a Remediation Project so findings can be prioritized, scope of work can be defined, projects can be assigned, and progress can be tracked. Remediation projects can be set to be completed at a fixed date, or within a specified timeframe.
More information on the creation , viewing, editing, closing, or suspending of remediation projects can be found on the Remediation Projects page of the Tenable documentation. Remediation projects that are created within Tenable Vulnerability Management can also be exported as a .csv for use outside of Tenable Vulnerability Management.