Asset Inventory and Discovery
The Asset Inventory & Discovery (SEE) Tenable Vulnerability Management Dashboard and the Asset Inventory & Discovery (SEE) Tenable.sc Dashboard displayed the following provides guidance to establish an asset discovery, including:
-
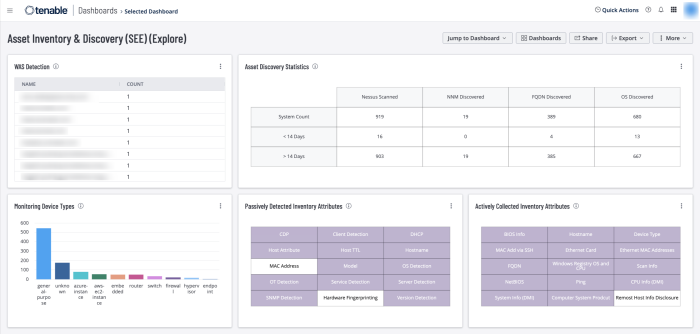
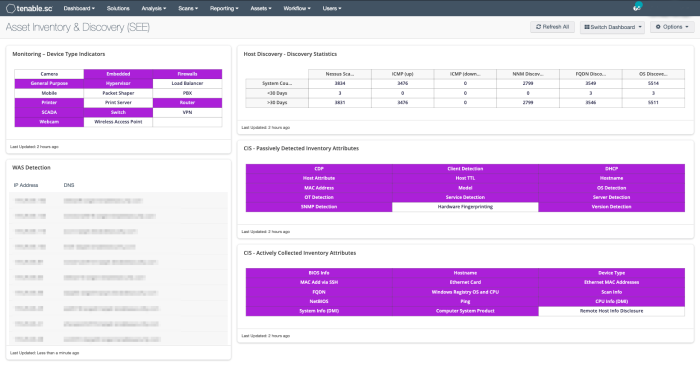
Actively and passively detected assets
-
Asset discovery statistics
-
Detected web applications
-
Indications for device types (printers, cameras, routers, firewalls, WAPs)
In addition to the Articles previously listed, the following DORA Articles are related to Asset Inventory and Discovery efforts:
-
Article 8.2, Financial entities shall, on a continuous basis, identify all sources of ICT risk
-
Article 8.3,Financial entities shall identify all information assets and ICT assets, including those on remote sites, network resources and hardware equipment
-
Article 16.1 (d), allow sources of ICT risk and anomalies in the network and information systems to be promptly identified and detected
In this section the following Tenable products will be highlighted:
-
Tenable Security Center
-
Tenable Vulnerability Management
-
Tenable OT Security
For more information on Asset Discovery and Classification see the Asset Inventory and Discovery Cyber Exposure Study.
Tenable OT
Industrial controls are not the first things that come to mind when working with the financial industry. However, there are many IoT devices that may be present. IoT sensors and smart devices are known to be installed to monitor bank branches, ATMs, POS Terminals,and data centres, such as building automation and building management. IoT devices are being used to deliver real-time data on financial interactions between customers and banks to generate analytics. And with the advancements of artificial intelligence (AI) and machine learning, we can expect to see more of these devices being connected.
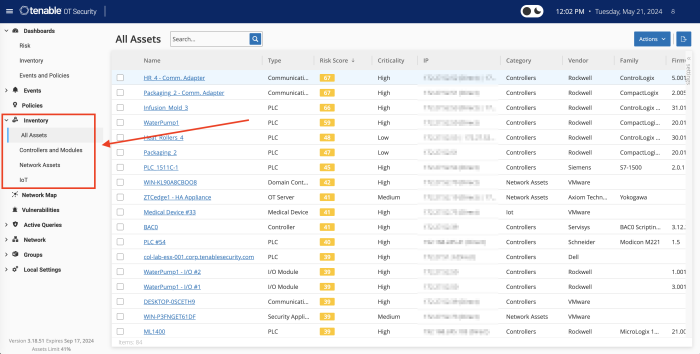
Identification of IoT assets is accomplished with Tenable OT Security. Native communication protocols are used to query both Information Technology (IT) and Operational Technology (OT) devices in your Industrial Control Systems (ICS) environment in order to identify all of the activities and actions occurring across your network. All the assets in the network appear on the Inventory page. The Inventory page includes details about the asset that enables comprehensive asset management as well as monitoring of the status of each asset and its related events. OT Security collects this data using the Network Detection and Active Query capabilities.
The All Assets page shows data for all types of assets. Subsets of assets are shown on separate screens for each of the following asset types: Controllers and Modules, Network Assets, and IoT.
The Vulnerability Handling widget for Tenable OT, located on the compliance dashboard assists in the process of identifying, assessing, reporting, and remediating vulnerabilities. Using this widget, analysts can focus first on assets that have the potential to impact on business operations.
Mean time to Respond (MTTR) is a critical key performance indicator (KPI). A shorter MTTR indicates a more efficient incident resolution process. Minimising downtime and disruptions is crucial for maintaining productivity and service availability. From a Vulnerability Management perspective, OT security personnel can utilise the MTTR for each vulnerability severity within scope, track improvements, and measure SLAs and progress over time. Key items displayed are severity results, high risk assets and MTTR/SLA.
For more information on using Tenable OT Security, reference the documentation for your organisation's version here: Getting Started with Tenable OT Security.