Identity Management and Access Control
Identity and access control are fundamental concepts within information security and system management. Identity refers to the digital representation of a person, device, or entity accessing a system or network. Examples include usernames, email addresses, and digital certificates. Access control is the process of regulating and restricting access to resources or services based on the identity of users or devices. Access control ensures that only authorised users, processes, or systems can access certain resources or perform specific tasks.
Concepts within identity and access control include identity management which is the process and technologies used to create, manage, and authenticate identities throughout the identity lifecycle. Access control typically includes mechanisms such as authentication, authorization, and auditing. These mechanisms verify the identity of users, determine what resources are available to authorised users, and monitor access for security and compliance purposes.Identity and access control work together to ensure that the correct individual or systems have the appropriate access to resources, while safeguarding against unauthorised access and potential security breaches. These concepts are crucial for maintaining the confidentiality, integrity, and availability of information within the organisation's network.
In addition to the Articles previously listed, the following DORA Articles are related to Identity Management and Access Control efforts:
-
Article 9.4(c), Establish to that end a set of policies, procedures and controls that address access rights and ensure a sound administration thereof
-
Article 9.4(d), Implement policies and protocols for strong authentication mechanisms, based on relevant standards and dedicated control systems, and protection measures of cryptographic keys whereby data is encrypted based on results of approved data classification and ICT risk assessment processes
-
Article 10.3, Financial entities shall devote sufficient resources and capabilities to monitor user activity
In this section the following Tenable products will be highlighted:
-
Tenable Identity Exposure
-
Tenable Security Center
-
Tenable Vulnerability Management
-
Tenable Cloud Security
Tenable Identity Exposure provides various methods to access the information collected through the Indicators of Exposure (IoE) and Indicators of Attack (IoA) panes. Tenable Vulnerability Management provides the ability to use the Explore Findings through the use of dashboards and reports.
To begin taking control of the organisation’s Identity Management, every account within the environment must be enumerated. The level of access for each account must also be determined. All accounts must be uniquely identified and assigned to particular entities, such as users and applications.
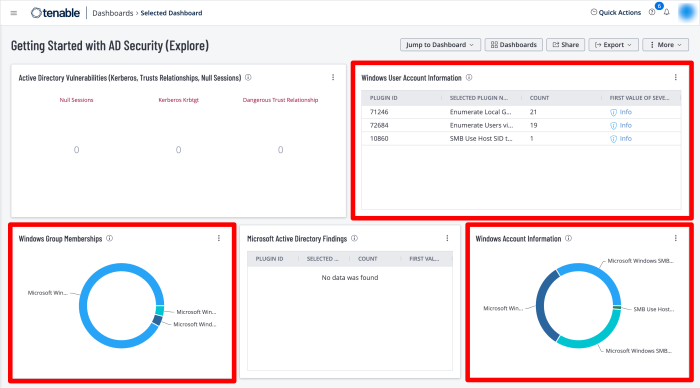
The Getting Started with AD Security dashboard in Tenable Vulnerability Management contains widgets to enumerate user accounts.
The Cyber Security Framework (CSF), developed by the National Institute of Standards and Technology, and the CIS Critical Security Controls, developed by the Center for Internet Security, are both globally applied standards. Therefore, organisations can also reference widgets such as the CSF - Account and Group Information widget located in the CIS Control 4/5: Secure Configurations & Group Memberships dashboard in Tenable Security Center, which leverages plugins that enumerate Windows account information.
Operating Systems and applications are often distributed with service and default accounts that are either not password-protected or have a default password that is well known. Tenable Nessus and Tenable Identity Exposure help identify these accounts, enabling organisations to review and disable any unnecessary accounts to reduce the attack surface. Organisations can leverage the following Nessus plugins to enumerate service and default accounts:
-
Plugin Family: Default Unix Accounts – This plugin family contains over 170 Nessus plugins that check for the existence of default accounts/passwords on a number of devices. In addition, there are many plugins that check for simple passwords such as “0000”, “1234”, and more commonly identified password combinations for “root” or administrator accounts.
-
171959 Windows Enumerate Accounts – This plugin enumerates all Windows Accounts
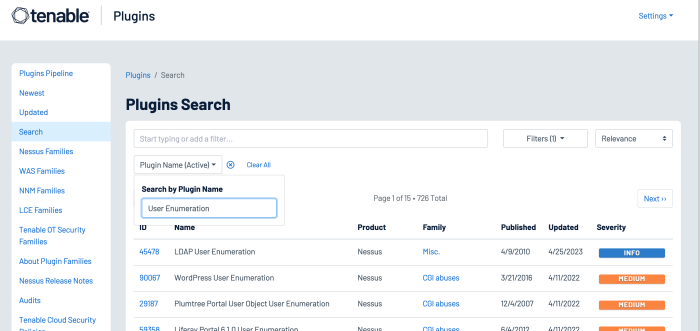
Several hundred plugins can be identified by searching for “Default Account” from the Nessus Plugins Search page using the Enable Default Logins filter. Nessus default account plugins are available for Databases, Web Servers, SCADA devices, Unix/Linux devices, Cisco devices and more. Many of the plugins are associated with the Default Unix Account Nessus family, however, many are in other families as well.
In addition, Tenable Identity Exposure provides the ability to determine if a default administrator account was recently used in the environment, as shown in the image below:
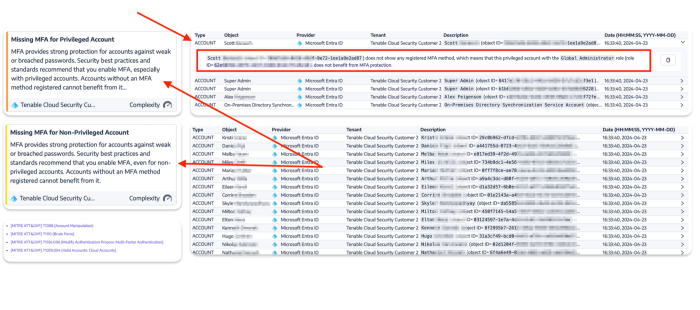
Tenable Identity Exposure is also able to determine if items such as MFA are being used. In this example, a privileged account with a Global Administrators role does not have a registered MFA method. The user account and detailed information on the vulnerability are present to assist organisations mitigate the identified concerns.
Depending on the threat level of the misconfiguration, the Indicator of Exposure (IOE) will rise in a different category: Critical – High – Medium – Low. This provides the context required to minimise distractions. Organisations are able to effectively investigate incidents, hunt for threats, and manage and prioritise security challenges that pose the greatest threats.
For more information on Tenable Identity Exposure review the documentation located here.
For more detailed information review the Identity and Access Management Cyber Exposure guide.
Additionally, the Identity and Access Control section of the NIS 2 Directive Cyber Exposure Study can be referenced.
Cloud Provider Misconfigurations
Several hundred plugins can be identified by searching for “Default Account” from the Nessus Plugins Search page using the Enable Default Logins filter. Nessus default account plugins are available for Databases, Web Servers, SCADA devices, Unix/Linux devices, Cisco devices and more. Many of the plugins are associated with the Default Unix Account Nessus family, however, many are in other families as well.
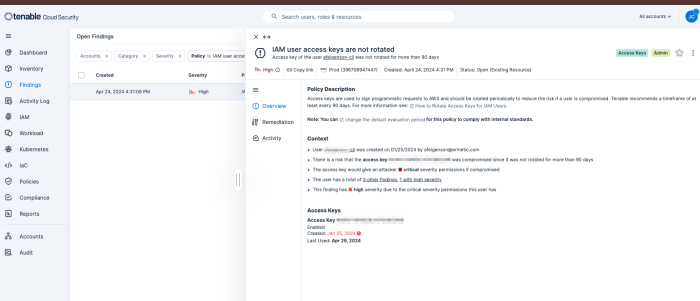
Details within each policy violation contain an overview, policy violation details, and policy remediation strategies, as well as defining any impacted resources. Policies are used to identify misconfigurations and vulnerabilities present on cloud resources. Tenable Cloud Security has built-in policies for cloud and IaC resources that define the compliance standards for your cloud and IaC infrastructure. Related policies are combined within a policy group. A policy can support multiple benchmarks. Therefore, a policy group includes all the benchmarks supported by the policies in the group.
A full list of Tenable Cloud Security policies is available online here.
Additionally, Tenable Cloud Security automates threat detection and remediation to eliminate noise enabling your team to focus on what matters most. In-depth investigation, monitoring, and reporting on suspicious or unusual activity across AWS, Azure, and GCP is simplified by creating a behavioural baseline for each identity. By continuously assessing and prioritising risk across human and service identities, network configuration, data, and compute resources Tenable Cloud Security proactively reduces the attack surface and blast radius in case of a breach.
The organisation's entire multi-cloud environment is continuously analysed, evaluating risk factors including effective exposure, misconfigurations, excessive and risky privileges, leaked secrets and vulnerabilities. Unusual data access, privilege escalation and other identity-related threats, as well as changes in login settings, unusual reconnaissance, and unauthorised use or theft of access keys, can all be detected. Tenable analyses cloud provider logs to reveal the identity behind each activity and affected accounts, resources, and services.
More information on getting started with Tenable Cloud Security is available in the Tenable Cloud Security User Guide.