Mitigation
Verify Mitigation
Frequently, vulnerabilities targeted for remediation are never fully remediated. While security teams are responsible for detecting and prioritizing vulnerabilities, patching the vulnerabilities is the responsibility of IT staff and developers who speak a different language and have different goals. Integration of Risk-Based Vulnerability Management (RBVM) solutions with ITSM and ticketing systems is of the utmost importance to automate workflows, correlate vulnerabilities with patches, and verify that all instances of a vulnerability have been patched or remediated by a compensating control. Use authenticated scans to ensure that patches are activated, not just installed, since some patches require a system reboot or a registry change.
Track Progress
Tenable assigns a vulnerability state to all vulnerabilities detected on the network: New, Active, Fixed, and Resurfaced. The Vulnerability state Fixed is assigned when the vulnerability was present on a host, but is no longer present. This vulnerability state can be used to track vulnerabilities that were previously New or Active and have now been remediated. Vulnerabilities that have been marked as Fixed are no longer displayed in the active vulnerability dashboards and workbenches but can be found when using the Vulnerability State filter for Fixed. If a vulnerability was previously marked as Fixed and returns to the host, that vulnerability will be marked as Resurfaced and will re-appear in the active vulnerability dashboards and workbenches.
Measure Performance
Successful teams take time to reflect on their performance, and security is no different. This requires developing key metrics to measure and communicate how operational controls are working (or not working) and benchmarking data to compare performance across internal groups or externally against peers. Generate metrics that cover foundational cyber hygiene practices, such as assessment capabilities, remediation speed, and overall risk reduction.
| Widget Description | Widget Image |
|---|---|
|
The Vulnerability Overview by CVE Widget, which can be found in the Defending Against Ransomware (ACT) Tenable Vulnerability Management Dashboard and Tenable Vulnerability Management widget library, displays a count of the following:
|
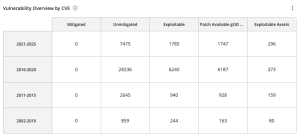
|
|
The Fixed Vulnerability State filter displays vulnerability findings that have been fixed and can be combined with other filters, such as the CVE filter, in workbench searches and custom widgets. While Tenable provides dashboard templates, such the Defending Against Ransomware (ACT) Tenable Vulnerability Management Dashboard, users have the ability to create custom widgets for their specific requirements. The log4shell - Log4j Concerns pre-configured widget uses the FixedVulnerability State filter with the CVE filter to display fixed Log4j and Java vulnerabilities. |
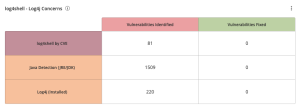
|
|
The Fixed Patches by Vulnerability Publication Date widget, which can be found in the Defending Against Ransomware (ACT) Tenable Vulnerability Management Dashboard and Tenable Vulnerability Management widget library, displays counts of fixed vulnerabilities grouped by the patch publication date. This matrix assists organizations with mapping mitigation progress and presents data to determine whether organizational SLAs are being met. Each cell contains a count of fixed vulnerabilities grouped by Microsoft Windows systems, *nix systems, Network devices, and vulnerabilities specified in the DHS BOD 22-01 and Tenable's 2021 Threat Landscape Retrospective with a patches published 0-30, 31-60, 61-90, and more than 90 days ago. |
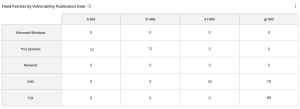
|