Vulnerabilities
Vulnerabilities are exposures that can be exploited and can be in the form of a software defect, configuration error, or basic human error. The impact of exploiting a vulnerability depends on the value of the targeted asset. Risk Based Vulnerability Management (RBVM) is a process that reduces vulnerabilities across the attack surface by prioritizing remediation based on the risks posed to the organization. Unlike legacy vulnerability management, RBVM goes beyond discovering vulnerabilities by providing threat context and insight into potential business impact.
Identification
As information about new vulnerabilities is discovered and released into the public domain, Tenable Research designs programs to detect them. Each plugin contains vulnerability information, a simplified set of remediation actions, and the algorithm to test for the presence of the security issue. Tenable Research has published over 165,000 plugins, which can be found on the Tenable Plugins Page.
Prioritize Vulnerability Scanning
Identifying vulnerabilities and configuration errors in the infrastructure is the first step to determine susceptibility to ransomware attacks. Prioritize vulnerability scanning by targeting critical assets first. Leverage tactical scan templates to ensure scans are configured appropriately for the assets’ function, such as:
- Critical business servers
- Critical infrastructure devices
- Managed servers
- User / Desktop
- Off-site (VPN, Managed)
- Production servers
- Development servers
- Test systems
- Web servers
- Operational Technology devices
Organizations often define a “gold standard” for various system deployments, based on the CIS benchmarks. However, day-to-day operational requirements tend to cause a drift from this standard over time, creating weak links. Technical staff can use the Tenable Vulnerability Management Cyber Exposure Platform to analyze endpoint operating systems, software configurations, web applications, and Operational Technology (OT) devices. Organizations can verify that established configuration policies are followed by including Tenable CIS Audits in policy compliance vulnerability scans. Use Tenable Vulnerability Management to configure vulnerability, compliance, and web application scans. Assessing the configuration of systems within the network is a vital step in risk-based vulnerability management (RBVM).
Determine Current State
| The Vulnerability and Missing Patch Heat Map widget, which can be found in the Defending Against Ransomware (ACT) Tenable Vulnerability Management Dashboard and Tenable Vulnerability Management widget library, uses the Vulnerability Published date filter cross mapped with the Patch Published date filter to show the organization's current vulnerability state. The Patch Published date indicates when a vendor published a patch for a vulnerability, while the Vulnerability Published date indicates when the vulnerability was first published (for example, the date the CVE was published to NVD). The widget uses a heat map approach, with the upper left corner containing the vulnerabilities and patches that have been published in the last 30 days. Moving lower and to the right in the matrix, the colors change from yellow to red as the risk levels increase. Tenable recommends remediating vulnerabilities shown in the lower right cells and working towards the upper left cells, since the lower right cells represent missing patches associated with vulnerabilities that have been known to the public for a longer period of time. Vulnerabilities displayed in this table are based on the plugins in the Local Security Checks plugin families for each Operating System, which will only run in an authenticated scan. Tenable provides a comprehensive collection of plugins for a large variety of operating systems to check for security issues, which are enumerated on the Tenable Plugins Page. | 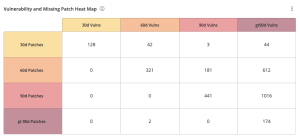
|