Attack Path
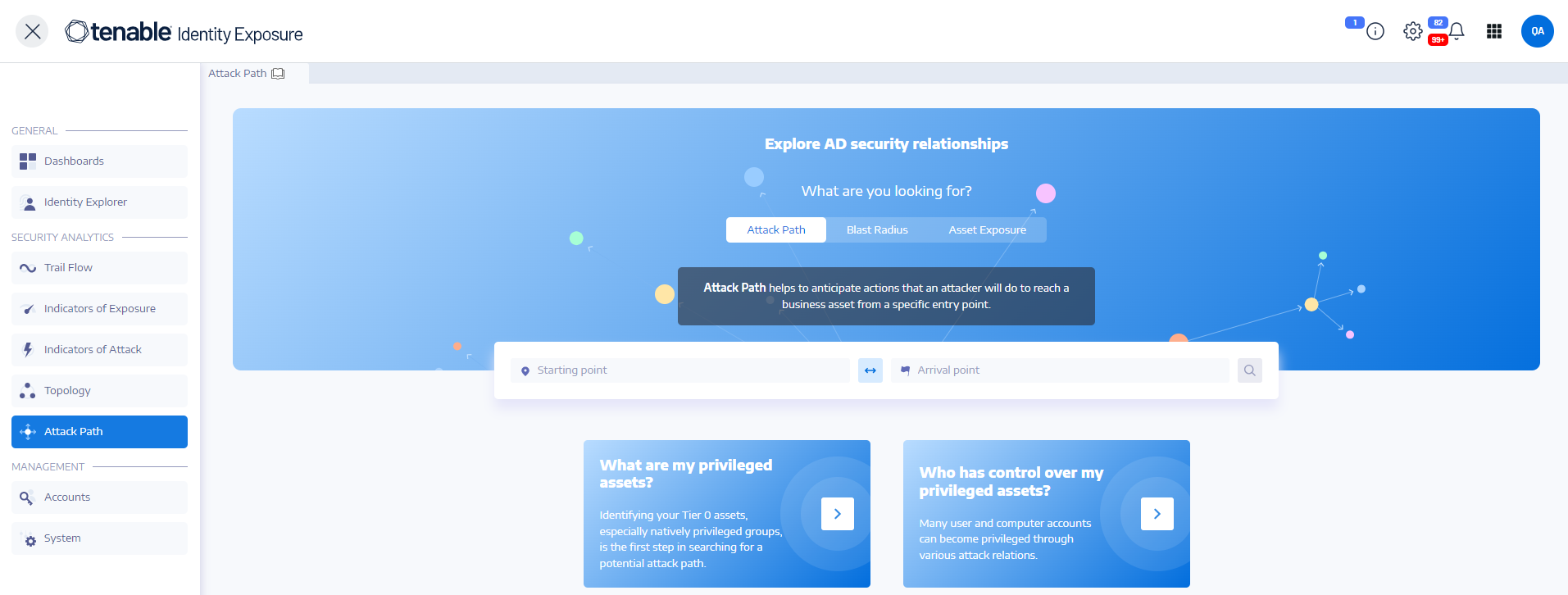
Tenable Identity Exposure offers several ways to visualize the potential vulnerability of a business asset through graphical representations.
-
Attack Path: Shows the possible paths that an attacker can take to compromise an asset from an entry point.
-
Blast Radius: Shows the possible lateral movements into the Active Directory from any asset.
-
Asset Exposure: Shows all paths that can potentially take control of an asset.
Understanding the attack path enables you to identify necessary mitigation steps to block attackers from exploiting vulnerabilities. This might involve patching systems, hardening configurations, implementing stronger access controls, or raising awareness among users.
Benefits of using Attack Path in Tenable Identity Exposure:
-
Proactive security: It helps anticipate and address potential attack vectors before they are exploited.
-
Prioritization: It guides towards focusing security efforts on the most critical vulnerabilities and attack paths.
-
Visualization: It provides a clear and easy-to-understand representation of complex security relationships within your AD.
-
Communication: It facilitates communication of security risks to stakeholders by offering visual evidence of potential attack scenarios.
Attack Path
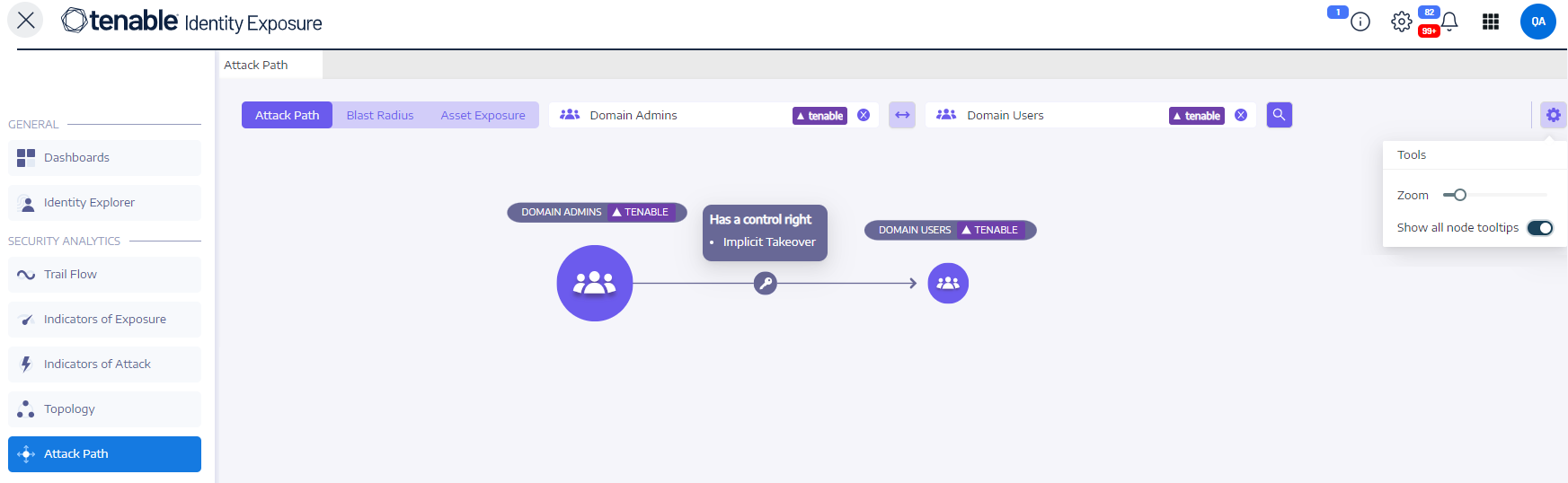
You specify the starting point, which could be any asset in your AD (e.g., a user account, computer, group). You define the arrival point, representing the asset the attacker ultimately aims to compromise (e.g., a domain controller, sensitive data server).
To display the Attack Path:
-
In Tenable Identity Exposure, click Attack Path on the sidebar menu.
The Attack Path pane appears.
-
In the banner, click Attack Path.
-
In the Starting point box, type the asset at the entry point.
-
In the Arrival point box, type the asset at the end of the path.
-
Click the
 icon.
icon.Tenable Identity Exposure displays the attack path between the two assets.
-
Optionally, you can click on the
 icon to do the following:
icon to do the following:-
Click the Zoom slider to adjust the magnification of the graphics.
-
Click the Show all node tooltips toggle to display information about the assets.
-
To pin an attack path:
-
Click on a node on the attack path that you want to highlight.
Tenable Identity Exposure pins that attack path on the screen.
-
To unpin the attack path, click the
 icon or another node on a different attack path.
icon or another node on a different attack path.
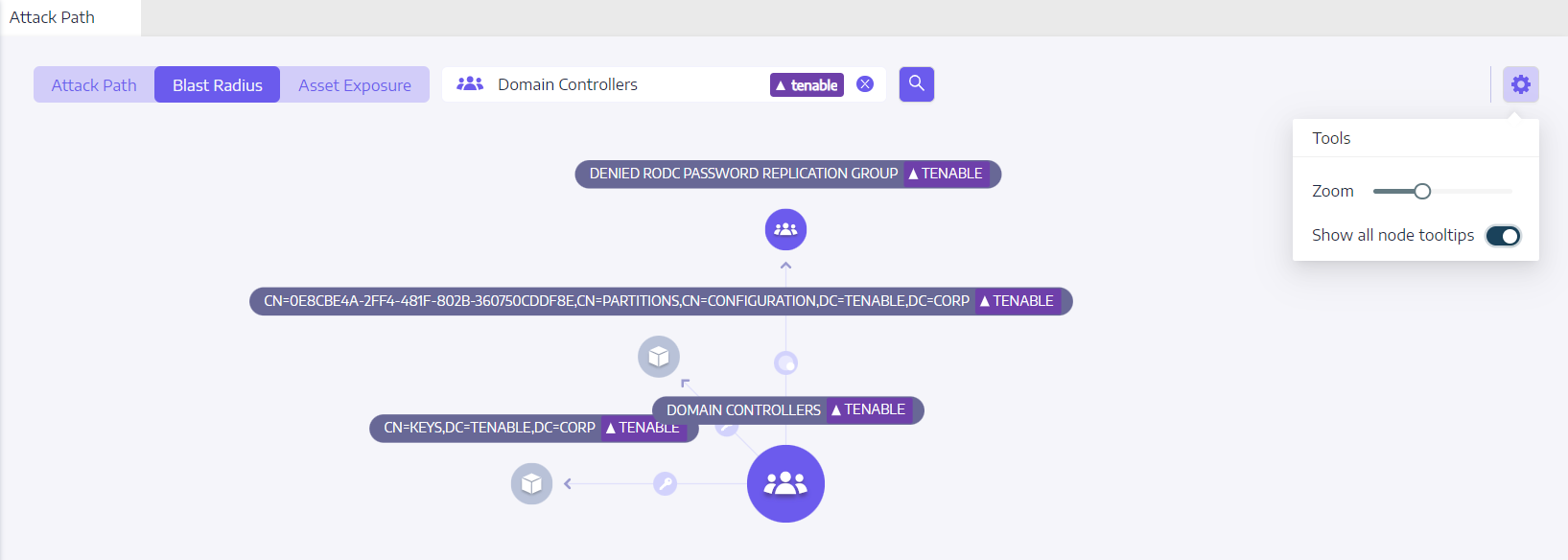
Blast Radius
Tenable Identity Exposure displays a graphical representation of the potential attack path, highlighting the connections between assets. Each connection represents a potential vulnerability or misconfiguration that the attacker could exploit to move laterally within your AD. You can zoom in and out to gain a better understanding of the path's details.
To display the Blast Radius:
-
In Tenable Identity Exposure, click Attack Path on the sidebar menu.
The Attack Path pane appears.
-
In the banner, click Blast Radius.
-
In the Search for an object box, type the name of an asset.
-
Click the
 icon.
icon.Tenable Identity Exposure displays the lateral connections radiating from that asset:
-
Click on the icons on the arrows between the assets to display the relations between them.
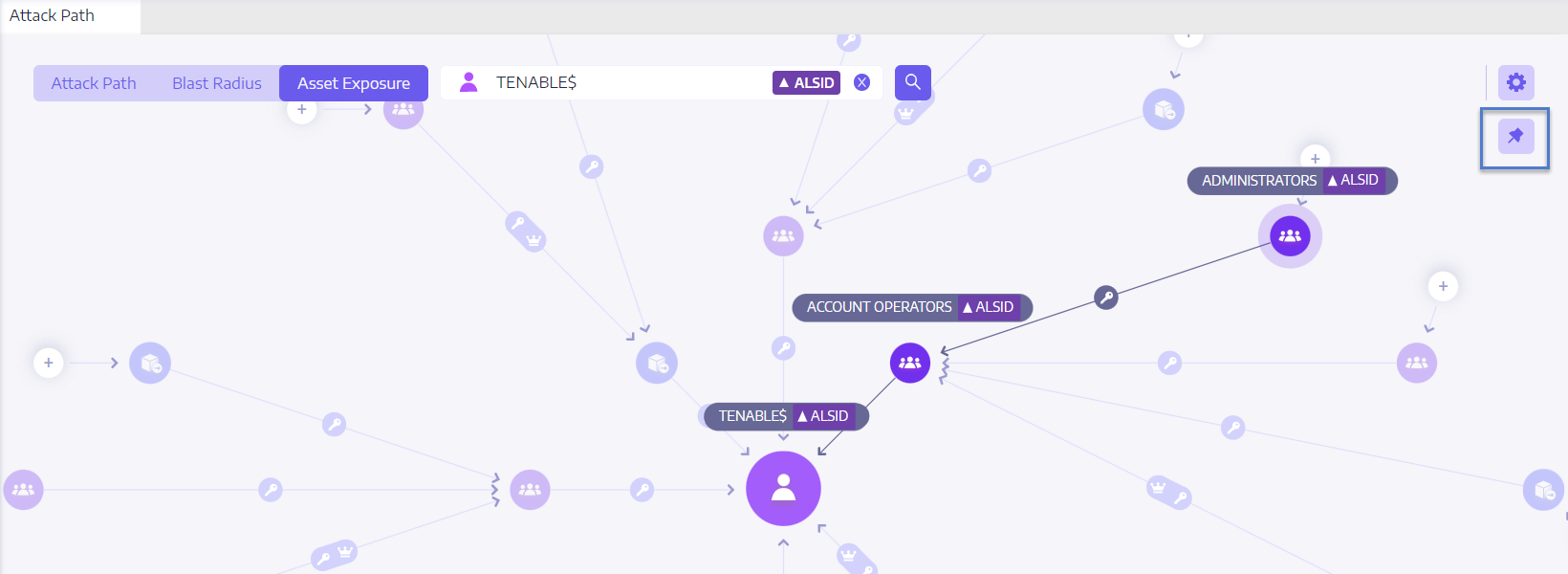
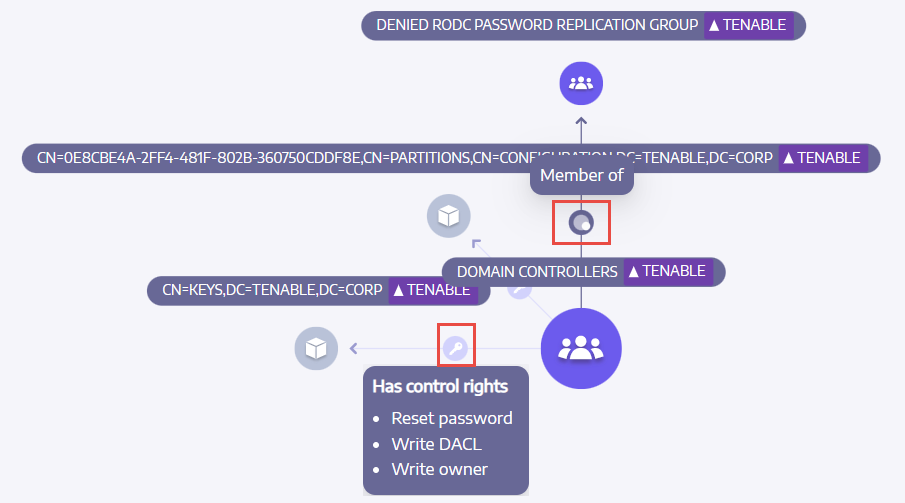
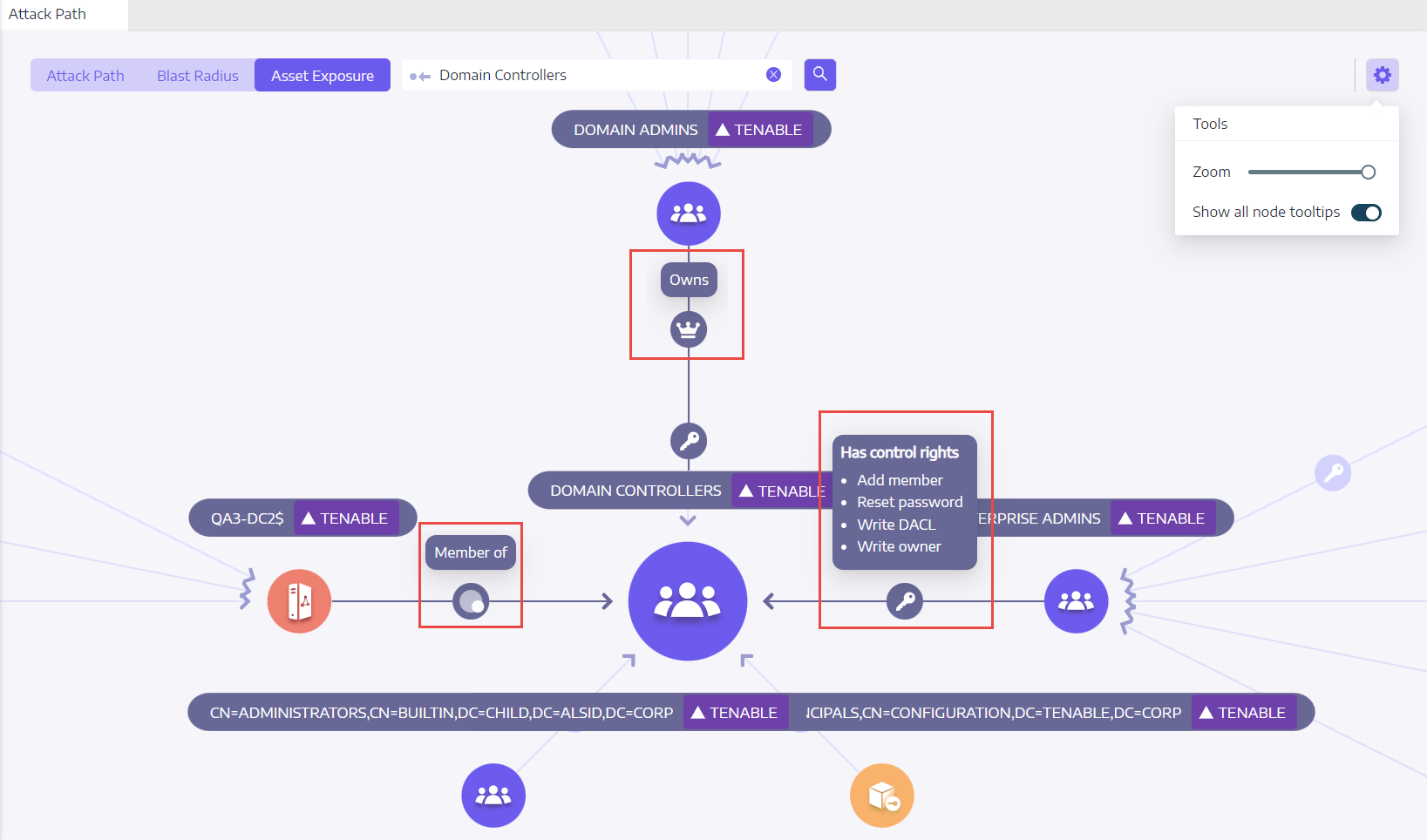
Asset Exposure
Each step in the attack path is associated with a risk score, indicating the severity of the vulnerability. This helps you prioritize which paths pose the most significant threat and require immediate attention. You can also click on individual connection points for more details about the specific vulnerability or misconfiguration involved.
To display the Asset Exposure:
-
In Tenable Identity Exposure, click Attack Path on the sidebar menu.
The Attack Path pane appears.
-
In the banner, click Asset Exposure.
-
In the Search for an object box, type the name of an asset.
-
Click the
 icon.
icon.Tenable Identity Exposure displays the paths leading to the asset and the relations between the assets.
-
Click on the icons on the arrows between the assets to display the relations between them.
See also