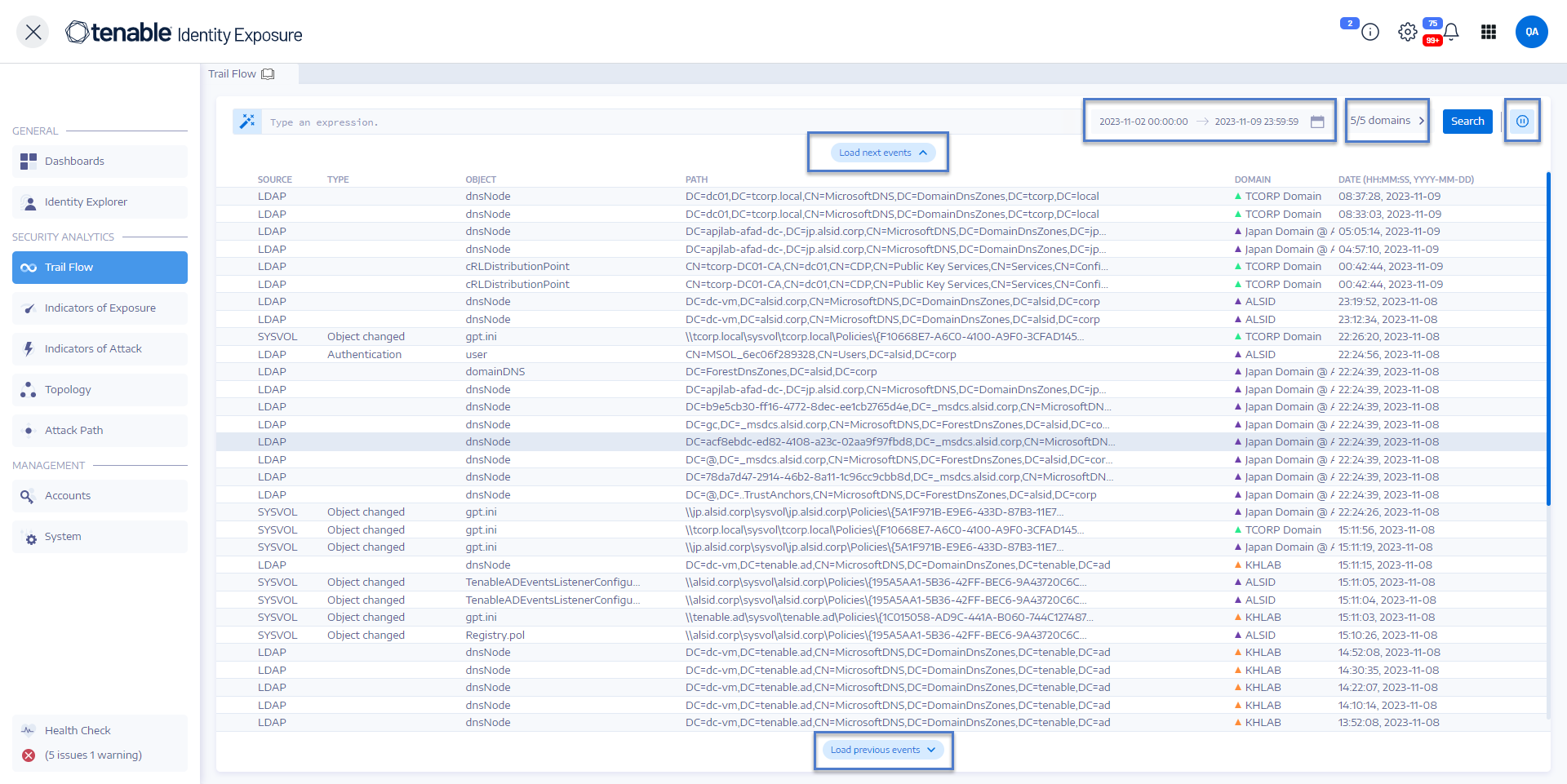
Trail Flow
Tenable Identity Exposure's Trail Flow shows the real-time monitoring and analysis of events affecting your AD infrastructure. It allows you to identify critical vulnerabilities and their recommended courses of remediation.
Using the Trail Flow page, you can go back in time and load previous events or search for specific events. You can also use its search box at the top of the page to search for threats and detect malicious patterns.
The Trail Flow tracks the following events:
-
User and group changes: Includes the creation, deletion, and modification of accounts and groups.
-
Permission alterations: Encompasses modifications to access controls on objects such as files, folders, and printers.
-
System configuration adjustments: Involves changes to Group Policy Objects (GPOs) and other critical settings.
-
Suspicious activities: Encompasses unauthorized attempts, privilege escalations, and other events that raise red flags.
Tenable Identity Exposure offers these capabilities to leverage the Trail Flow data:
-
Searchable and filterable: Easy navigation through the event stream by using keywords or specific criteria, enabling focused attention on pertinent activities while minimizing extraneous noise.
-
Detailed event information: Each event entry furnishes exhaustive details, encompassing the affected object, the user responsible for the change, the protocol utilized, and associated Indicators of Exposure (IoEs).
-
Visualized relationships: The ability to illustrate the relationships between events, illuminating how seemingly unrelated activities may contribute to a broader attack campaign.
To access the Trail Flow:
-
In Tenable Identity Exposure, click Trail Flow in the navigation bar on the left.
The Trail Flow page opens with a list of events. For more information, see Trail Flow Table.
To select a timeframe:
-
At the top of the Trail Flow page, click on the calendar box.
-
Select a start date and an end date.
-
Click Search.
Tenable Identity Exposure updates the Trail Flow table with the selected timeframe.
To select a domain:
-
At the top of the Trail Flow page, click n/n domain >.
The Forest and Domains pane opens.
-
Select the forests and domains.
-
Click Filter on selection.
Tenable Identity Exposure updates the Trail Flow table with information for the selected forest and domain.
To view an event:
-
In the Trail Flow table, click on a line that contains the event you want to explore.
The Event Details pane appears. For more information, see Event Details.
To pause and restart the Trail Flow:
-
Do one of the following:
-
Click on the
 icon to pause the Trail Flow.
icon to pause the Trail Flow.Pausing the Trail Flow stops the automatic vertical scrolling of the most recent events while the analysis continues to run in the background and allows you to run a search on events.
-
Click on the
 icon to restart the Trail Flow.
icon to restart the Trail Flow.
-
To load the next or previous events:
-
In the Trail Flow page, do one of the following:
-
Click Load next events
-
Click Load previous events
-