Install the Tenable App for Microsoft Sentinel
Required User Role: Basic User
Note: The Tenable integration with Microsoft Sentinel works with a Basic User if that user is assigned Can View permissions on the assets they are to export, along with Can Use permissions on tags the assets are assigned. Without the Can Use tag permissions, the assets return undefined or the integration fails to export vulnerabilities if a tag filter is used. For more information on Tenable Vulnerability Management permissions and user roles, refer to Permissions in the Tenable Developer Portal.
The Tenable App for Microsoft Sentinel combines Tenable's Cyber Exposure insights with Sentinel's collection, detection, and investigation capabilities. This integration supports Tenable Vulnerability Management and exports asset and vulnerability data from Tenable Vulnerability Management directly to Microsoft Sentinel.
Microsoft Sentinel is a scalable, cloud-native, security information event management (SIEM), and security orchestration automated response (SOAR) solution. For more information about Microsoft Sentinel, see the Microsoft documentation.
Before you begin:
- You must have a Logs Analytics Workspace with Microsoft Sentinel enabled in your Azure subscription.
- For assistance with launching Microsoft Sentinel, see the Microsoft Sentinel quick start guide.
-
Resource Group (This requires Microsoft Sentinel Contributor Role at Subscription Level.)
Caution:Tenable recommends you deploy the latest version of the Tenable App (v3.1.0) in a new Microsoft Sentinel workspace rather than upgrading the existing one. Version 3.1.0 supports the Log Ingestion API, which requires the use of Data Collection Rules (DCR) and Data Collection Endpoints (DCE). Since table names are tied to specific DCRs, the tables used in the previous app version cannot be reused.
-
In the Azure portal, navigate to Resource Group and select your resource group.
-
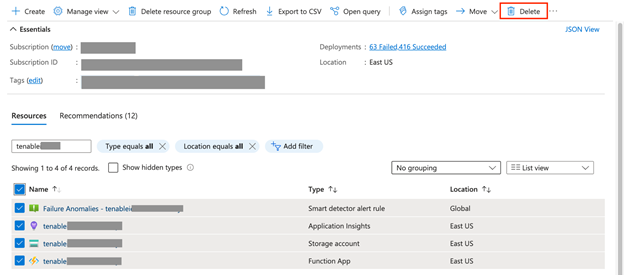
In the Resources section search for the currently running Tenable function app name and select all the resources for that function app.
-
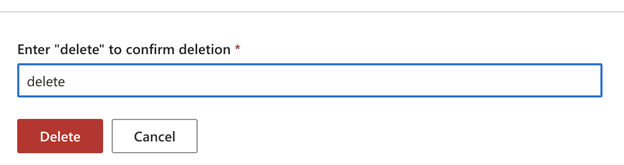
After clicking on the delete button, the portal will ask for confirmation. Write delete in the textbox and click on the delete button.
Note: For more information, refer to the Microsoft documentation.
-
In the Azure portal, navigate to Resource Group and select your resource group.
-
In the left menu, click Access control (IAM).
-
Click Add.
-
Select Add role assignment.
-
Select Microsoft Sentinel Contributor.
-
Click Next.
-
In Assign access to, select either User, Group, or Service Principal.
-
Click Add members.
-
Type the name of the application you created, and select it.
-
Click Review + assign.
A new window appears.
-
In the new window, again click Review + assign.
Note: For more information, refer to the Microsoft documentation.
-
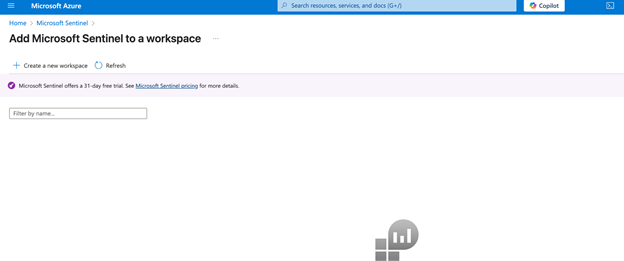
Navigate to Microsoft Sentinel within the Microsoft Azure Portal and click Create Microsoft Sentinel.
The workspace homepage appears:
-
Add a workspace for Microsoft Sentinel. Click Create a new workspace.
-
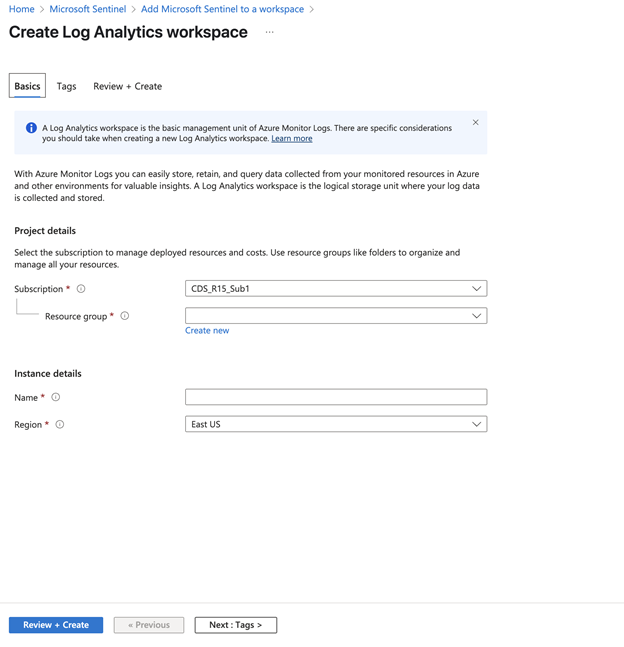
To create the Log Analytics workspace, you must first create a new Resource Group. Click Create new under Resource Group Connector.
-
Input a Name for the instance detail and select the appropriate Azure Region from the drop-down menu.
Click Review + Create.
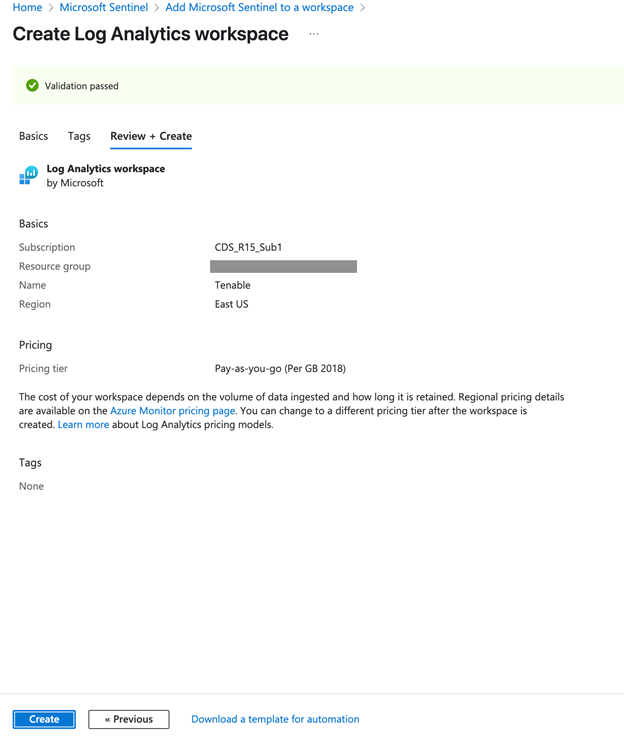
The settings are finalized and the page updates:
-
Click Create.
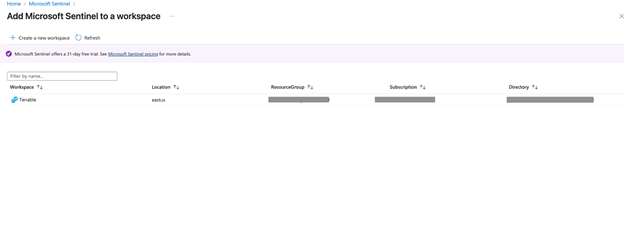
The workspace homepage appears with your new Microsoft Sentinel workspace:
The Log Analytics Workplace for Microsoft Sentinel has been created.
-
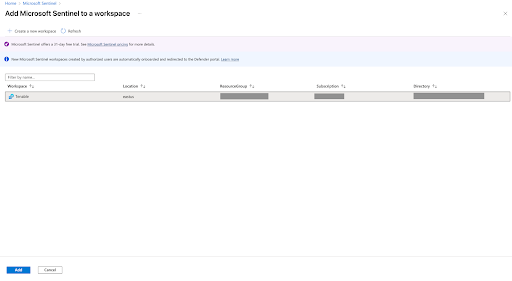
In the workspace, click Add to add Microsoft Sentinel to a workspace.
Note: Navigate to Log Analytics workspace > Network Isolation and ensure that the two Virtual network access configuration settings (required to accept data ingestion and queries from public networks not connected through a Private Link Scope) are set to Yes.
Caution:Tenable recommends you deploy the latest version of the Tenable App (v3.1.0) in a new Microsoft Sentinel workspace rather than upgrading the existing one. Version 3.1.0 supports the Log Ingestion API, which requires the use of Data Collection Rules (DCR) and Data Collection Endpoints (DCE). Since table names are tied to specific DCRs, the tables used in the previous app version cannot be reused. Follow the steps in the Delete the existing Function App and associated resources section before proceeding.
-
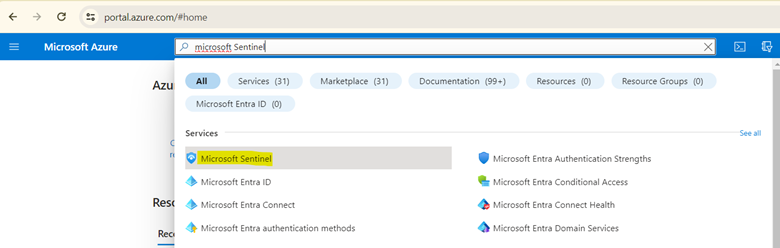
Login to the Microsoft Azure portal and search for "Microsoft Sentinel" in the search box.
-
Select Microsoft Sentinel.
-
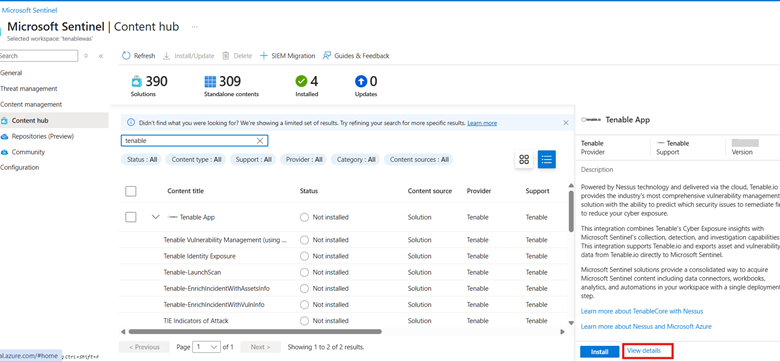
Select your workspace and navigate to Content Hub.
-
In the search box, type "Tenable App."
-
Select Tenable App.
-
Click View Details.
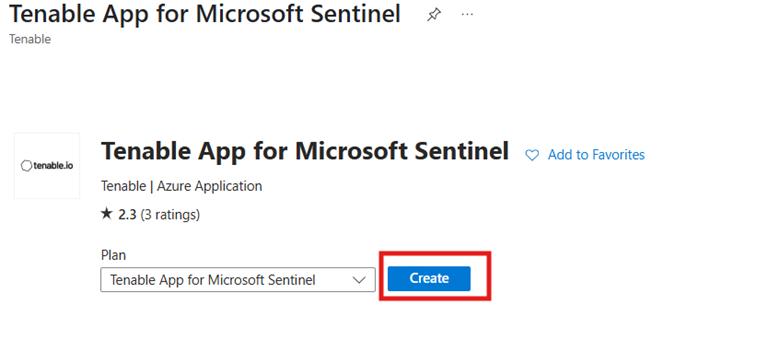
A confirmation screen appears:
-
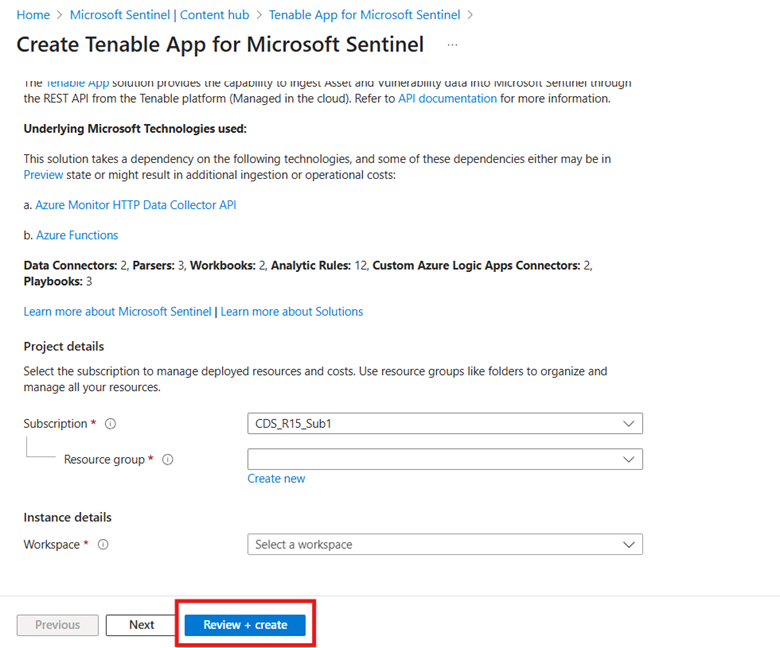
Fill in the details of the Workspace and Resource group.
-
Click Review + Create.
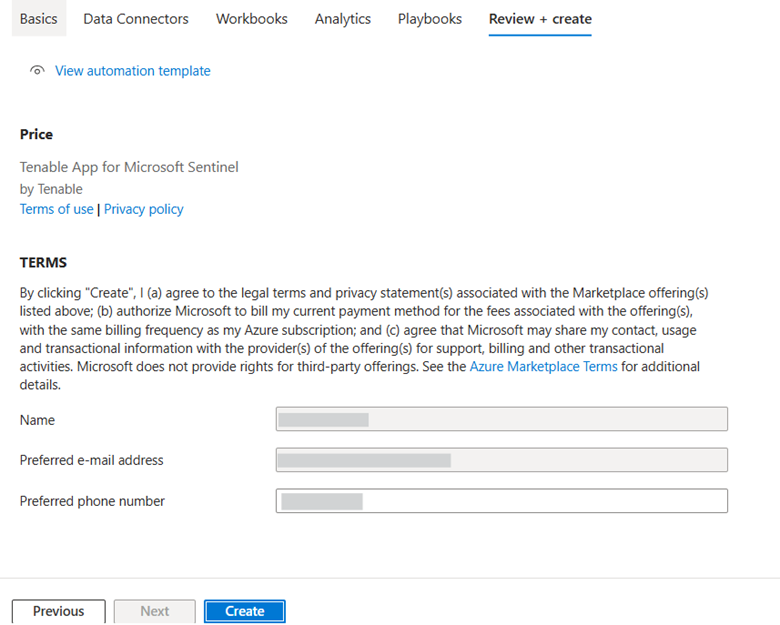
-
Click Create.
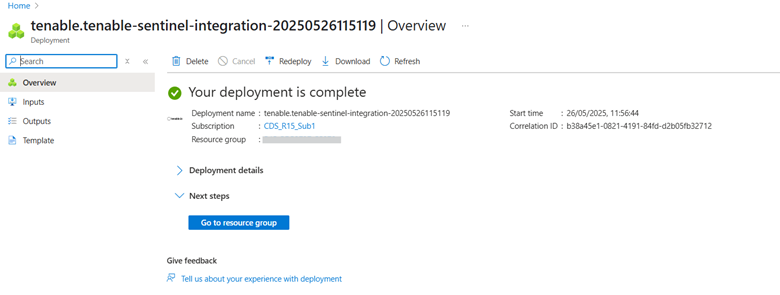
The integration installs the solution into the Microsoft Sentinel workspace.
-
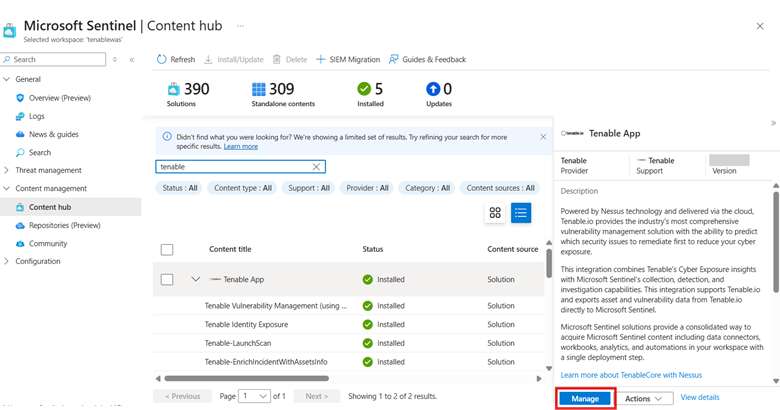
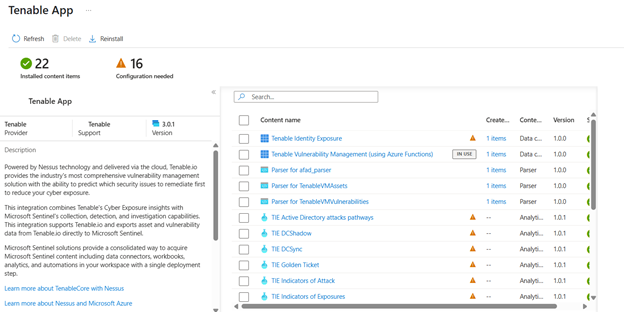
In Microsoft Sentinel (the workspace you just created) > Content Hub, search for the solution that you have installed and click Manage.
The list of components associated with this integration appears:
What to do next (do one of the following):