Tenable Vulnerability Management 2026 Release Notes
Tip: You can subscribe to receive alerts for Tenable documentation updates.
These release notes are listed in reverse chronological order.
February 18, 2026
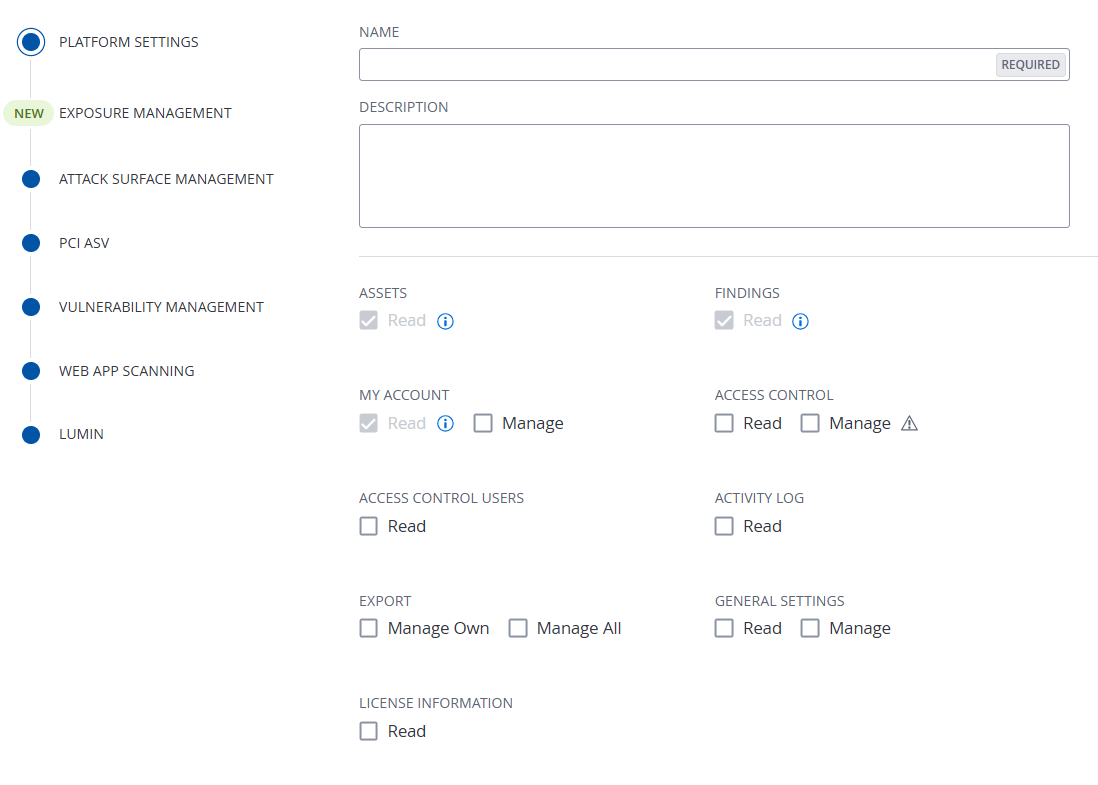
In preparation for upcoming custom role updates within Tenable Vulnerability Management, Tenable has relocated the Export > Manage Own and Manage All options from the Vulnerability Management Settings section to the Platform Settings section of the custom role creation workflow.
For more information, see Create a Custom Role in the Tenable Vulnerability Management User Guide.
February 2, 2026
Tenable has standardized the naming conventions for asset classification across Tenable Exposure Management (EM) and Tenable Vulnerability Management (VM). Previously referred to as Device Profiling, this feature is now universally titled Asset Classification. This alignment ensures that risk drivers and asset properties are labeled identically regardless of which platform or view you are using, providing a seamless experience for cross-platform analysis.
Key Terminology Updates:
-
Asset Category: Replaces Device Class (VM) and Device Profile (EM).
-
Asset Function: Replaces Device Subclasses (VM) and Device Functionality (EM).
-
Categorization Confidence/Drivers: Replaces all Profile Confidence/Drivers labels.
-
Unified Value Display: Data values are now standardized across the platform. For example, inconsistent labels like "Workload device" vs. "VM or Workload" have been unified into a single, clear naming convention based on the Tenable standard.
For more information, see the Asset Categorization Quick Reference Guide.
January 27, 2026
Tenable has added two Plugin Download Concurrency global settings to Tenable Vulnerability Management: one for linked Tenable Nessus scanners and one for linked Tenable Agents.
When enabled, this setting determines how many linked Tenable Nessus scanners or Tenable Agents can download plugins from Tenable Vulnerability Management at the same time. This can help with managing network bandwidth and preventing resource exhaustion due to large-scale updates.
For more information, see Manage Linked Scanners and Modify Global Agent Settings in the Tenable Vulnerability Management User Guide.
Tenable has added the CPU Utilization Controls setting to agent profiles in Tenable Vulnerability Management.
When enabled, this setting allows you to configure the maximum percentage of a host's CPU that a Tenable Agent can use when installed on Windows or Linux hosts. This allows you to manage the performance impact of agent scans on critical host systems.
For more information, see Manage Agent Profiles in the Tenable Vulnerability Management User Guide.
January 23, 2026
Tenable is excited to announce the addition of the Finding Enriched Attributes stream to Tenable Data Stream. This new stream provides a centralized, push-based mechanism to export all manual risk adjustments — including vulnerability recasts, risk acceptances, and host audit result changes — directly to your AWS S3 bucket in JSON format. This feature automates the delivery of the override data currently managed within the Vulnerability Management Recast user interface, allowing you to integrate your manual risk decisions with external reporting and analysis tools.
What's New?
This enhancement expands the metadata available within the Tenable Data Stream ecosystem, capturing modifications that override automated Tenable findings:
-
Manual Risk Management (Vulnerability & WAS) — Continuously export details for findings that have been recast (severity changed) or accepted (risk accepted), including the source system and the original versus current risk levels.
-
Host Audit Overrides — Track when the results of a host audit have been manually changed or accepted (for example, changing a result to PASSED, FAILED, or WARNING), ensuring compliance visibility for configuration audits.
-
Full Contextual Audit Log — Each entry includes the specific Rule ID, the user-provided comment or justification, the modification target (RISK or RESULT), and expiration timestamps for temporary rules.
Manual Risk Management (Vulnerability & WAS) — Continuously export details for findings that have been Recast (severity changed) or Accepted (risk accepted), including the source system and the original versus current risk levels.
Host Audit Overrides — Track when the results of a Host Audit have been manually changed or accepted (for example, changing a result to PASSED, FAILED, or WARNING), ensuring compliance visibility for configuration audits.
Full Contextual Audit Log — Each entry includes the specific Rule ID, the user-provided comment or justification, the modification target (RISK or RESULT), and expiration timestamps for temporary rules.
For more information, see the following topics in the Tenable Vulnerability Management User Guide:
January 22, 2026
Tenable is excited to announce the Tenable FedRAMP Moderate availability of mobilization services in Tenable Vulnerability Management. Unify teams and streamline remediation workflows by automatically or manually creating bi-directional tickets via Exposure Response initiatives. This capability accelerates response times by synchronizing your security findings with tickets in Jira Cloud or ServiceNow.
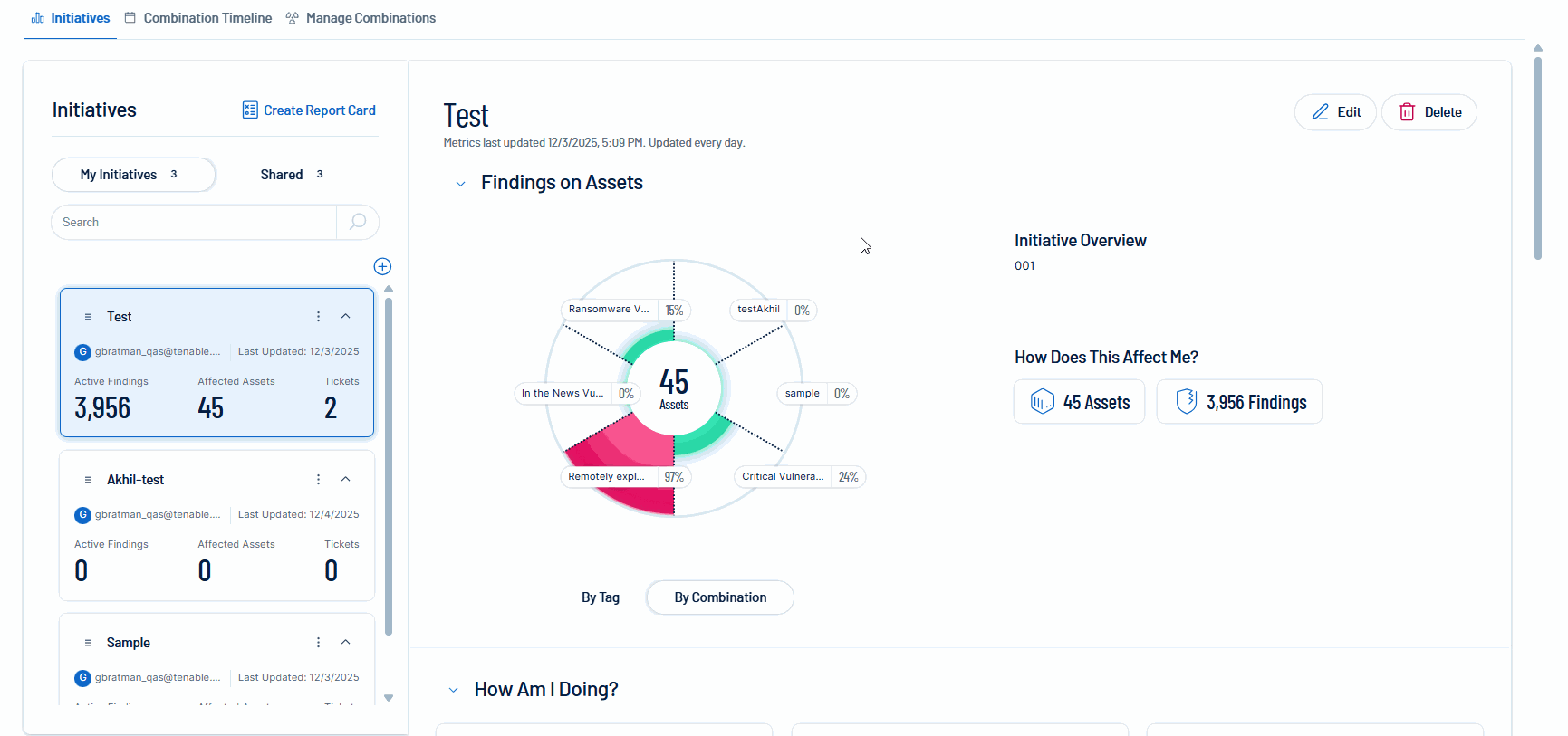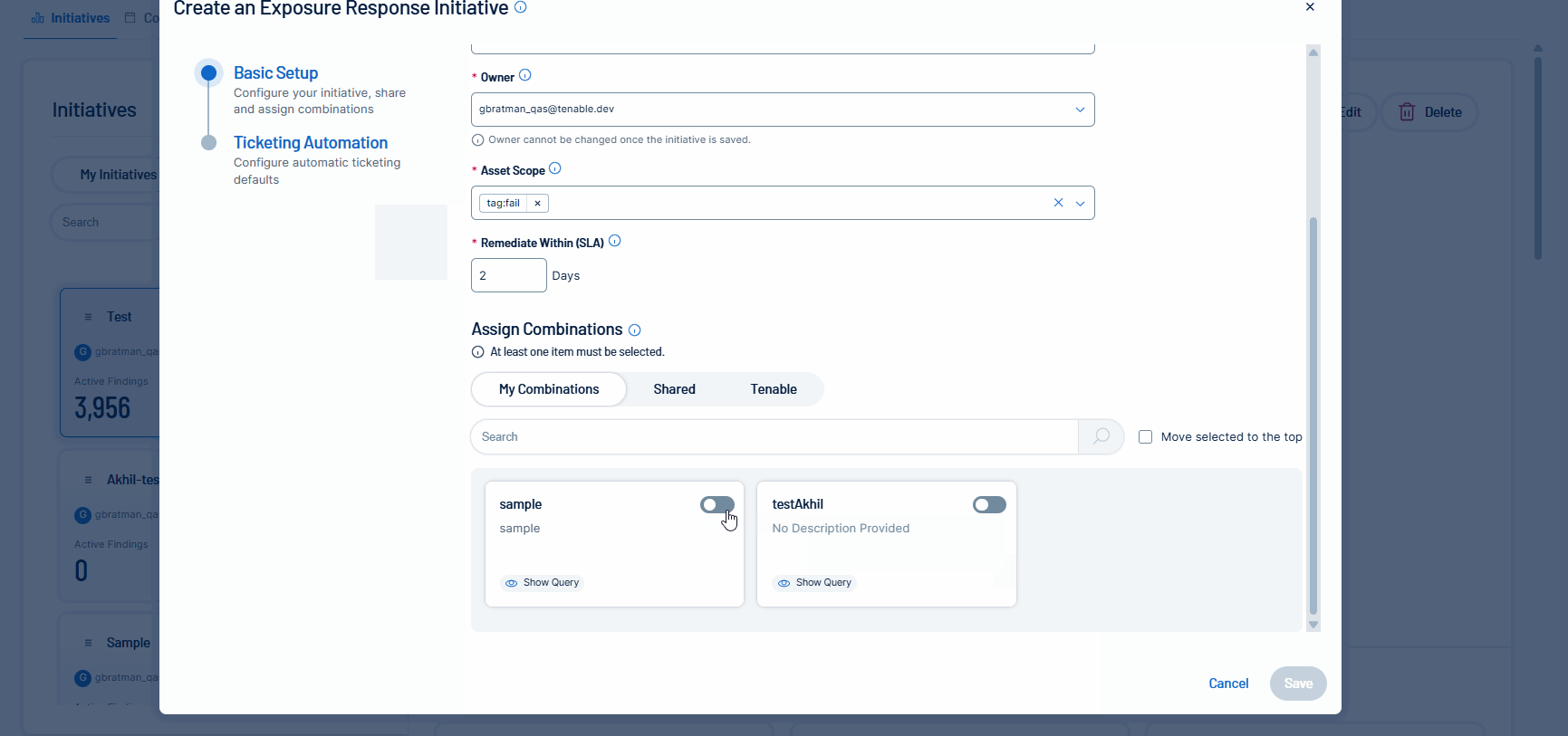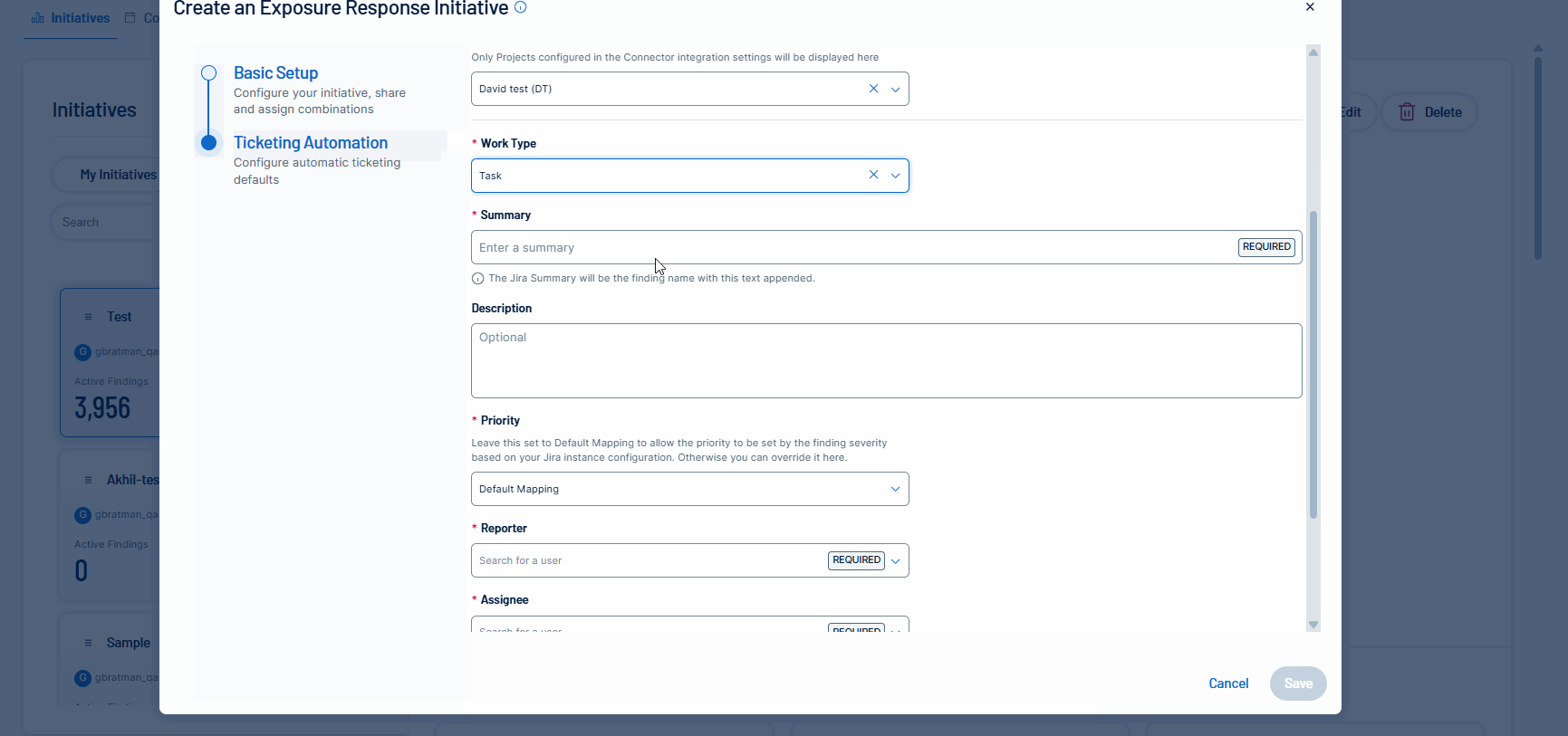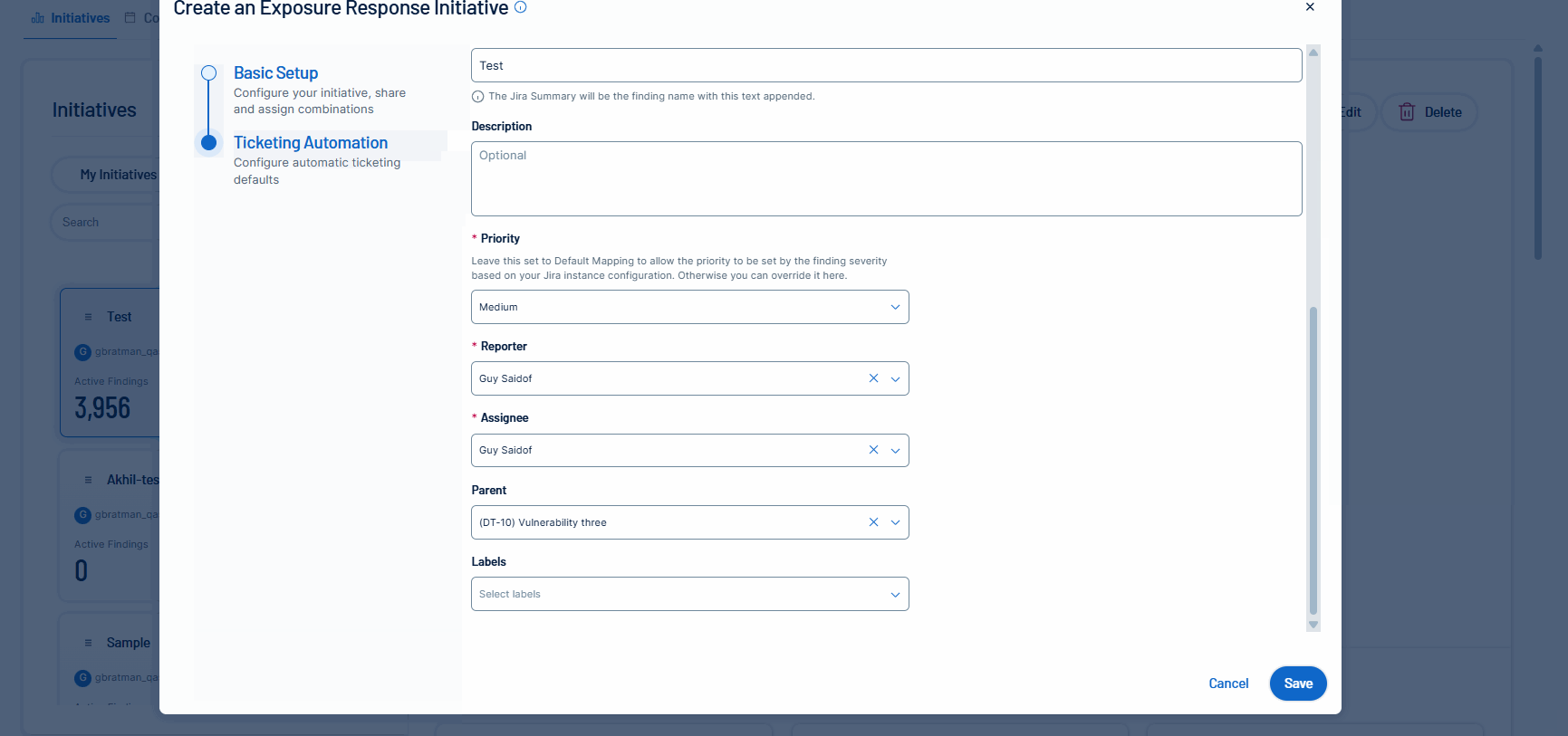
For more information, see:
-
Storylane demo for Tenable Mobilization
-
Create an Initiative in the Tenable Vulnerability Management User Guide
-
Mobilization Quick Reference Guide
January 13, 2026
Tenable has added two Plugin Download Concurrency global settings to Tenable Vulnerability Management: one for linked Tenable Nessus scanners and one for linked Tenable Agents.
When enabled, this setting determines how many linked Tenable Nessus scanners or Tenable Agents can download plugins from Tenable Vulnerability Management at the same time. This can help with managing network bandwidth and preventing resource exhaustion due to large-scale updates.
For more information, see Manage Linked Scanners and Modify Global Agent Settings in the Early Access Tenable Vulnerability Management User Guide.
Tenable has added the CPU Utilization Controls setting to agent profiles in Tenable Vulnerability Management.
When enabled, this setting allows you to configure the maximum percentage of a host's CPU that a Tenable Agent can use when installed on Windows or Linux hosts. This allows you to manage the performance impact of agent scans on critical host systems.
For more information, see Manage Agent Profiles in the Early Access Tenable Vulnerability Management User Guide.