CIS Control 16: Account Monitoring and Control
The focus of this control is to ensure that all accounts are managed in a fashion that promotes clean account hygiene. This misuse or neglect of account maintenance can lead to system compromise.
The CIS states this Control is critical:
“Attackers frequently discover and exploit legitimate but inactive user accounts to impersonate legitimate users, thereby making discovery of attacker behavior difficult for security personnel watchers. Accounts of contractors and employees who have been terminated and accounts formerly set up for Red Team testing (but not deleted afterwards) have often been misused in this way. Additionally, some malicious insiders or former employees have gained access to accounts left behind in a system long after contract expiration, maintaining their access to an organization’s computing system, and sensitive data for unauthorized and sometimes malicious purposes.”
The journey of implementing the CIS Controls continues with practicing good user account hygiene and maintenance. Many systems (operating systems and application systems) may have the ability to set controls and policies on user accounts. The centralized management of these types of accounts can often be neglected or fall out of scope of normal business processes. Organizations are directed to disable any unassociated or dormant accounts. These accounts are often overlooked or set up with a default password, both of which are undesirable for more than a short period of time. For example, if a user contacts the helpdesk to change the password, then it is appropriate for a default password to be set. However, the password should then be changed within minutes, not weeks. Organizations are directed to configure systems to automatically lock workstation sessions after a specified inactivity period. This setting is a common configuration and is set using Group Policy Objects for Windows computers.
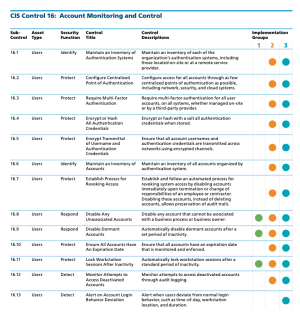
The three specific sub-controls that are part of Implementation Group 1 (IG1) are:
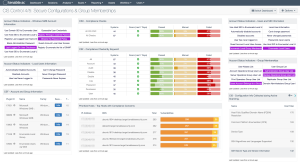
For CIS Control 16, there is a strong connection to CIS Control 4 which speaks to elevated privileges. Control 16 looks at all accounts and how local computer/application policy can be configured to support good account hygiene. Tenable products allow security operations teams to use Tenable Security Center Continuous View to analyze system configurations, many of which set local security policies, e.g., control of screen locking. In addition to several audit checks, there are many plugins that assist in tracking accounts that are unused, passwords that have never been changed, and so forth. Account management is often easily controlled by properly configured systems or centralized authentication. Tenable Security Center quickly identifies the systems with an issue and can help the organization create a plan of action to remediate or mitigate the risk associated with account management. The CIS Control 4/5 Secure Configurations and Group Memberships Dashboard provides useful information to assist organizations with this control.
For more information about the CIS Control 4/5 dashboard, see CIS Control 4/5: Secure Configurations & Group Memberships.
NIST also provides helpful information directly related to this CIS Control under the NIST Special Publication 800-53 (Rev. 4) - AC-2 ACCOUNT MANAGEMENT.