AWS Connector with Key-based Authentication
The following is not supported in Tenable FedRAMP Moderate environments. For more information, see the Tenable FedRAMP Product Offering.
The Amazon Web Services (AWS) Connector provides real-time visibility and inventory of EC2 assets in AWS accounts.
You can create an AWS connector to discover AWS assets and import them to Tenable Vulnerability Management. Assets discovered through the connectors do not count against the license until and unless the asset is scanned for vulnerabilities.
Key-based Authentication
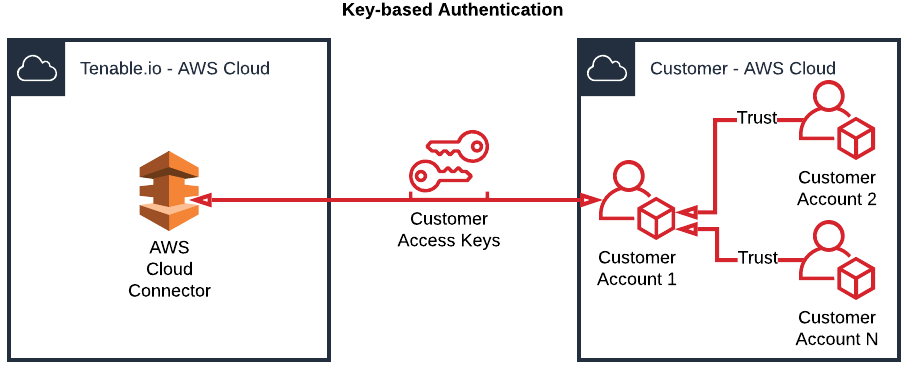
Tenable Vulnerability Management AWS connectors support key-based authentication that uses an IAM user with permissions and a secret key and access key. In this scenario, the Tenable Vulnerability Management AWS connector authenticates with your primary AWS account via a secret key and an access key. Additionally, you can manually configure secondary linked AWS accounts with trust relationships to your primary AWS account., as shown in the diagram below.
For more information about other AWS authentication options, see Amazon Web Services Connector.
To fully configure AWS key-based authentication with Tenable Vulnerability Management:
- In AWS, configure your primary AWS account to support key-based authentication for your connectors, as described in Configure AWS for Key-based Authentication.
- (Optional) In AWS, manually configure linked AWS accounts, as described in Configure Linked AWS Accounts (Key-based).
- In Tenable Vulnerability Management, create your AWS connector, as described in Create an AWS Connector with Key-based Authentication.