Key Component 4: Malware Protection
The focus of this key component is Malware Protection. Malicious software, or “malware” is software that is designed to cause harm to information systems and is one of the biggest challenges organizations face in maintaining cyber hygiene. Malware exploits weaknesses and vulnerabilities to make software or hardware perform actions not originally intended. Malware protection is one of the five key technical controls in the Cyber Essentials. This key component applies to all the following in scope devices: Boundary Firewalls, Desktop Computers, Laptops, Routers, Servers, Iaas, PaaS, and SaaS devices.
The goal is to ensure that all devices are protected from malware (viruses, worms, trojans, ransomware, spyware) which can lead to data breaches, system outages, and financial loss. The Cyber Essentials requires organizations to implement at least one of the following methods to protect against malware:
-
Application Allow Listing
-
Only approved applications are allowed to run
-
-
Anti-Malware Software
-
Traditional antivirus/antimalware tools (such as Microsoft Defender), configured to conduct regular scans, and set applications to receive automatic updates and security patches
-
-
Sandboxing
-
Running applications in isolated environments.
-
Devices that can not support malware protection (such as some IoT devices) must be segregated from other systems using appropriate controls such as firewalls and/or network isolation.
Malware Protection Assessment Questions Directly Addressed
Questions in this section apply to: servers, desktop computers, laptops, tablets, thin clients,
mobile phones, IaaS, PaaS and SaaS. Within this section, information is provided which addresses the following questions.
A8.1. Are all of your desktop computers, laptops, tablets and mobile phones protected from malware
A8.2.Is anti-malware software set to update in line with the vendor’s guidelines and prevent malware from running on detection
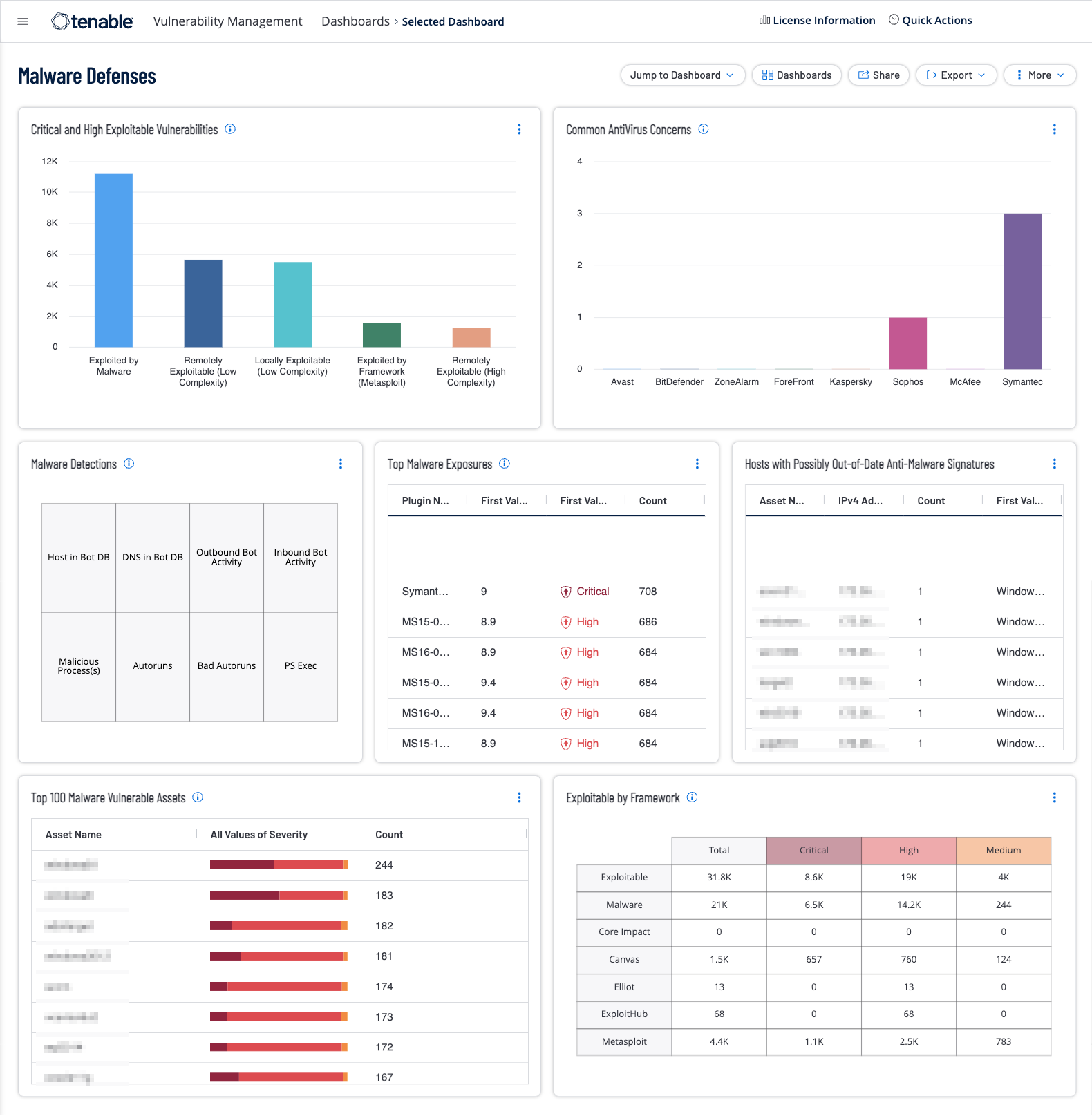
Tenable Security Center and Tenable Vulnerability Management enables organizations to evaluate vulnerability data gathered from multiple active and passive scanners distributed across the enterprise. The Tenable Vulnerability Management Malware Defenses dashboard provides the necessary context to understand which assets in the organization are vulnerable to malware exploitation.
More information can be found by referring to the Malware Defences Cyber Exposure Study.
Malware threats are one of the most common and damaging cyber threats. The primary objective is to defend against threats, such as malware, viruses, ransomware, and others. Section 4 ensures you have an active protection in place for protection. Active protection helps prevent business disruptions from downtime, and costly recovery efforts. These dashboard highlight concerns that have been identified in the environment to help organisations address malware concerns.
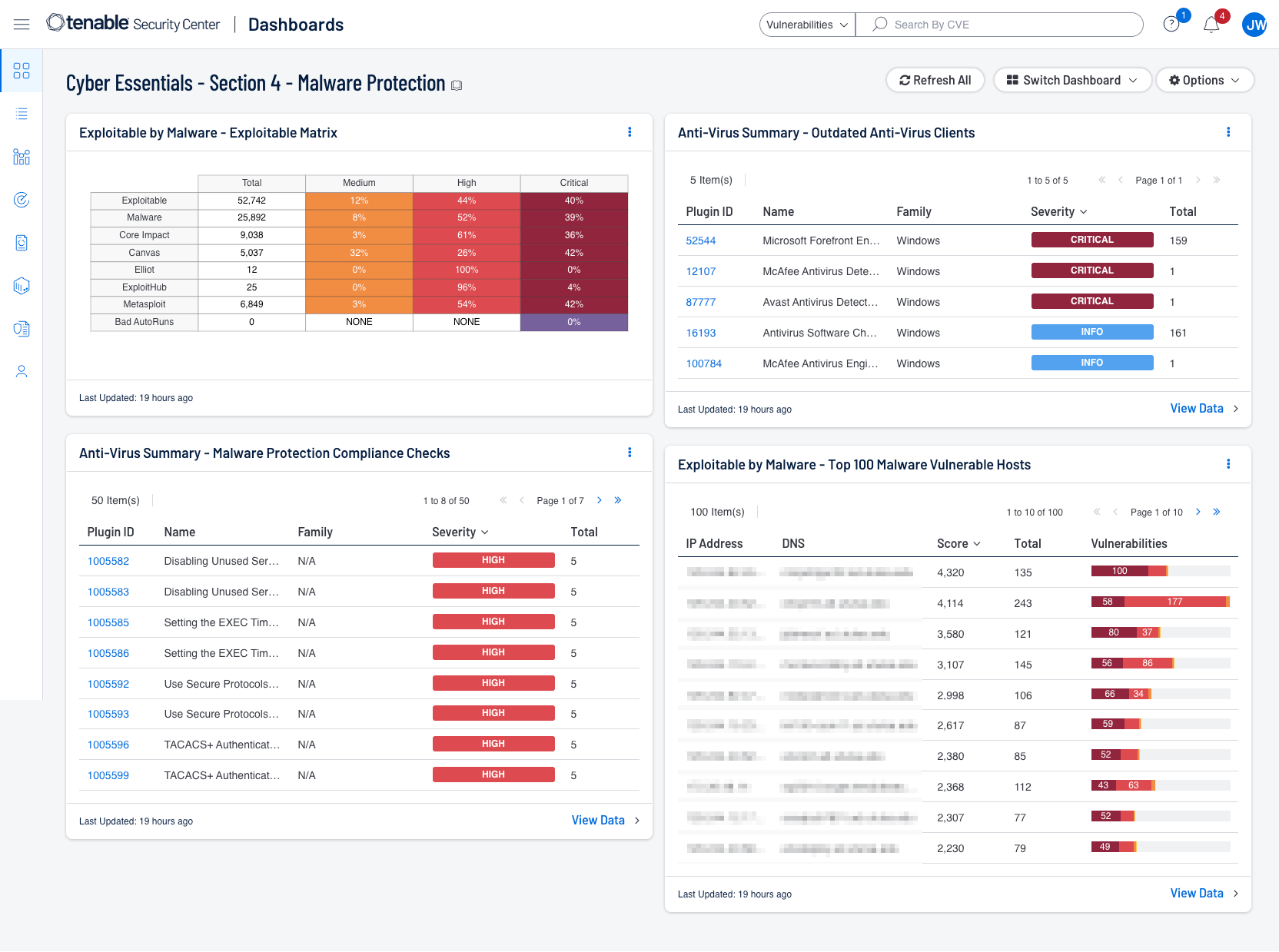
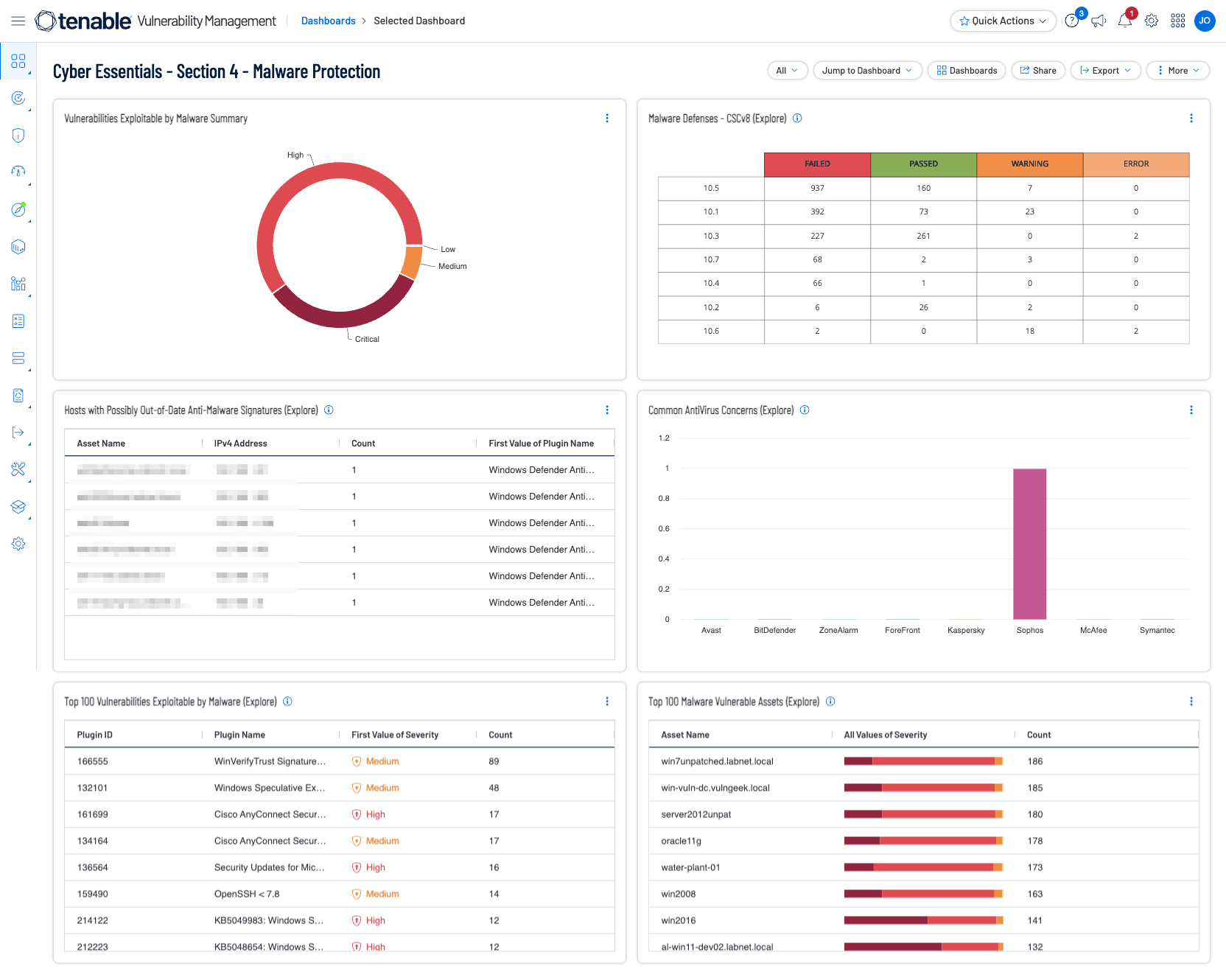
Tenable has provided a Cyber Essentials Dashboard and Report for Tenable Security Center and Tenable Vulnerability Management for this Key Component. Those dashboards and reports can be found here by using the term “Cyber Essentials” as a search query:
Security Center Dashboards and Reports
Vulnerability Management Dashboards and Reports
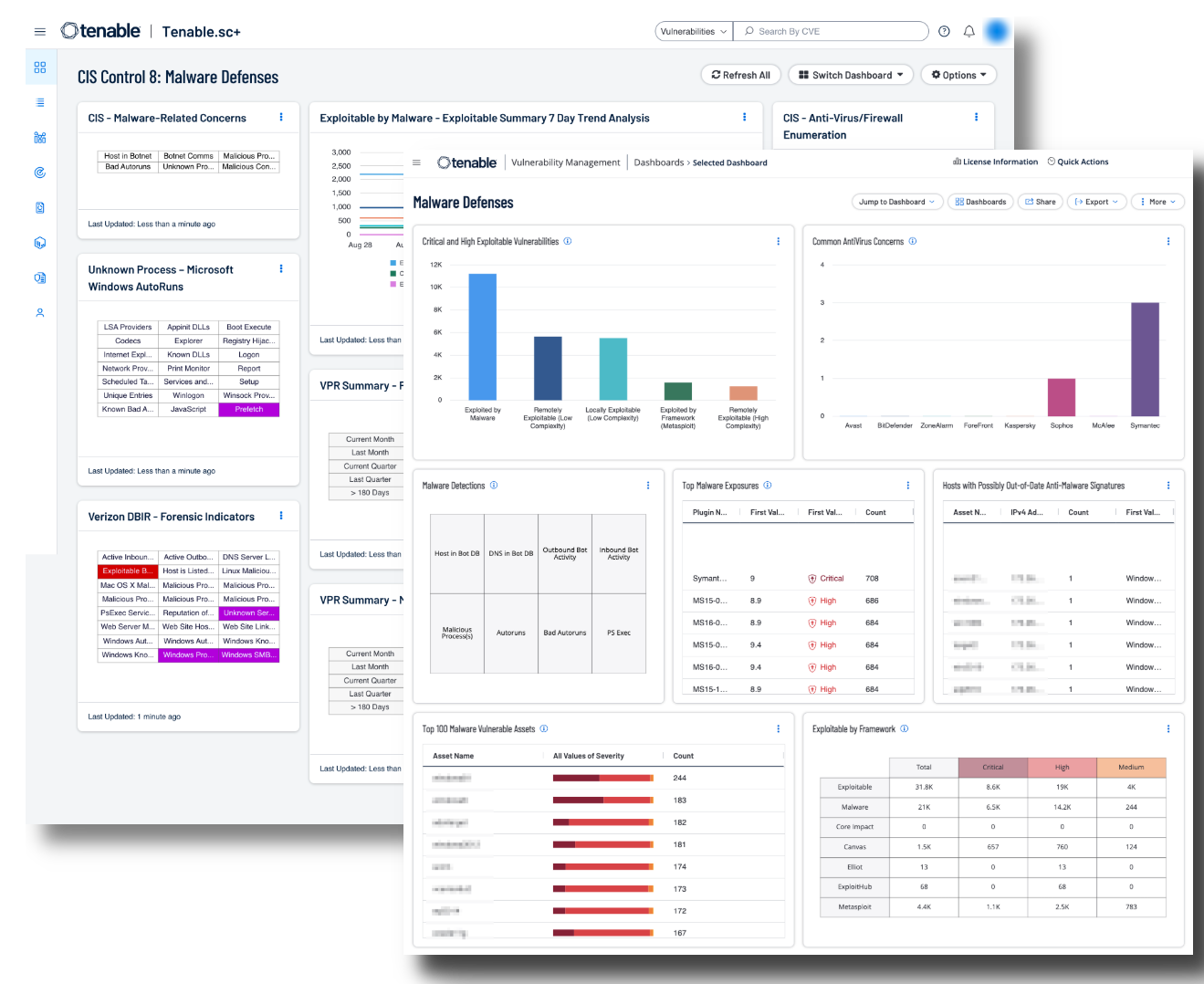
Shown below are screenshots of this section's dashboards for Security Center and Vulnerability Management.
Additionally, a critical part of keeping the network secure is enabling a continuous monitoring strategy and monitoring of all possible network endpoints. Information gathered from Tenable products provides organizations with a complete picture of malicious activity, malware infections, and compromised hosts. Tenable provides Malware Defense dashboards for Tenable SC (based off CIS Control 8) and Tenable Vulnerability Management which provide a detailed view of potential malware, suspicious processes, and malicious activity, enabling security analysts to easily identify malware activity on hosts. Data collected provides valuable information from devices and services on suspicious files, unauthorised logins, malicious websites, requests, and more. Systems are scanned for malicious backdoors, botnet activity, potential malware, and unknown processes. Indicators provide information on systems communicating with botnets or other malicious hosts.
Tenable Cloud
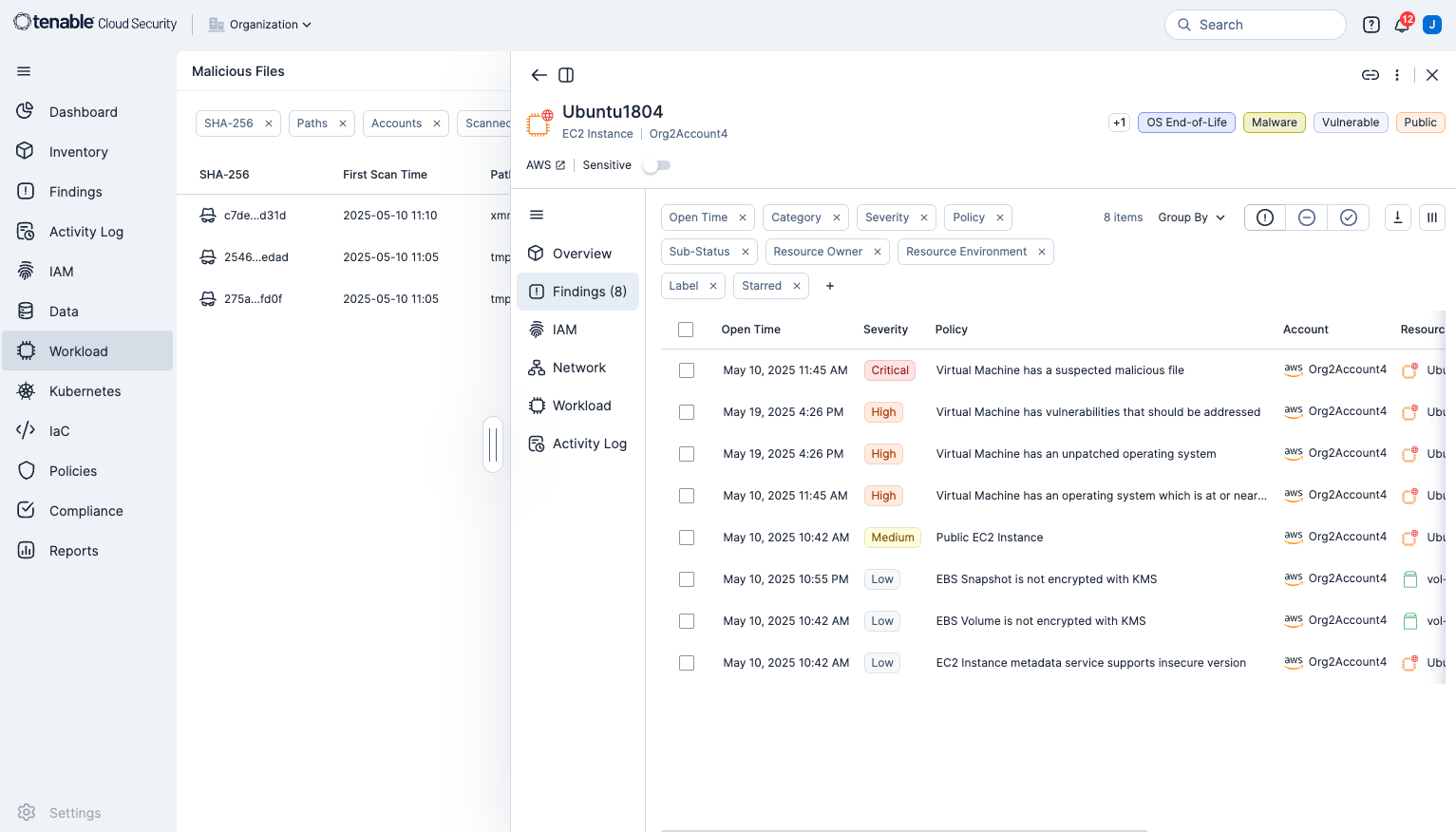
Tenable Cloud Security has unique Malware Scanning features that allow for the detection of potentially malicious files in your workloads. Tenable Cloud Security scans workloads for malicious executable files (such as a DLL), then generates a SHA-256 hash for each file. The hash is sent to a known reputation service, if the hash is known metadata about the file, combined with a reputation verdict from all supported malware engines is received.
This data is analysed and used to calculate a proprietary view on the level of maliciousness of the file. If the file is determined to exceed the threshold in terms of the number and type of vendors who deem the file to be malicious, a record of threat is created. This record is then available in the Tenable Cloud Security Console as a malicious file and a finding.
To view scan results:
-
In the Tenable Cloud Security Console, click Workload Protection > Malicious Files. The Malicious Files page displays all potentially malicious files identified by Tenable. See Malicious Files Column Data for more information.
-
Filter the table to narrow the scope of the visible data. Use the column picker on the top right of the table to choose which columns to display.
-
To mark a file as trusted, click on the three dots next to the entry and then click Mark as trusted.
-
(Optional) Export all visible data (according to any applied filters) to a CSV file.
-
Click on a SHA-256 entry to see more information about the file. The results open in a slideout panel.
Tenable OT
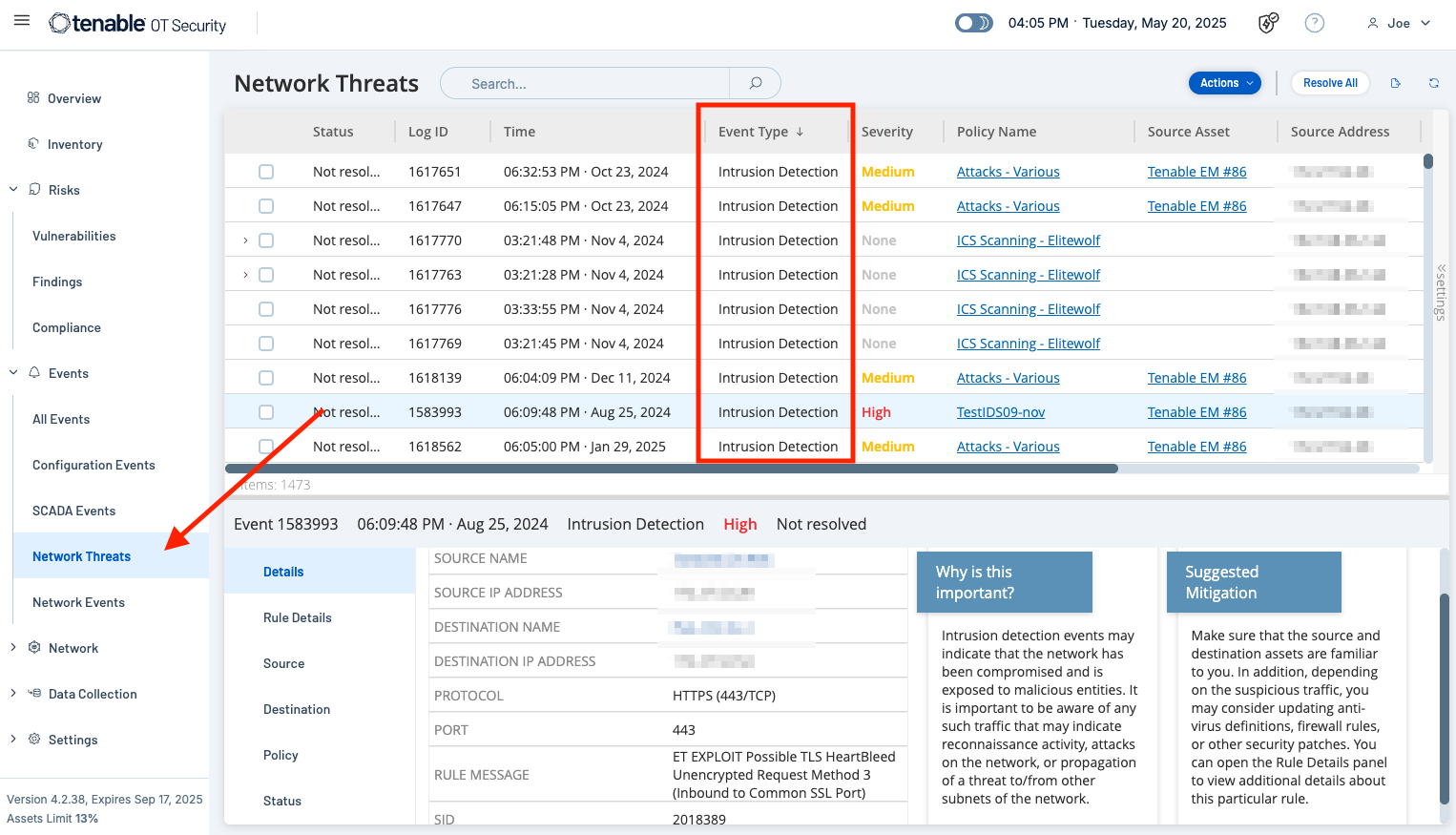
Malware detection within Tenable OT is accomplished based on communications from the device and IDS Policy Events. Intrusion detection events may indicate that the network has been compromised and is exposed to malicious entities. It is important to be aware of any such traffic that may indicate reconnaissance activity, attacks on the network, or propagation of a threat to/from other subnets of the network.
From the Events tab, navigate to Network Threats to view these types of events. Filters allow analysts to focus and narrow down results.