Key Component 2: Secure Configuration
Secure Configuration (also called security hygiene) is ensuring that devices and software are configured in the most secure way possible to reduce vulnerabilities and exposure to cyber threats. Unused software or services can introduce exploitable vulnerabilities. Default accounts and passwords are widely known and easy to exploit. The focus of this section applies to: servers, desktop computers, laptops, tablets, thin clients, mobile phones, IaaS, PaaS and SaaS.
A secure configuration is your first line of defense. Default configurations and installations are not always secure. As previously stated, pre-set and widely known passwords are major weak points. Access Control will be covered in the next section. However default accounts and pre-installed software that are not needed, or no longer required may allow attackers to gain unauthorised access to sensitive information. Secure configuration begins with the identification and removal/disabling of unnecessary accounts, applications, and services, organisations can minimise vulnerabilities.
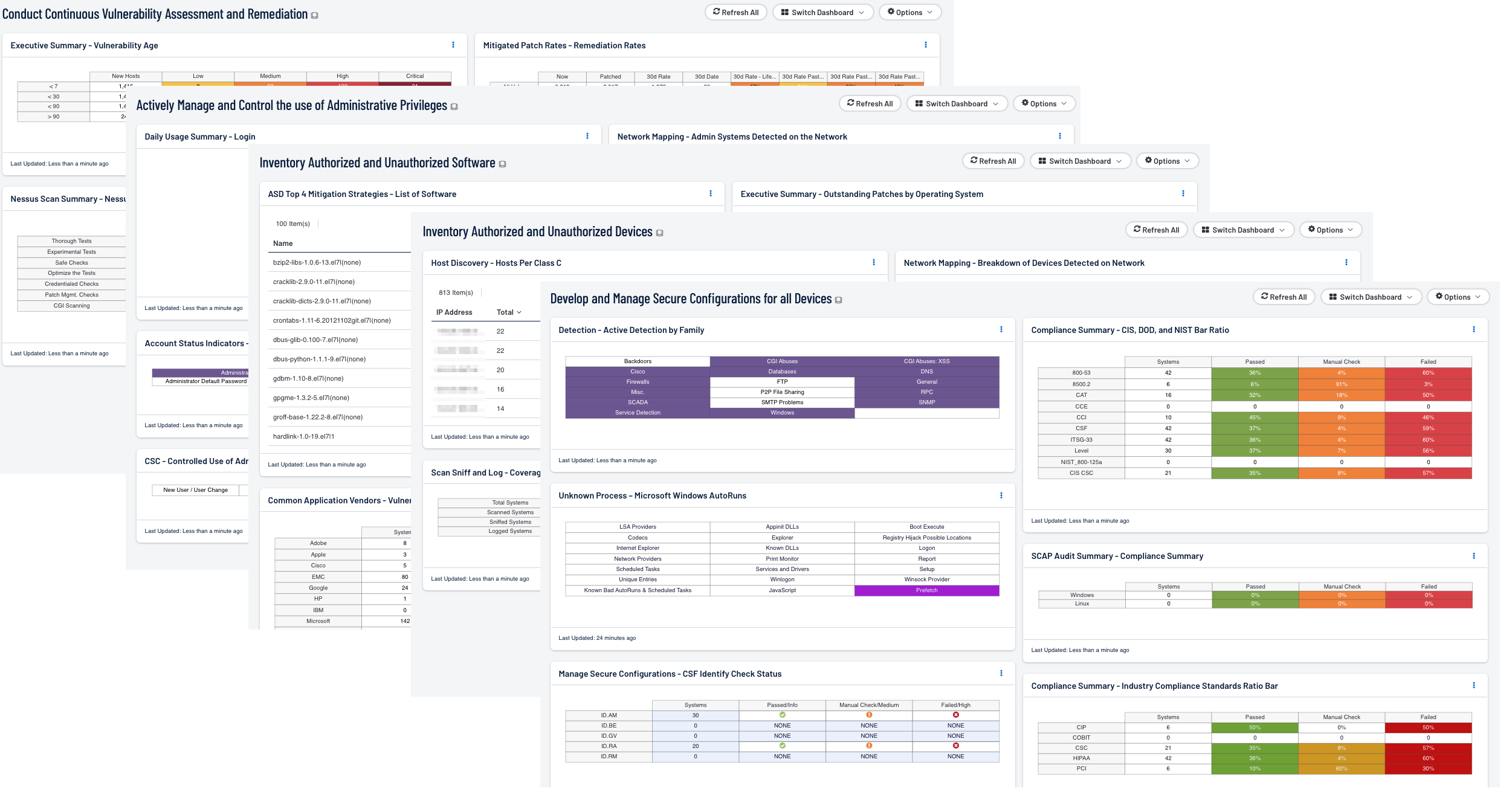
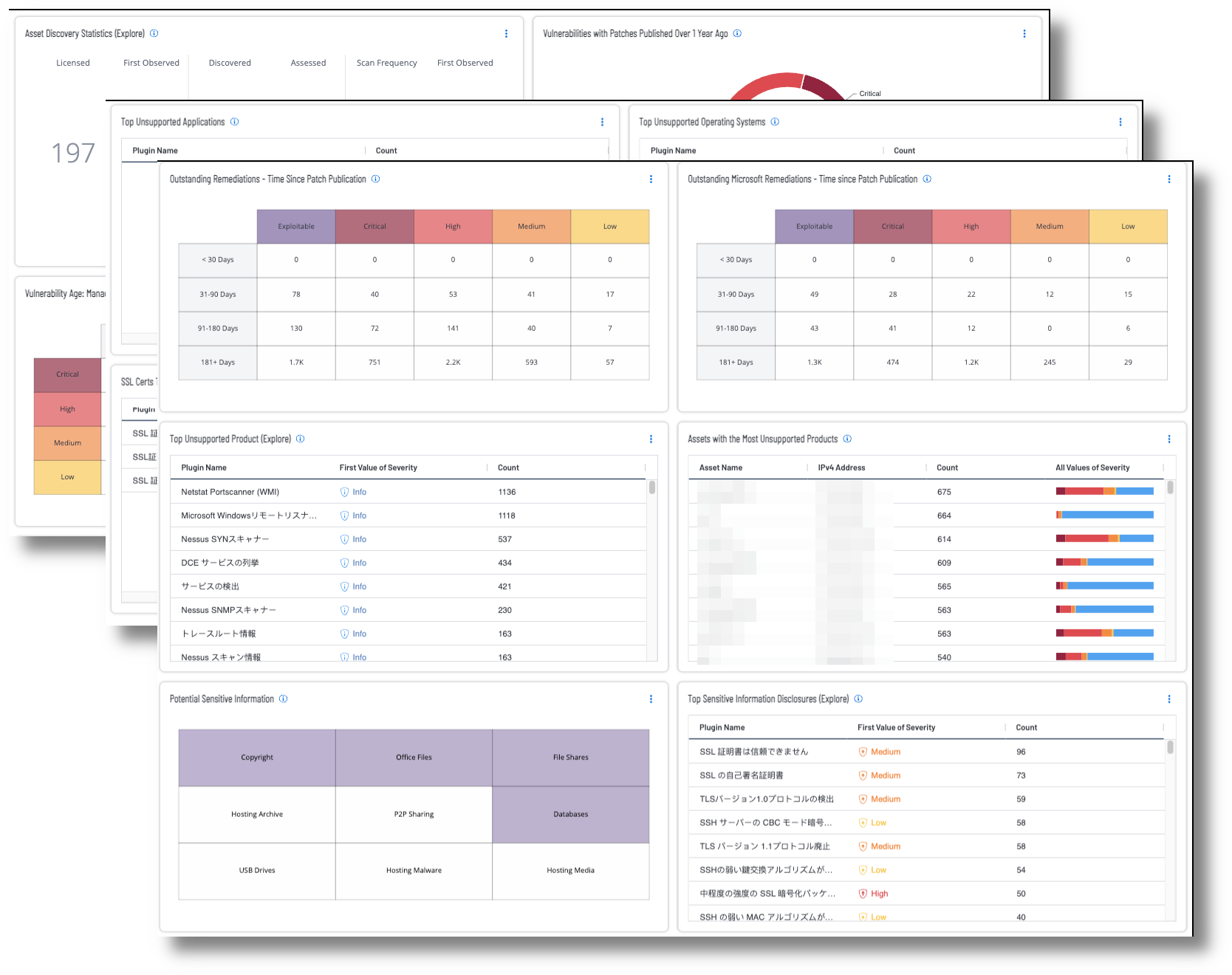
How Tenable can help: Tenable brought together a group of dashboards described in the “Tenable Solutions for the Cyber Hygiene Campaign” technical paper. These dashboards relate to the five actions identified by the Cyber Hygiene Campaign along with helping an organisation fulfil basic security needs such as monitoring.
For Tenable Security Center those dashboards are the Cyber Hygiene Dashboards.
For Tenable Vulnerability Management that dashboard is the Fundamental Cyber Hygiene Report Card.
The key areas of focus of these Cyber Hygiene dashboards related to the Cyber Essentials is:
Inventory Authorised and Unauthorised Devices: This collection of components provides information to analysts and auditors about systems discovered on the network and device inventory.
Inventory Authorised and Unauthorised Software: This dashboard and its components provide information to analysts about software that is discovered on the network.
Develop and Manage Secure Configurations for all Devices: Tenable has the ability to audit system configurations according to the standards. The components in this dashboard use forensic plugins, detections, and compliance checks to provide information about how systems are configured.
Conduct Continuous Vulnerability Assessment and Remediation: Tenable has the ability to monitor for vulnerabilities using active, passive, and event-based detection.
Actively Manage and Control the Use of Administrative Privileges: A common problem found in networks is that too many accounts with administrative privileges exist. Organisations should make an effort to use dual accounts when administrative rights are to be used. This dashboard provides information about which users have administrative control and how this control is used.
More information can be located within the Cyber Exposure Study NIS 2 Directive, Security Hygiene section.
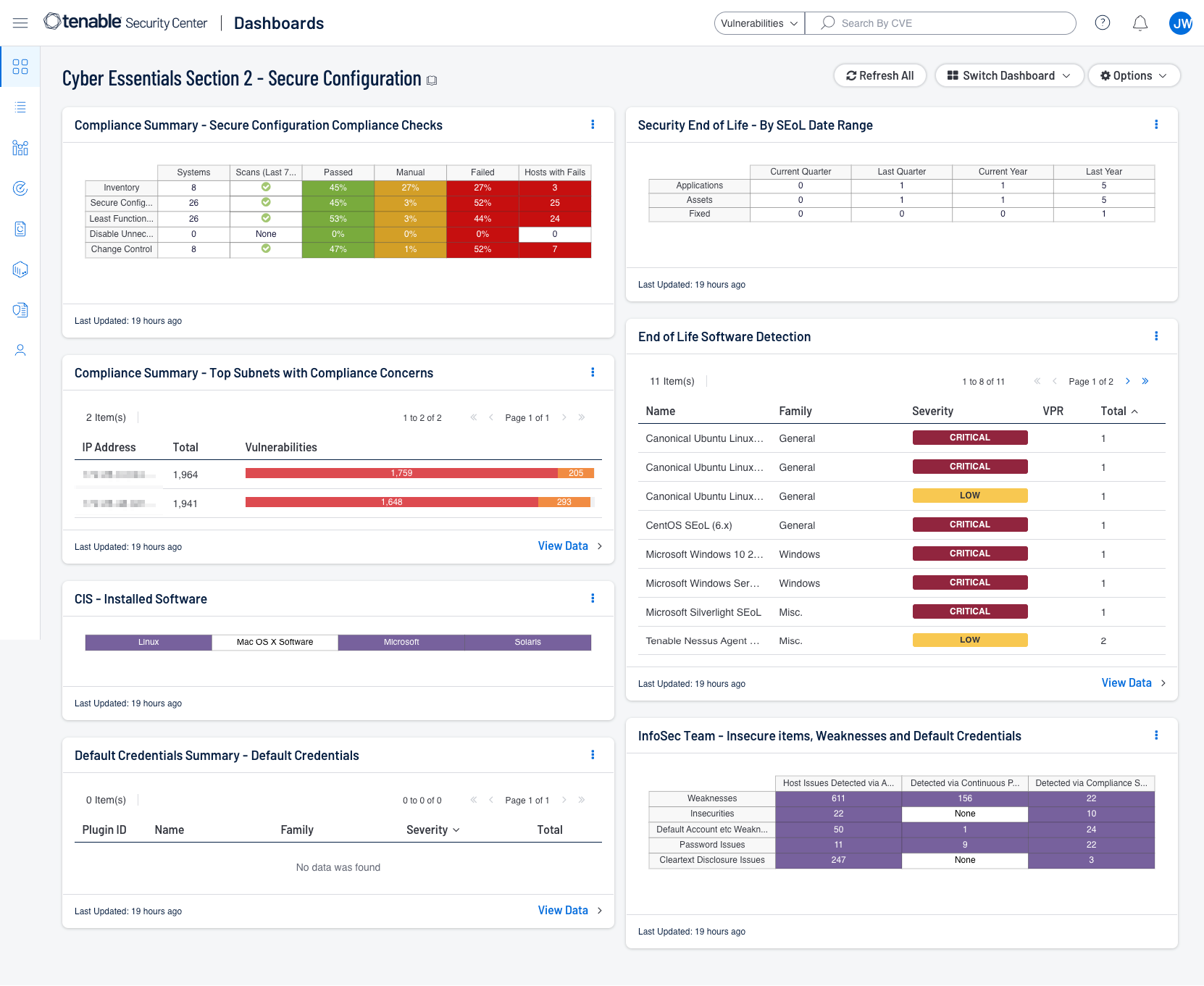
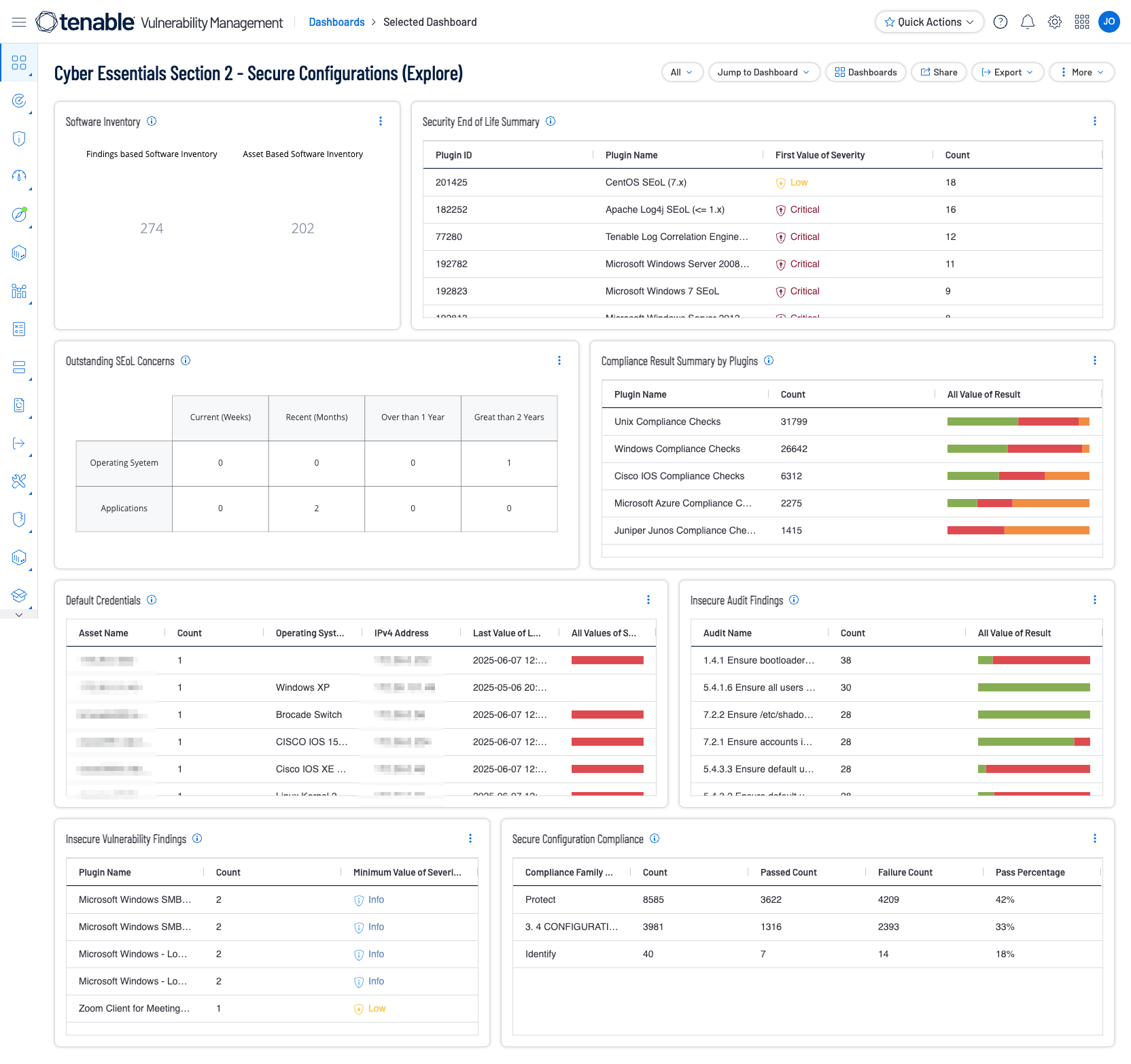
Tenable has provided a Cyber Essentials Dashboard and Report for Tenable Security Center and Tenable Vulnerability Management for this Key Component. Those dashboards and reports can be found here by using the term “Cyber Essentials” as a search query:
Security Center Dashboards and Reports
Vulnerability Management Dashboards and Reports
Shown below are screenshots of this section's dashboards for Security Center and Vulnerability Management.
Secure Configuration Assessment Questions Directly Addressed
Software
A6.1. Are all operating systems on your devices supported by a vendor that produces regular security updates and vulnerability fixes?
A6.2. Is all the software on your devices supported by a supplier that produces regular vulnerability fixes for any security problems?
Removing and/or disabling unused software and services reduces the attack surface, limits vulnerabilities by preventing exploitation. Additionally, fewer applications simplifies maintenance and configuration/patch management and improves performance. Questions in this section apply to: servers, desktop computers, laptops, tablets, mobile phones, thin clients, IaaS, PaaS, and SaaS. Regarding this Key Component area, the following Assessment questions can be directly addressed.
A5.1. Have you removed or disabled software and services that you do not use on your laptops, desktop computers, thin clients, servers, tablets, mobile phones and cloud services?
How Tenable can help: Detailed information related to managing a software inventory, detecting services, application server hardening, and unsupported software is available for review in the Software Inventory section of the cyber exposure study Application Software Hardening.
Necessary User Accounts and Default Passwords
Operating Systems and applications are often distributed with service and default accounts that are either not password-protected or have a default password that is well known. Questions in this section apply to: servers, desktop computers, laptops, tablets, mobile phones, thin clients, IaaS, PaaS, and SaaS. Regarding this Key Component area, the following Assessment questions can be directly addressed.
A5.2. Have you ensured that all your laptops, computers, servers, tablets, mobile devices and cloud services only contain necessary user accounts that are regularly used in the course of your business?
A5.3. Have you changed the default password for all user and administrator accounts on all your desktop computers, laptops, thin clients, servers, tablets and mobile phones that follow the Password-based authentication requirements of Cyber Essentials?
How Tenable can help: Tenable Nessus and Tenable Identity Exposure help identify these accounts, enabling organisations to review and disable any unnecessary accounts to reduce the attack surface. Organisations can leverage the following Nessus plugins to enumerate service and default accounts:
-
Plugin Family: Default Unix Accounts – This plugin family contains over 170 Nessus plugins that check for the existence of default accounts/passwords on a number of devices. In addition, there are many plugins that check for simple passwords such as “0000”, “1234”, and more commonly identified password combinations for “root” or administrator accounts.
Several hundred plugins can be identified by searching for “Default Account” from the Nessus Plugins Search page using the Enable Default Logins filter. Nessus default account plugins are available for Databases, Web Servers, SCADA devices, Unix/Linux devices, Cisco devices and more. Many of the plugins are associated with the Default Unix Account Nessus family, however, many are in other families as well.
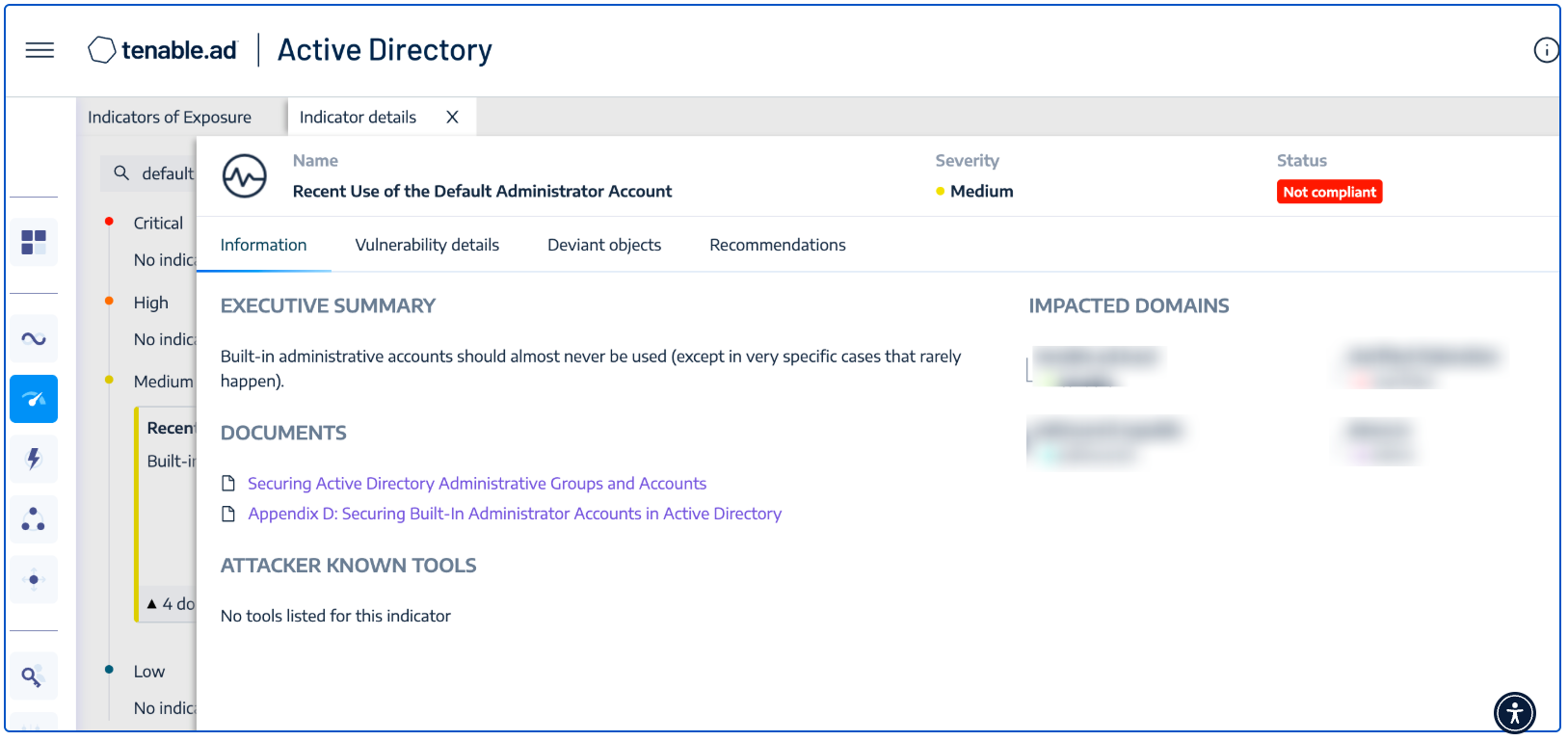
In addition, Tenable Identity Exposure provides the ability to determine if a default administrator account was recently used in the environment, as shown in the image below:
Compliance Scanning
Compliance and reporting are two concepts within business and regulatory frameworks. Compliance refers to the rules, regulations, standards, and laws set forth by external entities, such as government agencies, industry associations, or internal policies. Questions in this section apply to: servers, desktop computers, laptops, tablets, mobile phones, thin clients, IaaS, PaaS, and SaaS. Regarding this Key Component area, the following Assessment questions can be directly addressed.
A5.7. When not using multi-factor authentication, which option are you using to protect your external service from brute force attacks?
-
A. Throttling the rate of attempts
-
B. Locking accounts after 10 unsuccessful attempts
-
C. None of the above, please describe
A5.8. Have you disabled any feature which allows automatic file execution of downloaded or imported files without user authorisation?
A5.9. When a device requires a user to be present, do you set a locking mechanism on your devices to access the software and services installed?
How Tenable can Help: Tenable solutions include reporting features that help organisations demonstrate compliance with a number of cybersecurity regulations. This can be valuable for NIS 2 compliance, as organisations are required to report incidents and maintain proper documentation. Risk management measures can be validated with compliance scanning, providing detailed reports on applications and assets within the organisation.
Tenable has introduced key features and content that give you visualisation of Compliance scan results through the built-in dashboards or custom dashboards using the newly added widgets. Performing a compliance audit scan is not the same as performing a vulnerability scan, although there can be some overlap. A compliance audit determines if a system is configured in accordance with an established policy. A vulnerability scan determines if the system is open to known vulnerabilities. Organisations can deploy and customise audit files to meet their local security policy. Once the audit file is customised, the file can be used with Tenable products to manage and automate the configuration compliance process. Detailed or summarised reports can also be generated in PDF format for the host audit findings. Dashboards and reports exist for a wide variety of existing compliance standards such as:
-
GDPR
-
HIPAA
-
PCI-DSSv4.0
-
ISO/IEC-27001
-
NIST 800-53
-
ITSG-33 (Canada)
-
DISA STIG
-
Center for Internet Security
-
Tenable Best Practice Audits
-
Vendor-Based Audits
Detailed information on all the available Compliance dashboards can be found online by referencing these locations for Tenable Security Center and Tenable Vulnerability Management. For each select the Compliance and Configuration Assessment Category to list the available content and references.
Additional details on Compliance scanning can be found within the Host Audit Data Audit Overview Cyber Exposure Study located here.
Cloud services are an integral part of business operations, offering scalability, flexibility, and accessibility. Cloud environments store vast amounts of sensitive data, including personal information, financial records, intellectual property, and proprietary business data. Ensuring robust security measures protects this information from unauthorised access, breaches, or theft.
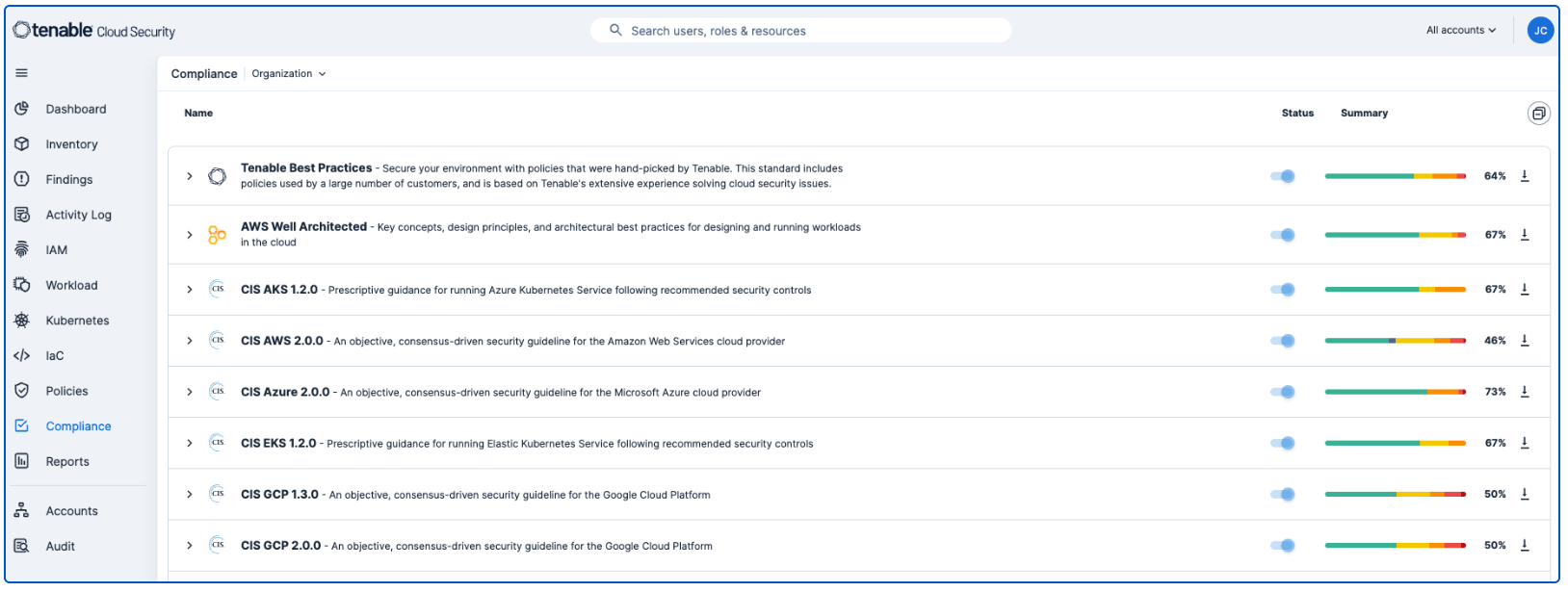
Protecting cloud environments is vital for protecting data, ensuring compliance with regulatory requirements, maintaining operational continuity, managing risks, and optimising business efficiency. Tenable Cloud Security provides out-of-the-box, continuously updated support for all major compliance frameworks, and best practices. Tenable Cloud Security provides the ability to create customised frameworks to meet the exact needs of your organisation. Using customised reports, communicate with stakeholders on internal compliance, external audit and daily security activities.
Compliance reporting is available by navigating to the Compliance tab. On the Compliance dashboard, analysts have the option to select the appropriate compliance benchmark from the list. By default, this dashboard reports compliance details for all Benchmarks combined if no option is selected.
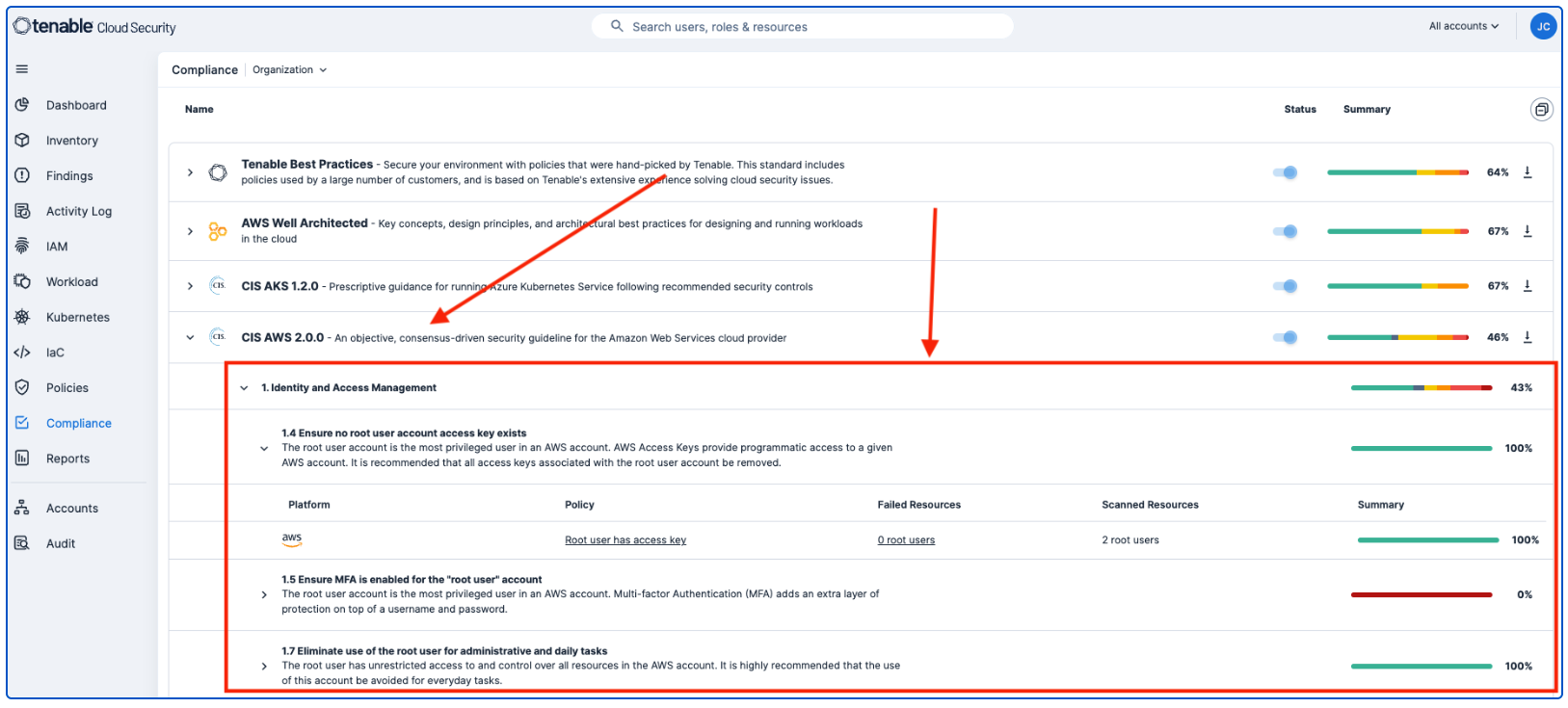
To view details, analysts can drill down into any of the findings. In this example, drilling down into the CIS AWS 2.0.0 item provides details on the root account.