Key Component 1: Firewalls and Internet Gateways
The focus of this key component is Firewalls and Internet Gateways. This key component applies to all the following in scope devices: Boundary Firewalls, Desktop Computers, Laptops, Routers, Servers, Iaas, PaaS, and SaaS devices. Devices must be secure and only necessary network services should be able to be accessed from the Internet. The objective of this key component is the control of inbound/outbound traffic.
This requirement applies to every in scope device, and can be achieved using Boundary Firewalls to restrict inbound or outbound traffic, a software firewall which is installed and configured on each end point device, or for cloud services, data flow policies. Most end point devices, such as desktops and laptops come with software firewalls pre-installed, and the Cyber Essentials recommends that these services be enabled. Essentially, every in-scope device must be protected by either a properly configured firewall, or a network device with firewall functionality.
Tenable provides audit files for a number of firewall vendors, such as Palo Alto, Check Point, Fortigate, Cisco, and more. Audit files can be reviewed online here. Unless otherwise specified, recommended audit files would be those such as the Center for Internet Security (CIS) labeled audit files, which has a global mission. The CIS audit files are based on the CIS Controls and Benchmarks, which test for applicable items within the categories of Identification and Authentication, Access Control, System and Communications Protection, and Configuration Management.
More information on configuring and using audit files can be found in the Tenable Documentation for Tenable Security Center, and Tenable Vulnerability Management. Detailed information is also available in the Tenable Compliance Checks Reference Guide.
Tenable has provided a Cyber Essentials Dashboard and Report for Tenable Security Center and Tenable Vulnerability Management for this Key Component. Those dashboards and reports can be found here by using the term “Cyber Essentials” as a search query:
Security Center Dashboards and Reports
Vulnerability Management Dashboards and Reports
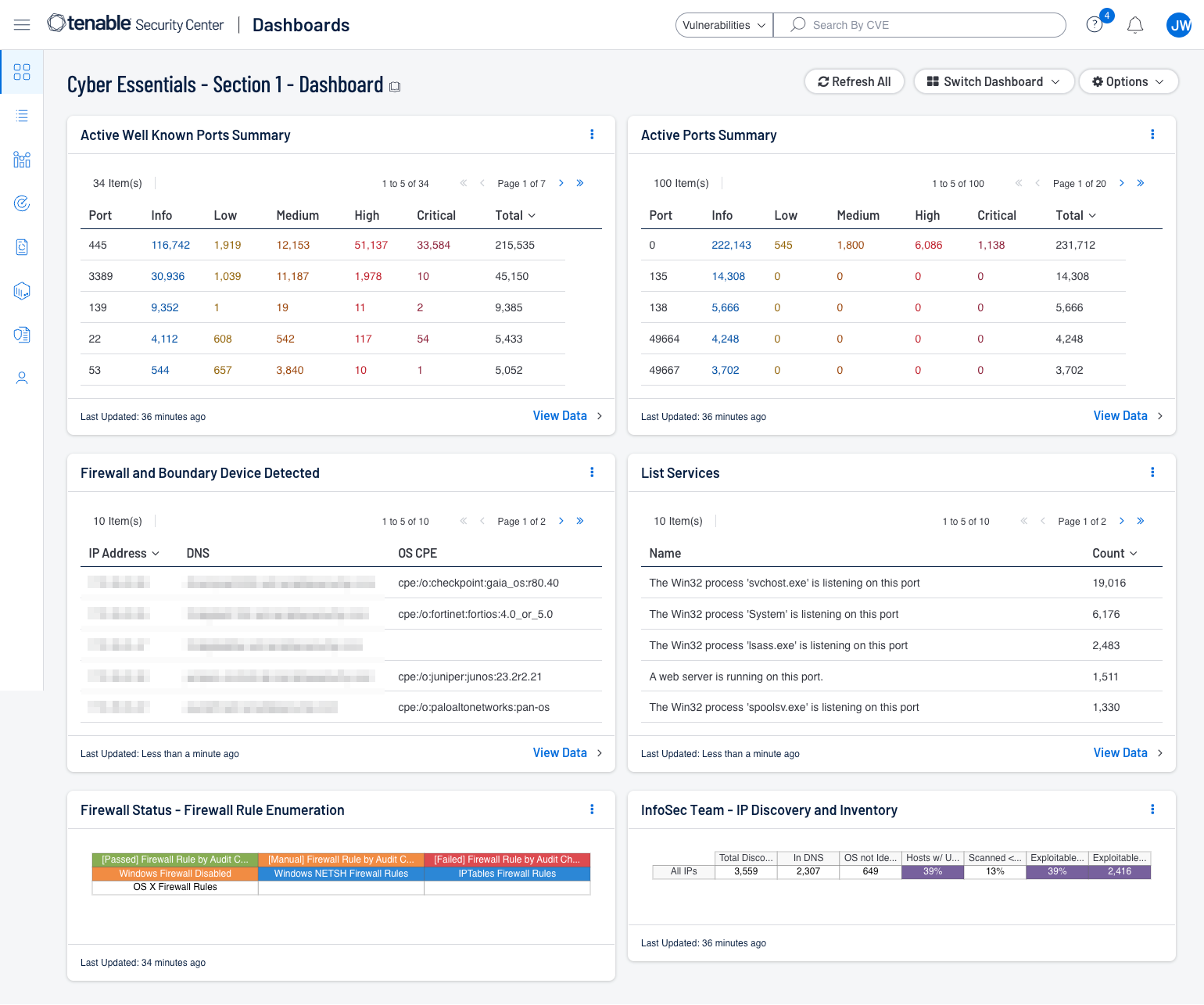
Shown below are screenshots of the this sections dashboards for Security Center and Vulnerability Management.
Firewalls Assessment Questions Directly Addressed
Questions in this section apply to: boundary firewalls, desktop computers, laptops, routers, servers, IaaS, PaaS, and SaaS. Regarding this Key Component area, the following Assessment questions can be directly addressed.
A4.1. Do you have firewalls at the boundaries between your organisation’s internal networks, laptops, desktops, servers, and the internet?
A4.1.1 Do you have software firewalls enabled on all of your computers, laptops and servers?
A4.1.2 If you answered no to question A4.1.1, is this because software firewalls are not installed by default as part of the operating system you are using? Please list the operating systems.
How Tenable can help: Can be accomplished by conducting discovery and assessment scans. Tenable recommends performing discovery scans to get an accurate picture of the assets on your network, and assessment scans to understand the vulnerabilities on your assets. The requirement includes mobile devices and the cloud infrastructure, as well as any other devices in scope. Reference the Getting Started and Scope of Assessment (Asset Identification) section of this document to identify assets.
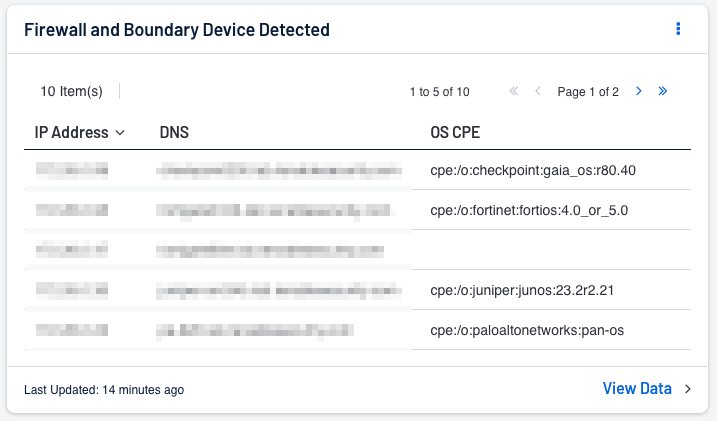
The Firewall and Boundary Device component for Tenable SC and widget for Tenable Vulnerability Management assists organisations with the rapid identification of firewall and boundary devices that have been identified in the environment. Displayed is the IP Address, DNS and OS CPE identifier for the device.
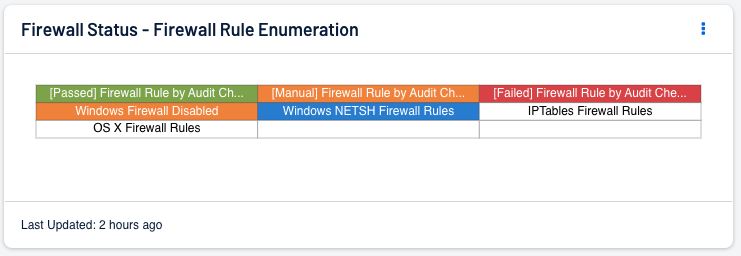
The Firewall Status - Firewall Rule Enumeration component addresses the identification of firewall software running or disabled on Windows devices, Firewall rules on macOS devices, and compliance issues. Scanning firewalls and reviewing the compliance findings can address the following items:
A4.6. Have you reviewed your firewall rules in the last 12 months? Please describe your review process.
A4.5. Do you have a process to manage your firewall?
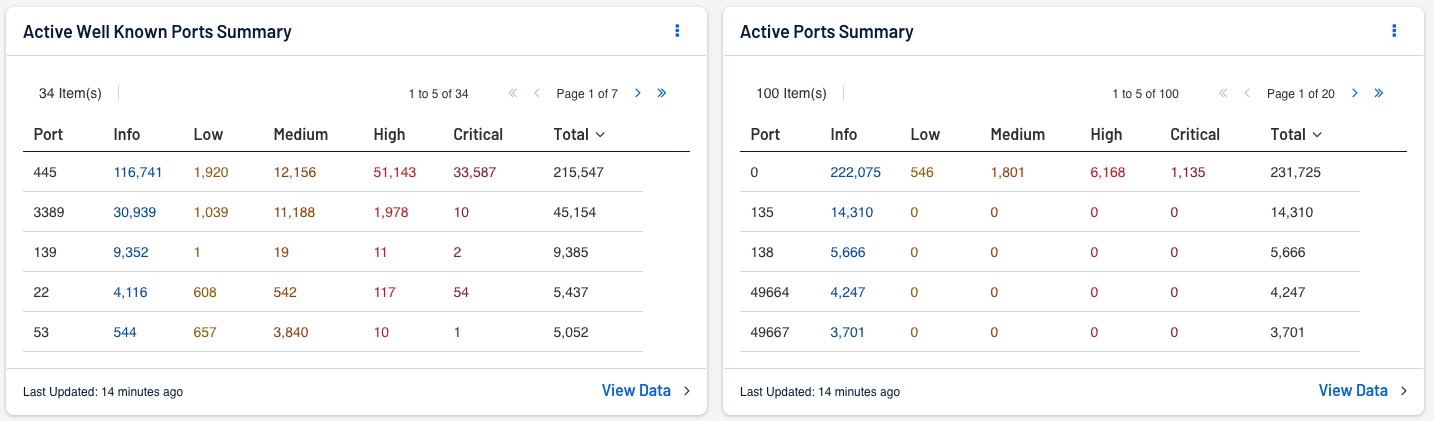
How Tenable can help: Can be accomplished with scanning for open ports. The Active Well Known Ports Summary component display the currently active well known ports (7, 20, 21, 22, 23, 25, 53, 67, 68, 69, 80, 88, 110, 111, 123, 137, 139, 143, 161, 194, 389, 443, 445, 464, 514, 547, 596, 636, 873, 1720, 2049, 3306, 3389, 5060, 5061, 5900, 8000, 8080, 8443) along with the count of those active ports, and the Active Ports Summary component display all identified active ports.
A5.4. Do you run or host external services that provide access to data (that shouldn't be made public) to users across the internet?
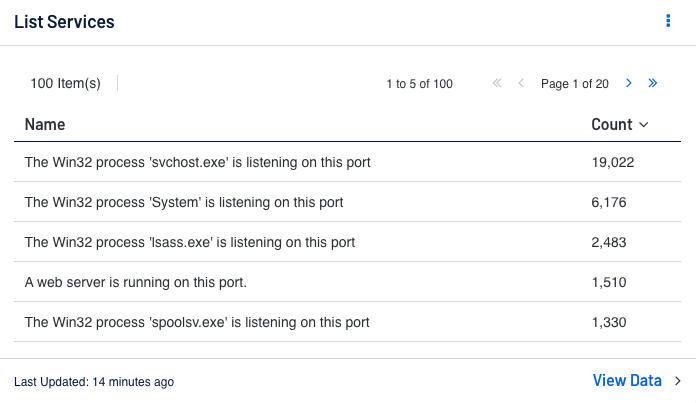
How Tenable can help: Can be accomplished with scanning for running services. The List Services component lists all services that have been identified in the environment, and displays them using the List Services Tool. As all devices may be in scope, all scanned devices are included in the display. Tenable Vulnerability Management and Tenable Security Center include plugins that detect running services and process information. The information from these plugins can display unregistered software that may be running on the system that is not shown in the registry. The plugins below provide visibility into services that may appear only in running processes rather than in installed software packages. The plugins below provide this valuable information.
-
58452 - Microsoft Windows Startup Software Enumeration
-
70329 - Microsoft Windows Process Information
-
70330 - Microsoft Windows Process Unique Process Name
-
70331 - Microsoft Windows Process Module Information
-
70767 - Reputation of Windows Executables: Known Process(es)
-
70768 - Reputation of Windows Executables: Unknown Process(es)
-
70943 - Reputation of Windows Executables: Never seen process(es)
-
110483 - Unix/Linux Running Processes Information
More information can be found in the Cyber Exposure Study for Establishing a Software Inventory under Detecting Running Services.
A4.2. When you first receive an internet router or hardware firewall device, it may have had a default password on it. Have you changed all the default passwords on your boundary firewall devices?
A4.3. A. B. C. D. E. How is your firewall password configured?
Please select the option being used:
-
Multi-factor authentication, with a minimum password length 8 characters and no maximum length
-
Automatic blocking of common passwords, with a minimum password length 8 characters and no maximum length
-
A password minimum length of 12 characters and no maximum length
-
Passwordless system is being used as an alternative to user name and password, please describe
-
None of the above, please describe
A4.7. Is your firewall configured to allow unauthenticated inbound connections?
A4.9. Are your boundary firewalls configured to allow access to their configuration settings over the internet?
A4.11. If you answered yes in question A4.9, is the access to your firewall settings protected by either multi-factor authentication or by only allowing trusted IP addresses combined with managed authentication to access the settings?
How Tenable can help: Can be accomplished with compliance scanning. The Firewall Rule Enumeration component uses plugin 56310 (Firewall Rule Enumeration) and audit checks to report on the status of software-based firewall rules. Compliance results; such as default passwords, MFA, and more are displayed on the Firewall Status - Firewall Rule Enumeration component within the appropriate Pass/Manual/Failed category.