Key Component 5: Patch Management
The focus of this key component is Patch Management. Unpatched vulnerabilities create known weaknesses that attackers can readily exploit. Well known is the fact that a large number of data breaches and ransomware attacks are directly attributed to systems with known, unpatched vulnerabilities. Organizations are brutally aware of the reasons for patching, such as regulatory compliance, risk mitigation, system stability, business continuity, reputation, and customer trust. Patch management is not just a technical necessity. Patch management is a strategic imperative for protecting assets, maintaining trust, and ensuring the resilience and sustainability of the organization.
Yet there are many challenges with regards to patching that must be addressed:
-
Patching is time-consuming, requiring a significant amount of time to conduct vulnerability assessments, patch deployment, and testing.
-
Patching requires down time, requiring restarts, downtime. Systems can crash, application errors can occur, and the potential to disrupt business operations is often high.
-
There are external factors involved such as relying on vendors to release patches, and organizations having limited access to equipment and resources.
This key component applies to all the following in scope devices: Boundary Firewalls, Desktop Computers, Laptops, Routers, Servers, Iaas, PaaS, and SaaS devices. The goal is to ensure that all devices are kept up to date with the latest security patches, reducing the risk of exploitation to known vulnerabilities. The Cyber Essentials requires organizations to:
-
Apply security patches promptly (within 14 days of release). This applies to all operating systems, applications, and firmware (routers/firewalls).
-
Remove and Replace all unsupported and outdated software. End-of-Life software must not be used unless the software is isolated and mitigation controls and/or compensating controls are in place.
-
Automatic updates are enabled where possible
Patch Management Assessment Questions Directly Addressed
Questions in this section apply to: servers, desktop computers, laptops, tablets, thin clients,
mobile phones, IaaS, PaaS and SaaS. Within this section, information is provided which addresses the following questions.
A6.2.1 Please list your internet browser(s) The version is required.
A6.2.2 Please list your malware protection software The version is required
A6.2.3 Please list your email applications installed on end user devices and servers. The version is required.
A6.2.4 Please list all office applications that are used to create organisational data. The version is required.
A6.3. Are any of the in-scope software or cloud services unlicensed or unsupported?
A6.3.1 If yes to A6.3, please list the unsupported or unlicensed software or cloud services.
A6.4. Are all high-risk or critical security updates and vulnerability fixes for operating systems and router and firewall firmware installed within 14 days of release?
A6.5. Are all high-risk or critical security updates and vulnerability fixes for applications (including any associated files and extensions) installed within 14 days of release?
A6.6. Have you removed any software installed on your devices that is no longer supported and no longer receives regular updates or vulnerability fixes for security problems?
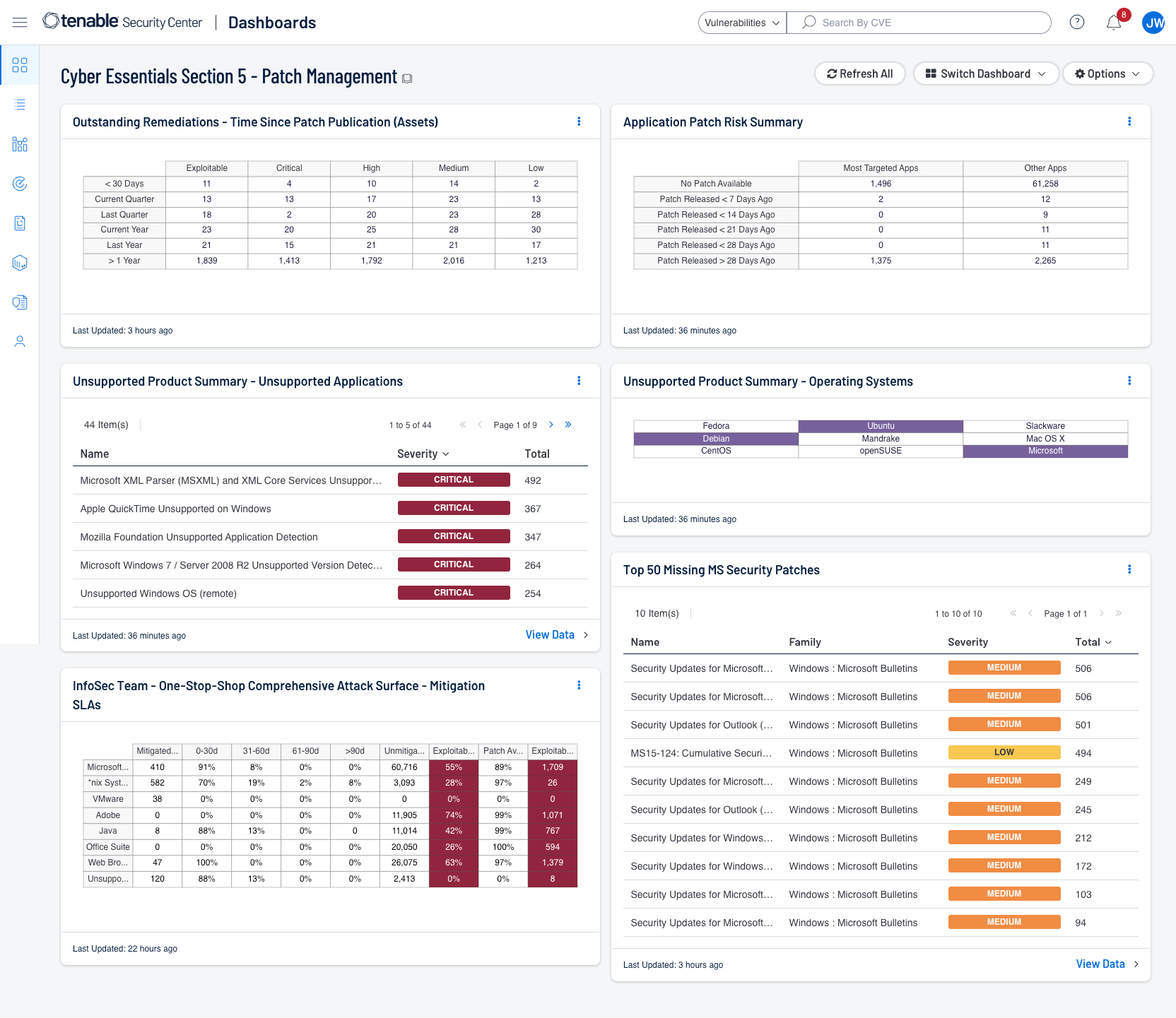
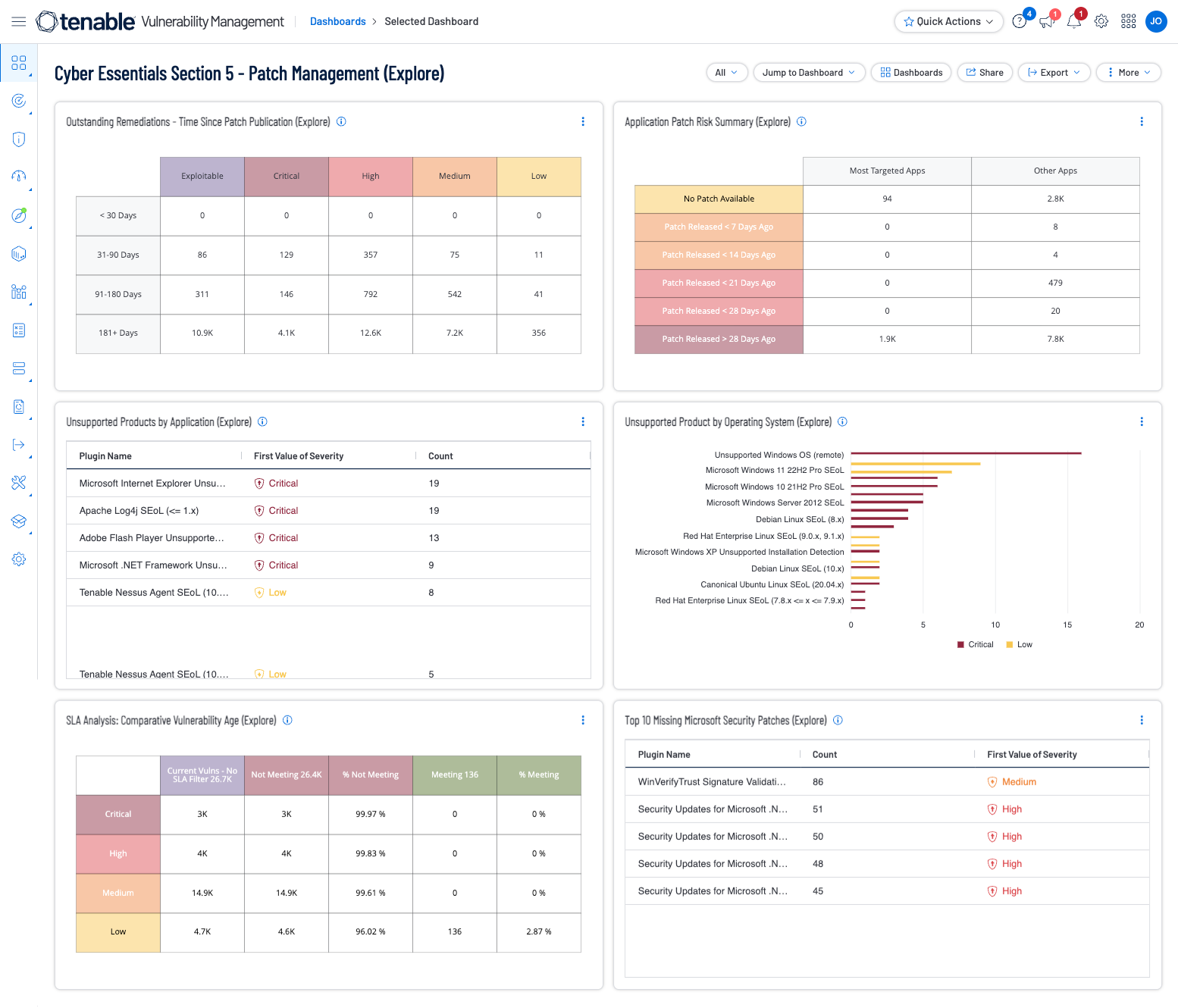
The Cyber Essentials - Section 5 Dashboard assists organizations by presenting a selection of widgets and components that track how application patching is currently being implemented by the organisation. Data provided includes patch rates, current vulnerabilities, and if the vulnerability can be patched or exploited for Operating Systems, and Applications in general. Missing Microsoft Security Updates are also displayed.
Tenable has provided a Cyber Essentials Dashboard and Report for Tenable Security Center and Tenable Vulnerability Management for this Key Component. Those dashboards and reports can be found here by using the term “Cyber Essentials” as a search query:
Security Center Dashboards and Reports
Vulnerability Management Dashboards and Reports
Shown below are screenshots of this section's dashboards for Security Center and Vulnerability Management.
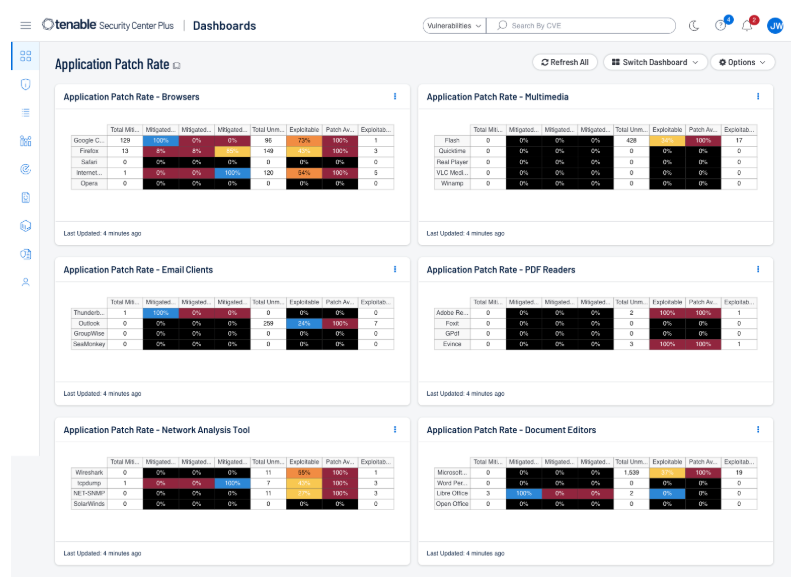
The Application Patch Rate Dashboard for Tenable Security Center presents an additional view of how application patching is currently being handled by the organization. The data provided includes the patch rates, current vulnerabilities, and if the vulnerabilities can be patched and exploited. The colors of the cells within the Application Patch Rate dashboard will change based on the percentage of patches applied. When 95% of vulnerabilities are mitigated the color will be blue. The color will be green for more than 75%, yellow for more than 50%, orange for more than 25%, and red when less that 25% of the vulnerabilities are patched. The total of the 3 columns will total 100%. When the majority of patches applied is in the forth column, a serious review of the patch management system should be conducted, because patches are taking longer than 30 days to be applied.
There is no set timetable to resolve vulnerabilities that fits every situation. SLAs can vary from organization to organization, and even vary between business units within the organization. Tenable recommends aligning SLAs with technology or business objectives, starting with the most important assets.More information on SLAs and Remediation can be found in the SLAs and Remediation section of the Cyber Exposure Study titled Cyber Insurance Report.
Once the highest priority vulnerabilities are identified, operations team needs to take the appropriate action to effectively manage the risk. For each vulnerability, there are three response options — remediate, mitigate, or accept. Which action is chosen for each should be in line with what was previously determined during the initial discovery phase, as you developed a comprehensive understanding of the environment. More information on Tracking and Reporting SLA Progress can be found within Tenable Documentation.
More details on Patch Management, including Operating System and Application Patch Management can be found in the Patch Management section of the Vulnerability Management Cyber Exposure Study
Getting Started with SLAs
Once the highest priority vulnerabilities are identified, operations team needs to take the appropriate action to effectively manage the risk. For each vulnerability, there are three response options — remediate, mitigate, or accept. Which action is chosen for each should be in line with what was previously determined during the initial discovery phase, as you developed a comprehensive understanding of the environment. But to be sure we’re clear on our terminology, here’s how we define each of them:
Remediate
Oftentimes, remediation is used interchangeably with patching. And in some cases, patching may be all that’s required. Something important to note is that typically, applying a patch is just one part of what’s required to remediate a vulnerability. The asset may also require removal or rebuilding the operating system, specific software components may need to be upgraded, or there could be a configuration error that needs to be corrected. Once the vulnerability is verified to have been fully remediated, the amount of risk associated with the vulnerability is fully removed from the environment.
Mitigate
Mitigation employs other technologies to reduce the risk of a given vulnerability. This is different from remediation because with mitigation nothing has really been done to actually fix the vulnerability itself. Instead, organizations are accounting for other mitigating factors that neutralise some or all of the risk posed by the vulnerability. For example, organizations may have firewall rules in place that effectively block an exploit from accessing sensitive data. To account for this mitigating factor, organizations would reduce the severity of the vulnerability accordingly.
Accept
Risk acceptance is consciously deciding not to take any action at all. This may be done for a variety of reasons. For example, during the discovery phase, management may have determined some assets are so business-critical they can’t afford to take them down for maintenance unless the vulnerability is also business-critical. In other cases, the cost of the fix may be greater than the cost associated with a successful exploit. Regardless of the reason, when organizations choose to accept risk, the VM platform may allow you to remove the risk score from reports or set the score to “0." However, organizations need to understand that while the vulnerability may no longer be immediately visible, the actual risk still remains in your environment.
These actions should align with the organizational plans established during the discovery phase of the risk-based VM lifecycle when the business environment was mapped, along with IT policies, and procedures.
Tenable Vulnerability Management contains the Fundamental Cyber Hygiene Report Card dashboard, which can be reviewed here. As vulnerabilities are identified, remediation must be prioritised and tracked in accordance with organizational goals and Service Level Agreements (SLAs). Reviewing remediated vulnerabilities and the remediation timeframe provides valuable information to the organization on the effectiveness of the risk remediation program.
More information on how Tenable Vulnerability Management and Tenable Security Center can assist can be found in the Tracking and Reporting SLA Progress section of the Tenable Vulnerability Management Cyber Exposure Study.
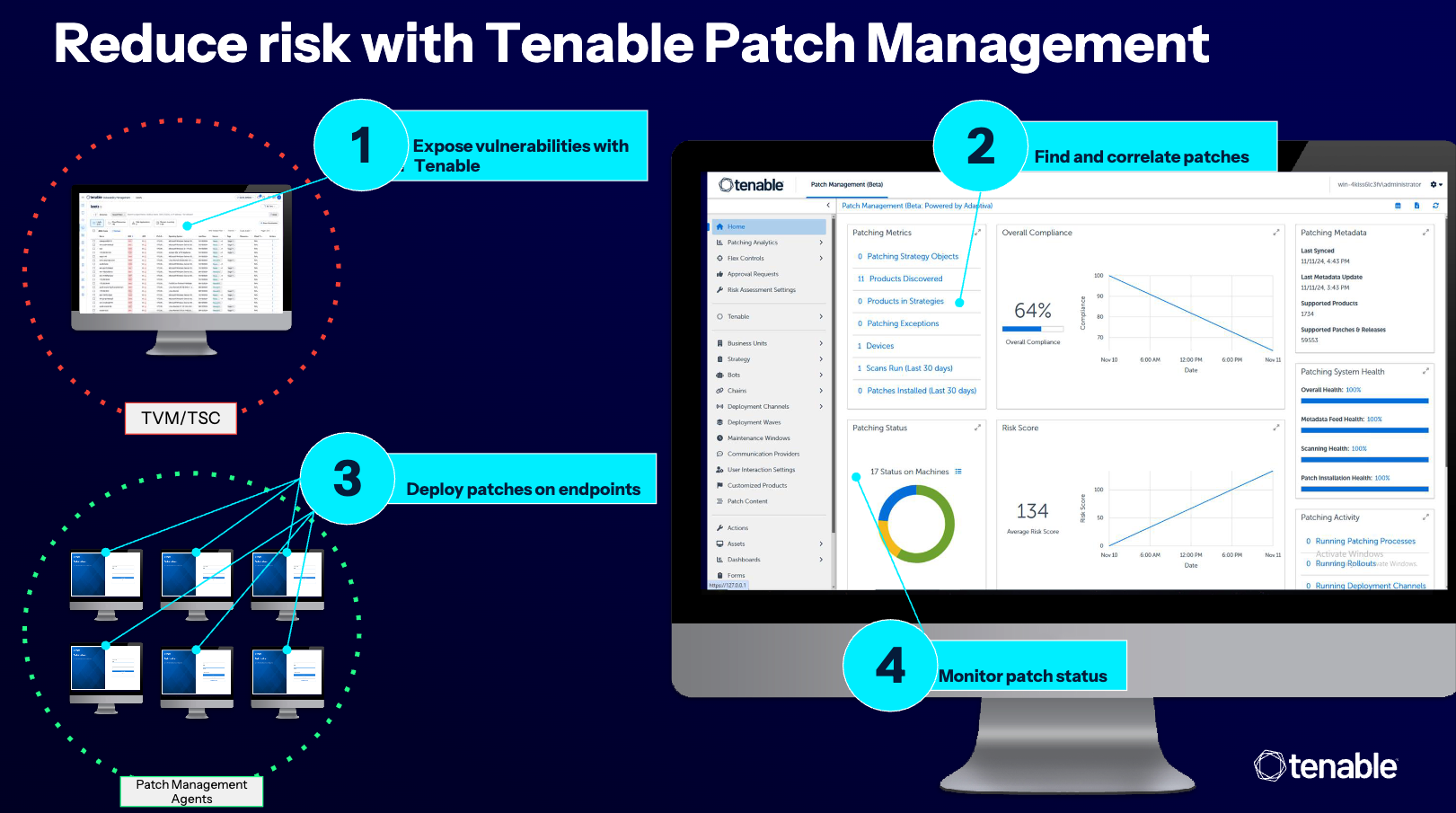
Tenable Patch Management
For customers that would like to have a patch requirement solution, or are required to have a patch management solution tied into the vulnerability management program, Tenable offers Tenable Patch Management. Patch Management allow organizations to:
-
Correlate vulnerabilities to patches
-
Easily tracks remediation compliance status with dedicated dashboards
-
Allows teams to determine how and where remediation actions are deployed
-
And maximises ROI by leveraging autonomous patching with customizable guardrails around approval workflows, version control, device type, and more.
More information on Tenable Patch Management is available here.
References:
Cyber Essentials Self-Assessment Preparation Booklet
IASME Consortium Ltd.
Cyber Essentials: Requirements for IT infrastructure v3.2
National Cyber Security Centre - a part of GCHQ
Cyber Essentials Plus Test Specification v3.2
National Cyber Security Centre - a part of GCHQ