Third-Party Risk Management
One key area that DORA regulates is Third-Party Risk Management. Third-party risk is significant, often because third parties have access to privileged information, such as customer data, and internal systems. Organisations can be negatively impacted in the form of data breaches, operational disruptions, and reputational damage. DORA requires that financial institutions identify their third party service providers. Tenable can assist organisations identify third-party vendors by identifying software, hardware, and cloud services that have been identified within the organisation. In addition to the Articles previously listed, the following DORA Articles are related to Third-Party Risk Management efforts:
-
Article 8.2, Financial entities shall, on a continuous basis, identify all sources of ICT risk.
-
Article 8.3, Financial entities shall identify all information assets and ICT assets, including those on remote sites, network resources and hardware equipment.
-
Article 9.4(e), Controls for ICT change management, including changes to software, hardware, firmware components, systems or security parameters are documented.
In this section the following Tenable products will be highlighted:
-
Tenable Vulnerability Management
-
Tenable Security Center
-
Tenable Cloud Security
Tenable has previously published a Cyber Exposure Study for the Network and Information Security 2 (NIS 2) Directive. While DORA and NIS 2 have a different focus, the two are related and work together to enhance cybersecurity and operational resilience in the EU. DORA builds on the standards set by the NIS 2 for ICT and resilience. The NIS 2 provides general guidelines and DORA tailors those specifically to the financial sector. The incident reporting requirements are aligned with NIS 2, and both DORA and the NIS 2 place a strong emphasis on third-party risk management.
Identifying installed applications is a key factor in the identification of third-party vendors, reducing risk, and securing the organisation from unwanted attacks. A software inventory helps demonstrate compliance with regulatory controls and Service Level Agreements (SLA) for software used in the environment. From the perspective of “less is more,” a software inventory also identifies unnecessary software running in the environment, which increases the attack surface without providing a business advantage. Tenable Vulnerability Management and Tenable Security Center help organisations identify software vendors and build a software inventory.
There are several software discovery plugins that run by default in the following scan templates:
-
Basic and Advanced Agent Scans
-
Basic and Advanced [Network] Scans
-
Credentialed Patch Audit
-
Internal PCI Network Scan
-
Collect Inventory Agent Scan (see below)
Inventory Agent Scanning in Tenable Vulnerability Management contains a Collect Inventory template which provides faster scan results and minimises the Nessus Agent load and installed footprint on the endpoint. Leveraging this new scan policy ensures the agent only runs an inventory collection plugin locally and sends results to Tenable Vulnerability Management for processing. Scan results are presented in the same format as traditional scans. While there is a coverage differential compared to using a traditional agent, the Inventory Agent provides a great option for host-based scanning on hosts with limited resources.
Note: Inventory Agent Scanning is supported on the following platforms:
Tenable Vulnerability Management Agent scans
Tenable Security Center imports of Tenable Vulnerability Management cloud agent scans
Other methods of application identification to utilise software enumeration plugins. The most common software enumeration plugins are OS Identification (11936), Microsoft Windows Installed Software Enumeration (credentialed check) (20811), Software Enumeration (SSH) (22869), and List Installed Mac OS X Software (83991). There are several other software enumeration plugins that provide information that can help build a software inventory:
-
OS Fingerprinting via DHCP (7120)
-
Oracle Installed Software Enumeration (Linux / Unix) (71642)
-
Oracle Installed Software Enumeration (Windows) (71643)
-
OS Identification and Installed Software Enumeration over SSH v2 (Using New SSH Library) (97993)
-
Unix Software Discovery Command Checks (152741)
-
Unix Software Discovery Commands Available (152742)
-
Unix Software Discovery Commands Not Available (152743)
Note: Plugin Spotlight: Plugin ID 22869, Software Enumeration (SSH), identifies the package list on Linux systems, which includes package name, version, epoch information for each package installed on the system, and (on RPM-based systems) the date the operating system reports that a package was installed. This information is included in the plugin output (also referred to as “vulnerability text") in the scan results.
Dashboards and Reports, such as Establishing a Software Inventory (SEE), for Tenable Security Center, helps demonstrate compliance with regulatory controls and Service Level Agreements (SLAs) for software used in the environment. From the perspective of “less is more,” a software inventory also identifies unnecessary software running in the environment, which increases the attack surface without providing a business advantage.
For more information on Software Inventory see the Establishing a Software Inventory Cyber Exposure Study here.
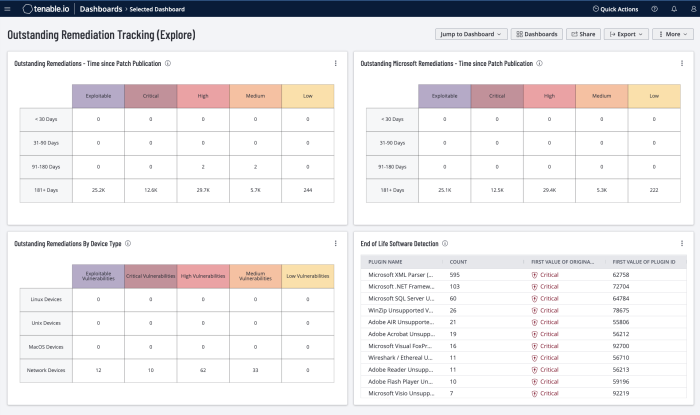
The Outstanding Remediations Tracking dashboards for Tenable Security Center and Tenable Vulnerability Management address third-party risk associated with unsupported, out-dated, and end-of-life software. These dashboards also address risk associated with third-party products by identifying software/applications that are out of compliance or present risk to the organisation.
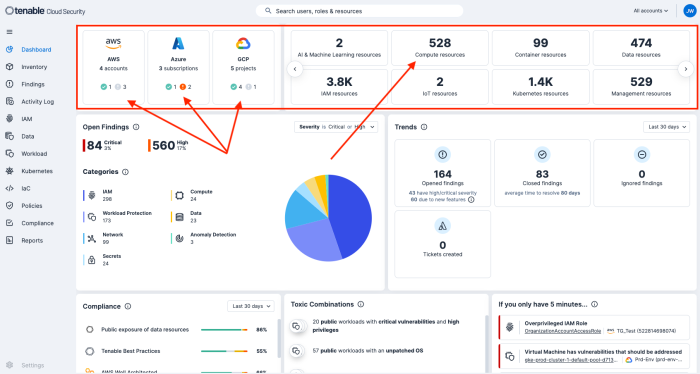
Tenable Cloud Security not only automates threat detection and remediation to eliminate noise, but also identifies cloud services and prioritises risk by continuously monitoring the cloud environment. Tenable analyses cloud provider logs to reveal the identity behind each activity and affected accounts, resources, and services.
From the Tenable Cloud Security dashboard, organisations can immediately begin to identify resources that have been identified such as Compute, Container, and more. Organisations can identify vendors such as AWS, Azure, and GCP.
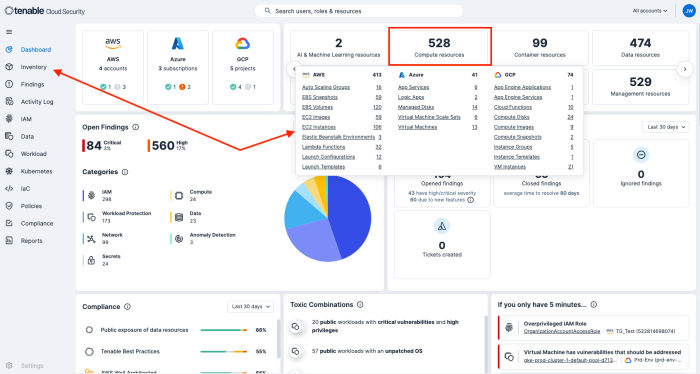
Clicking on Compute resources provides a shortcut to the Inventory tab, displaying important inventory items such as Volumes, Images, Instances, Virtual Machines, and more allowing fast and easy third-party vendor and application identification.
For more information on Tenable Cloud Security, reference the following documentation.