Continuous Monitoring
Continuous monitoring is the real-time, or near real-time process of monitoring and analysing systems for vulnerabilities. The process is an ongoing assessment of the organisation's infrastructure, networks, and systems to detect and respond to threats. By continuously collecting and analysing information, organisations can identify issues early, mitigate risks, and improve the overall effectiveness of the cyber security program. Continuous monitoring helps to quickly identify vulnerabilities and potential breaches, helping organisations maintain a proactive approach to risk management.
The following sections within the NIS 2 may be best suited to fall into the Continuous Monitoring category:
-
Article 21(2) (c): Business Continuity: Business Continuity Process and Technology
-
Article 21(2) (i): Access Control Policies and Asset Management: Asset Discovery and Access Control
A successful continuous monitoring program includes automated tools and techniques to monitor the organisation's infrastructure for vulnerabilities. These include using a vulnerability scanner to scan networks, systems, and applications for known vulnerabilities, misconfigurations, or weak points that can be exploited.
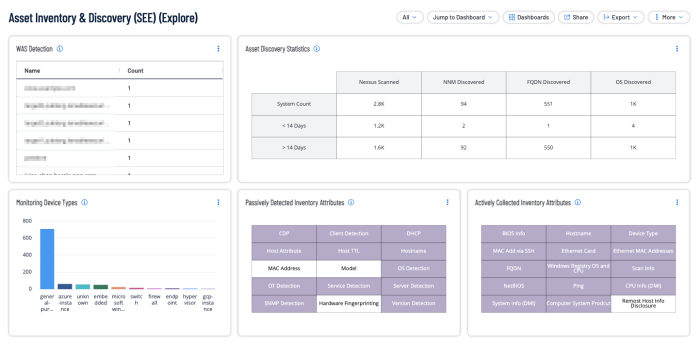
Organisations must know the existence and location of critical assets to ensure that assets are monitored and protected based on each asset’s business risk rating. Identifying assets facilitates vulnerability scanning and remediation by ensuring that scans are configured to probe for common weaknesses in the platform or application. Discovering all assets enables organisations to establish an inventory, which can be used to assess and mitigate associated risks to the organisation. The Asset Inventory and Discovery dashboards for Tenable Vulnerability Management and Tenable Security Center assist organisations with the continuous monitoring and identification of assets with the organisation.
The next steps include a vulnerability assessment, risk prioritisation, remediation, and patch management. The continuous monitoring program feeds data into these processes. Each of these steps has their own sections within this guide which focus on providing strategies which enable organisations to be successful in starting or maintaining their vulnerability management program. Continuous asset discovery is also an important aspect of continuous monitoring. For more information on Asset Discovery and Classification reference the Asset Inventory and Discovery Cyber Exposure Study.
In order to monitor for, and to identify vulnerabilities, meet guidelines/SLAs for timely remediation, compliance requirements, manage organisational assets, and proactively manage risks – continuous monitoring is an essential component of any comprehensive security strategy. For this section, the focus is on the first step, ensuring that the organisation’s assets are being assessed on a regular basis. This can best be achieved by first ensuring that the scanning program is healthy.
Ensure that the proper scan credentials are being used for the broadest vulnerability analysis. For more information on Authenticated vs. Unauthenticated Scanning see the Vulnerability Management section of this guide, and the Vulnerability Assessment/Scanning section of the Vulnerability Management Cyber Study.
There are a number of useful plugins used to authenticate to the remote host which assist in determining the health of the vulnerability scanning program. These plugins gather the information necessary for local checks, and enable local checks. These plugins can be used to troubleshoot authentication problems. Their output and audit trails provide details of any problems that were encountered. These plugins and their descriptions are listed under Local Authentication in the following guide: Vulnerability Assessment/Scanning section of the Vulnerability Management Cyber Study.
Web Applications
Web Applications require additional treatment. Tenable Web App Scanning provides easy-to-use, comprehensive, and automated vulnerability scanning for modern web applications. There are significant differences between scanning for vulnerabilities in web applications and scanning for traditional vulnerabilities with Tenable Nessus, Tenable Nessus Agents, or Tenable Nessus Network Monitor. As a result, Tenable Web App Scanning requires a different approach to vulnerability assessment and management.
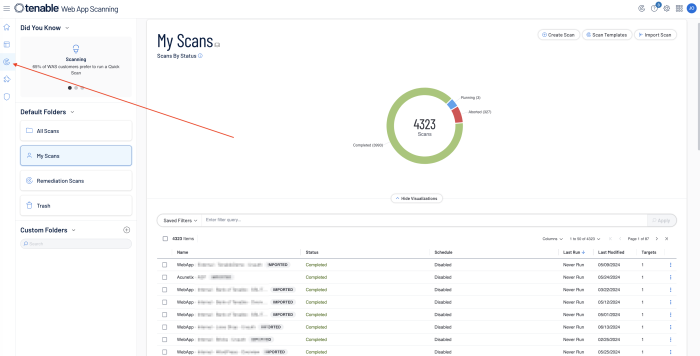
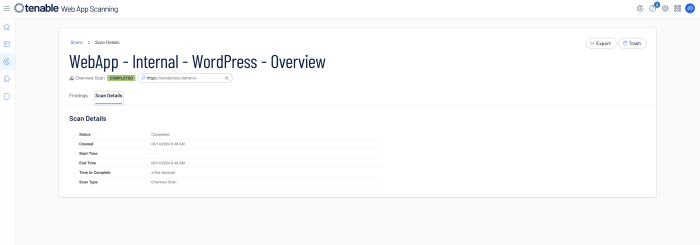
When reviewing scan program health details from within Tenable Web App Scanning, click on the Scans icon that is available on any page. The My Scans page will load and information on the status of the Web Application Scanning program will be displayed. To view additional details click on any scan and then select Scan Details.
The Scan Details displays information on the status of the scan (Completed, Aborted), the start and end time, duration of the scan, and the scan type.
For more information on Web App Scanning, see the following information: Getting Started with Web Application Scanning.
Industrial Control Systems
When OT devices are an integral part of the organisation, Tenable.ot continuously monitors all ICS activities, including activities taking place over proprietary PLC protocols. Tenable.ot identifies real-time anomalies, suspicious and unauthorised activities, and reports on these cyber security events. Tenable.ot uses a network threat detection engine that routinely searches for malicious activity in the network. The engine generates alerts based on the identification of these threats in the network.
This is accomplished by automatically establishing a baseline of each controller configuration and continuously monitoring for configuration changes. All changes are reported, and security staff members are alerted if any unauthorised change is made through the network or physically by connecting directly to the OT device. Besides providing useful information, this capability documents that all configuration changes to controllers were noted and accounted for.
Tenable.ot regularly (at user-defined intervals) scans each controller and takes a snapshot of the device's configuration file. These snapshots are then compared with the previous day’s file, changes are noted, and alerts with information on those changes are created. This allows organisations to catch suspicious changes and investigate or reverse them. Conventional anomaly detection solutions can’t do this. New baselinings can be invoked at any time by the administrator.
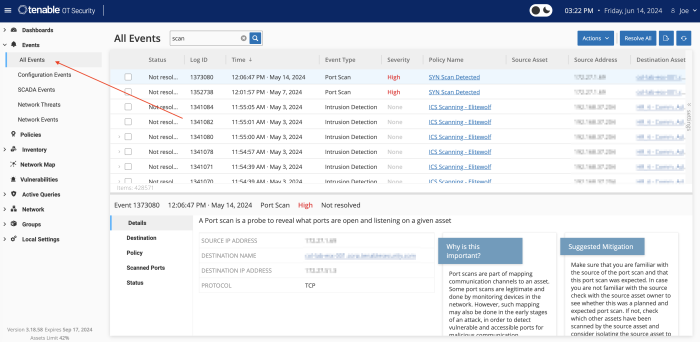
Additionally, Tenable.ot monitors the network traffic and creates a baseline of the expected network communications. Any violation to this baseline triggers an alert. Tenable.ot monitors the used network ports/protocols and any deviation from the expected network protocols (baseline) triggers an alert which can be viewed under the Events page, and then selecting a filtering option or All Events.
Cloud Infrastructure
The dynamic, distributed nature of cloud environments often creates alerts that lack context at a volume that can overwhelm security teams. Manually sifting through log data and attempting to correlate the data can quickly flood teams with false positives instead of actionable insights. To make matters worse, when suspicious or unusual activity such as misconfigurations or access-related risks are found, teams may quickly realise they lack the depth and context needed to get to the bottom of it.
Tenable Cloud Security automates threat detection and remediation to eliminate noise enabling your team to focus on what matters most. In-depth investigation, monitoring, and reporting on suspicious or unusual activity across AWS, Azure, and GCP is simplified by creating a behavioural baseline for each identity. By continuously assessing and prioritising risk across human and service identities, network configuration, data, and compute resources Tenable Cloud Security proactively reduces the attack surface and blast radius in case of a breach.
The organisation's entire multi-cloud environment is continuously analysed, evaluating risk factors including effective exposure, misconfigurations, excessive and risky privileges, leaked secrets and vulnerabilities. Unusual data access, privilege escalation and other identity-related threats, as well as changes in login settings, unusual reconnaissance, and unauthorised use or theft of access keys, can all be detected. Tenable analyses cloud provider logs to reveal the identity behind each activity and affected accounts, resources, and services.
For more information on Tenable Cloud Security, reference the following documentation.
The following cross-reference information is provided to derive a more comprehensive and effective approach to managing information security requirements. NIS 2 Article 21(2) (c) references security in resilience and Business continuity management. NIS 2 Article 21(2) (i) references Asset Discovery, both processes fall within continuity management.
Security domains define how information is classified, categorised, or administered. The following Security Domains, Sub-Domains, and Measures are related to NIS 2 Article 21(2) (c) and (i), and can assist organisations already using other standards and frameworks to comply with NIS 2.
SECURITY DOMAIN: Resilience
SECURITY SUB-DOMAIN: Continuity of operations
SECURITY MEASURE: Business continuity management
In an effort to foster higher consistency and reliability across multiple frameworks and the NIS 2, Article 21(2) (c) and (i) can be associated with the ISO 27001, NIST CSF, and ISA/IEC 62443 utilising the following cross-references for continuity of operations. The following cross-references cover the processes and procedures related to Resilience and Business continuity management.
CROSS REFERENCES:
The ISO 27001 references sections within Performance Evaluation, and Improvement, specifically the following sections:
-
ISO 27001 (9.3, 10.2, A.5.1.2, A.11.2.4, A.17.1, A.17.2)
-
The NIST CSF references the following sections within Identify, Protect, Respond, Recover, and Protect.
-
NIST CSF (ID.RM-1, 2, 3, PR.IP -4, 7, 9, 10, RS.IM- 2, RC.IM -1, 2, RC.RP -1, RC.CO -1,2,3, PR.PT -5, PR.DS -4, ID.BE -5, ID.SC -5)
The ISA/IEC 62443 references the following sections within Auditable Events, Security Functionality Verification, Boundary Protection, Audit Logs, and Resource Availability.
-
ISA/IEC 62443 (SR 2.8, SR 3.3, SR 5.2, SR.6.1, SR 7.1, SR 7.2, SR 7.3, SR 7.4)
_thumb_700_0.png)