Vulnerability Management
Vulnerability Management is the process of identifying, assessing, reporting, managing, and remediation of vulnerabilities across the organisation on an on-going basis. Article 21(2) (e) addresses Network and Information Systems Security, including, acquisition, development, maintenance, and vulnerability handling and disclosure. Organisations can map NIS 2 to other standards, such as ISA IEC 62433, ISO 27001, and NIST CSF via the Cross-Reference notes. This document provides readers with a key aspect in addressing specific requirements within the topic area.
Key Aspects of Vulnerability Management
Tenable utilises Risk-based Vulnerability Management (RBVM) to take the guesswork out of which vulnerabilities you should tackle first. RBVM gives organisations clear answers to reduce the time and effort in navigating through a never-ending vulnerability backlog.
RBVM is a process that reduces vulnerabilities across your attack surface by prioritising remediation based on the risks they pose to your organisation. Unlike legacy vulnerability management, risk-based vulnerability management goes beyond just discovering vulnerabilities. This unique approach helps organisations understand vulnerability risks with threat context and insight into potential business impact.
Risk-based vulnerability management uses machine learning to correlate asset criticality, vulnerability severity, and threat actor activity. This helps organisations cut through vulnerability overload so they can focus on the relatively few vulnerabilities that pose the most risk to your enterprise. Article 21, paragraph 2, section e, references Network and Information Systems Security, including Vulnerability Handling and Disclosure. This section specifically addresses preventative network and information vulnerability management.
Preventative Network and Information Vulnerability Management
Several sections within the NIS 2 may be best suited to fall into the Vulnerability Management category. Those include:
-
Article 21(2)(e) Network and Information Systems Security, including Vulnerability Handling and Disclosure
-
Article 21(2) (d): (d) Supply chain security, including security-related aspects concerning the relationships between each entity and its direct suppliers or service providers.
-
Article 21(2)(g) Basic Cyber Hygiene Practices and Cybersecurity Training
-
Article 21(2)(a) Risk Analysis and Information System Security
The Cyber Hygiene, Section (g), and Risk Analysis, Section (a), are special topics and therefore will be discussed in more detail in the Security Hygiene Practices, and Risk Assessment section of this guide.
Knowing what hosts are on your network is the starting point to any vulnerability assessment. The diverse location of assets makes discovery and identification a challenge. Understanding where critical assets are and accurately inventorying assets is the crucial first step in Risk-Based Vulnerability Management (RBVM). Through credentialed scanning, assets can be reliably identified and attributes collected, which enables organisations to establish and validate inventory management. Tenable Vulnerability Management helps validate and collect information needed to maintain a healthy asset inventory. As assets are discovered, an organisation can begin to establish an inventory, which can be used to assess and mitigate associated risks to the organisation.
Attackers are not tied to a specific timezone and are continuously scanning the address space of target organisations, searching for new and possibly unprotected systems to be attached to the network. Transient devices, such as laptops or Bring-Your-Own-Device (BYOD) devices may be out of synchronisation with security updates or already compromised, providing a ripe attack vector. Often, hardware may be installed on the network one evening but not configured and patched with appropriate security updates until the following day, providing an easy target for exploitation. Devices that are not visible from the Internet can be exploited by attackers who have already gained internal access and are hunting for internal pivot points.
Maintaining a comprehensive and up-to-date asset inventory is a fundamental and critical component of RBVM. Modern IT environments encompass on-premises, cloud infrastructure, mobile devices, ephemeral and transient assets, web applications, IoT devices, and more. Asset identification of all connected assets within an organisation is a common baseline requirement in a number of security standards. Maintaining an asset inventory is also the critical first step in the Discovery phase of RBVM, allowing organisations to be more proactive. This document provides guidance to establish an asset inventory.
The first step of RBVM begins with asset discovery to identify and map every asset across the environment. Devices are detected through active scanning with Nessus and passive network analysis with Nessus Network Monitor to build a comprehensive list of assets and provide a clear picture of risk in the environment.
The Asset Inventory & Discovery (SEE) Tenable Vulnerability Management Dashboard and the Asset Inventory & Discovery (SEE) Tenable.sc Dashboard displayed the following provides guidance to establish an asset discovery, including:
-
Actively and passively detected assets
-
Asset discovery statistics
-
Detected web applications
-
Indications for device types (printers, cameras, routers, firewalls, WAPs)
For more information on Asset Discovery and Classification see the Asset Inventory and Discovery Cyber Exposure Study.
Tenable OT
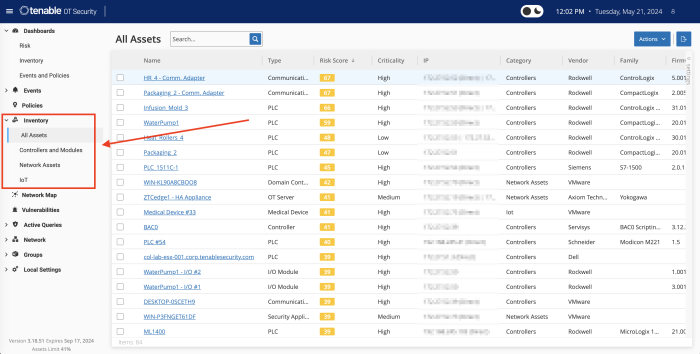
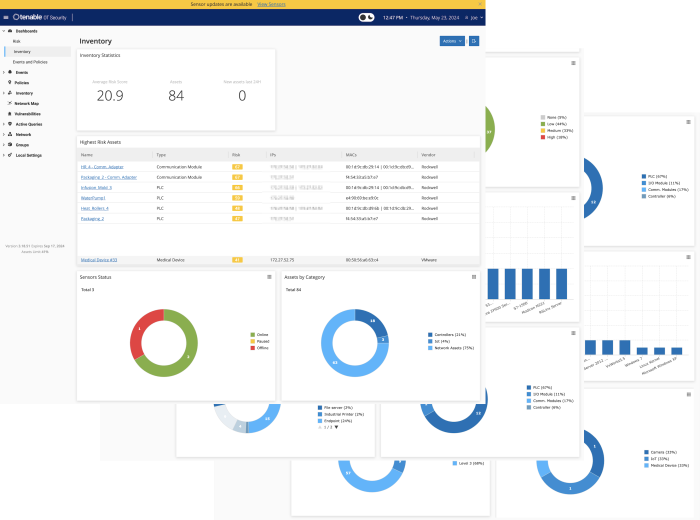
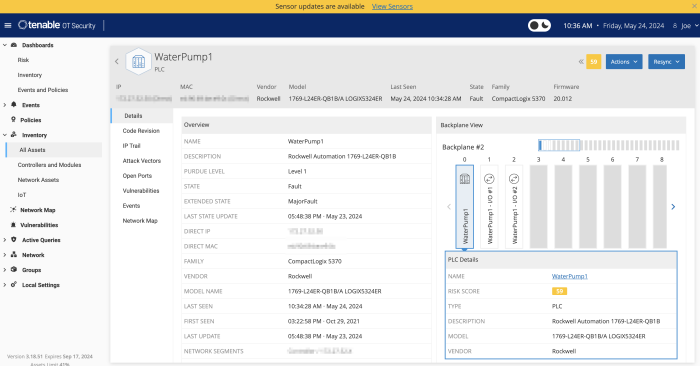
For organisations with industrial controls, identification of IoT assets is accomplished with Tenable OT Security. Native communication protocols are used to query both Information Technology (IT) and Operational Technology (OT) devices in your Industrial Control Systems (ICS) environment in order to identify all of the activities and actions occurring across your network. All the assets in the network appear on the Inventory page. The Inventory page includes details about the asset that enables comprehensive asset management as well as monitoring of the status of each asset and its related events. OT Security collects this data using the Network Detection and Active Query capabilities.
The All Assets page shows data for all types of assets. Subsets of assets are shown on separate screens for each of the following asset types: Controllers and Modules, Network Assets, and IoT.
Tenable OT provides three in product dashboards that display assets in groupings such as by Category, Vendor, Module Type, Purdue Level, and more, facilitating asset management and tracking. Tenable OT Security provides a complete visibility of assets across the environment (IT and OT). A service called "Asset Gateway" receives asset information and tries to consolidate assets that have matching identifiers. In the case of an IT laptop, for example, we show "Sources" of Nessus, Agent, and Tenable OT Security all together. In the case of OT assets, they will not be merged into existing assets.
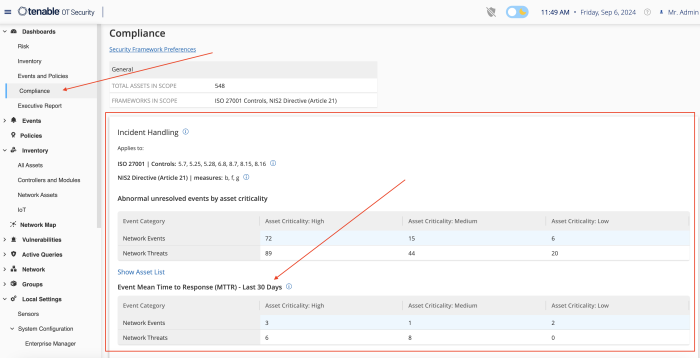
The Vulnerability Handling widget for Tenable OT, located on the compliance dashboard assists in the process of identifying, assessing, reporting, and remediating vulnerabilities. Using this widget, analysts can focus first on assets that have the potential to impact on business operations.
Mean time to Respond (MTTR) is a critical key performance indicator (KPI). A shorter MTTR indicates a more efficient incident resolution process. Minimising downtime and disruptions is crucial for maintaining productivity and service availability. From a Vulnerability Management perspective, OT security personnel can utilise the MTTR for each vulnerability severity within scope, track improvements, and measure SLAs and progress over time. Key items displayed are severity results, high risk assets and MTTR/SLA.
For more information on using Tenable OT Security reference the documentation for your organisation's version here: Getting Started with Tenable OT Security.
Tenable One
Tenable One is an exposure management platform, designed to allow customers to gain visibility across the entire modern attack surface. Tenable One focuses efforts to prevent likely attacks, and accurately communicate cyber risk to optimise business performance.
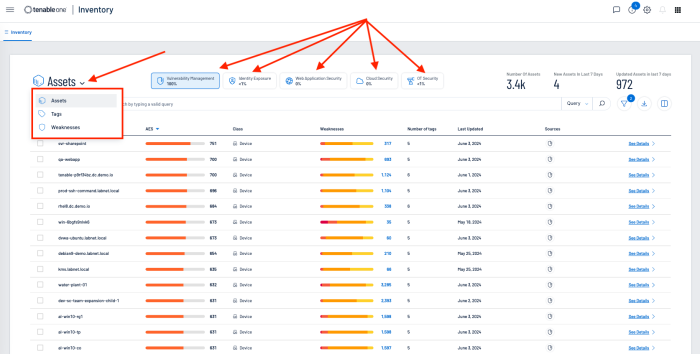
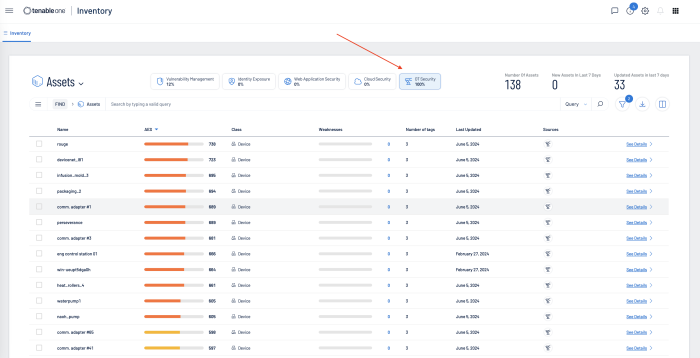
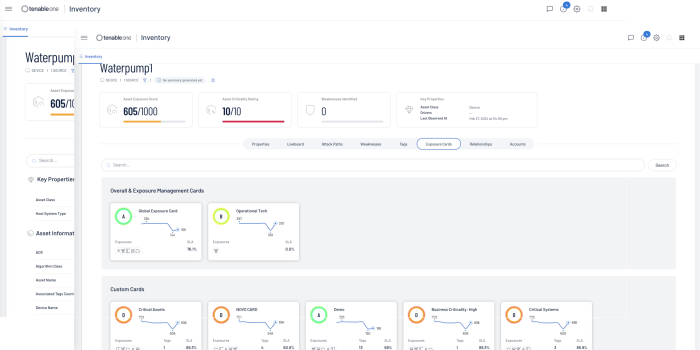
Tenable One Asset Inventory provides a comprehensive view of all assets across the entire attach surface. Sensors pull data from multiple applications across the platform, providing details on all known systems. At the highest level on the Asset Inventory page is shown the Number of Assets identified, New Assets identified in the last 7 days, and assets that have been updated in the last 7 days. Buttons allow you to select any combination of assets (Vulnerability Management, Identity Exposure, Web Application Security, Cloud Security, OT Security).
Displayed in the main body of the page is the Asset, the Asset Exposure Score, Class of device, Weakness, Tags, Last Update Date, Source, and Details. Selecting the Asset drop-down also allows all assets to be displayed by Tag or by Weakness. Weakness is a Common Vulnerability and Exposure (CVE), which is a reference method for publicly known vulnerabilities, maintained by the MITRE Corporation, and funded by the US National Cyber Security Division and the US Department of Homeland Security. Assets can be grouped together, or displayed separately within Vulnerability Management, Identity Exposure, Web Application Security, Cloud Security, and OT Security, by selecting (or deselecting the corresponding icon).
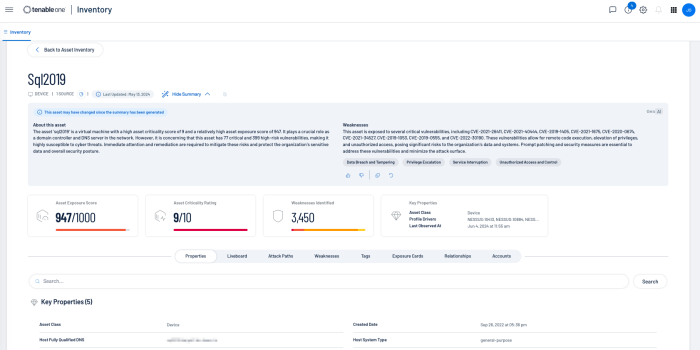
Drilling down into the Asset details provides a wealth of information, including insights into the assets properties, Attack Paths, Weaknesses, Exposure Cards, Relationships, and Accounts. For more information on Tenable One features and benefits, go here.
Once an organisation has determined NIS 2 compliance is required, based on size or categorization as an Essential or Important Entity, steps must be taken to ensure compliance with a number of Articles. In an effort to make compliance with the NIS 2 as easy as possible, this document links NIS 2 articles to pre-established Standards and Security Domains.
Article 21(2) (e): Network and Information Systems Security, including Vulnerability Handling and Disclosure
NIS 2 Article 21(2) (e) references security in network and information systems acquisition, development and maintenance, including vulnerability handling and disclosure.
Security domains define how information is classified, categorised, or administered. The following Security Domains, Sub-Domains, and Measures are related to NIS 2 Article 21(2) (e), and can assist organisations already using other standards and frameworks to comply with NIS 2.
SECURITY DOMAIN: Governance and Ecosystem
SECURITY SUB-DOMAIN: Information System Security Governance & Risk Management
SECURITY MEASURE: Information system security indicators.
In an effort to foster higher consistency and reliability across multiple frameworks and the NIS 2, Article 21(2) (e) can be associated with the ISO 27001, NIST CSF, and ISA/IEC 62443 utilising the following cross-references for vulnerability handling and disclosure. The following cross-references cover the processes and procedures related to asset management, software management, risk management strategies, data security, and the business environment.
CROSS REFERENCES:
The ISO 27001 references sections within Planning, Support, Performance Evaluation, and Annex A, specifically the following sections:
-
ISO 27001 (6.2, 7.1, 7.2, 9, A.12.1.3)
The NIST CSF references the following sections within Identify and Protect.
-
NIST CSF (ID.AM -5, ID.RM-2, 3, PR.IP -7,8, PR.DS -4, ID.BE -5)
The ISA/IEC 62443 references the following sections within System Integrity, and Data Confidentiality.
-
ISA/IEC 62443 (SR 3.4, SR 4.1)
Measurable metrics that provide insights into an organisation's security posture are important indicators in determining the effectiveness of an organisation's vulnerability management program. These indicators may relate to the risk management organisation’s performance, the maintaining of resources in secure conditions, the number of unpatched systems, or the severity ratings of vulnerabilities.
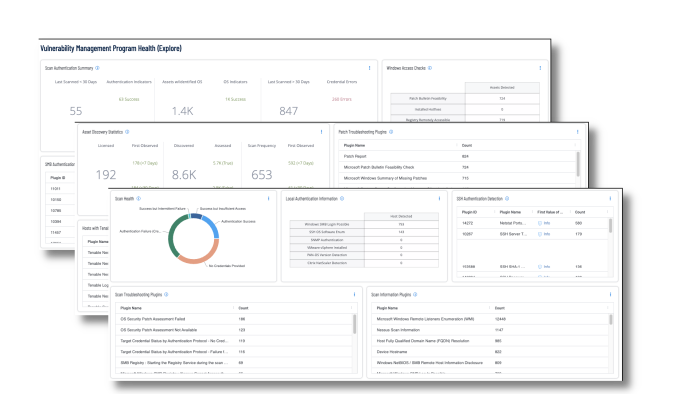
When managing the effectiveness of a vulnerability assessment program within the organisation, dashboards such as the Vulnerability Management Program Health dashboard, for Tenable Vulnerability Management, shown in the following image, helps security operations teams ensure their scanning program is appropriately maintained for an evolving operational technology landscape aligned with business strategy.
There are many factors that can adversely affect the scope and accuracy of scan data, such as failed credentials, network problems, or licence limitations. This dashboard provides security analysts comprehensive information to monitor the health of their scanning program.
Analysts can drill into the summary information displayed in the dashboard to troubleshoot upstream scanning problems that can adversely impact downstream reporting to stakeholders.
For additional in-depth information related to Vulnerability Management, see the Vulnerability Management Cyber Exposure Guide.
Audit and Accreditation
An IT Security Audit is a comprehensive assessment of an organisation’s infrastructure and security posture. The definitive method to find and identifying vulnerabilities within an organisation's network is by conducting authenticated scanning. Authenticated scanning can be defined by connecting to a system and providing credentials in order to gain access to the system. Nessus scans systems by using different network protocols (SSH, SMB, HTTPS, SNMP, etc.) in order to gain access to the remote target asset. For example, logging in to a remote host via SSH using a username and password is a method of authentication. Each remote asset is able to authenticate using several protocols. Assets with more than one authenticatable protocol, for example Windows server running a SQL server, could report both authentication success and failure.
Optionally, Tenable Nessus Agents can also be utilised. Tenable Nessus Agent scans use lightweight, low-footprint programs that are installed locally on hosts. Tenable Nessus Agents collect vulnerability, compliance, and system data, and report that information back to Tenable Nessus Manager or Tenable Vulnerability Management for analysis. Tenable Nessus Agents are designed to have minimal impact on the system and the network, giving you the benefit of direct access to all hosts without disrupting your end users.
Understanding this fact during analysis is key to understanding if the system was successfully scanned or not. While in many cases the successful authentication of an asset may seem binary, there are many examples of successfully scanned systems with authentication failures. The system administrator should review all the failures and understand the services which are enabled on the asset for a complete analysis. The following Security Domains, Sub-Domains, and Measures are related to authentication, and can assist organisations already using other standards to comply with NIS 2. Specifically, information systems security audit and accreditation are the main elements to focus on here.
NIS 2 Article 21(2)(e) references security in network and information systems acquisition, development and maintenance, including audits within vulnerability handling and disclosure.
Security domains define how information is classified, categorised, or administered. The following Security Domains, Sub-Domains, and Measures are related to NIS 2 Article 21(2)(e), and can assist organisations already using other standards and frameworks to comply with NIS 2.
SECURITY DOMAIN: Governance and Ecosystem
SECURITY SUB-DOMAIN: Information System Security Governance & Risk Management
SECURITY MEASURE: Information system security audit (and accreditation)
In an effort to foster higher consistency and reliability across multiple frameworks and the NIS 2, Article 21(2)(e) can be associated with the ISO 27001, NIST CSF, and ISA/IEC 62443 utilising the following cross-references for information security audits and accreditation. The following cross-references cover the processes and procedures related to audits and accreditation, assisting organisations meet the requirements of authenticated/credentialed scans, by confirming that scans are successful.
CROSS REFERENCES (Audit Related):
The ISO 27001 references sections within Planning, Operations, Performance Evaluation, Improvement, Organisational, and Technological Controls, specifically the following items
-
ISO 27001 (6, 8, 9.2, 9.3, 10, A.5.1.2, A.12.7.1, A.18.2)
The NIST CSF references the following sections within Identify, and Detect.
-
NIST CSF (ID.GV -3, 4, ID.RA-1, 3, 4, 5, 6, ID.RM-1, 2, 3, DE.CM -8, DE.DP -5, ID.SC -4, PR.AC-1, PR.PT -1, PR.IP -7, 12, RS.IM -1, 2, RC.IM -1, 2)
The ISA/IEC 62443 references the following sections within Policies and Procedures.
-
ISA/IEC 62443 (SR 2.8, SR 2.9, SR 2.10, SR 2.11, SR 2.12)
NIS 2 Article 21(2)(e) references security in network and information systems acquisition, development, and maintenance, including accreditation of vulnerability audits.
CROSS REFERENCES (Accreditation Related):
The ISO 27001 references sections within Planning, Operations, Performance Evaluation, Improvement, and Organisational Controls, specifically the following items:
-
ISO 27001 (6.1, 8, 9.2, 10.1, A.12.1.1, A.12.7.1)
The NIST CSF references sections within Identify and Detect.
-
NIST CSF (ID.RA-1, 3, 4, 6, ID.RM-1, 2, 3, ID.SC -1, RS.IM -1, 2, PR.IP -7, 12, PR.PT -1, DE.CM -8, RS.MI -3)
NIST CSF The ISA/IEC 62443 references sections within Policies and Procedures.
-
ISA/IEC 62443 (SR 2.8, SR 2.9, SR 2.10, SR 2.11, SR 2.12)
Authenticated (credentialed) and unauthenticated (non-credentialed) scans offer different approaches to vulnerability assessments. They primarily differ in the level of access and permissions granted to the Tenable Nessus scanner. Agent or credentialed scans perform a wider variety of checks than non-credentialed scans, which can result in more accurate scan results. However, there are benefits to an unauthenticated scan as well. For example, unauthenticated scanning is fast, and can detect vulnerabilities that are visible from outside the network, such as open ports, services, and potential entry points for attackers. The choice between the two methods depends on the specific goals of the assessment. Often a combination of both will provide the most comprehensive view of a system's vulnerabilities.
The Authentication Summary dashboard for Tenable Vulnerability Management and the Authentication Summary dashboard for Tenable Security Center brings together plugins used to verify successful authentication of assets during vulnerability scans, providing security administrators visibility into areas of concern so the appropriate actions can be taken.
Authentication is a process of connecting to a system by providing credentials to gain access. Systems are scanned using different network protocols (SSH, SMB, HTTPS, SNMP, etc.) to gain access to the target asset. For example, logging into a remote host via SSH using a username and password is a method of authentication. Each asset can allow authentication using several protocols. Assets with more than one available authentication protocol (for example, a Windows server running a SQL server) could report both authentication success and failure. Understanding this fact during analysis is key to determining if the system was successfully scanned or not. While in many cases the successful authentication of an asset may seem binary, there are many examples of successfully scanned systems with authentication failures. Tenable recommends system administrators review all of the failures and investigate the services which are enabled on the asset for a complete analysis.
Credentialed vulnerability scans are easier with Nessus Agents, because after the agents are installed, they don’t need on-going host credentials. When Nessus Agents are installed (either manually or with a software management system), they are installed under the local SYSTEM account in Windows or root on Unix-based operating systems. The agents then inherit the permissions of the account used for installation so they can perform credential scans, even if the credentials on the system have changed.
Tenable Nessus Agents are designed to have minimal impact on the system and the network, giving organisations the benefit of direct access to all hosts without disrupting your end users. Additionally Tenable Nessus Agents provide extended scan coverage and continuous security, eliminate the need for credential management, reduce network bandwidth, and minimise maintenance.
There are also cases where there is overlap in the intent of the check. For example, if you use OS fingerprinting without credentials in a network-based scan and query the system for the exact version of its OS in a credentialed scan, this overlap heightens the credential findings over the network, since the network version tends to be a best guess.
Local checks are required to ensure the scans are complete and accurate. Users enable local checks by providing credentials with elevated privileges, administrative access, or by deploying Tenable Nessus Agents. Tenable Security Center and Tenable Vulnerability Management requires privileged access to provide a comprehensive assessment of risk on an asset. The more access to a system Tenable Security Center and Tenable Vulnerability Management has, the more complete the vulnerability detection.
Additional information can be located in the Vulnerability Assessment/Scanning section of the Vulnerability Management Cyber Study.
Industrial Control Systems
Article 21(2) (d): (d) Supply chain security, including security-related aspects concerning the relationships between each entity and its direct suppliers or service providers.
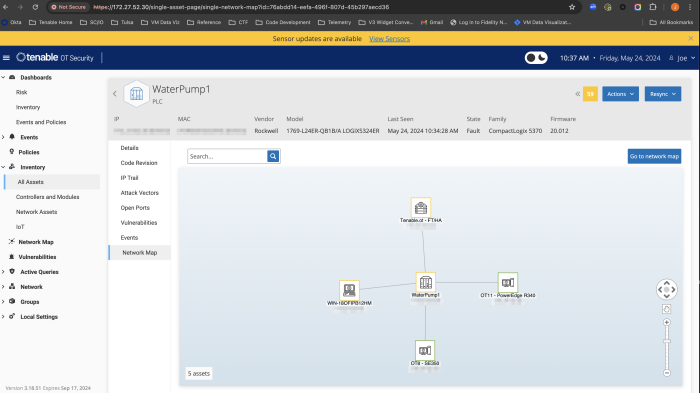
Tenable OT Security maps out assets as well as communication paths. A complete visibility of assets across the environment (IT and OT) is available. Tenable OT Security uses active sensors that can be deployed deep within network segments, to sniff packets and identify the devices communicating on the wire. Once there is an inventory of the assets on the network, Tenable OT Security sends active queries in a safe and secure manner to discover the remaining dormant devices. This discovery process is called hybrid discovery and Tenable is the first to use this methodology for effective asset inventory and mapping.
Information Technology (IT) primarily deals with data processing and communications. Operational Technology (OT) generally refers to the hardware and software that is used to monitor and control devices and processes within industry, manufacturing, energy, transportation, and utility environments. OT can also include industrial control systems (ICS), supervisory control and data acquisition (SCADA) systems, programmable logic controllers (PLC), and other devices used to monitor and control industrial processes.
As technology advances and IT-OT systems converge, new challenges are created and these systems become more vulnerable to cyber threats. Safety and security become increasingly important. Security teams can now get visibility into device make and model, as well as firmware version and status.
Connections can also be mapped to other devices on the network.
Utilising Tenable One, OT Assets can be displayed by selecting the OT Security icon.
Clicking on the See Details link to the right of the page presents additional information on the asset, such as properties, Attack Paths, Weaknesses, Exposure Cards and more.
The following Security Domains, Sub-Domains, and Measures are related to Industrial Control Systems, and can assist organisations already using other standards to comply with NIS 2.
For click here for more information on Tenable One.
NIS 2 Article 21(2) (d) references supply chain security, including security-related aspects concerning the relationships between each entity and its direct suppliers or service providers.
Security domains define how information is classified, categorised, or administered. The following Security Domains, Sub-Domains, and Measures are related to NIS 2 Article 21(2) (d), and can assist organisations already using other standards and frameworks to comply with NIS 2.
SECURITY DOMAIN: Protection.
SECURITY SUB-DOMAIN: IT Security Maintenance.
SECURITY MEASURE: Industrial Control Systems.
In an effort to foster higher consistency and reliability across multiple frameworks and the NIS 2, Article 21(2) (d) can be associated with the ISO 27001, NIST CSF, and ISA/IEC 62443 utilising the following cross-references for Industrial Control Systems. The following cross-references cover the processes and procedures related to supply chain security and other security-related aspects.
CROSS REFERENCES:
The ISO 27001 references sections within Context, Leadership, Support, Operation, Performance Evaluation, and Improvement, specifically the following sections:
-
ISO 27001 (4, 5.2, 5.3, 7, 8, 9.1, A.6.1.1, A.8.1.1, A.8.2.3, A.9, A.11, A.12, A.14, A.15, A.17)
The NIST CSF references the following sections within Identify and Protect.
-
NIST CSF (ID.BE -1, 2, 3, 4, ID.AM -1, 2, 4, 6, ID.GV -2, ID.SC -1, 2, 3, 4, 5, PR.AC -5, PR.PT -4)
The ISA/IEC 62443 references the following sections within nearly every system requirement.
-
ISA/IEC 62443 (SR 1.10, SR 1.13, SR 2.1, SR 2.2, SR 2.3, SR 2.4, SR 2.5, SR 2.6, SR 2.7, SR 2.8, SR 2.9, SR 2.10, SR 2.11, SR 2.12, SR 3.1, SR 3.2, SR 3.3, SR 3.4, SR 3.5, SR 3.8, SR 3.9, SR 4.1, SR 4.2, SR 4.3, SR 5.1, SR 5.2, SR 5.3, SR 5.4, SR.6.1, SR 6.2, SR 7.1, SR 7.2, SR 7.3, SR 7.4, SR 7.6, SR 7.8)
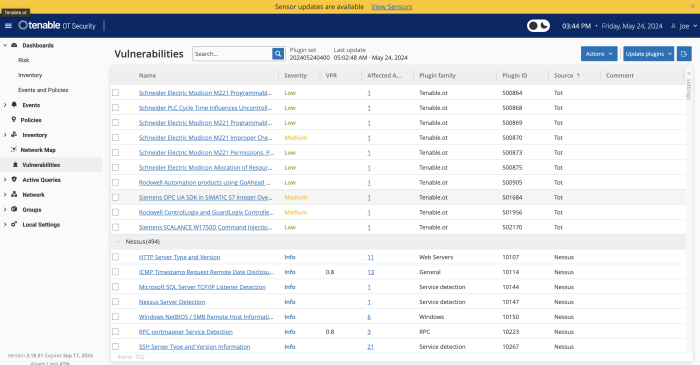
The Vulnerabilities screen within Tenable OT Security displays a list of all vulnerabilities detected by the Tenable Plugins that affect your network and assets. Vulnerabilities include those detected by Tenable OT Sensors, as well as Nessus. You can customise the display settings by adjusting which columns are displayed and where each column is positioned. For an explanation of the customization features, see Management Console User Interface Elements.
The Vulnerabilities page displays the following details:
| Parameter | Description |
|---|---|
| Name | The name of the vulnerability. The name is a link to show the full vulnerability listing. |
| Severity | This score indicates the severity of the threat detected by this Plugin. Possible values: Info, Low, Medium, High, or Critical. |
| VPR | Vulnerability Priority Rating (VPR) is a dynamic indicator of the severity level, which is constantly updated based on the current exploitability of the vulnerability. Tenable generates this value as the output of Tenable Predictive Prioritization, which assesses the technical impact and threat posed by the vulnerability. VPR values range from 0.1-10.0, with a higher value representing a higher likelihood of exploitation. |
| Plugin ID | The unique identifier of the Plugin. |
| Affected Assets | The number of assets in your network affected by this vulnerability. |
| Plugin family | The family (group) with which this Plugin is associated. |
| Comment | You can add free text comments about this Plugin. |
For more information on Tenable OT Security, consult the Getting Started with Tenable OT Security found here.
IT Security Maintenance
Timely and effective remediation remains the Achilles’ heel for too many organisations. Even if security teams identify a concise list of prioritised CVEs, they must work closely with their IT counterparts to address those issues, providing detailed information about how to remediate each vulnerability and why it’s a priority. Without adequate teamwork, the security program is not nearly as effective. Remediation also involves indirect costs, whether that’s IT Operations or Information Security team’s time or the cost of taking down a business-critical system to install and test a patch. The teams are required to efficiently allocate resources where they can have the greatest impact for the least amount of effort.
Once the highest priority vulnerabilities are identified, the operations team needs to take the appropriate action to effectively manage the risk. For each vulnerability, there are three response options — remediate, mitigate, or accept. Which action is chosen for each should be in line with what was previously determined during the initial discovery phase, and as organisations develop a comprehensive understanding of the environment. The terms remediate, mitigate, and accept, can be best defined as:
Remediate
Oftentimes, remediation is used interchangeably with patching, and in some cases, patching may be all that’s required. Something important to note is that typically, applying a patch is just one part of what’s required to remediate a vulnerability. The asset may also require removal or rebuilding the operating system, specific software components may need to be upgraded, or there could be a configuration error that needs to be corrected. Once the vulnerability is verified to have been fully remediated, the amount of risk associated with the vulnerability is fully removed from the environment.
Mitigate
Mitigation employs other technologies to reduce the risk of a given vulnerability. This is different from remediation because with mitigation nothing has been done to actually fix the vulnerability itself. Instead, organisations are accounting for other mitigating factors that neutralise some or all of the risk posed by the vulnerability. For example, organisations may have firewall rules in place that effectively block an exploit from accessing sensitive data. To account for this mitigating factor, organisations would reduce the severity of the vulnerability accordingly.
Accept
Risk acceptance is consciously deciding not to take any action at all. This may be done for a variety of reasons. For example, during the discovery phase, management may have determined some assets are so business-critical they can’t afford to take them down for maintenance unless the vulnerability is also business-critical. In other cases, the cost of the fix may be greater than the cost associated with a successful exploit. Regardless of the reason, when organisations choose to accept risk, the Vulnerability Management platform may allow you to remove the risk score from reports or set the score to “0." However, organisations need to understand that while the vulnerability may no longer be immediately visible, the actual risk still remains in your environment.
NIS 2 Article 21(2) (e) references network and information systems security, including vulnerability handling and disclosure.
Security domains define how information is classified, categorised, or administered. The following Security Domains, Sub-Domains, and Measures are related to NIS 2 Article 21(2) (e), and can assist organisations already using other standards and frameworks to comply with NIS 2.
SECURITY DOMAIN: Protection.
SECURITY SUB-DOMAIN: IT Security Maintenance.
SECURITY MEASURE: IT security maintenance procedure.
In an effort to foster higher consistency and reliability across multiple frameworks and the NIS 2, Article 21(2) (e) can be associated with the ISO 27001, NIST CSF, and ISA/IEC 62443 utilising the following cross-references for IT security maintenance. The following cross-references cover the processes and procedures related to IT security maintenance procedures.
CROSS REFERENCES:
The ISO 27001 references sections within Support, Operations, Improvement, and Technological Controls, specifically the following sections:
-
ISO 27001 (7.5.3, 8.1, 10.1, A.11.2.4, A.12.1.2, A.12.6.1, A.14.1.1, A 14.2, A.15.2.2)
The NIST CSF references the following sections within Protect.
-
NIST CSF (PR.MA -1, 2, PR.IP -1, 2, 3,4, 7, PR.DS -3, 4, ID.SC -4)
The ISA/IEC 62443 references the following sections within Audit Logs and Network and Security Configuration Settings.
-
ISA/IEC 62443(SR 3.1, SR 3.3, SR 3.4, SR 3.8, SR 6.1, SR 7.6)
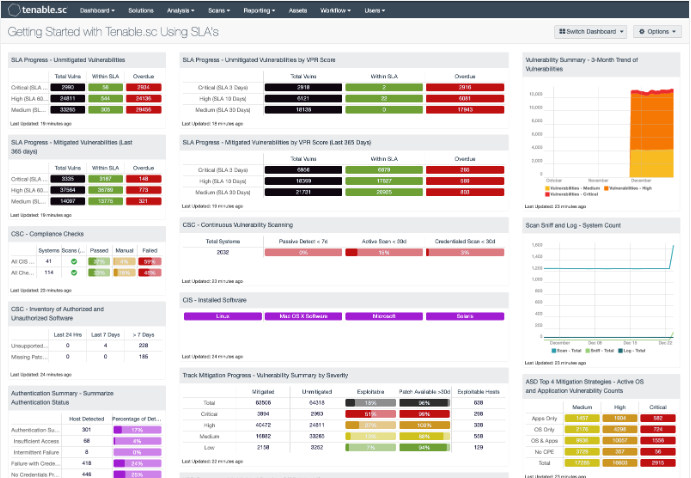
Service Level Agreements (SLA) are often utilised in the IT industry to outline or track expectations between a service provider and a customer. An SLA is a great; and often used, option to track other items within an organisation, such as patching and vulnerability remediation progress. Tracking SLA progress is a definitive method to demonstrate the success of an organisation’s remediation efforts.
Service Level Agreements often change from one organisation to the next, however meeting SLAs is a common issue among organisations industry wide. Tenable.sc provides a vast array of data that provides vulnerability management SLA metrics, but where can organisations get started? This dashboard is commonly used by the sales team at Tenable to help coach organisations to meet SLAs. The components in this dashboard are grouped in 3-series, which provide a CISO and Risk Manager with a starting point for SLA analysis.
https://www.tenable.com/sc-dashboards/getting-started-with-tenable-sc-using-slas
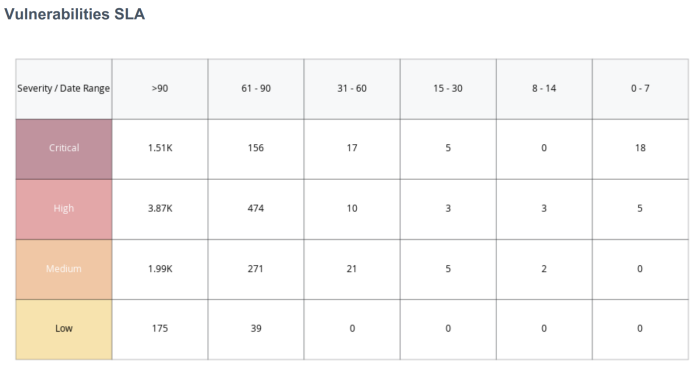
Within Tenable Vulnerability Management, the Vulnerability SLA widget enables organisations to track and report on their remediation efforts over time and severity.
Vulnerabilities are displayed by severity and time to remediate from less than 7 days to over 90 days. Tenable recommends prioritising remediation of exposures that pose the greatest risk to the organisation. This widget enables organisations to identify the vulnerabilities that are not being remediated quickly, or outside of established timeframes. Organisations with an effective vulnerability management program have critical vulnerabilities displayed in the far right three columns, representing remediations occurring within 30 days or less. Vulnerabilities that pose less risk of exposure could have higher counts in the middle of the matrix in the 30-90 day time period. Numbers in the far left of the matrix depict vulnerabilities that are remediated after 90 days have passed.
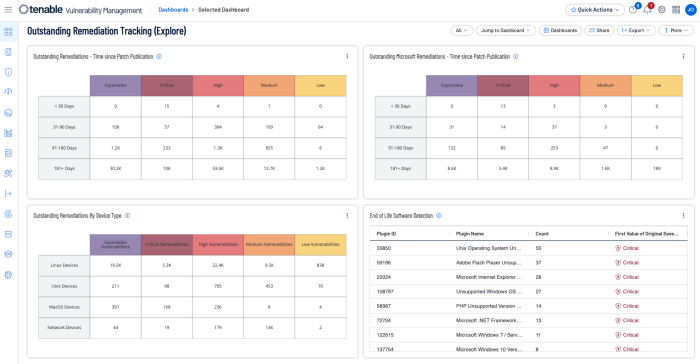
Unpatched assets expose organisations to vulnerabilities that are actively being exploited. End of life assets may pose the greatest risk since they are unsupported and no longer receiving security updates or support from the vendor. Tenable provides the Outstanding Remediation Tracking dashboard for Tenable Vulnerability Management and Outstanding Remediations Tracking.
The Outstanding Remediations Tracking dashboard provides risk guidance using the “Remediation Summary” tool. This tool works by employing a concept called “top patch”. Tenable.sc uses proprietary technology to identify a chain of patches. The first patch in the chain is called the “top patch”. If the “top patch” is applied, all subsequent vulnerabilities will also be remediated at the same time. Using both the Remediation Summary tool and “Patch Report” plugin, the organisation can better plan remediation efforts. Within Tenable Vulnerability Management several filters are used including those for unsupported products, patch publication date ranges.
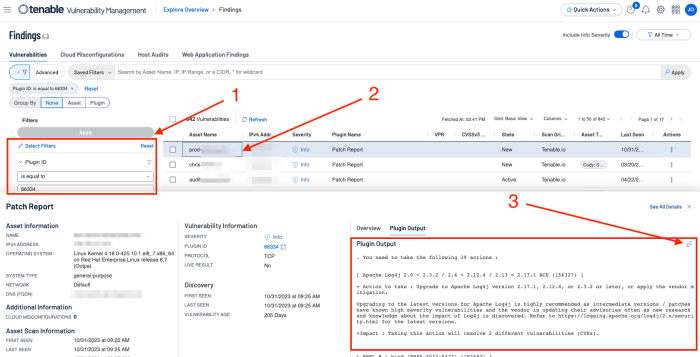
The Nessus "Patch Report" plugin (66334) summarises all of the missing patches and general remediation actions required to remediate the discovered vulnerabilities on a given host. Instead of counting the number of vulnerabilities, the plugin lists applications that need to be upgraded. The approach is not only much easier for IT administrators to consume, but the count of applications provides a measure of how much "work" is required to secure a system.
Within Tenable Vulnerability Management, analysts can create a filter for plugin 66334 within the filters component on the Findings page as shown following (1). Once results have appeared to select an asset (2) by clicking on the asset name opens the details window at the bottom of the page. Selecting Plugin Output reveals the detailed Actions to undertake, including the Impact those actions have. The information can easily be exported to the clipboard by clicking the copy (3) icon. An additional filter can be added to change the State filter to “Fixed” to review patches that have previously been resolved.
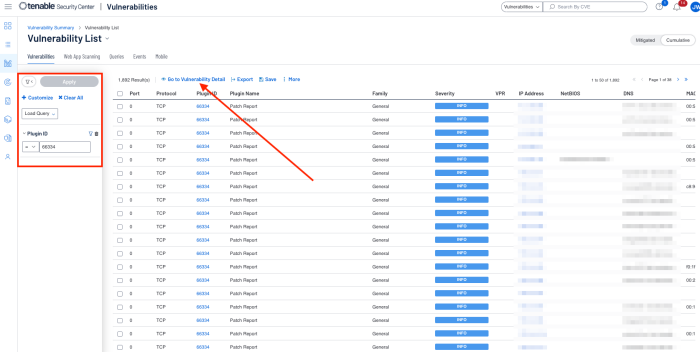
The steps are similar if using Tenable Security Center, however they vary slightly. From the Analysis tab, choose Vulnerabilities. Create a filter for plugin 66334. After the results are displayed choose to go to Vulnerability Detail.
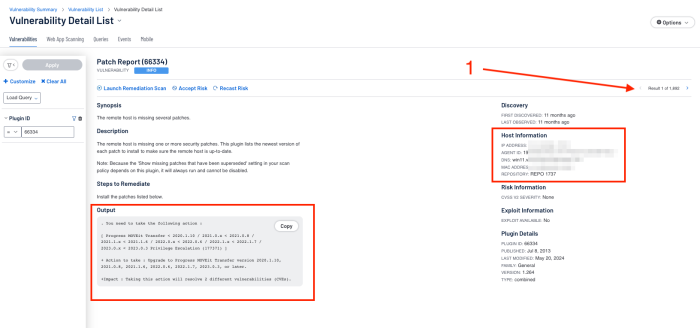
The Vulnerability Detail is shown with the detailed Actions to undertake, including the Impact those actions have. The information can easily be exported to the clipboard by clicking the copy icon. To select the next detail click next (1). An additional filter can be added to change the state to “Mitigated” and “Previously Mitigated” to review patches that have previously been resolved.
_thumb_700_0.png)
_thumb_700_0.png)
_thumb_700_0.png)
_thumb_700_0.png)
_thumb_700_0.png)