Tenable One: Okta IdP
One of the most common IdPs used to configure SAML with Tenable One is Okta. The following steps guide you through the configuration process from start to finish.
Manual configuration requires the following:
-
Login URL: A custom URL provided by Tenable in the following format:
https://cloud.tenable.com/saml/login/PLACEHOLDERTip: FedRAMP environments use the following custom URL format: https://fedcloud.tenable.com/saml/login/PLACEHOLDER -
Audience URI (SP Entity ID): A custom ID provided by Tenable during SAML configuration in the following format:
TENABLE_IO_PLACEHOLDER -
A certificate within the SAML metadata object that matches the data originally sent to Tenable.
Note: Tenable does not support the use of multiple certificates and only extracts the first certificate from the metadata object. If the object includes multiple certificates, you must specify which certificate to use if it is not the first one listed.
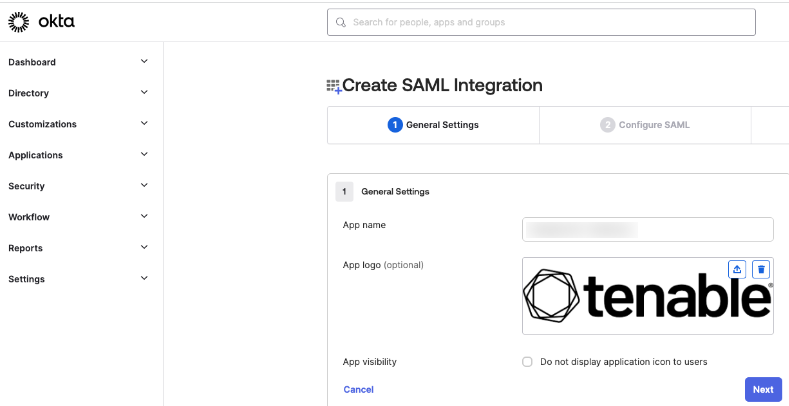
Okta: Create Initial Application Integration
To create an application integration in Okta:
-
In your browser, navigate to the Okta Admin portal.
-
In the left navigation menu, click Applications > Applications.
The application window appears.
-
Click Create App Integration.
The Create a new app integration window appears.
-
Select the SAML 2.0 radio button.
-
Click Next.
The General Settings options appear.
-
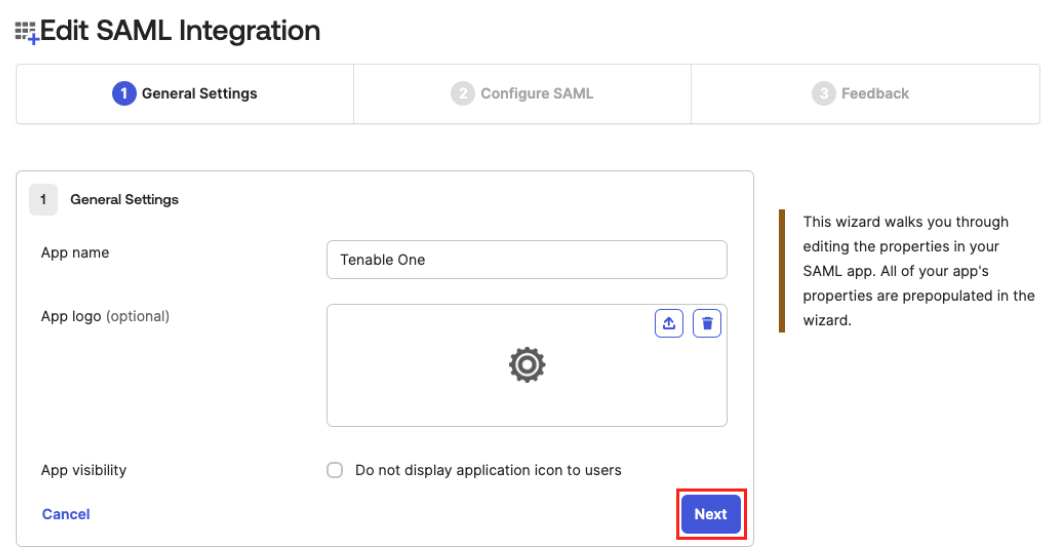
In the App name text box, type a name for your application.
-
(Optional) To add a custom logo for the application, in the App logo section, upload a .png, .jpeg, or .gif file.
-
Click Next.
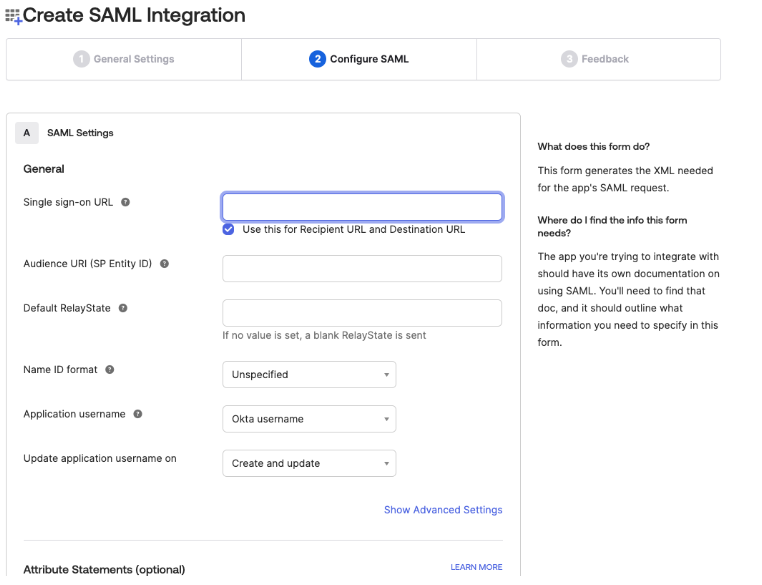
The Configure SAML options appear.
-
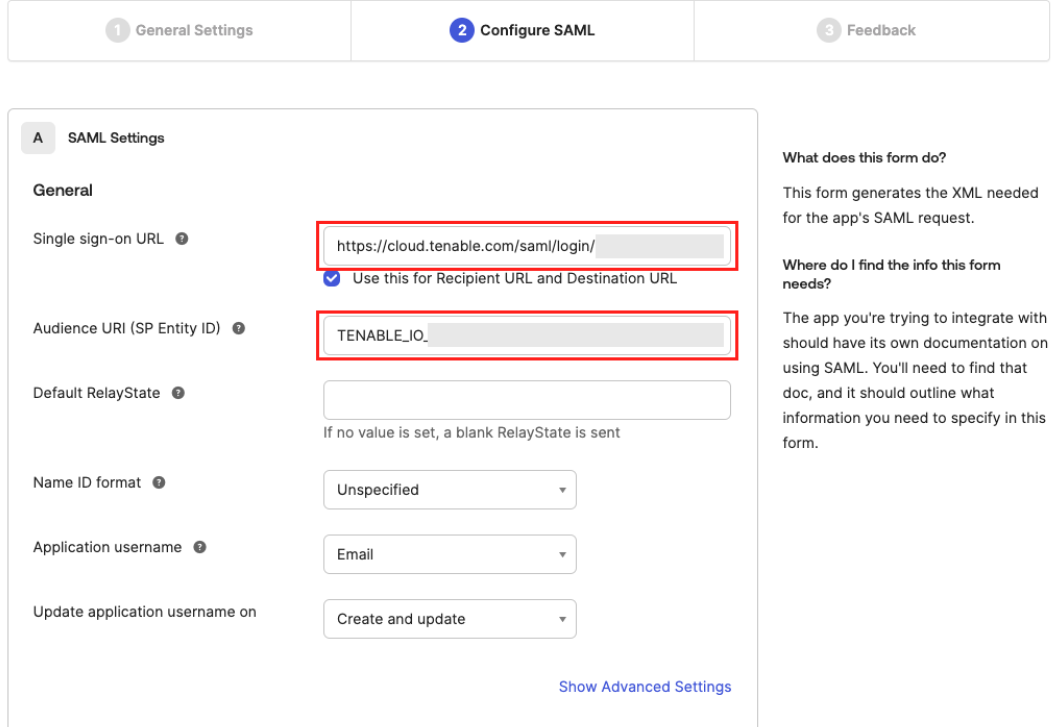
In the Single sign-on URL text box, type the following placeholder URL:
https://cloud.tenable.com/saml/login/PLACEHOLDERNote: You will later replace PLACEHOLDER with a unique UUID for the SAML configuration. This link is case-sensitive. -
In the Audience URI (SP Identity ID) text box, type the following placeholder text:
TENABLE_IO_PLACEHOLDERNote: You will later replace PLACEHOLDER with a unique UUID for the SAML configuration. -
In the Application username drop-down, select Email.
-
Leave all other default settings. For reference:
-
The Use this for Recipient URL and Destination URL check box is selected.
-
The Default RelayState text box is blank.
-
The Name ID format drop-down is set to Unspecified.
-
The Update application username on drop-down is set to Create and update.
-
-
Click Next.
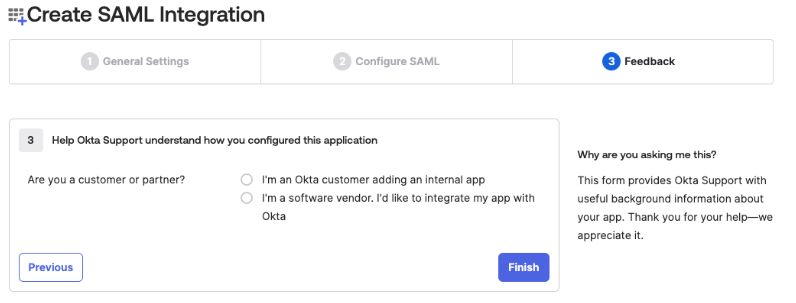
The Feedback options appear.
-
(Optional) Provide any feedback you want to include.
-
Click Finish.
Okta saves your application configuration and the new application's Sign On settings page appears.
-
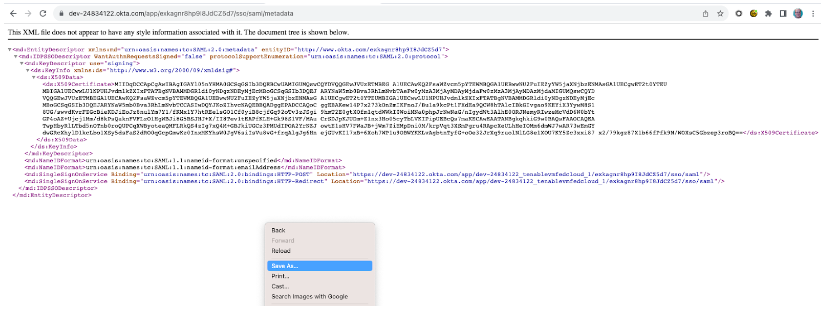
Under SAML 2.0 > Metadata details > Metadata URL, click Copy.

-
In a new browser tab, navigate to the copied URL.
The application's metadata appears in XML format.
-
In your browser, using the Save Page As option, save the resulting file as metadata.xml.
Your browser downloads the metadata.xml file.
Tenable One SAML Configuration
Once you have downloaded your medata.xml file, you can use it to configure SAML in Tenable One. You can configure this directly in the Tenable Vulnerability Management application.
To set up the Tenable One SAML configuration:
- In your browser, navigate to Tenable One.
- On the Workspace page, click Tenable Vulnerability Management.
The Tenable Vulnerability Management user interface appears.
-
In the upper-left corner, click the
 button.
button. The left navigation plane appears.
-
In the left navigation plane, click Settings.
The Settings page appears.
-
Click the SAML tile.
The SAML page appears.
-
In the action bar, click
 Create.
Create.The SAML Settings page appears.
-
Do one of the following:
 To provide configuration details by uploading the metadata.xml file from your IdP:
To provide configuration details by uploading the metadata.xml file from your IdP:
-
In the first drop-down box, select Import XML.
Note: Import XML is selected by default.
-
The Type drop-down box specifies the type of identity provider you are using. Tenable One supports SAML 2.0 (for example, Okta, OneLogin, etc.).
This option is read-only. -
Under Import, click Add File.
A file manager window appears.
-
Select the metadata.xml file.
The metadata.xml file is uploaded.
 To manually create your SAML configuration using data from the metadata.xml file from your IdP:
To manually create your SAML configuration using data from the metadata.xml file from your IdP:
-
In the first drop-down box, select Manual Entry.
A SAML configuration form appears.
-
Configure the settings described in the following table:
Settings Description Enabled toggle A toggle in the upper-right corner that indicates whether the SAML configuration is enabled or disabled.
By default, the Enable setting is set to Enabled. Click the toggle to disable SAML configuration.
Type Specifies the type of identity provider you are using. Tenable One supports SAML 2.0 (for example, Okta, OneLogin, etc.).
This option is read-only.Description A description for the SAML configuration. IdP Entity ID The unique entity ID that your IdP provides.
Note: If you want to configure multiple IdPs for a user account, create a new configuration for each identity provider with separate identity provider URLs, entity IDs, and signing certificates.
IdP URL The SAML URL for your IdP. Certificate Your IdP security certificate or certificates.
Note: Security certificates are found in a metadata.xml file that your identity provider provides. You can copy the content of the file and paste it in the Certificate box.
Authentication Request Signing Enabled A toggle that indicates whether authentication request signing is enabled.
When this toggle is enabled, if:
-
a user is logged in via SAML and their session expires
-
a user logs out and tries to log back in directly via the Tenable One interface rather than their IdP
Tenable One automatically signs the SAML authentication request that is sent to the IdP to log the user back in.
Note: The authentication request can only be validated if the IdP is also configured to accept this setting. For more information, see the following resources:- Manage Signing Certificates in Okta
- Enforce Signed SAML Authentication Requests in Microsoft Entra ID
- Edit a SAML Application in Ping Identity (Enforce Signed AuthnRequest option)
User Auto Provisioning Enabled A toggle that indicates whether automatic user account creation is enabled or disabled. Automatic account provisioning allows users with an account for the IdP named in the SAML configuration to create a Tenable Vulnerability Management account the first time they log in via the IdP.
Note: This option only appears during intial configuration if the setup is manual. Otherwise, you must edit the configuration after initial setup to enable this option.IdP Assigns User Role at Provisioning To assign a user role during provisioning, enable this toggle. In your SAML identity provider, add an attribute statement with userRoleUuid as the attribute name and the user role UUID as the attribute value. To obtain the UUID for a user role, go to Settings > Access Control > Roles.
Note: This option only appears during intial configuration if the setup is manual. Otherwise, you must edit the configuration after initial setup to enable this option.IdP Resets User Role at Each Login To assign a role each time a user logs in, overwriting the current role with the one chosen in your IdP, enable this toggle. In your SAML identity provider, add an attribute statement with userRoleUuid as the attribute name and the user role UUID as the attribute value.
To obtain the UUID for a user role, go to Settings > Access Control > Roles.
Note: This option only appears during intial configuration if the setup is manual. Otherwise, you must edit the configuration after initial setup to enable this option.Group Management Enabled Enable this toggle to allow the Tenable One SAML configuration to manage user groups. You must enable this toggle for the Managed by SAML option to function successfully. -
-
-
Click Save.
Tenable Vulnerability Management saves your SAML configuration and you return to the SAML page.
-
In the row for the SAML configuration you just created, click the
 button.
button.An actions menu appears.
-
Click Download SAML SP metadata.
Your browser downloads the metadata.xml file. You can now use this file for final configuration in your IdP.
Optional: Configure One or More User Groups to Automatically Add a User upon SAML Login
User groups allow you to manage user permissions for various resources in Tenable One. When you assign users to a group, the users inherit the permissions assigned to the group. When you enable the Managed by SAML option for a user group, Tenable One allows you to automatically add any user that logs in via SAML to that group.
Before you begin:
Ensure you've enabled the Group Management Enabled toggle when configuring the SAML settings within Tenable One.
To enable the Managed by SAML option:
-
In Tenable Vulnerability Management, in the upper-left corner, click the
 button.
button. The left navigation plane appears.
-
In the left navigation plane, click Settings.
The Settings page appears.
-
Click the Access Control tile.
The Access Control page appears.
-
Click the Groups tab.
The Groups page appears.
-
In the user groups table, click the user group to which you want to automatically add your SAML users.
The Edit User Group page appears.
-
In the General section, select the Managed by SAML check-box.
-
Click Save. Tenable Vulnerability Management saves your changes. Once you configure the related claim within your IdP, any time a user logs in via your SAML configuration, Tenable One automatically adds them to the specified user group.
Okta: Configure Final Application Integration and Upload Metadata
Now that you have downloaded the completed metadata file, you can use that file to finalize the Tenable application configurations in Okta.
-
In your browser, navigate to the Okta Admin portal.
-
In the left navigation menu, click Applications > Applications.
The Applications page appears.
-
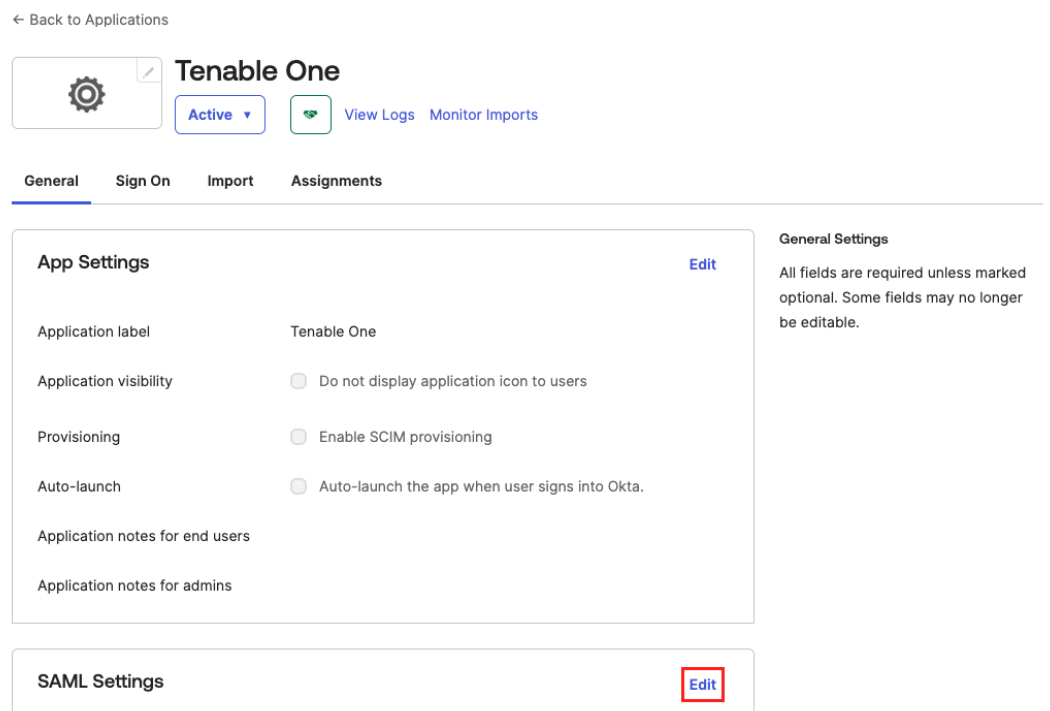
Select the application you previously created.
The General page appears.
-
In the SAML Settings section, click Edit.
The General Settings page appears.
-
Click Next.
The Configure SAML options appear.
-
In the Single sign-on URL text box, replace the previously submitted placeholder with the URL listed in the metadata.xml file that you downloaded from Tenable One.
Tip: This URL is in the following format: https://cloud.tenable.com/saml/login/PLACEHOLDER. -
In the Audience URI (SP Identity ID) text box, replace the previously submitted placeholder with the ID listed in the metadata.xml file that you downloaded from Tenable One.
Tip: This ID is in the following format: TENABLE_IO_PLACEHOLDER. -
Click Next.
The Feedback options appear.
-
Click Finish.
Okta saves your changes to the application.
Assign Users and/or Groups to the Okta Application
To assign the application to your users or groups:
-
In your browser, navigate to the Okta Admin portal.
-
In the left navigation menu, click Applications > Applications.
The Applications page appears.
-
Select the application you previously created.
The General page appears.
-
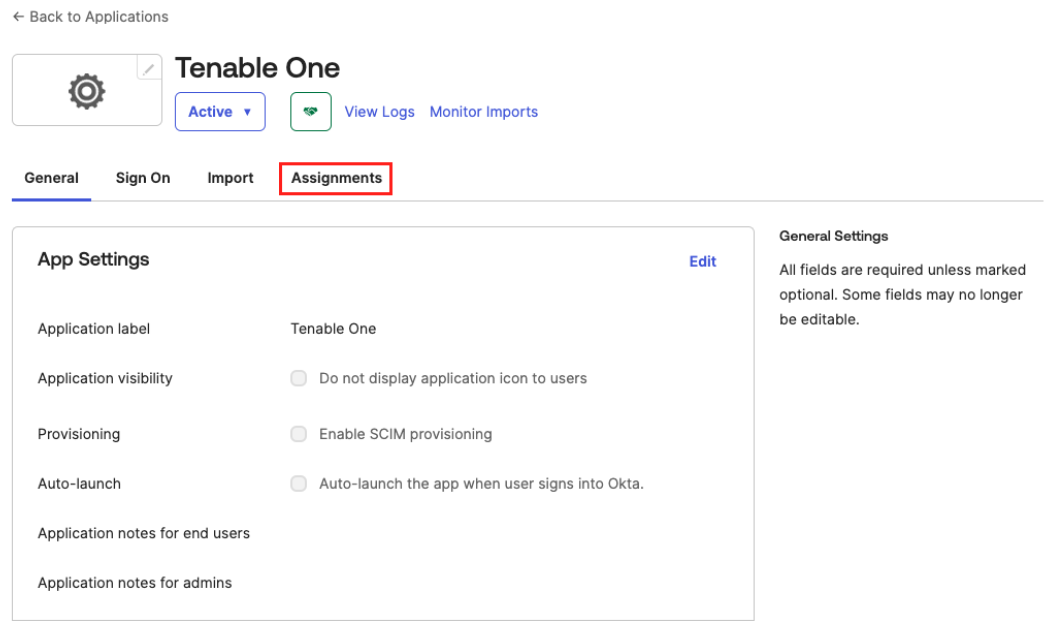
Click the Assignments tab.
The Assignments page appears.
-
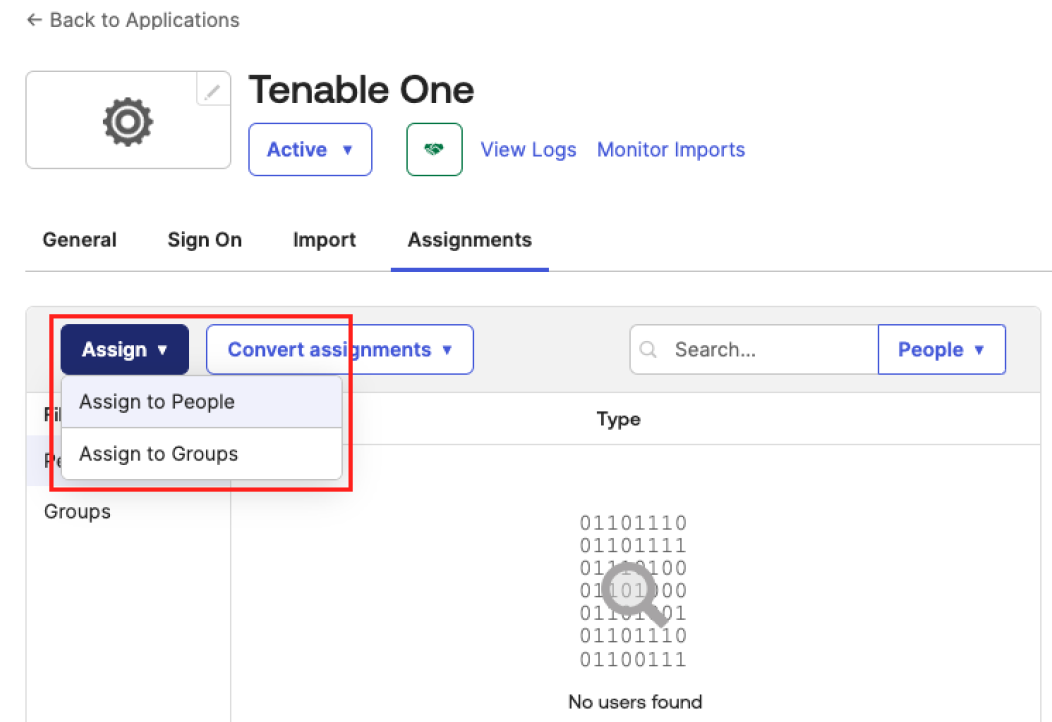
Click the Assign button and, in the drop-down, select one or both of the following:
-
Assign to People — Any assigned users will have access to this application within their Okta My Apps dashboard, and will be able to login to Tenable One.
-
Assign to Groups — Any users within assigned groups will have access to this application within their Okta My Apps dashboard, and will be able to login to Tenable One.
Important: If you’ve opted to optionally Configure One or More User Groups to Automatically Add a User upon SAML Login, ensure any assigned group name in Okta matches the user group name within Tenable One. If the names do not match, the user and/or user group link will fail.An Assign window appears.
-
-
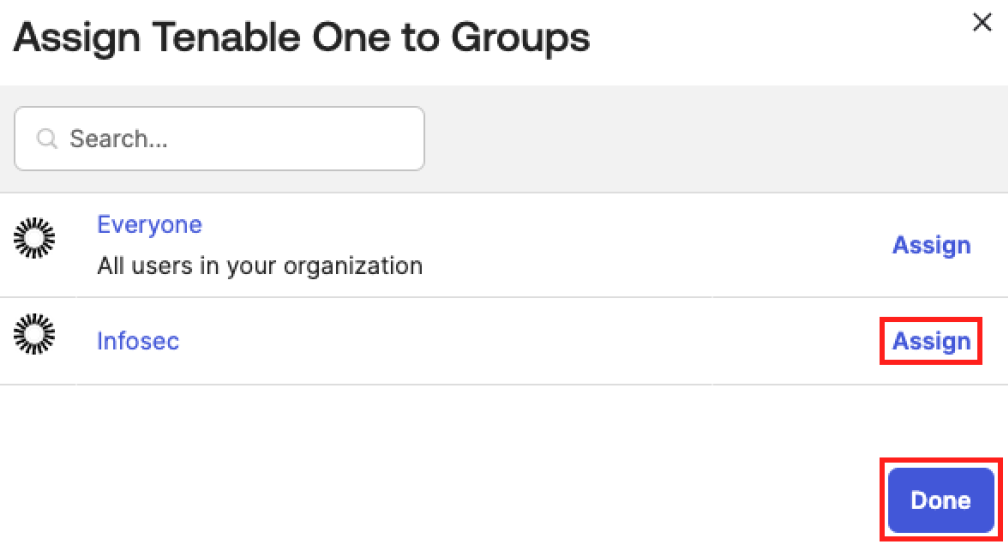
Next to the user or group to which you want to assign the application, click Assign.
-
Repeat for each user or group to which you want to assign the application.
-
Click Done.
Okta saves your changes, and your configuration is ready for use.
Optional: Finalize Configuration for Managed by SAML Group Option
If you enabled the Managed by SAML option to automatically add any user that logs in via SAML to a user group, then you must configure a related group claim within the Okta IdP.
To configure the IdP group claim:
-
In your browser, navigate to the Okta Admin portal.
-
In the left navigation menu, click Applications > Applications.
The Applications page appears.
-
Select the application you previously created.
The General page appears.
-
In the SAML Settings section, click Edit.
The General Settings page appears.
-
Click Next.
The Configure SAML options appear.
-
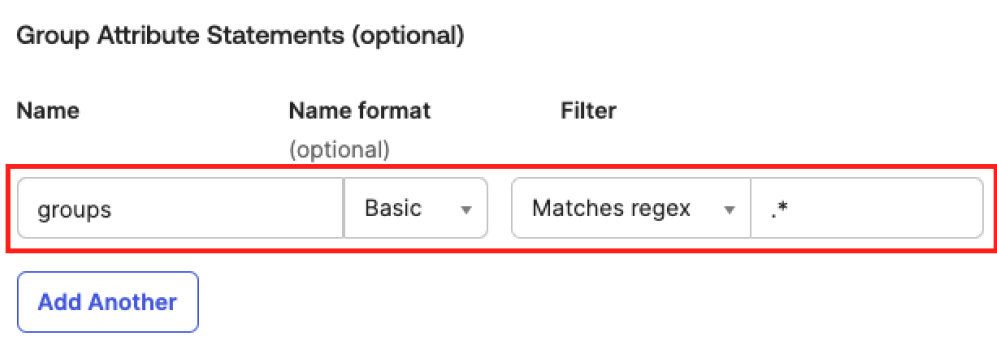
Do one of the following:
-
Click Next.
The Feedback options appear.
-
Click Finish.
Any time a user assigned to this Okta group name logs in via your SAML configuration, Tenable One automatically adds them to the specified matching user group within Tenable One.
Optional: Finalize Configuration for Managed by SAML Role Option
Roles allow you to manage privileges for major functions in Tenable One and control which Tenable One resources users can access.
If you enabled the IdP Assigns User Role at Provisioning and/or IdP Resets User Role at Each Login (to automatically add and/or assign any user that logs in via SAML to a user role) settings, then you must complete the following steps within Okta:
To configure the managed by SAML role option:
-
In your browser, navigate to the Okta Admin portal.
-
In the left navigation menu, click Applications > Applications.
The Applications page appears.
-
Select the application you previously created.
The General page appears.
-
In the SAML Settings section, click Edit.
The General Settings page appears.
-
Click Next.
The Configure SAML options appear.
-
Do one of the following:
-
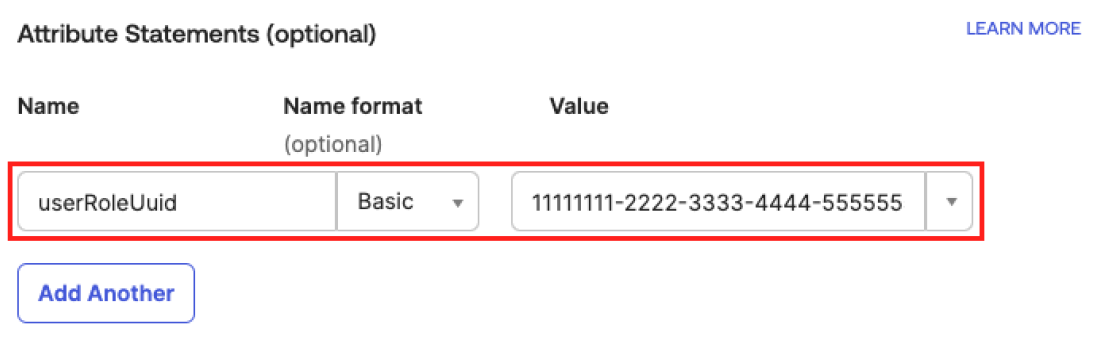
 To map all users assigned to the application to the same role:
To map all users assigned to the application to the same role:
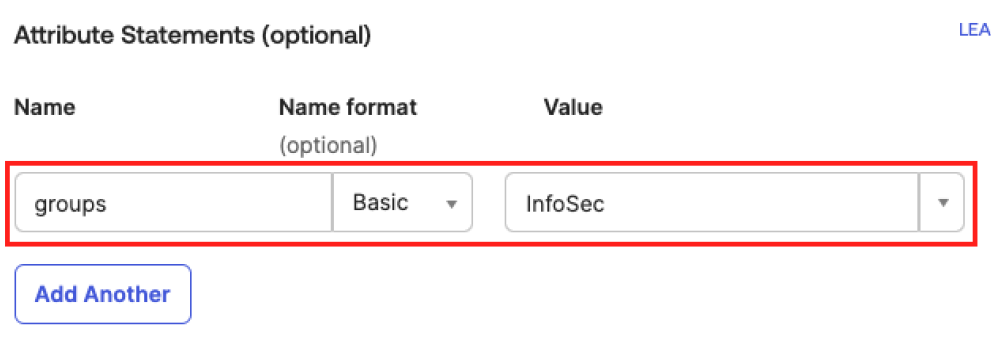
In the Attribute Statements section, insert the following values:
-
In the Name text box, type userRoleUuid.
-
In the Name format drop-down, select Basic.
-
In the Value text box, type the UUID of the Tenable user role.
Tip: Tenable user role UUIDs can be found in Tenable Vulnerability Management, in the Settings > Access Control > Roles table. -
Click Next.
The Feedback options appear.
-
Click Finish.
-
-
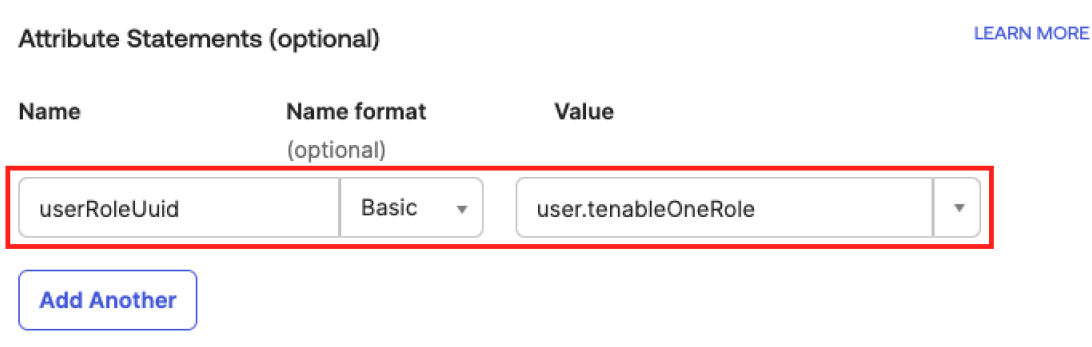
 To map individual users assigned to the application to different roles:
To map individual users assigned to the application to different roles:
In the Attribute Statements section, insert the following values:
-
In the Name text box, type userRoleUuid.
-
In the Name format drop-down, select Basic.
-
In the Value text box, type user.tenableOneRole.
-
Click Next.
The Feedback options appear.
-
Click Finish.
-
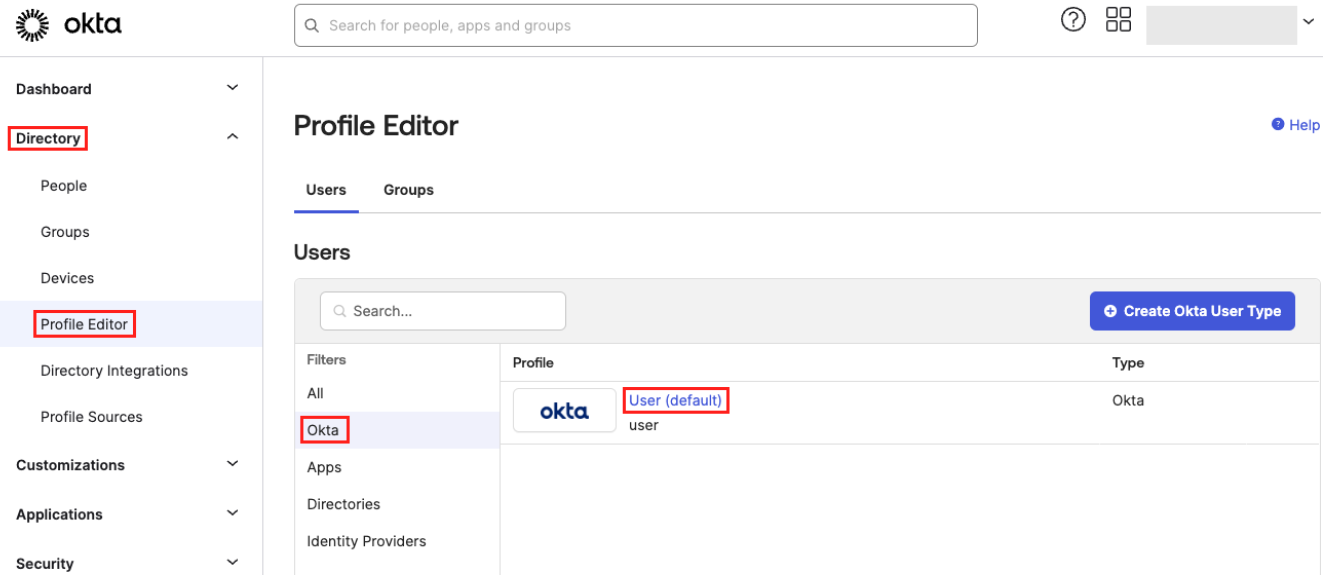
In the left navigation menu, click Directory > Profile Editor.
The Profile Editor page appears.
-
In the Filters section, click Okta.
-
Click the User (default) profile to edit it.
The Profile Editor appears.
-
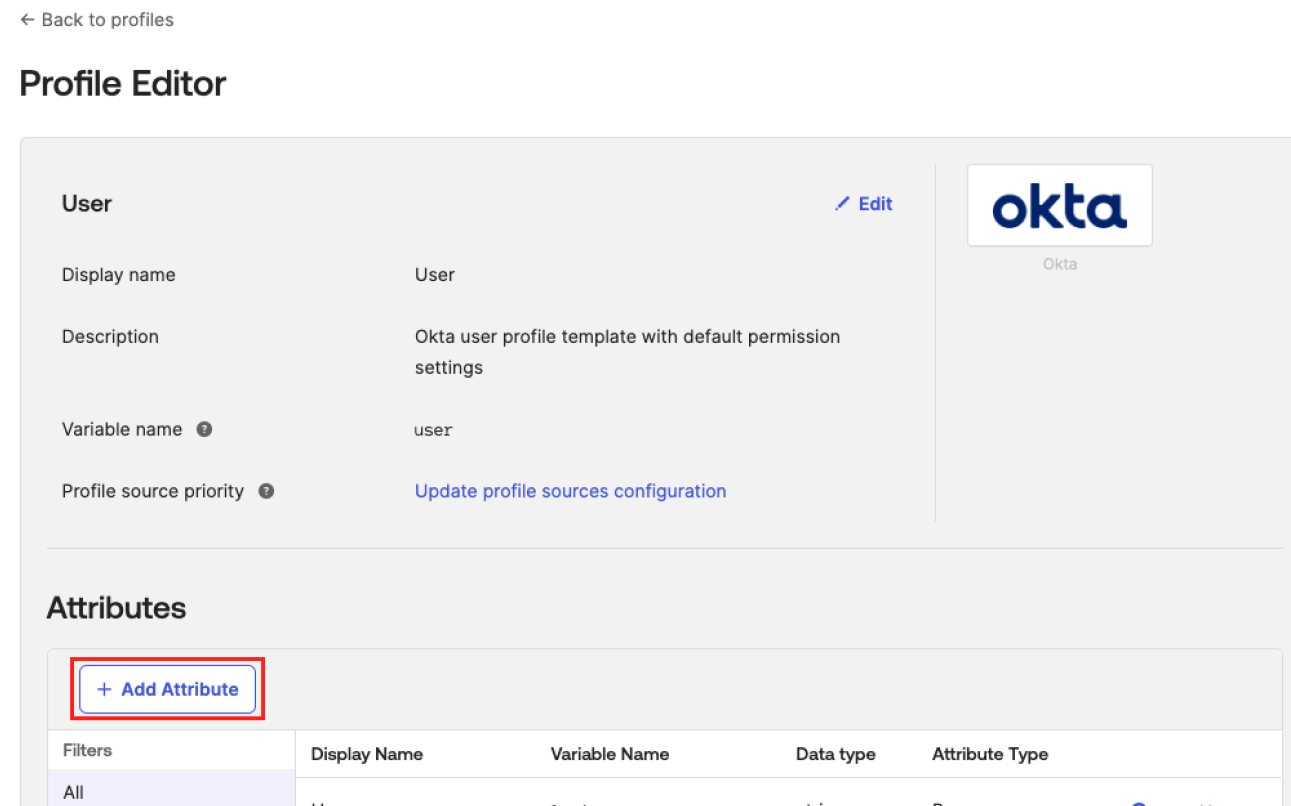
In the Attributes section, click Add Attribute.
The Add Attribute page appears.
-
Modify the following fields:
-
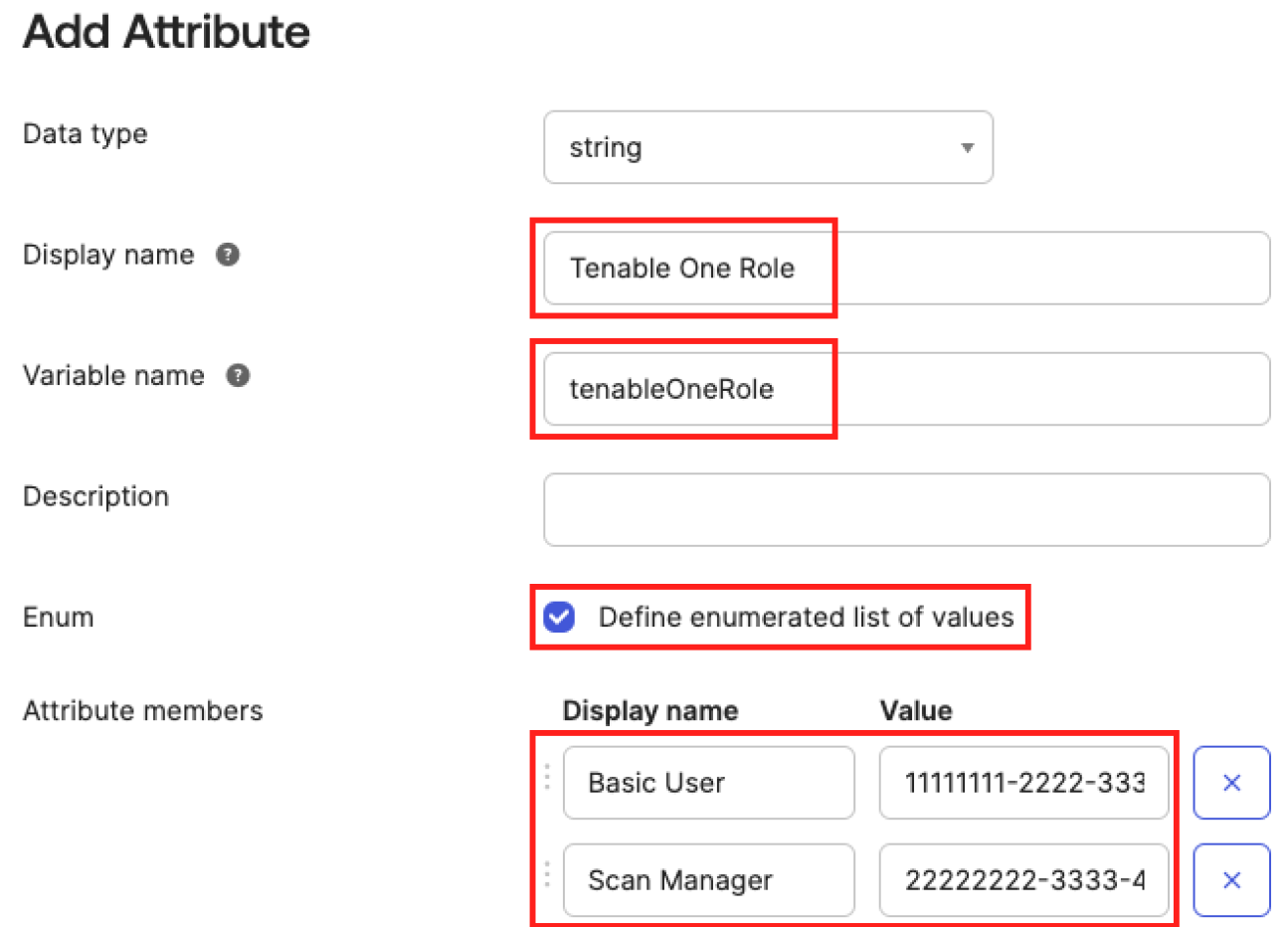
In the Display name text box, type a descriptive name to display for the attribute in the Admin Console (for example, Tenable One Role).
-
In the Variable name text box, type an attribute name for the attribute that can be referenced in mappings (for example, tenableOneRole).
Tip: Variable names should only contain alphanumeric characters and underscores, and should not start with a digit. Once created, Okta prepends "user." to the chosen variable name. If you configure a variable name other than user.tenableOneRole, refer back to step c in this section and ensure the variable name matches.
For more information on custom user attributes, see Add custom attributes to an Okta user profile. -
Select the Enum check box.
-
In the Attribute Members section:
-
In the Display name text box, type the user role you’re interested in mapping (for example, Basic User).
-
In the the Value text box, type the UUID of the corresponding Tenable user role.
Tip: Tenable user role UUIDs can be found in Tenable Vulnerability Management, in the Settings > Access Control > Roles table. -
To map more roles, select Add Another and repeat the process.
-
-
-
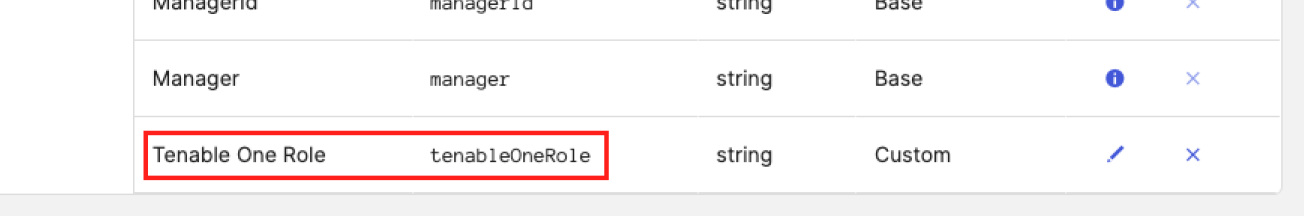
Click Save.
The default user Profile Editor page appears, and Okta adds the newly added custom attribute to the bottom of the list of attributes.
-
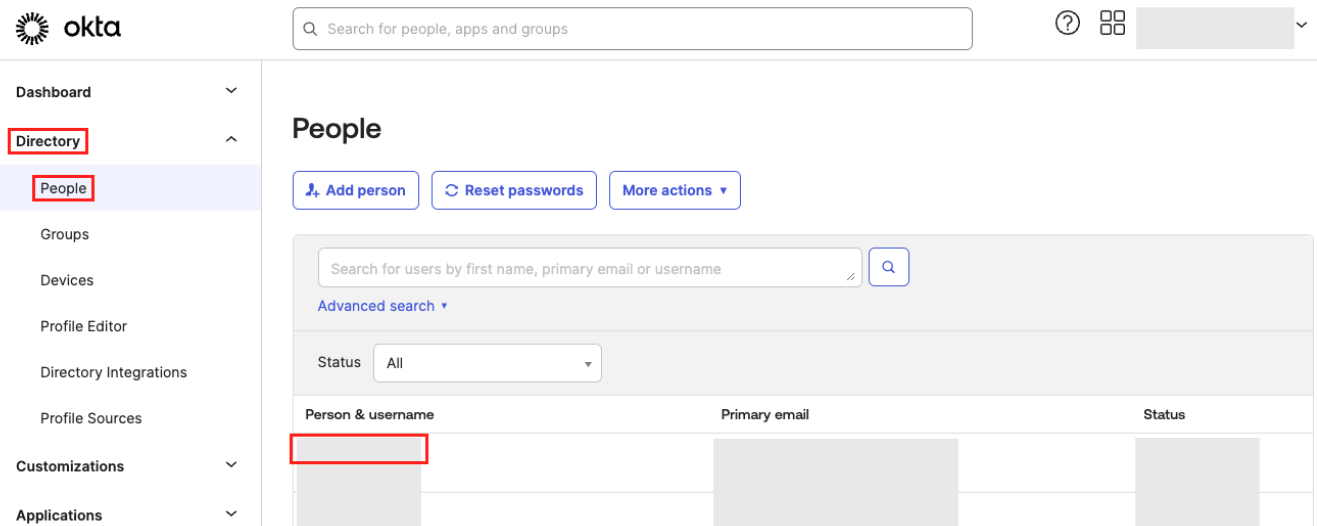
In the left navigation menu, click Directory > People.
The People page appears.
-
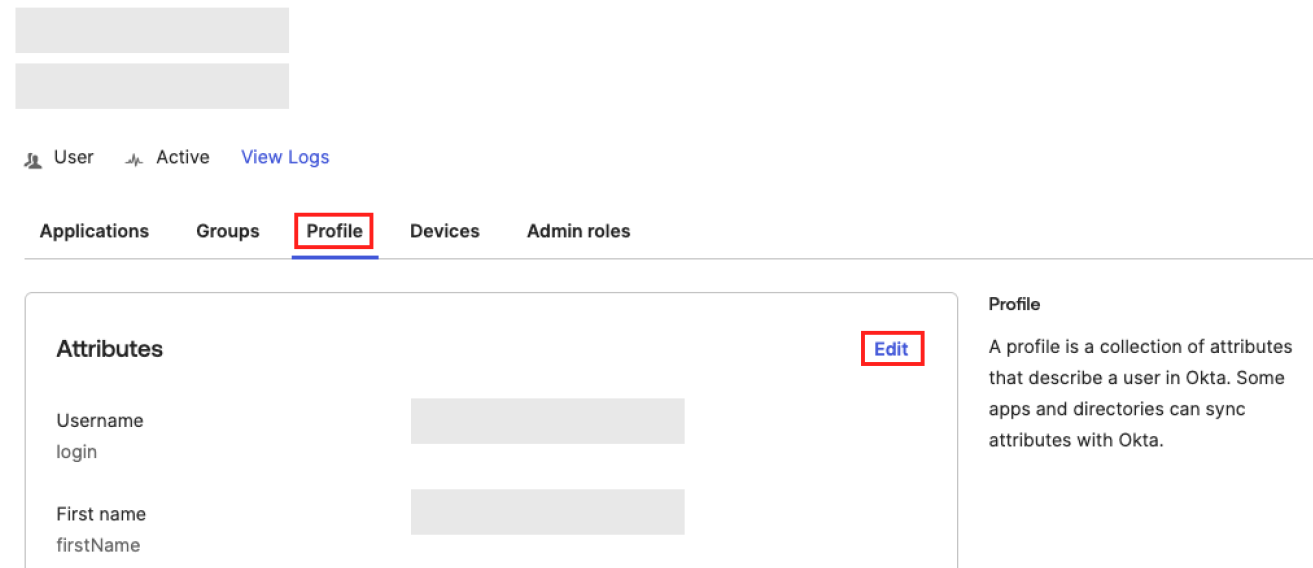
Click the name of the user to which you want to map a Tenable One role.
The user’s Application page appears.
-
Click Profile > Edit.
-
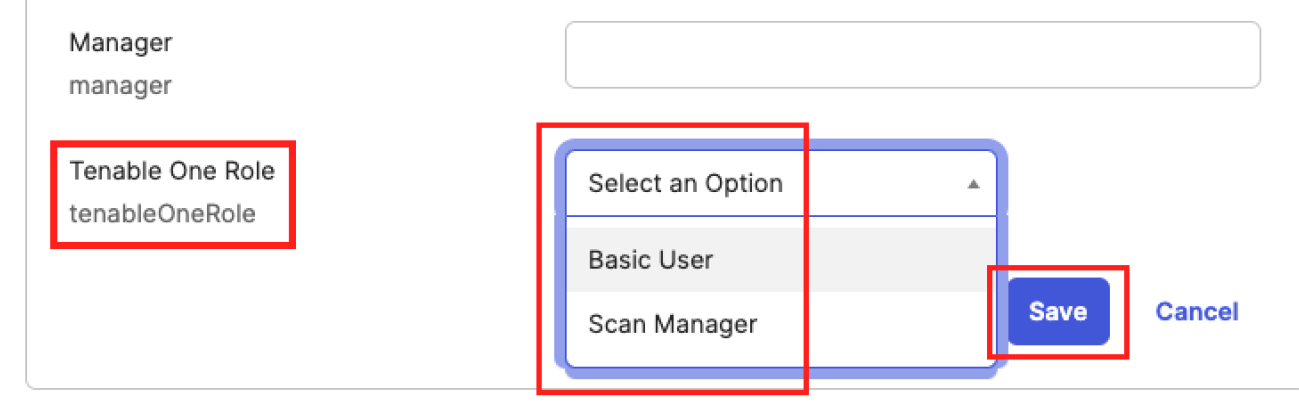
Locate the newly added custom attribute.
-
In the Select an Option drop-down, select the appropriate Tenable role for the selected user (for example, Basic User).
-
Click Save.
-
Any time a user assigned to the application logs in via your SAML configuration, Tenable One automatically adds them to the user role mapped to the Okta application, or, depending on your configuration, mapped to their Okta user profile.
-
Additional Resources
For more information on Okta IdP configuration, see the following resources: