Roles
Roles in Tenable Vulnerability Management allow you to manage the primary privileges and control the main functions users can access within your organization's account. By assigning a role to a user, you broadly determine the actions they can perform, such as managing users, configuring scans, or simply viewing vulnerability data. You can use Tenable-provided roles for standard access levels or create custom roles to tailor privileges to specific organizational needs, ensuring users have the appropriate access to perform their security and vulnerability management tasks.
When you create a user, you must select a role for that user that broadly determine the actions the user can perform.
Note: You can further refine user access to specific resources by assigning permissions to individual users or groups. For more information, see Permissions.
- Roles — Roles allow you to manage privileges for major functions in Tenable Vulnerability Management and control which Tenable Vulnerability Management modules and functions users can access.
- Permissions — Permissions allow you to manage access to data, such as Tags, Assets, and their Findings.
Simply put, roles are the actions you can take in a product, and permissions determine the data to which you can perform those actions.
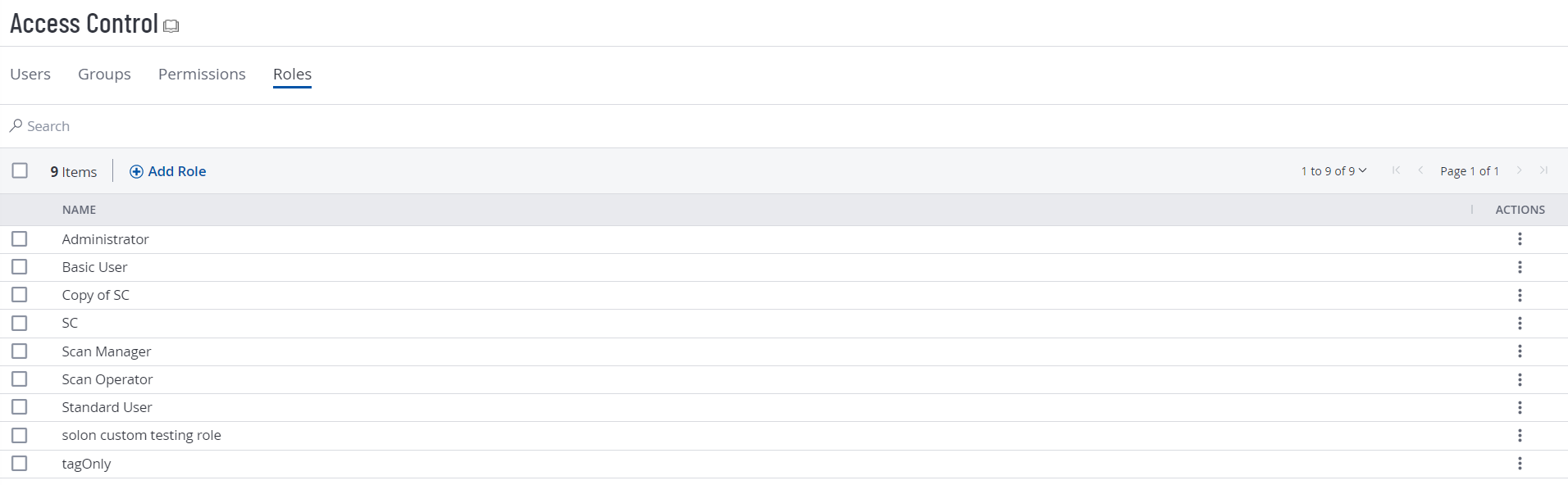
On the Roles page, you can view all Tenable-provided roles and any custom roles created in your Tenable Vulnerability Management instance.
You can assign one of the following role types to users:
| Role Type | Description |
|---|---|
| Tenable-Provided Roles and Privileges | Contains a predefined set of privileges determined by the Tenable Vulnerability Management product specified on your account license. Each role encompasses the privileges of lower roles and adds new privileges. Administrators have the most privileges. Basic users have the fewest. |
| Custom Roles | Contains a custom set of privileges that allow you to tailor user privileges and access to resources on your Tenable Vulnerability Management instance. |
To view your user roles:
Required User Role: Administrator
-
In the left navigation, click
 Settings.
Settings.The Settings page appears.
-
Click the Access Control tile.
The Access Control page appears. On this page, you can control user and group access to resources in your Tenable Vulnerability Management account.
-
Click the Roles tab.
The Roles page appears. This page contains a table that lists all the user roles available on your Tenable Vulnerability Management instance.
Export Roles
On the Roles page, you can export one or more user groups in CSV or JSON format.
To export your user roles:
- Access the Roles page.
-
(Optional) Refine the table data. For more information, see Tables in Tenable Vulnerability Management.
-
Do one of the following:
-
To export a single role:
-
In the roles table, right-click the row for the role you want to export.
The action options appear next to your cursor.
-or-
In the roles table, in the Actions column, click the
 button in the row for the role you want to export.
button in the row for the role you want to export.The action buttons appear in the row.
-
Click Export.
-
-
To export multiple roles:
-
In the roles table, select the check box for each role you want to export.
The action bar appears at the top of the table.
-
In the action bar, click
 Export.
Export.Note: You can individually select and export up to 200 roles. If you want to export more than 200 roles, you must select all the roles on your Tenable Vulnerability Management instance by selecting the check box at the top of the roles table and then click
 Export.
Export.
-
The Export panel appears.
-
- In the Name box, type a name for the export file.
-
Click the export format you want to use:
Format Description CSV A CSV text file that contains a list of roles.
Note: If your .csv export file includes a cell that begins with any of the following characters (=, +, -, @), Tenable Vulnerability Management automatically inputs a single quote (') at the beginning of the cell. For more information, see the related knowledge base article.JSON A JSON file that contains a nested list of roles.
Empty fields are not included in the JSON file.
-
(Optional) Deselect any fields you do not want to appear in the export file.
-
In the Expiration box, type the number of days before the export file expires.
Note: Tenable Vulnerability Management allows you to set a maximum of 30 calendar days for export expiration.
-
(Optional) To set a schedule for your export to repeat:
- Click the Schedule toggle.
- In the Start Date and Time section, select the date and time on which you want the export schedule to start.
- In the Time Zone drop-down box, select the time zone to which you want the schedule to adhere.
- In the Repeat drop-down box, select how often you want the export to repeat.
- In the Repeat Ends drop-down, select the date on which you want the schedule to end.
Note: If you select never, the schedule repeats until you modify or delete the export schedule.
The Schedule section appears.
-
(Optional) To send email notifications on completion of the export:
Note: You can enable email notifications with or without scheduling exports.-
Click the Email Notification toggle.
The Email Notification section appears.
-
In the Add Recipients box, type the email addresses to which you want to send the export notification.
-
(Required) In the Password box, type a password for the export file. You must share this password with the recipients to allow them to download the file.
Note: Tenable Vulnerability Management sends an email to the recipients and from the link in the email, the recipients can download the file by providing the correct password.
-
-
Click Export.
Tenable Vulnerability Management begins processing the export. Depending on the size of the exported data, Tenable Vulnerability Management may take several minutes to process the export.
When processing completes, Tenable Vulnerability Management downloads the export file to your computer. Depending on your browser settings, your browser may notify you that the download is complete.
- Access the export file via your browser's downloads directory. If you close the export plane before the download finishes, then you can access your export file in the Export Management View.
Manage Custom Roles
For more information about managing your custom roles, including creating, editing, and deleting, see Manage Custom Roles.