Tenable One 2024 Release Notes
These release notes are listed in reverse chronological order.
Tenable One December 30, 2024
Tenable Inventory now includes an Attack Path column on the Assets and Weaknesses pages, as well as a Choke Point column on the Assets page. Users can click on the data within these columns to navigate directly to Attack Path Analysis to dive deeper into the relevant attack path information.
For more information, see Assets and Weaknesses in the Tenable Inventory User Guide.
Tenable One December 05, 2024
Users can now input a CIDR range for the IPv4 address property. This allows you to efficiently filter assets and simplifies querying by reducing the complexity of managing IP-based filters.
For more information, see Global Asset Search in the Tenable Inventory User Guide.
Cloud labels can now be used to filter, search, and create tags by using the new External Tags property. This provides improved context by adding more detailed information to the Assets page. Additionally, this improves advanced reporting by enabling the creation of custom exposure cards using cloud labels for tailored reporting needs.
For more information, see Assets in the Tenable Inventory User Guide.
Tenable One November 20, 2024
-
Attack Path Analysis Quick Filters - On the Discover page in Attack Path Analysis, you can now use quick filter buttons to automatically filter the top attack paths list in one click.
-
Tenable One Performance Improvement - You will notice performance improvements in the following areas of Tenable One:
- Tenable Inventory:
- Asset Details page
- Attack Path Analysis:
- Findings page
- Discover page > Top Attack Paths
- Discover page > Node Search
- Tenable Inventory:
Tenable One October 30, 2024
-
Exposure Signals - As part of the Tenable Inventory module, the Exposure Signals provides additional context for increased prioritization to help security teams focus on true exposures. It includes:
-
A library of pre built signals to help get you started. These can be modified.
-
The ability to create custom exposure signals leveraging query capabilities.
-
Incorporated AI to help with the explainability of the exposure signals and their impacted assets.
-
The ability to drill down into either the filtered Inventory view or the Asset Details page to get more information.
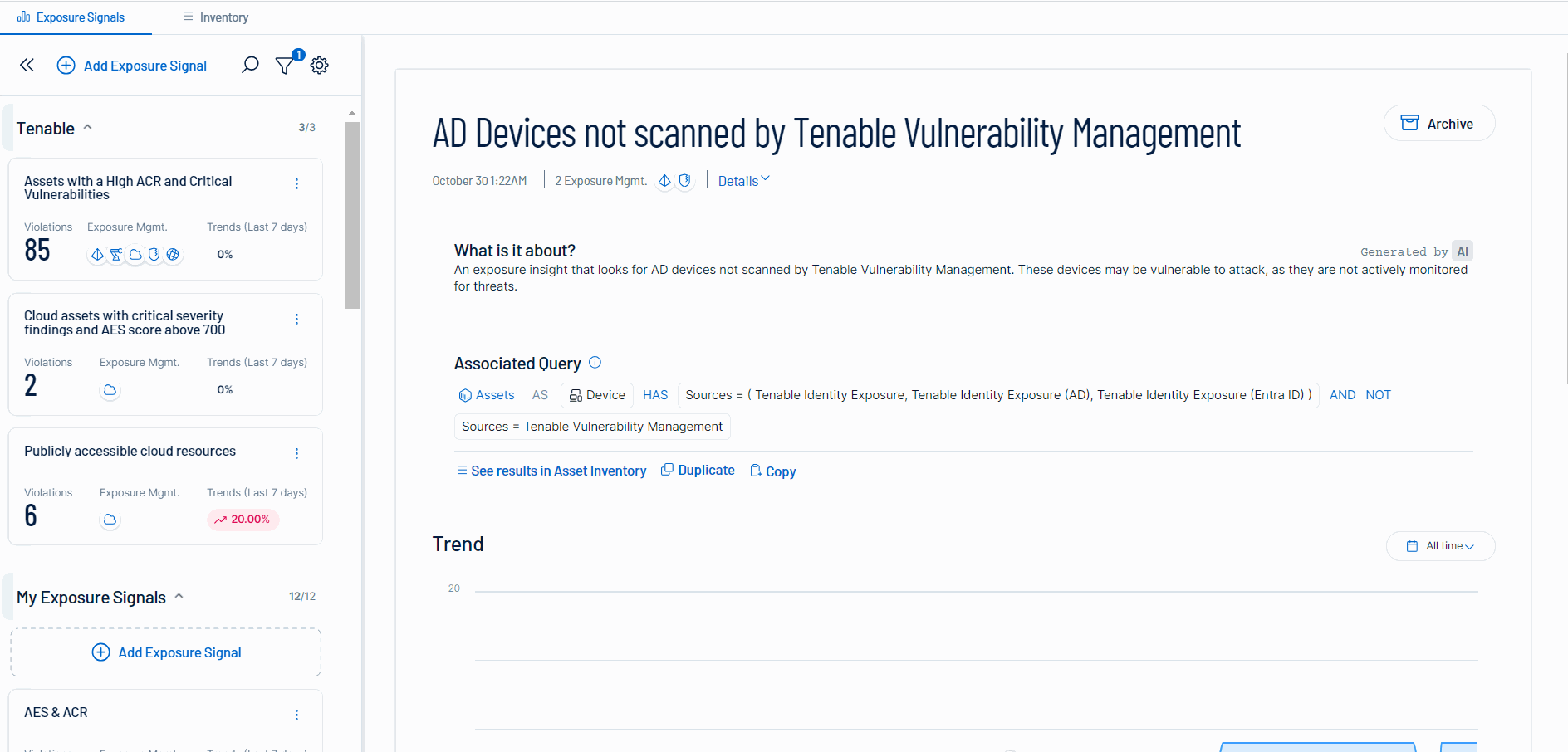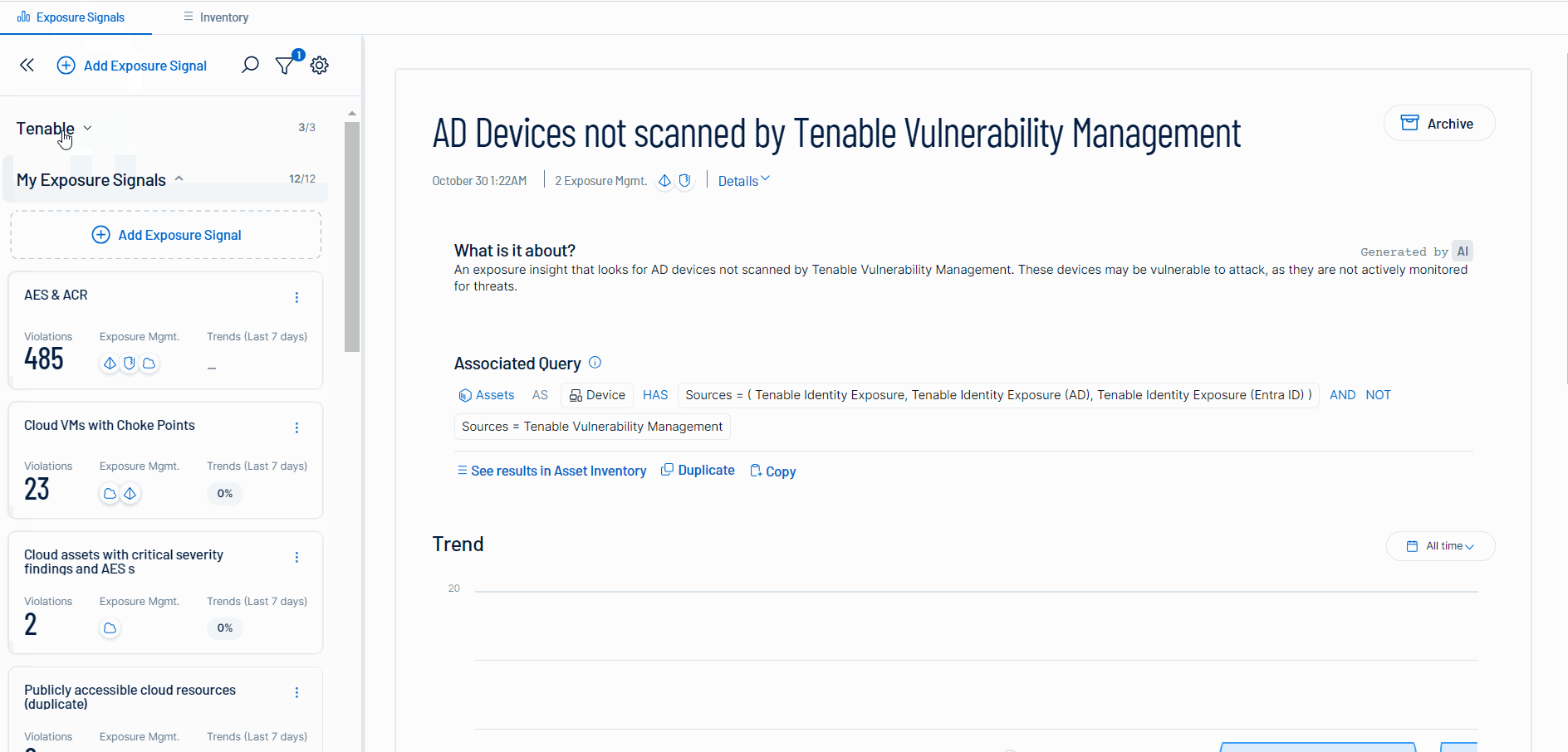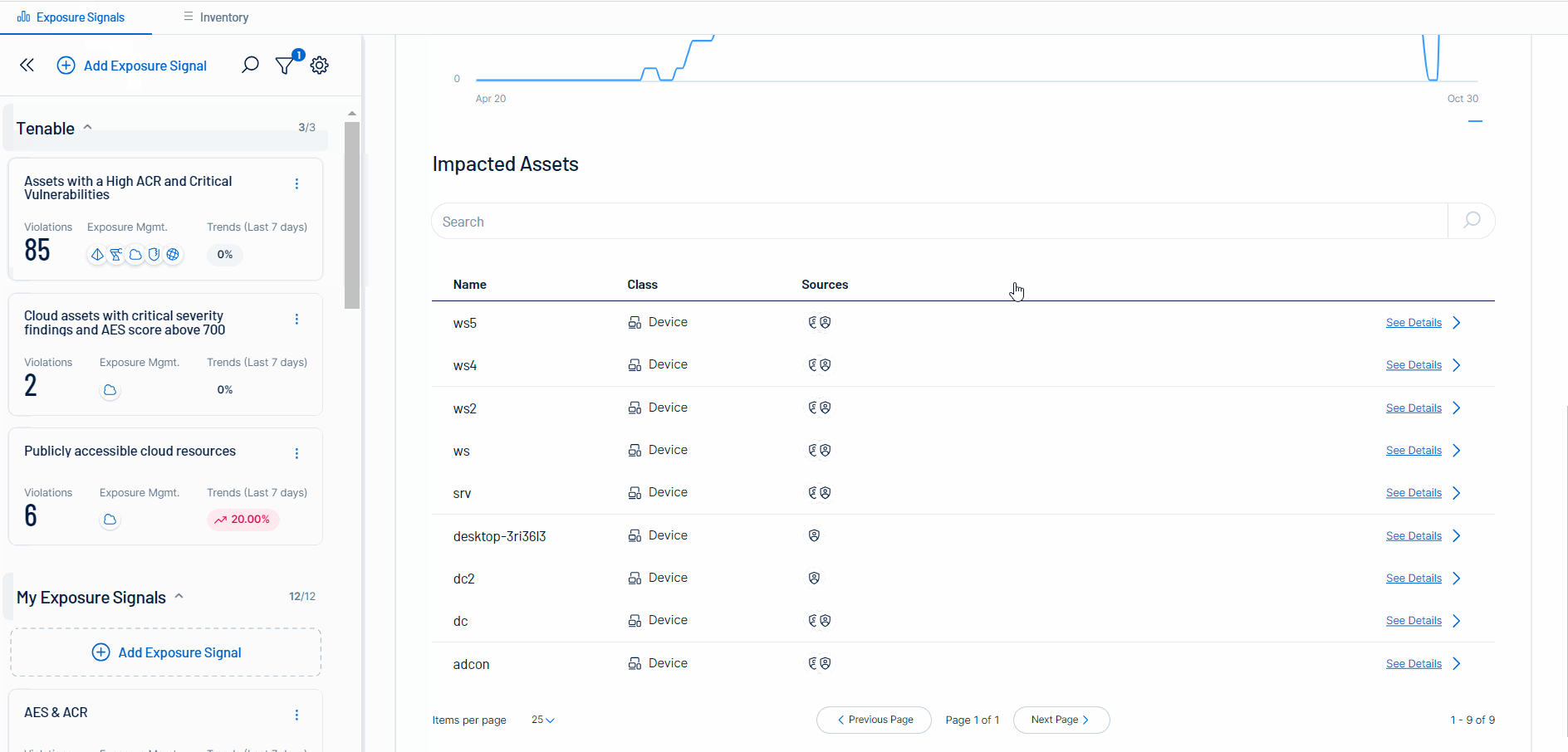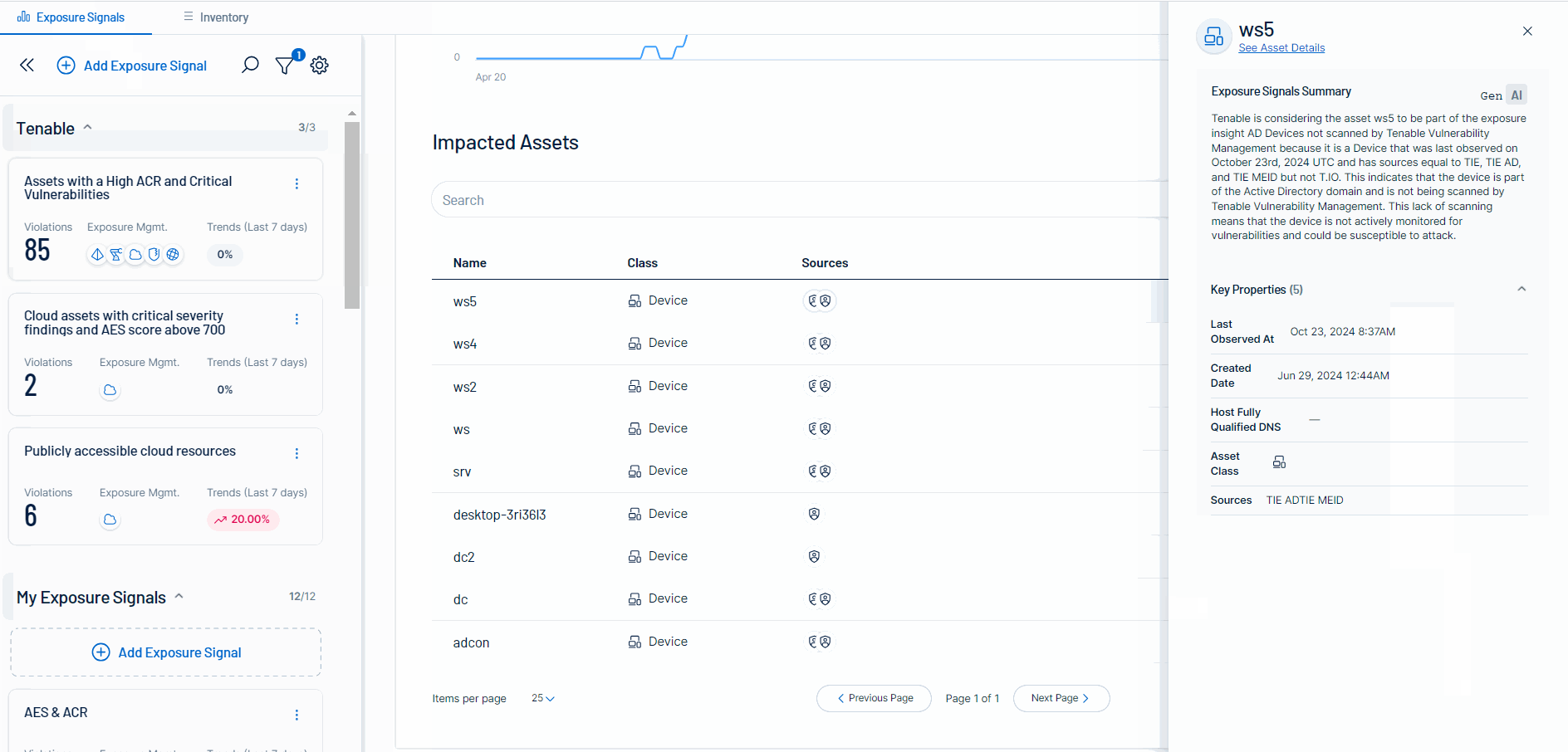
For more information, see the Exposure Signals walk-through.
-
-
Cloud Security Integration with Tenable One
-
Lumin Exposure View has been updated to include Cloud Security for both the Global and Tenable-provided exposure cards.
-
Tenable Inventory has been updated to include Cloud assets (excluding EntraID/OCI):
-
Cloud Security quick filter
-
3 new Tenable queries
-
2 new Exposure Insights
-
New Cloud asset properties for searching and tagging capabilities
-
-
Attack Path Analysis has been updated to include cloud assets and findings:
-
Internet-based attacks that can reach sensitive information
-
Hybrid attack paths, which allow an attacker to move from a corporate network to the cloud and back
-
Attack paths based on policies that can result in privilege escalation or access to sensitive information
-
For more information, see the Tenable Cloud Security in Tenable One walk-through.
-
Attack Path Analysis October 1, 2024
Attack Path Analysis added support for the following:
- Performance improvement on the initial load for the following areas of the user interface:
- Discover
- Findings
- Attack Path Analysis Dashboard Matrix
- Renamed the matrix from "Attack Path Matrix" to "Top Attack Path Matrix"
- Renamed "Target Filter" to "Data Source"
- Contains additional options for data from Tenable OT Security and Tenable Attack Surface Management.
- The matrix now only includes top attack paths (paths leading to critical assets).
Tenable One September 30, 2024
Tenable One is pleased to announce the full availability of Tenable Inventory to all Tenable One customers. This includes:
- Inventory Views: An easy way to view your Asset, Tags, and Weaknesses all within the new Inventory application
- Asset Inventory: Introduction of asset classes & several new asset properties
- Tag Inventory: Create static and dynamic tags leveraging the properties
- Weakness Inventory: View your Misconfigurations and CVEs
- Advanced Search: Quickly find asset information with a natural language processing (NLP) search or build your own search queries with our new query builder leveraging asset classes and the new properties
- Tenable Queries: Preconfigured queries that are editable
- Bookmarks: Ability to save the queries for quick reference
- Enhanced Asset Details: Additional context for assets with new data fields to give a better understanding of classification and function, related attack paths, exposure cards, relationships, etc. These attributes can be used in the new search capability to show the granularity of asset and weakness data.
- Asset Explainability: Each asset can be summarized to get a high level breakdown of the asset and risk information associated.
- Score & Score (Beta) Toggle: With the updates made to our data model, there are two versions of the scores provided within both Tenable Inventory and Lumin Exposure View to help with the transition.
For more information, see:
-
Enhancements Release Notes
Attack Path Analysis September 17, 2024
Attack Path Analysis has added a link to Vulnerability Intelligence user interface from CVE nodes on the Attack Path Analysis graph. When viewing the graph, click View in Vulnerability Intelligence to navigate directly to the Tenable Vulnerability Intelligence user interface, filtered by the selected CVE.
Attack Path Analysis September 12, 2024
Attack Path Analysis added support for the following:
- Added support for sorting over the choke point column in weaknesses.
- Added origin support for history and Tenable queries.
- Updated the filter to present a dropdown of all Tenable products rather than using free text.
- Adjusted the navigation and UI of the Attack Path Analysis dashboard's matrix.
- Ensured legacy operators are used for asset drill down.
| Bug Fix |
|---|
|
Attack Path Analysis August 29, 2024
Attack Path Analysis has added Data Source attribution to Attack Paths. These enhancements can be found in the following UI locations:
-
The Discover tab when exploring an attack path's details.
-
In the attack path summary section.
-
The Findings tab when viewing findings details
Attack Path Analysis August 26, 2024
Attack Path Analysis has added Microsoft Entra ID as a data source within the Attack Path Analysis application. This includes the following additions:
- Microsoft Entra ID weakness search filters
- Microsoft Entra ID detection filters
- Microsoft Entra ID technique filters
-
Search by Microsoft Entra ID data source
Attack Path Analysis July 31, 2024
Attack Path Analysis has added Tenable OT Security and OT data as a data source within the Attack Path Analysis application. This includes the following additions:
- OT data source search filters
-
OT weakness search filters
-
OT detection filters
-
OT Technique filters
-
Search by number of steps in an Attack Path
-
Search by Asset ID
Tenable InventoryJuly 31, 2024
Tenable Inventory now includes Attack Path Analysis choke points as part of the Weaknesses page.
For more information, see Weaknesses in the Tenable Inventory User Guide.
Attack Path Analysis June 24, 2024
Attack Path Analysis added support for the following:
- Enterprise
Attack Path Techniques
- Trust Modification - Find on-prem services with SSO configured to EntraID
- Group Policy Discovery
- ICS Attack Path Techniques
- Program Download - Engineering Stations with access to PLC
- Remote System Discovery - All devices that are part of a backplane
- Exploitation of Remote Services - CVEs allowing lateral movement between devices including network access validation
- Hardcoded Credentials - Vulnerable devices configured with services allowing credential access
-
PyTenable and API for Findings
-
Performance improvement for multi-technique searching on the Discover page
| Bug Fix |
|---|
| [GA] Fix local group membership mixed membership |
Tenable Inventory June 18, 2024
- [Product rebrand] Asset Inventory has been revamped and rebranded to Tenable Inventory.
- [Navigation] Improved navigation with quick access menus.
- [Advanced Search] The enhanced Advanced Search Bar incorporates more contextual information and provides easier searching capabilities either with the Query or Natural Language Processing (NLP) option with a primary focus on efficiency and productivity for deriving asset-related information.
- [Queries and Bookmarks] View and reuse your previously created queries and quickly jump to content you have marked to return back to.
- [Asset Classes] Formalized asset classification based on the "types" property utilized in Vulnerability Management.
- [Weakness Inventory] View all Misconfiguration and CPE level vulnerability data from across the organization.
- [Asset Explainability] You can view an AI-generated summary of an asset and its top identified weaknesses.
- [New Properties] More than 400 attributes can be used to enrich the asset and weakness views.
- [AI Asset Explainability] Added an AI Asset Summary button to asset details. This button summarizes the assets and the asset's related weaknesses.
- [Account Tab] View all accounts associated with a selected asset.
- [Weakness Tab] Access a comprehensive view of all weaknesses associated with your asset for better risk management.
- [Attack Paths] Identify the primary Attack Paths your asset is part of, helping you prioritize effectively.
- [Tags] Explore asset-related Tags to understand its context and relationships with other assets.
- [Relationships] Enhance your understanding of asset connections to optimize operational strategies.
- [Exposure Cards] View all Lumin Exposure View Exposure Cards associated with an asset.
- [Devices] (Restricted By Asset Class) View devices associated with an account or Identity’s class asset.
- [Entitlements] (Restricted By Asset Class) View an Identity’s entitlements.
- [Roles] (Restricted By Asset Class) View all roles associated with an Identity.
- [Groups] (Restricted By Asset Class) View all groups associated with an Identity.
- [Access] (Restricted By Asset Class) View all of an Identity’s access permissions.
-
[Dynamic Tags] Currently, you can only create new tags with “Match All” tag rules. Any existing dynamic tags with “Match Any” rules will not function as expected and cannot currently be edited in the Inventory interface. Tag asset counts may take up to an hour to update after a tag is generated in Asset, Tag and Weakness Inventory views.
-
[RBAC Limitations] There are known Role Based Access Control (RBAC) limitations related to custom roles. For more information, see Tenable Roles and Privileges in the Tenable Vulnerability Management User Guide.
Tenable Roles and Privileges are outlined here /vulnerability-management/Content/Settings/access-control/TenableRolePrivileges.htm
Attack Path Analysis May 22, 2024
-
Attack Path Analysis added additional support for fixed Findings:
-
All findings that are resolved will be marked as Done and Archived.
-
All findings that are no longer part of an attack path will be marked as Archived within the relevant activity log.
-
Attack Path Analysis April 18, 2024
-
Attack Path Analysis includes new filters for Asset ID and Weakness ID on the Findings page. This feature allows customers to map from weaknesses to choke points.
For example:
-
Show me all choke points leveraging weak password IoE
-
Show me all the choke points of asset XXX
-
-
Attack Path Analysis includes new filters for Technique and Finding ID on the Discover page.
For example:
-
Show me all attack paths using the DCSync technique
-
Show me all attack paths that go through choke point XXX
-
-
Attack Path Analysis now includes an application navigator that allows users to search the entire application. When you select a search result, you automatically navigate to that page within Attack Path Analysis. You can look for pages in the application, queries in the query library, MITRE ATT&CK Heatmap categories, and more.
-
Added an AI Assistant button in the canvas interaction panel.
| Bug Fix |
|---|
| [Findings] Fix “View Path” for a specific finding returning no results |
Attack Path Analysis April 8, 2024
Attack Path Analysis reduced the data pipeline execution time by 25%. Additionally, Attack Path Analysis will only process licensed assets in order to optimize COGS and reduce data processing time.
Attack Path Analysis March 18, 2024
In the MITRE ATT&CK section, Attack Path Analysis now includes support for the Msiexec technique.
| Bug Fix |
|---|
| [GA] Fix invalid Subnet CIDR |
Attack Path Analysis March 12, 2024
The Attack Path Analysis Discover section now includes an AI assistant for Asset Node and Attack Path explainability.
-
The MITRE Att&ck page now includes support for the Remote Access Software technique.
-
Attack Path Analysis has decreased the Top Attack Paths processing time from an average of 7 minutes to 1 minute, and the maximum processing time from 86 minutes to 45 minutes.
| Bug Fix |
|---|
| [Side Panel] Fix Password nodes not clickable |
| [Side Panel] Extend max displayed characters for node properties (25 to 50 characters) |
| [Query Library] Fix built-in queries that are being processed show as enabled instead |
Attack Path Analysis February 20, 2024
-
The Query Library now includes the following built-in queries:
-
Internet to Critical Assets
-
Computers without SMB Signing
-
Computers with LLMNR enabled
-
-
The Discover page now includes support for the SecurityControl/SecurityControlAgent search parameters.
| Bug Fix |
|---|
| [Findings] Fix total findings count when navigating between pages |
Lumin Exposure View February 15, 2024
The Tenable One Exposure team is excited to announce that we have released an initial version of the new category card for OT in Lumin Exposure View. You can view the new OT Exposure Card under the Exposure Card Library > Category section. This card includes the Overall Score, Trend, and Tag Performance metrics. You can also drill down from Lumin Exposure View into Cyber Asset Management to see your OT assets. To easily filter OT assets within Inventory, we introduce quick filters to find all your OT assets quickly.
Attack Path Analysis February 15, 2024
Attack Path Analysis now supports the following Ransomware Queries within the Query Library:
-
LPHV Blackat
-
CL0P
-
LockBit
-
8base
-
Akira
| Bug Fix |
|---|
| [Data] Improve identification of network access from external device. If a device is found in Nessus scan, it will be treated as internal. If the device is unknown or found in Tenable Attack Surface Management, and has a public IP address, it is identified as external access |
| Fix filter search to be case insensitive |
Attack Path Analysis February 12, 2024
Beginning in this release, users can see which users created/updated a bookmark within the Attack Path Analysis Query Library.
-
In the MITRE ATT&CK section, we have extended External Remote Services technique support for SSH and VNC protocols.
-
On all Discover/Findings pages, all additional information now appears in the side details panel.
-
On the Discover page, we removed the Tactics List in the canvas bracket to avoid flooding the screen with text.
Attack Path Analysis January 30, 2024
Beginning in this release, the definition of the Path Priority Rating has changed:
-
Path Priority Rating (new metric) - prioritization metric for attack paths based on the exposure of the source, criticality of the target and the number of steps of the attack path.
-
Choke Point Priority (previously known as Path Priority Rating) - prioritization metric for attack techniques based on the number of attack paths exploiting the attack, the number of critical assets it leads to, and the complexity of the attack.
The new Discover landing page will now show the top attack paths by default. Additionally, you can now perform a search for asset nodes separately from attack paths by using the Asset Query Builder.
Attack Path Analysis now includes the following generative AI capabilities:
-
Attack Path Summarization - transforms the graphical representation of an attack path to natural language including title and executive summary. This enables our users to better understand the impact of attack paths and improve their ability to communicate it with the relevant stakeholders.
-
Mitigation Guidelines - The Findings Details page now includes the ability to get more practical mitigation guidelines. This improves the efficiency of users asking to act on findings and eliminate attack paths.
The attack path table is now the first step when searching attack paths. Each attack path has a title and summary. Each path has a new metric of Path Priority Rating, so users can better visualize the attack path.
When a user views an attack path, they can now drill down to the choke points (findings) that were found as part of the attack path.
Tenable One January 23, 2024
Tenable is pleased to announce the redesigned License Information page, which streamlines how you view cloud license details on the Tenable platform.
On the License Information page, you can:
-
In Tenable One only, use visual overviews by product or time period to spot trends.
-
View license information for all Tenable products in your cloud container.
-
View license usage snapshots, such as total assets or available assets.
-
View license resource counts for all your cloud products.
The License Information page is available to all users. To learn more, see License Information.
Attack Path Analysis January 22, 2024
Attack Path Analysis has added support for the following techniques:
-
Windows Credential Manager MITRE Attack Technique
Additionally, Attack Path Analysis now supports the following Trending Attack Paths:
-
APT28
-
APT33
-
Scattered Spider
-
Lockbit_3.0
-
Medusa
| Bug Fix |
|---|
| [Discover] Fix invalid last active date for Nessus AD identities |
| [Findings] Fix filters badge not visible when navigating from discover to findings |
| [Findings] Add truncation for the long names in the findings table |
| [Discover] Fix bookmarks deletion bug |