Tenable Vulnerability Management 2025 Release Notes
Tip: You can subscribe to receive alerts for Tenable documentation updates.
These release notes are listed in reverse chronological order.
December 16, 2025
The following is not supported in Tenable FedRAMP Moderate environments. For more information, see the Tenable FedRAMP Product Offering.
Tenable is excited to announce the next installation of mobilization services: ticketing integrations in Tenable Vulnerability Management for ServiceNow ITSM. Unify teams and streamline remediation workflows by automatically or manually creating bi-directional tickets in ServiceNow via Exposure Response initiatives. This capability accelerates response times by synchronizing your security findings with tickets in ServiceNow.
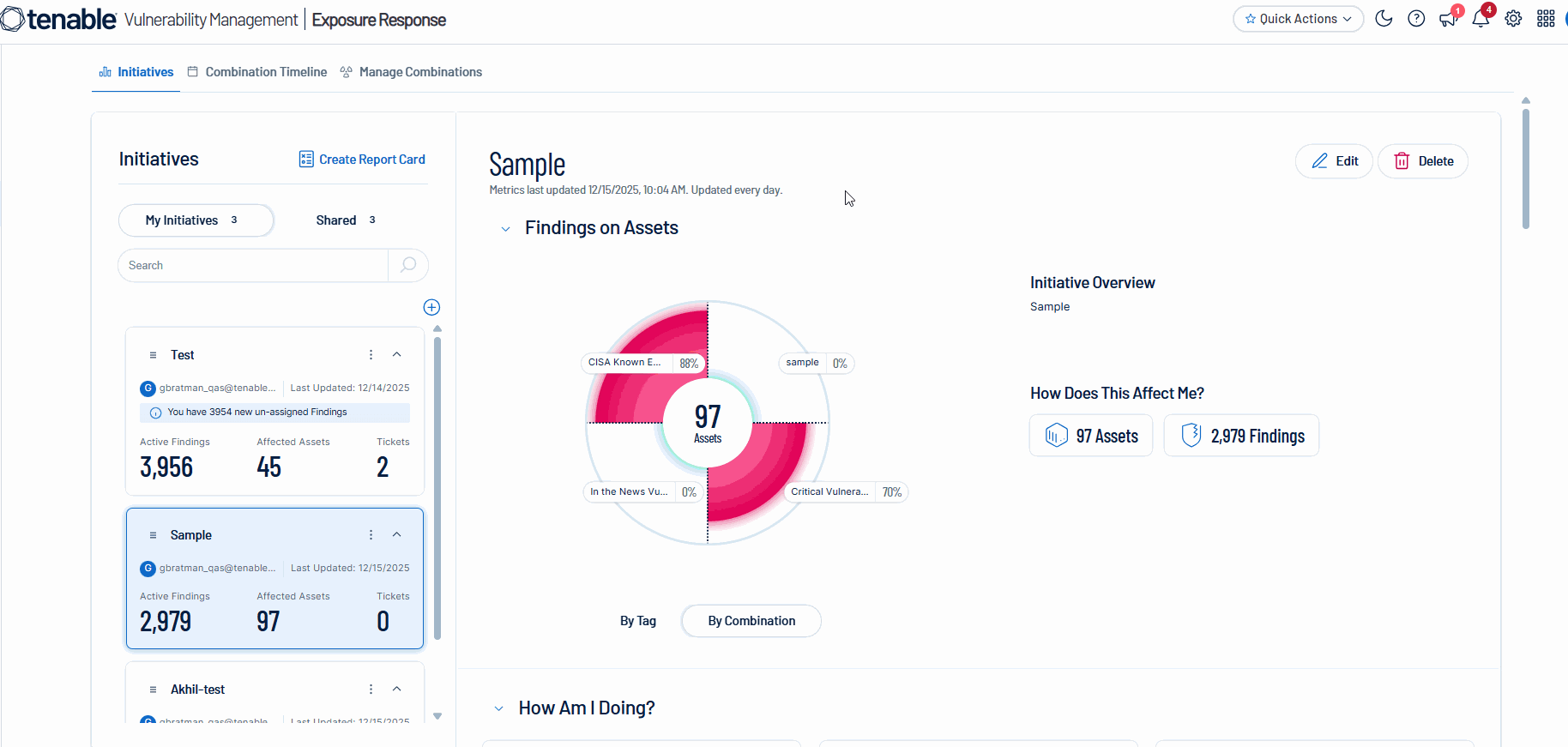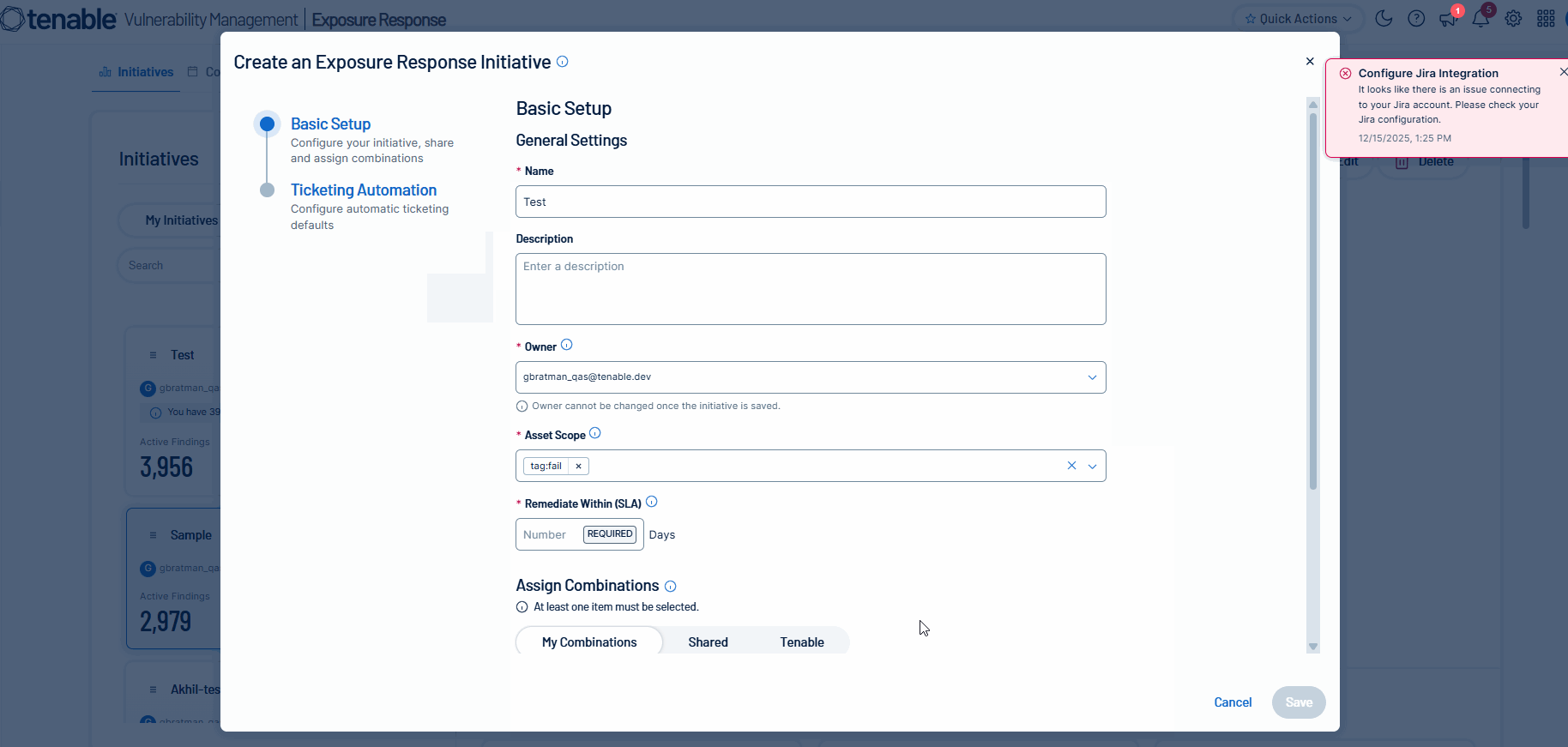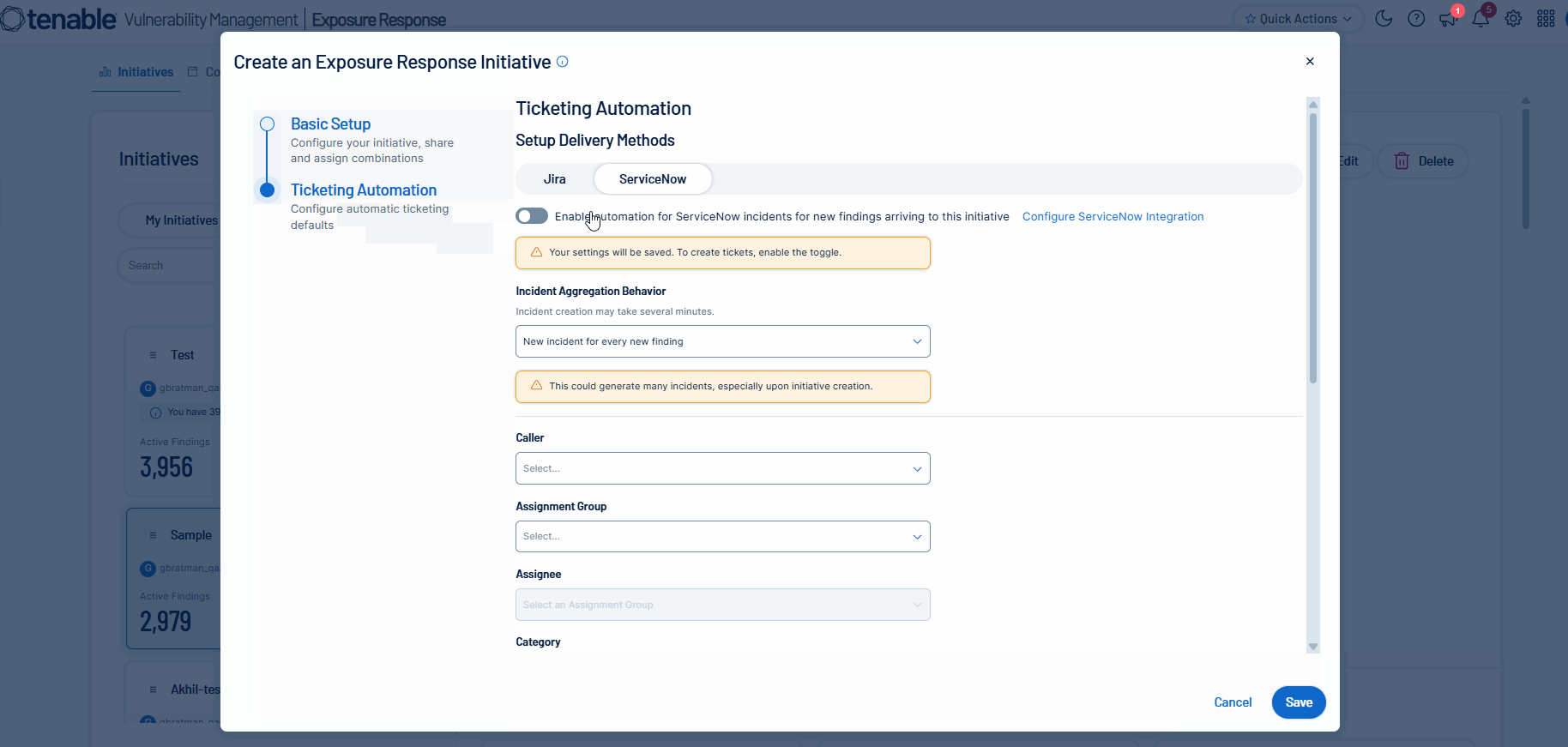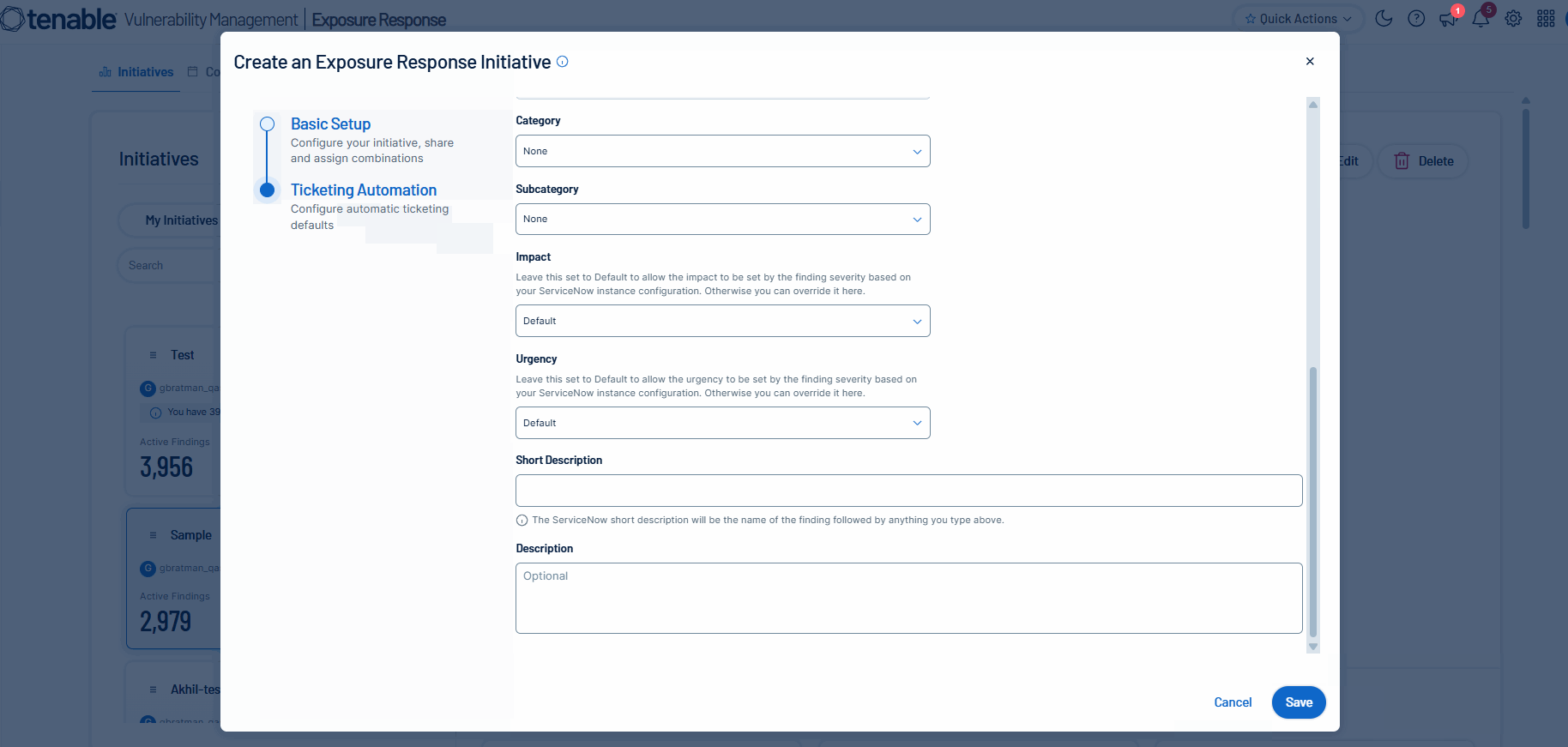
For more information, see:
-
Storylane demo for Tenable Mobilization
-
Create an Initiative in the Tenable Vulnerability Management User Guide
-
Mobilization Quick Reference Guide
December 10, 2025
Tenable is excited to announce the release of the following updates for Role-based Access Control (RBAC):
-
A new Read-Only role for Tenable Exposure Management and Tenable Vulnerability Management which allows users to view and drill down into information without affecting the data.
-
A new custom role for Tenable Exposure Management that consolidates access into a single place. This allows for more granular access and control across the different areas within the product.
Key Information:
-
By default, the Inventory section in Tenable Exposure Management is enabled
-
Disabling a navigation item:
-
Removes the widget from the Home page
-
Removes related fields and data from the Inventory section
-
Removes the tab from the Asset Details page
-
-
Privilege Highlights:
-
Read — Users can view and drill down into data. They cannot create, update, delete, or export data, and any action-related elements are scrubbed from the user interface.
-
Write — Users can create, update, delete, or export data.
-
-
New tag enforcement for Tenable Exposure Management
-
Tags created in Tenable Exposure Management are available on the Permissions page
-
-
Excludes Attack Path — To access the Attack Path section of Tenable Exposure Management, you must enable the Can View permission for All Assets. Note that this overrides and disables the ability to enforce specific tag permissions for this user in other parts of Tenable Exposure Management.
For more information, see Roles in the Tenable Vulnerability Management User Guide.
December 4, 2025
Tenable is excited to announce the initial release of mobilization services, beginning with ticketing integrations in Tenable Vulnerability Management for Jira Cloud. Unify teams and streamline remediation workflows by automatically or manually creating bi-directional tickets in Jira Cloud via Exposure Response initiatives. This capability accelerates response times by synchronizing your security findings with tickets in Jira Cloud.
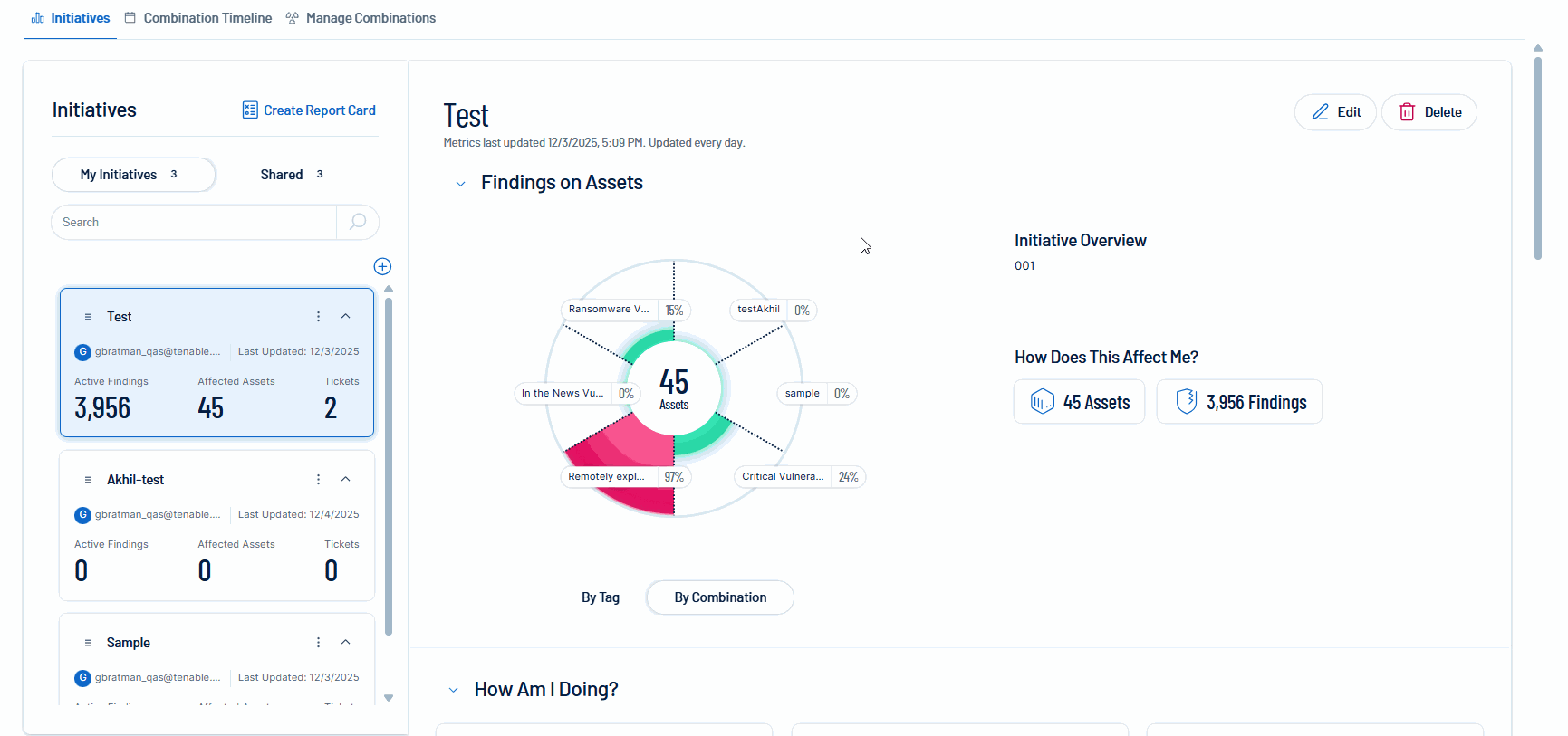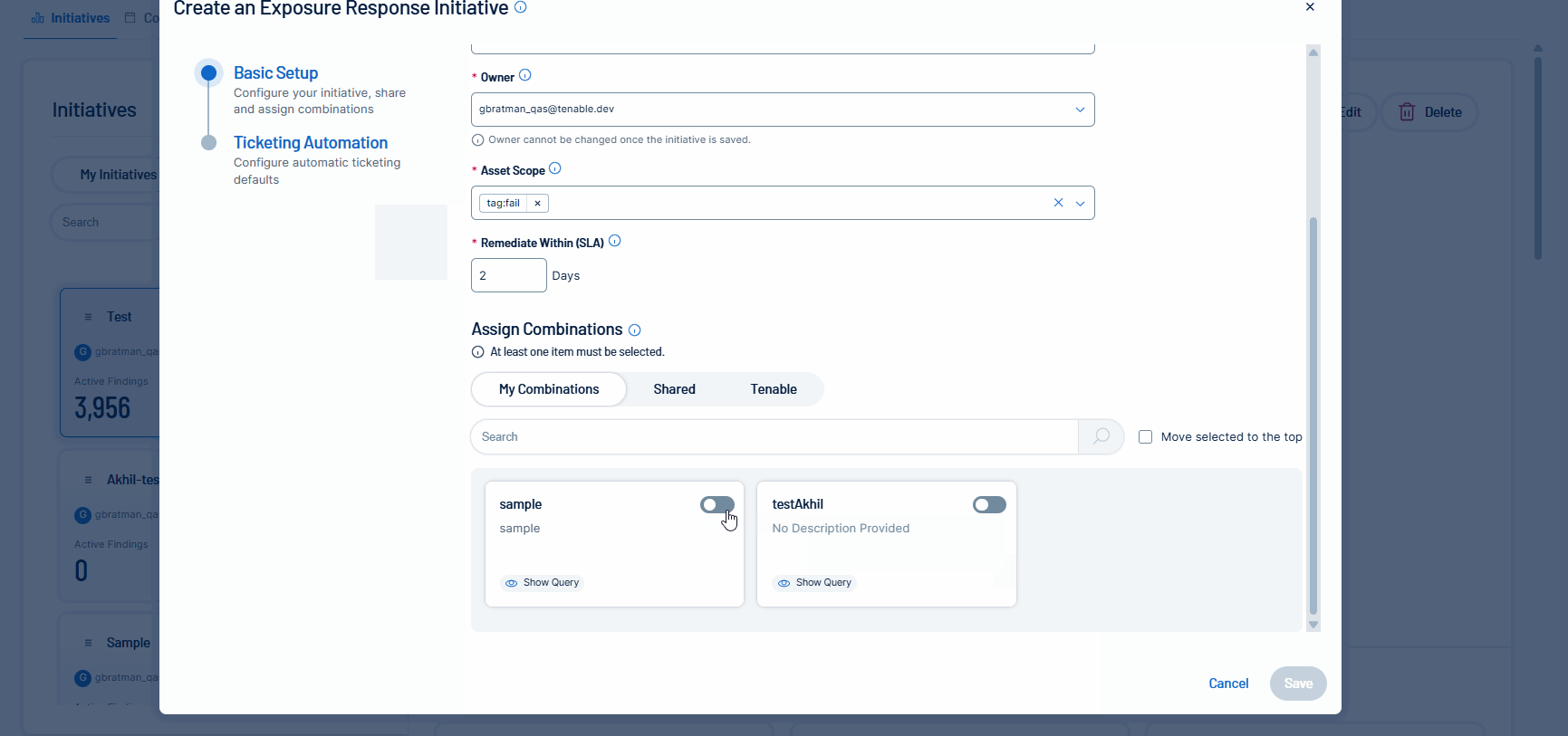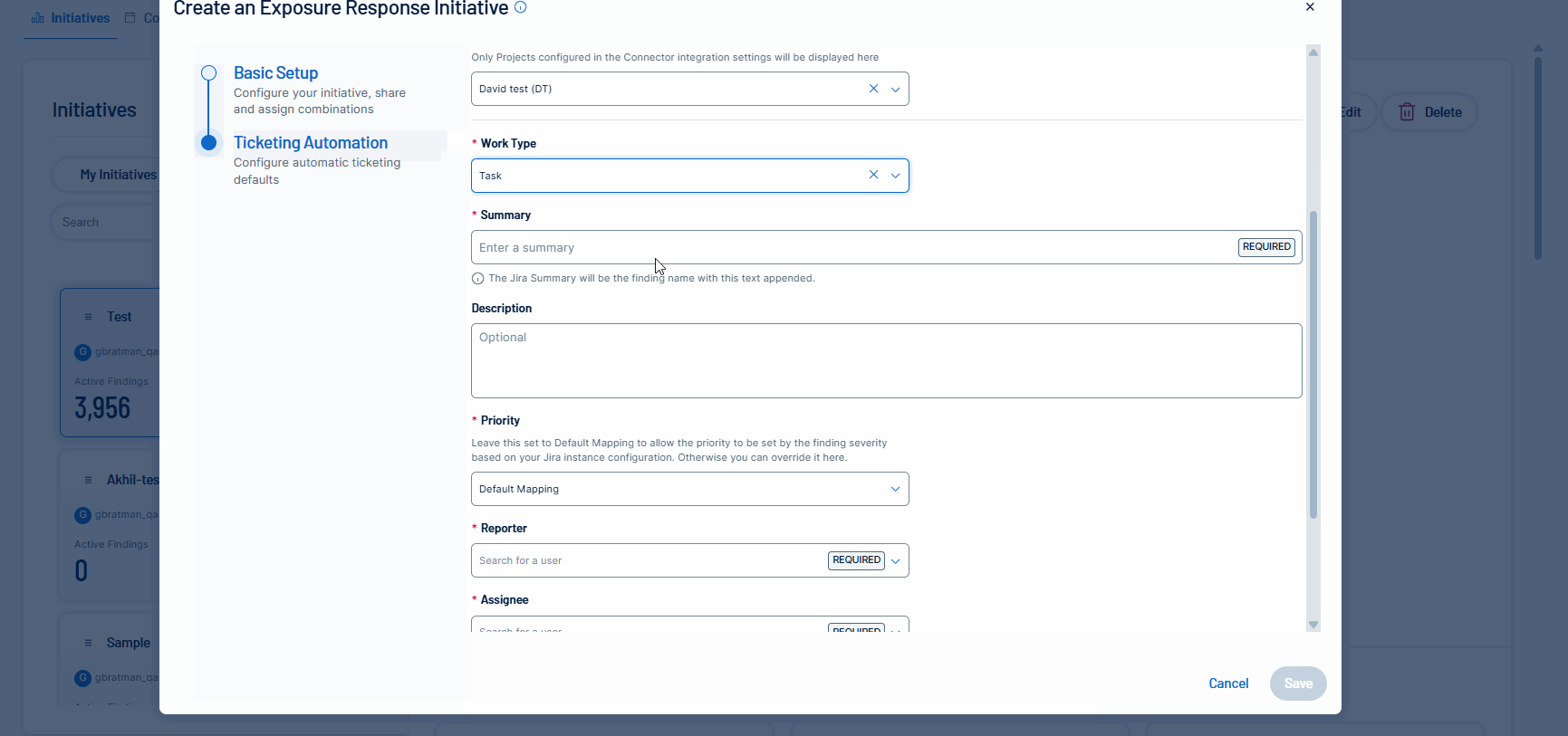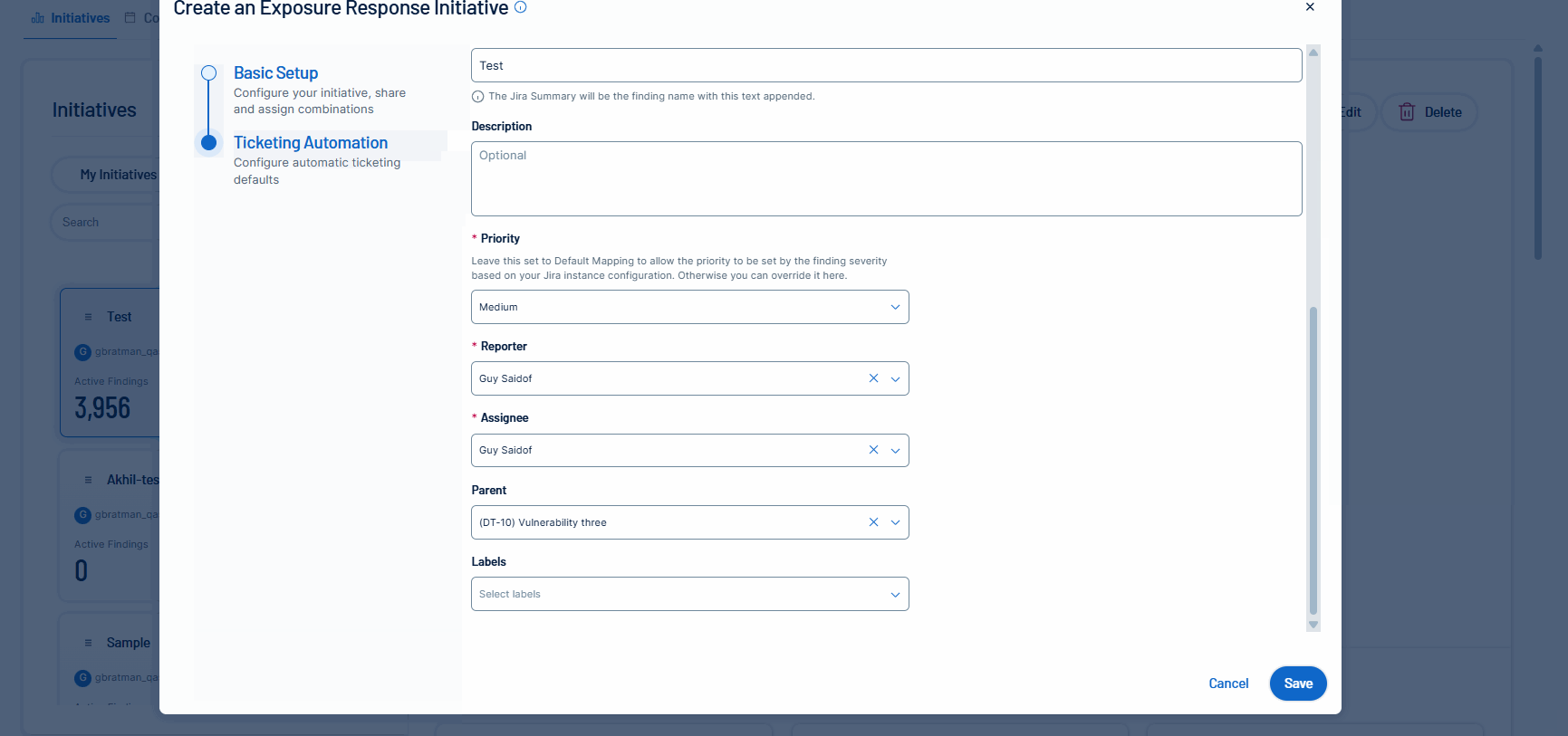
For more information, see:
-
Storylane demo for Tenable Mobilization
-
Create an Initiative in the Tenable Vulnerability Management User Guide
-
Mobilization Quick Reference Guide
December 3, 2025
Tenable has updated Tenable Vulnerability Management with the following capabilities:
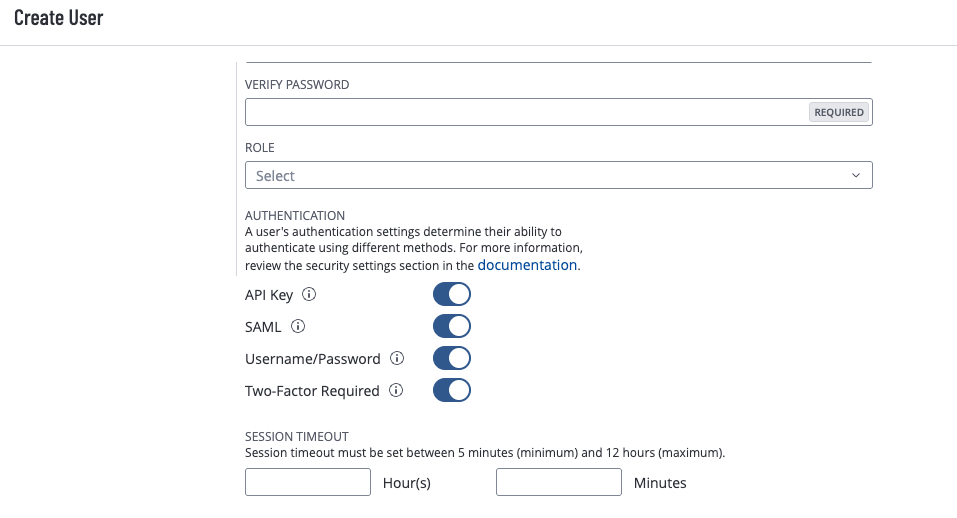
Configurable Session Timeout
Admins can now set session timeouts when creating new users or updating existing ones (individually or in bulk). The default remains 30 minutes, but timeouts can now be configured anywhere from 5 minutes to 12 hours.
For more information, see Create a User Account in the Tenable Vulnerability Management User Guide.
Query-Based Dynamic Asset Tagging in Explore
On the Explore > Assets page, users can convert their existing queries into dynamic tags, using the same workflow that’s currently available in the Tags section of Tenable Vulnerability Management.
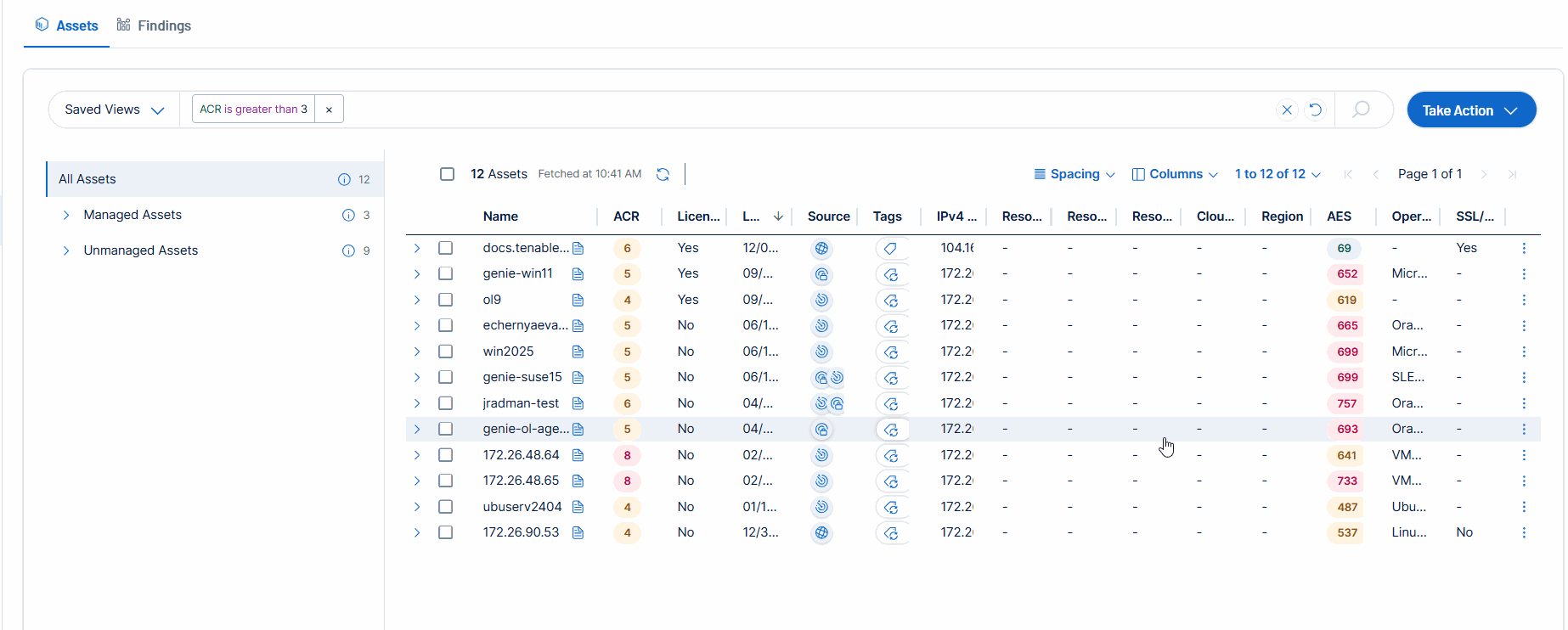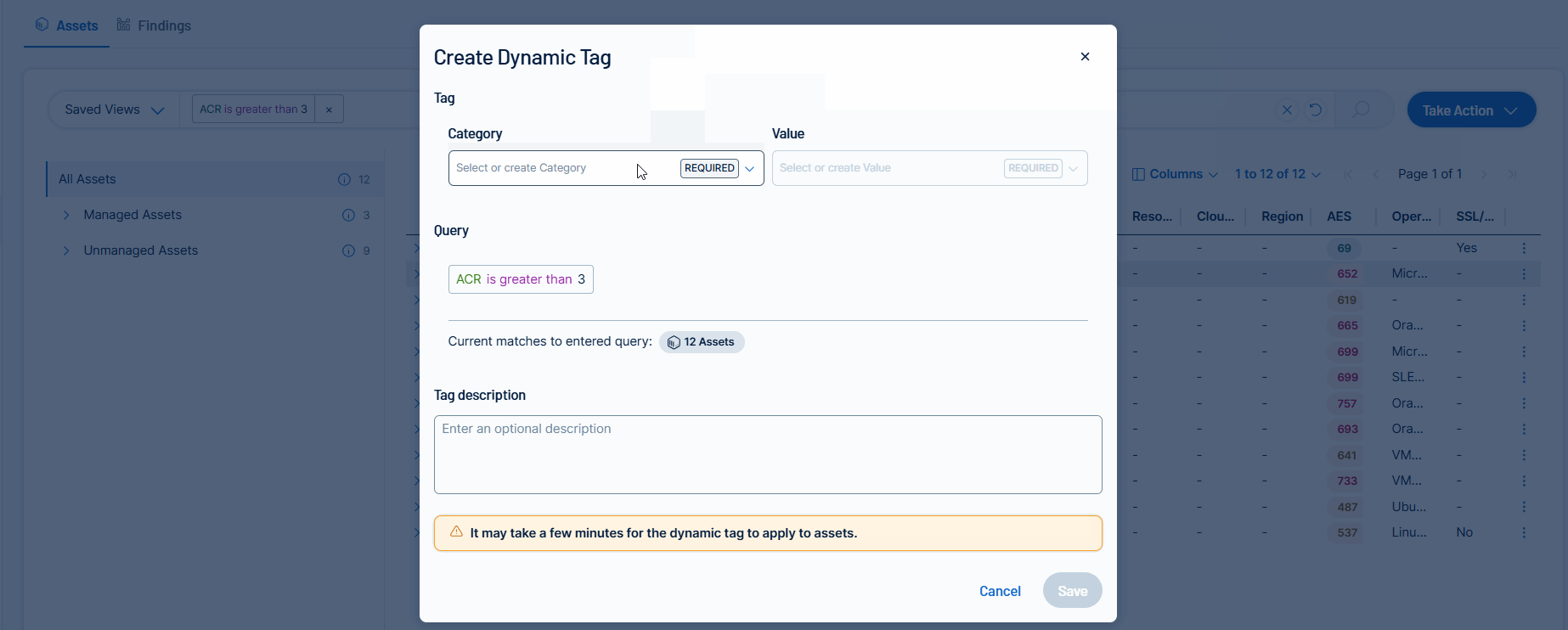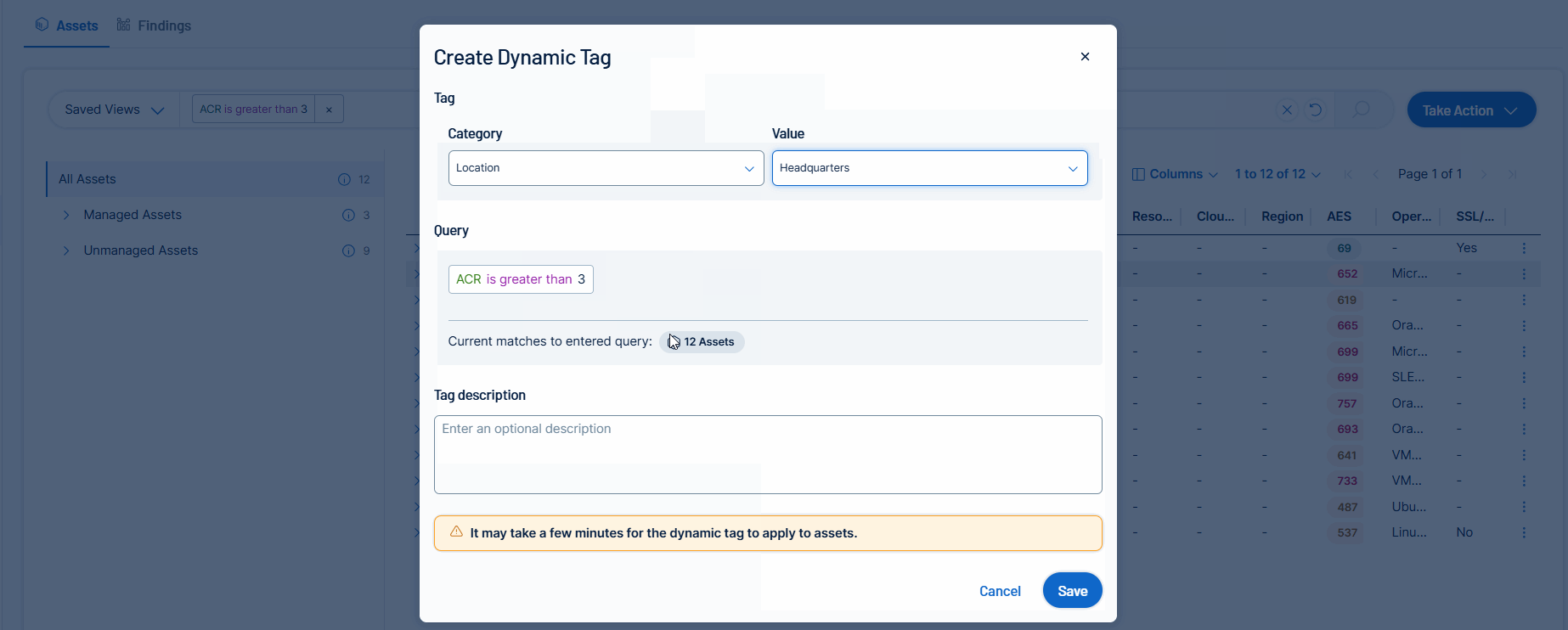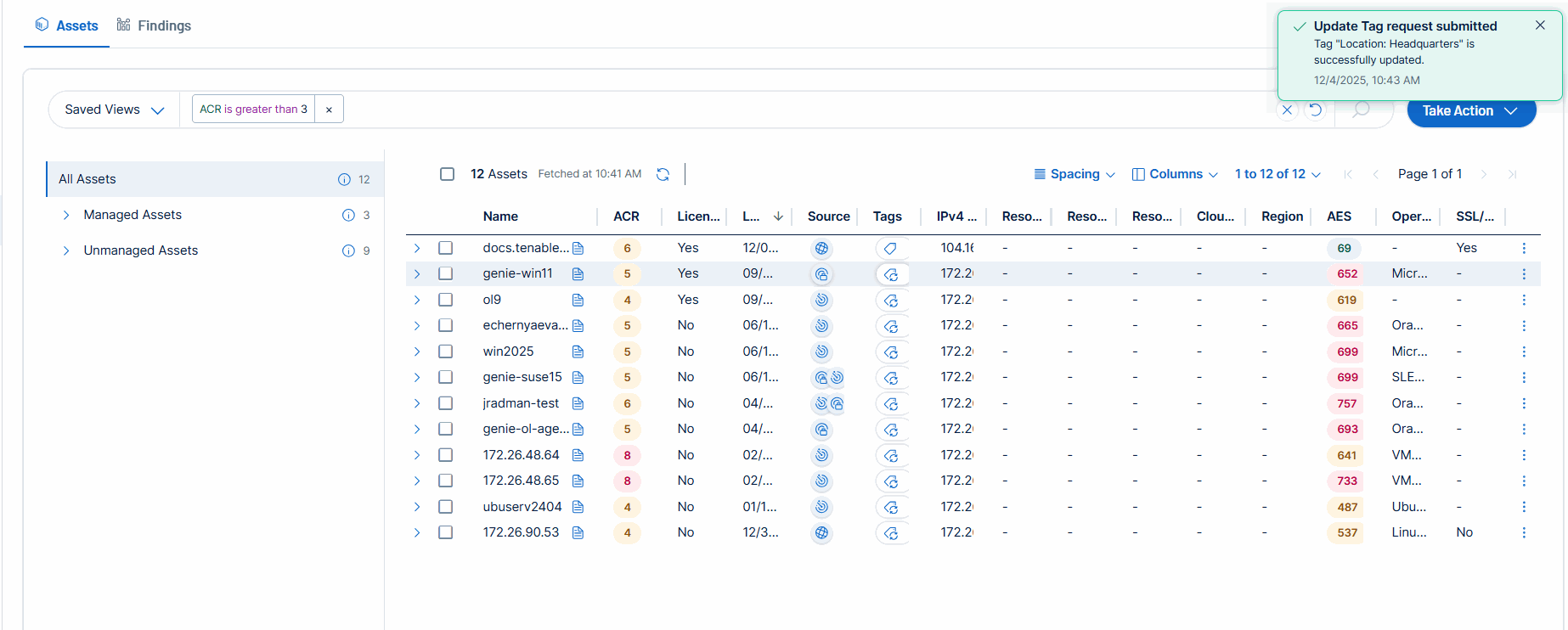
For more information, see Create an Asset Tag in the Tenable Vulnerability Management User Guide.
October 29, 2025
Tenable has updated Tenable Vulnerability Management with the ability to create and configure scanner profiles. Scanner profiles allow you to configure a range of settings for a specific group of linked Tenable Nessus scanners.
You can use scanner profiles to:
-
Assign a specific scanner version for testing or standardization purposes.
-
Control how and when scanners receive plugin updates.
-
Determine what plugins Tenable Vulnerability Management installs on linked scanners during the daily plugin update.
You can manage scanner profiles in the Profiles tab under Sensors > Nessus Scanners in the Tenable Vulnerability Management user interface.
For more information, see Scanner Profiles in the Tenable Vulnerability Management User Guide.
October 22, 2025
We're excited to announce the launch of query-based recast, a major enhancement to Tenable Vulnerability Management that gives you greater precision, automation, and control over your vulnerability exceptions. This release delivers the tools you need to streamline your security operations and confidently manage your risk posture.
Gain granular precision with query-based recast.
You can now create highly granular vulnerability exceptions with far more control than ever before. This enhancement is key to ensuring your exceptions are spot-on, so you can trust your vulnerability data.
-
Expanded Criteria: Create rules using 14 new criteria, giving you granular control over which vulnerabilities are accepted.
-
Supported Criteria Include: Asset Tags, CVEs, FQDNs, Network(s), Plugin ID(s), Plugin Name(s), Asset ID, Asset UUID, Host Audit Findings, IPv4 / IPv6 addresses, Port(s), and Protocol(s).
Simplify management and avoid conflicts.
The modernized rules management experience is built to eliminate administrative headaches and help you confidently avoid confusing or conflicting policies.
-
Intelligent Conflict Detection: The new Rules Management page flags related rules upfront, which helps you see potential overlaps and eliminate confusing, conflicting policy outcomes before they take effect.
-
Modern User Experience: Manage your rules in a clean, intuitive Rules Management page. We heard you, it supports dark mode!
Automate your workflow with a new recast API.
Stop manual work and fully automate the creation and deployment of your Recast rules.
-
Recast API: Use the new Recast API to automate rule creation, modification, and deployment across your entire environment.
-
Seamless Integration: This allows you to integrate exception management directly into your existing security and ticketing workflows, enhancing operational speed.
For more information, see Recast Rules in the Tenable Vulnerability Management User Guide.
October 17, 2025
Tenable has added Tenable OT Security license usage to the License Information page in Tenable Vulnerability Management. This provides a more accurate and comprehensive view of total licensed IP consumption for Tenable OT Security customers.
For more information, see License Information in the Tenable Vulnerability Management User Guide.
October 15, 2025
Tenable has updated Tenable Vulnerability Management with the ability to create and configure scanner profiles. Scanner profiles allow you to configure a range of settings for a specific group of linked Tenable Nessus scanners.
You can use scanner profiles to:
-
Assign a specific scanner version for testing or standardization purposes.
-
Control how and when scanners receive plugin updates.
-
Determine what plugins Tenable Vulnerability Management installs on linked scanners during the daily plugin update.
You can manage scanner profiles in the Profiles tab under Sensors > Nessus Scanners in the Tenable Vulnerability Management user interface.
For more information, see Scanner Profiles in the Tenable Vulnerability Management Early Access User Guide.
October 8, 2025
Tenable has added the Accelerate plugin updates setting to agent profiles in Tenable Vulnerability Management. When enabled, this feature bypasses the standard agent check-in cycle to immediately deploy new plugin sets, accelerating the detection of emerging threats and reducing your organization's overall risk.
For more information, see Agent Profiles.
September 24, 2025
You can configure agent scans in Tenable Vulnerability Management to run by asset tag, agent group, or a combination of both. This enhancement increases flexibility and control when targeting specific sets of agents.
Tag-based scanning is available for scheduled agent scans (in other words, agent scans configured with a scan window). Tenable will add support to triggered agent scans in a future release.
For more information, see Basic Settings in the Tenable Vulnerability Management User Guide.
September 10, 2025
You can configure agent scans in Tenable Vulnerability Management to run by asset tag, agent group, or a combination of both. This enhancement increases flexibility and control when targeting specific sets of agents.
Tag-based scanning is available for scheduled agent scans (in other words, agent scans configured with a scan window). Tenable will add support to triggered agent scans in a future release.
For more information, see Basic Settings in the Tenable Vulnerability Management Early Access User Guide.
September 5, 2025
Tenable is pleased to announce the update of Tenable Lumin to use the updated scoring model for Tenable One applications.
You can see these changes across the Tenable Lumin user interface, for example, in the Recommended Actions section, where CES and AES metrics now use the new scoring model.
Check out the documentation for more information on new scoring.
July 22, 2025
Tenable is thrilled to announce the general availability of enhanced Tenable Vulnerability Priority Rating (VPR) in the new Explore views and the Vulnerability Intelligence section within Tenable Vulnerability Management. These updates enable you to:
-
Sharpen precision to focus on what matters most: While traditional CVSS scores classify 60% of CVEs as High or Critical, our original VPR reduced this to 3%. The enhanced VPR further refines this, helping your teams focus on just 1.6% of vulnerabilities that represent actual risk to your business by leveraging an even broader spectrum of threat intelligence and real-time data input used to predict near-term exploitation in the wild.
-
Unlock AI-driven insights and explainability: Our new LLM-powered insights deliver instant clarity, helping you quickly understand why an exposure matters, how it has been weaponized by threat actors, and providing clear, actionable guidance for mitigation and risk reduction. See Vulnerability Intelligence for more information.
-
Prioritize with industry and regional context: New metadata provides crucial context, helping you understand if a vulnerability is being targeted in your specific industry or geographic region.
-
Leverage advanced querying & filtering: The enhanced VPR model is easily accessible for filtering and querying in the new Explore views, enabling faster investigations and response workflows.
Original VPR and the enhanced VPR ('VPR (Beta)') scores will coexist for a period of time in Tenable Vulnerability Management. Future deprecation of the original VPR will be communicated in advance.
For more information, see:
June 13, 2025
Tenable has added the PCI Internal Nessus Agent scan template. This template allows you to perform an internal PCI DSS 4.0 credentialed vulnerability scan, and can be used to satisfy internal PCI DSS 4.0 scanning requirements for ongoing vulnerability management programs that satisfy PCI compliance requirements. PCI DSS 4.0 provides the ability to use a customized approach objective, giving you the most comprehensive view of local PCI vulnerabilities on your systems.
PCI Internal Nessus Agent expands Tenable's toolbox of PCI scanning capabilities. Used in tandem with the existing Internal PCI Network Scan (DSS 11.3.1.2), you can use the template achieve full internal coverage of your systems.
To learn more, see Scan Templates in the Tenable Vulnerability Management User Guide.
June 12, 2025
Tenable is excited to announce the release of agent safe mode in Tenable Vulnerability Management. When Tenable Agent experiences an error, the agent now automatically enters safe mode. While the agent is in safe mode, it cannot compile plugins or run scans, but it maintains connection with Tenable Vulnerability Management so that your organization can see that an error occurred, work to remediate the error, and remotely recover the agent.

Note: Agents on an earlier version than 10.9.0 do not have safe mode capabilities.
To learn more, see Agent Safe Mode in the Tenable Vulnerability Management User Guide.
June 5, 2025
Tenable is happy to share that Tenable Data Stream (TDS) now supports streaming of Tenable Vulnerability Management host audit findings data and Tenable Web App Scanning assets, tags, and findings data.
In addition to the new payloads, Tenable has added new fields in Tenable Vulnerability Management findings payload, such as Resurfaced Date and Time Taken to Fix.
Lastly, the grouping of the files written in the AWS S3 buckets is now based on timestamp. This reduces number of files written, thus improving consumption and reducing latency. Before this update, the grouping was determined by scan ID and timestamp, which caused Tenable Vulnerability Management to write a larger number of files.
For more information, see the Tenable Data Stream documentation in the Tenable Vulnerability Management User Guide.
May 20, 2025
Tenable is excited to announce the early access release of agent safe mode in Tenable Vulnerability Management. When Tenable Agent experiences an error, the agent now automatically enters safe mode. While the agent is in safe mode, it cannot compile plugins or run scans, but it maintains connection with Tenable Vulnerability Management so that your organization can see that an error occurred, work to remediate the error, and remotely recover the agent.

Note: Agents on an earlier version than 10.9.0 do not have safe mode capabilities.
To learn more, see Agent Safe Mode in the Tenable Vulnerability Management Early Access User Guide.
May 14, 2025
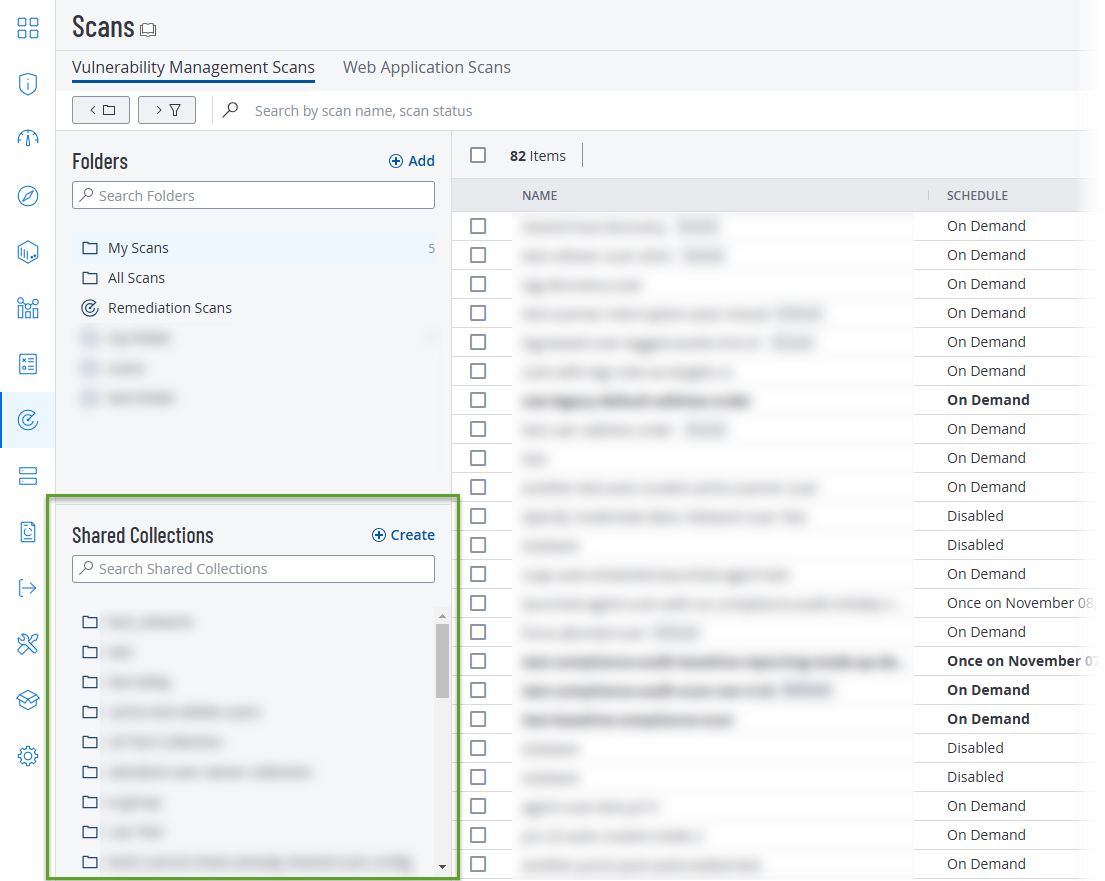
Tenable has added shared collections to the Scans menu. Shared collections allow you to quickly and conveniently share scan configurations with specific groups and other Tenable Vulnerability Management users.
You can use the Scans menu to create, edit, and delete shared collection, as well as add scan configurations to or remove scan configurations from shared collections.
To learn more, see Shared Collections in the Tenable Vulnerability Management User Guide.
May 13, 2025
Tenable is happy to share that Tenable Data Stream (TDS) now supports streaming of Tenable Vulnerability Management host audit findings data and Tenable Web App Scanning assets, tags, and findings data.
In addition to the new payloads, Tenable has added new fields in Tenable Vulnerability Management findings payload, such as Resurfaced Date and Time Taken to Fix.
For more information, see the Tenable Data Stream documentation in the Tenable Vulnerability Management Early Access User Guide.
May 12, 2025
Tenable is pleased to announce support for Common Vulnerability Scoring System Version 4.0 (CVSSv4) in Tenable Vulnerability Management.
To support this update, new filters and columns appear in the following areas:
-
On the Findings workbench.
-
In Explore, on the new Findings page.
-
On the Vulnerability Intelligence Overview page, in the CVEs, Findings, and My Affected Assets tabs.
-
In Exposure Response, under My Findings and Affected Assets and Combinations
To learn more about CVSSv4, see Common Vulnerability Scoring System Version 4.0 on the FIRST website.
May 8, 2025
Tenable is thrilled to announce some significant enhancements to your cloud product Workspace! We've redesigned the workspace to provide you with better visibility and access to Tenable products:
-
Improved Product Overview — You can now easily see both the products you've purchased and a range of other products available for exploration.
-
Detailed Product Information — Access More Details to demo the product, giving you in-depth knowledge about each product.
-
Product Utilization — We’ve added a utilization feature that shows the percentage of how much you’re using the subscribed products. It allows you to quickly direct you to the License Information page.
-
Trial Status Visibility — If you are currently evaluating a product or have done so within the past year, you will now see the status of the trial (In Trial or Trial Expired) directly in your workspace.
These changes are designed to help you get the most out of your Tenable solutions and discover new ways to enhance your security posture. To learn more, access the Workspace page via any Tenable cloud application.
May 7, 2025
Tenable is pleased to announce the following updates and enhancements to dashboards and widgets in Tenable Vulnerability Management:
-
Custom widget editing — When edited, custom widgets now seamlessly update on all the dashboards where they have been used.
-
Shared dashboard editing — When updating a shared dashboard, in a new dialog, easily re-share it with other users.
-
Custom widgets in custom reports — You can now add custom widgets to custom reports.
-
Dashboard ownership enhancements — When you delete a user in Access Control, their dashboards now transfer to a new owner.
To learn more, see the documentation for Dashboards and Reports in the Tenable Vulnerability Management User Guide.
April 30, 2025
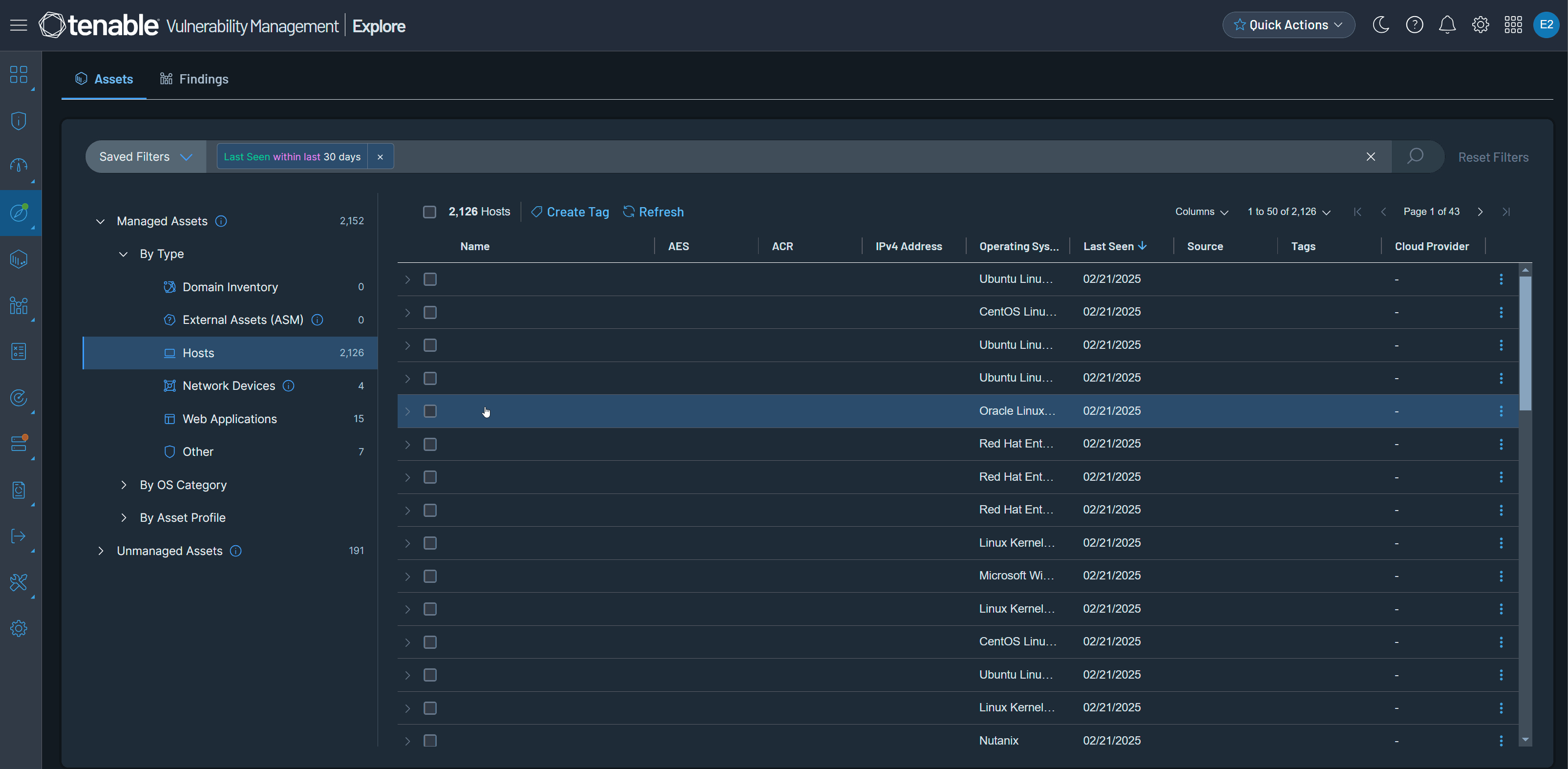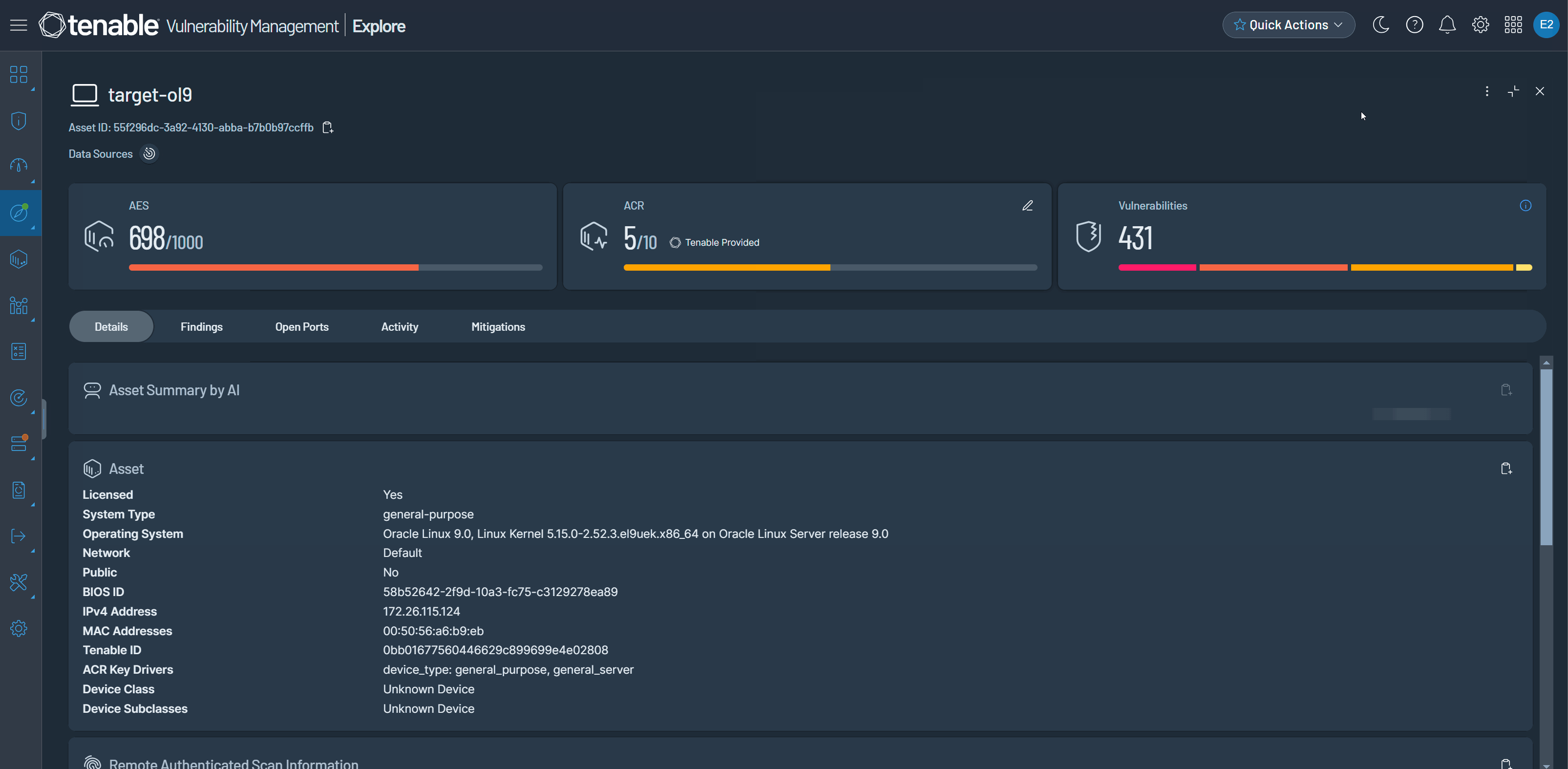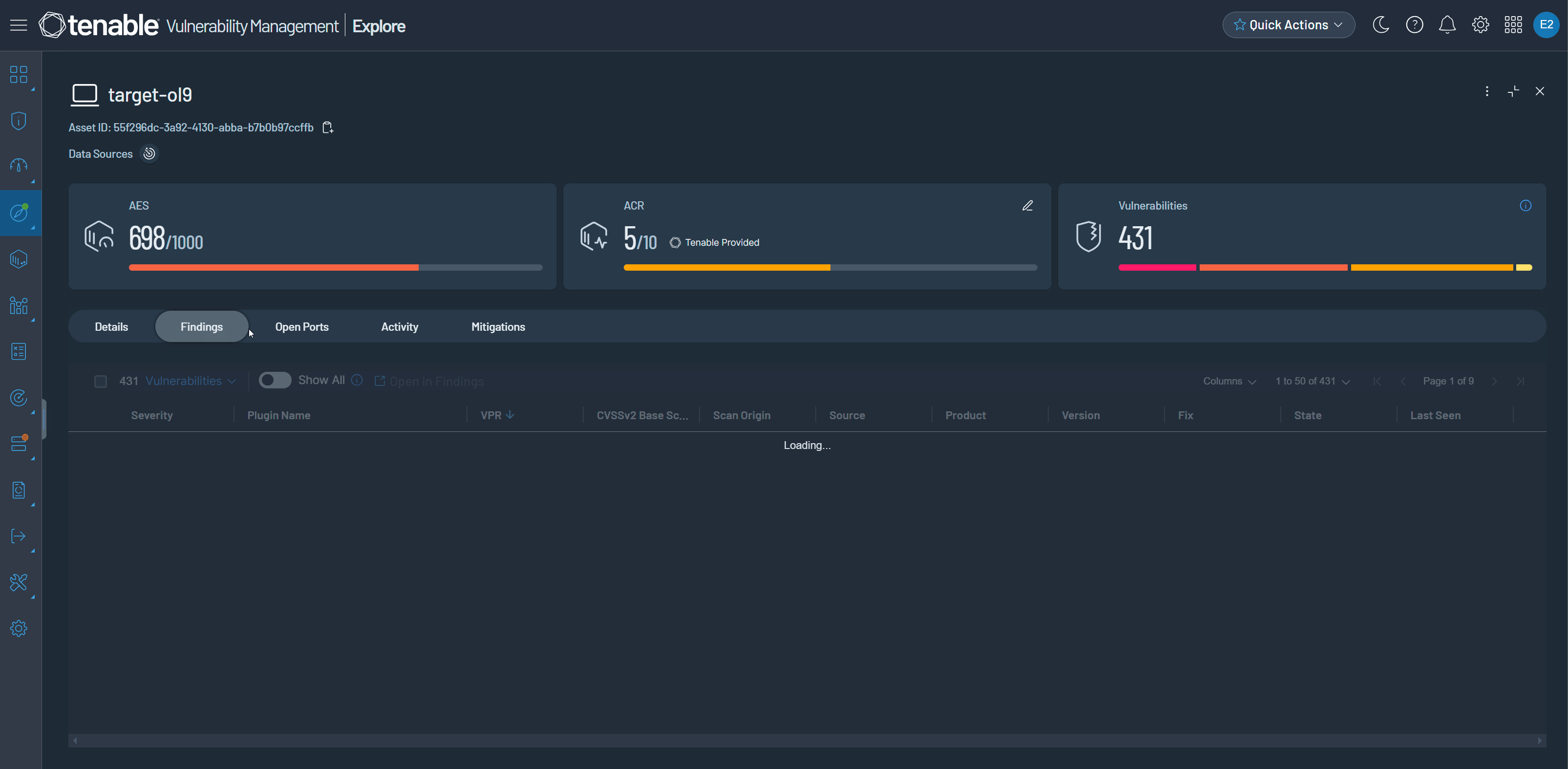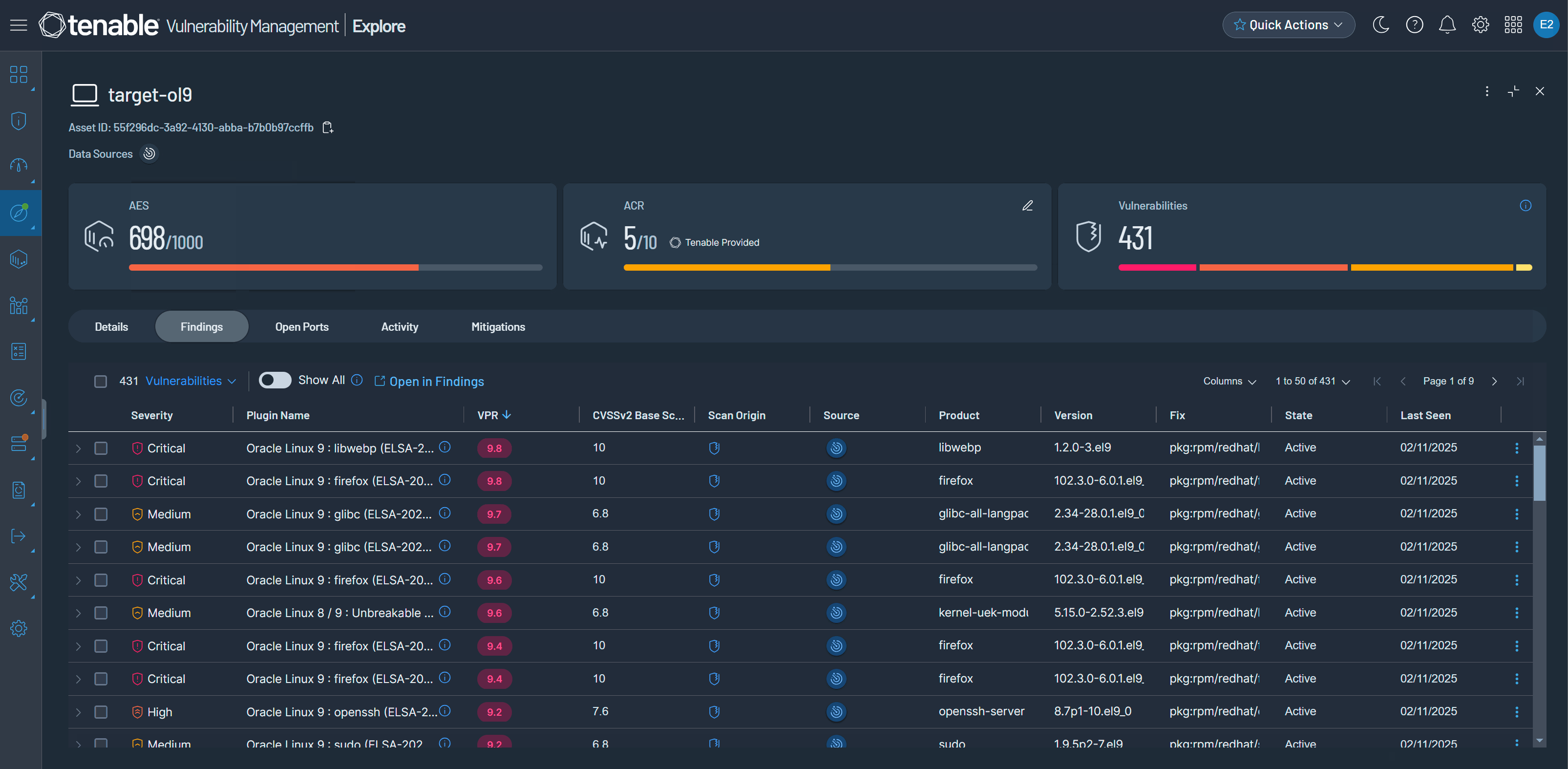
Tenable is pleased to announce Explore, an updated version of Assets and Findings. Explore has all the same features you currently use, plus many new ones—all in a streamlined design that highlights crucial details about your attack surface.
While Explore is being released as a preview which will run alongside Assets and Findings during a transition period, you can start using it right away as a replacement for the legacy pages.
In addition to its new design, Explore has the following new features:
-
Grouped resources — Group assets or findings and view them in drop-downs > designed like spreadsheet pivot tables.
-
Query builder — With the same easy-to-use query builder as the one in Exposure Response and Vulnerability Intelligence, build, save, and share custom lists using all the same filters, plus new ones.
-
New asset types — On the new Assets page, view assets by their profile or operating system, as described in Asset Types.
-
New asset filters — On the new Assets page, filter by Device Class, Device Subclass, and OS Category, as described in Asset Filters.
-
Add assets to scans — On the new Assets page, add assets to existing scans.
-
Findings by category — On the new Findings page, view findings by VPR, severity or state—or, for host audit findings, by the result of the audit. For more information, see Findings Types.
-
Software vulnerabilities — On the new Findings page, view information about software-related vulnerabilities in new columns: Product, Vendor, Product Type, Version, Path, Fix Type, and Fix. In addition, group Vulnerabilities by Product.
For complete coverage of these features, see Explore in the Tenable Vulnerability Management User Guide or contact your Tenable representative.
April 9, 2025
Tenable has added shared collections to the Scans menu. Shared collections allow you to quickly and conveniently share scan configurations with specific groups and other Tenable Vulnerability Management users.
You can use the Scans menu to create, edit, and delete shared collection, as well as add scan configurations to or remove scan configurations from shared collections.
To learn more, see Shared Collections in the Tenable Vulnerability Management Early Access User Guide.
Tenable is pleased to announce new metrics for Asset Criticality Rating (ACR) and Asset Exposure Score (AES) built on refined algorithms. The metrics appear as new filters and columns alongside the legacy ones on the Assets page, in Exposure Response, and in Vulnerability Intelligence. In June, they will replace the legacy ACR and AES metrics.
The following table defines the new metrics.
| Scoring Metric | Definition |
|---|---|
| ACR (Beta) |
The Tenable-defined Asset-Criticality Rating using a new algorithm which assigns assets to classes by business and device function. This metric rates the importance of an asset to your organization from 1 to 10, with higher numbers for more critical assets. For more information, see Scoring and Asset Criticality Rating. |
| AES (Beta) |
The Tenable-defined Asset Exposure Score using a new algorithm. This metric weighs an asset's Vulnerability Priority Rating (VPR) and Asset Criticality Rating (ACR) and then assigns a number from 1 to 1000, with higher numbers for more exposed assets. For more information, see Scoring (Beta). |
For more information, see Host Assets and Asset Filters in the Tenable Vulnerability Management User Guide. Note that the new columns are hidden by default; to show them, complete the steps in Use Tables.
March 19, 2025
In Vulnerability Intelligence, you can now export a PDF with details about each CVE entry to share with your organization. You can also schedule exports, email them, and password-protect them.
To learn more, see Export CVE Details in the Tenable Vulnerability Management User Guide or contact your Tenable representative.
March 17, 2025
Tenable is pleased to announce support for Common Vulnerability Scoring System Version 4.0 (CVSSv4) in Tenable Vulnerability Management.
To support this update, new filters and columns appear in the following areas:
-
On the Findings workbench.
-
In Explore, on the new Findings page.
-
On the Vulnerability Intelligence Overview page, in the CVEs, Findings, and My Affected Assets tabs.
-
In Exposure Response, under My Findings and Affected Assets and Combinations
To learn more about CVSSv4, see Common Vulnerability Scoring System Version 4.0 on the FIRST website.
February 18, 2025
Create a Google Cloud Platform connector with Workload Identity Federation authentication to discover Google Cloud Platform assets and import them to Tenable Vulnerability Management. For more information, see Create a GCP Connector with Workload Identity Federation Authentication.
January 29, 2025
Tenable has made the following enhancements to custom widgets for host audit data:
-
You can now choose these additional chart types for custom Host Audit widgets:
-
Multi-series bar
-
Multi-series column
-
Stacked bar
-
Stacked column
-
Matrix
-
To learn more, see Create a Custom Widget in the Tenable Vulnerability Management User Guide or contact your Tenable representative.
January 15, 2025
You can now view all IPV4 addresses for an affected asset on the Findings workbench as follows:
-
In a new All IP4v4 Addresses column.
-
On the Asset Details page under Asset Information.
-
When using findings filters.
To learn more, see Vulnerability Details in the Tenable Vulnerability Management User Guide.
January 9, 2025
Tenable is pleased to announce a new way to export your vulnerability data: Tenable Data Stream. With this new feature, you connect an AWS S3 bucket to Tenable Vulnerability Management, which then continuously sends your vulnerability data to your AWS bucket in JSON format. This feature is an alternative to the Tenable export APIs.
Once configured, Tenable Data Stream sends the following file types:
| File Type | Description |
|---|---|
| Assets payload |
New, updated, or deleted assets. |
| Findings payload |
New or updated findings. |
| Tags payload | New, updated, or deleted asset tags. |
| Manifest | Event logs for the payload files sent to your AWS bucket. |
For comprehensive documentation, see Tenable Data Stream in the Tenable Vulnerability Management User Guide.
Tenable Vulnerability Management now supports the ability to recast Host Audit data using custom roles. This means that custom role users can recast/accept Tenable Vulnerability Management, Tenable Web App Scanning, and Host Audit findings.
For more information, see Custom Roles in the Tenable Vulnerability Management User Guide.