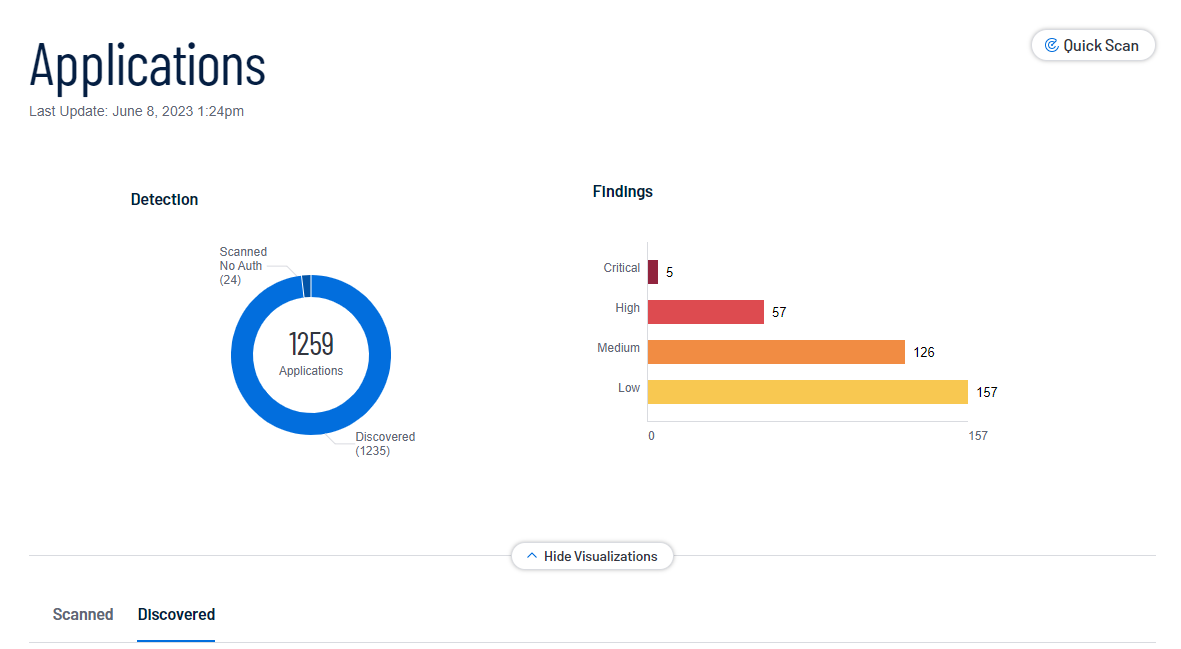
Discovered Applications
Required Tenable Web App Scanning User Role: Basic, Scan Operator, Standard, Scan Manager, or Administrator
On the Applications page, you can drill down to view only your Discovered applications.
Your Discovered applications are also populated from user-defined applications. You can create these using the Add Application button on the Applications page.
Before you begin:
- If you want to view applications in Tenable Web App Scanning generated from Tenable Attack Surface Management (ASM) assets, you need to create a Tenable Integration in the ASM platform. For more information, refer to Integrate with Tenable Web App Scanning in the Attack Surface Management User Guide.
To view your discovered applications:
-
In the left navigation plane, click
 Applications.
Applications.The Applications page appears. By default, the Scanned tab is visible and applications visualizations are shown.
-
In the lower-left, click the Discovered tab.
The Discovered applications list appears.
-
In the discovered applications assets table, you can perform any, or all, of the following actions by clicking the
 button:
button:-
Add Tag to your finding.
-
Remove Tag from your finding.
-
Delete the finding from your list.
You can view basic information about your discovered applications in the following table.
| Column | Description |
|---|---|
| Application ID | The UUID of the asset where a scan detected the vulnerability. This value is unique to Tenable Web App Scanning. |
| Created Date |
The time and date when Tenable Vulnerability Management created the asset record. |
| Domain | The domain name for the asset. |
| DNS (FQDN) (ASM) | The fully qualified domain name of the asset host. |
| First Seen |
The date when a scan first found the vulnerability on an application. |
| IP Address | The IP address for the asset, if any. |
| Host Name |
The hostname for the asset. |
| Hosting Provider | The hosting provider for the asset. |
| Last Seen |
Filter on the date that the asset was last observed by any successful scan, including vulnerability scans, configuration scans, and discovery scans. This value can also be the date that the asset was imported into Tenable Vulnerability Management. |
| Licensed | Specifies whether the asset is included in the asset count for Tenable Web App Scanning. |
| Name |
The asset name. Tenable Web App Scanning assigns this identifier based on the presence of certain asset attributes in the following order:
For example, if scans identify a NetBIOS name and an IPv4 address for an asset, the NetBIOS name appears as the asset name. This column appears in the table by default. |
| Port | The port associated with the asset. |
| Record Type | The type of asset. |
| Record Value | The value of the asset. |
| Source |
The source of the scan that identified the asset. Possible values include Agent for Tenable Agent, Nessus for Tenable Nessus, PVS/NNM for Tenable Network Monitor, and WAS for Tenable Web App Scanning. |
| Tags |
Filter and organize assets into logical groups (e.g., Network: Headquarters) for easier management and reporting. This filter is case-sensitive. You can add a maximum of 100 tags. For more information, see Tags. |
| Updated Date |
The time and date when a user last updated the asset. |
| Vulnerabilities | The number of vulnerabilities found on the scanned application. |