Getting Started
Scope of Assessment (Asset Identification)
Asset identification can be difficult for a variety of reasons, such as Shadow IT, Large and Diverse Inventories, and Virtual and Cloud Assets. Tenable simplifies asset identification with a variety of methods.
Active and Passive Scanning
Devices are detected through active scanning with Nessus and passive network analysis with Nessus Network Monitor to build a comprehensive list of assets and provide a clear picture of risk in the environment.
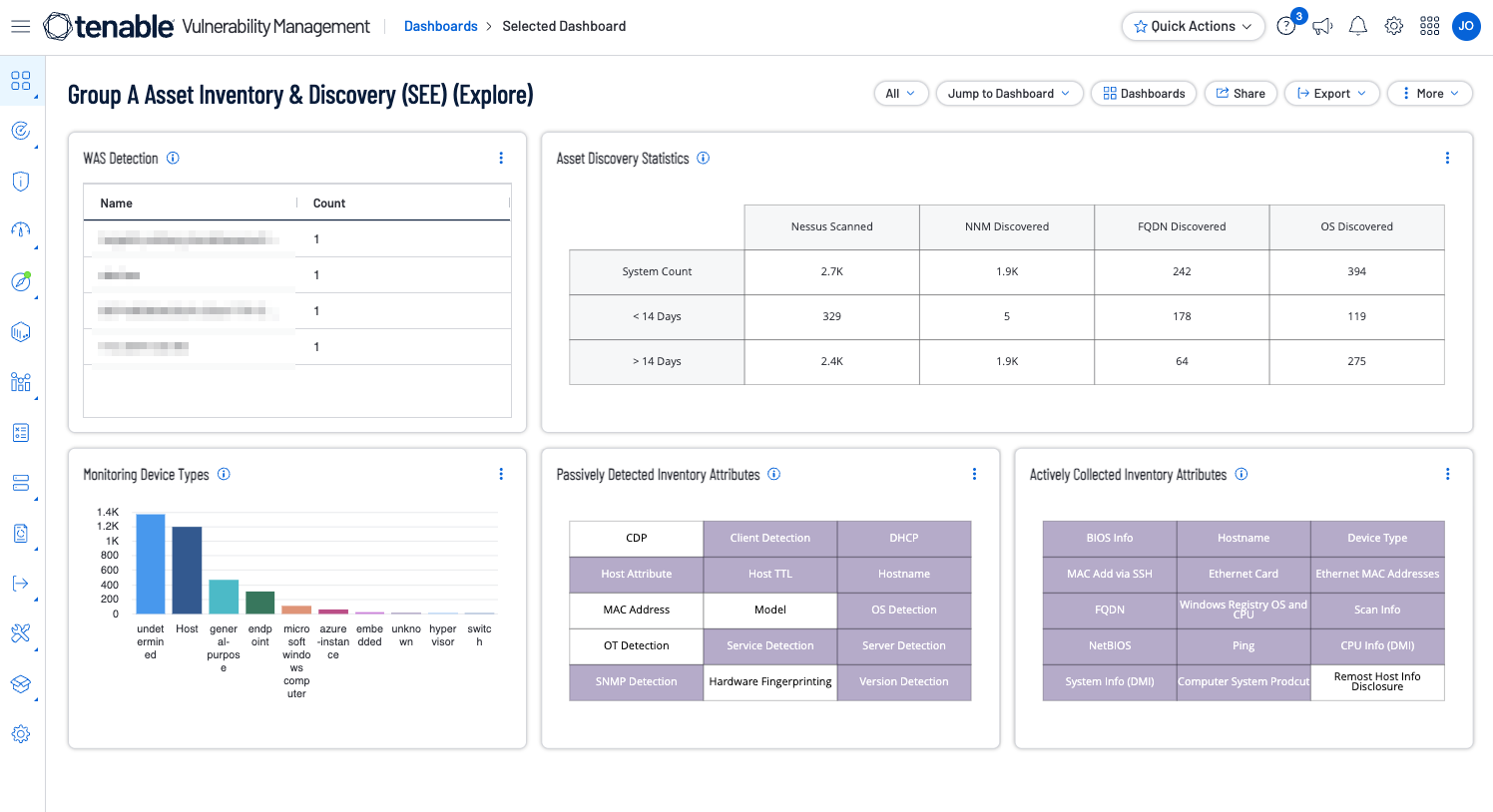
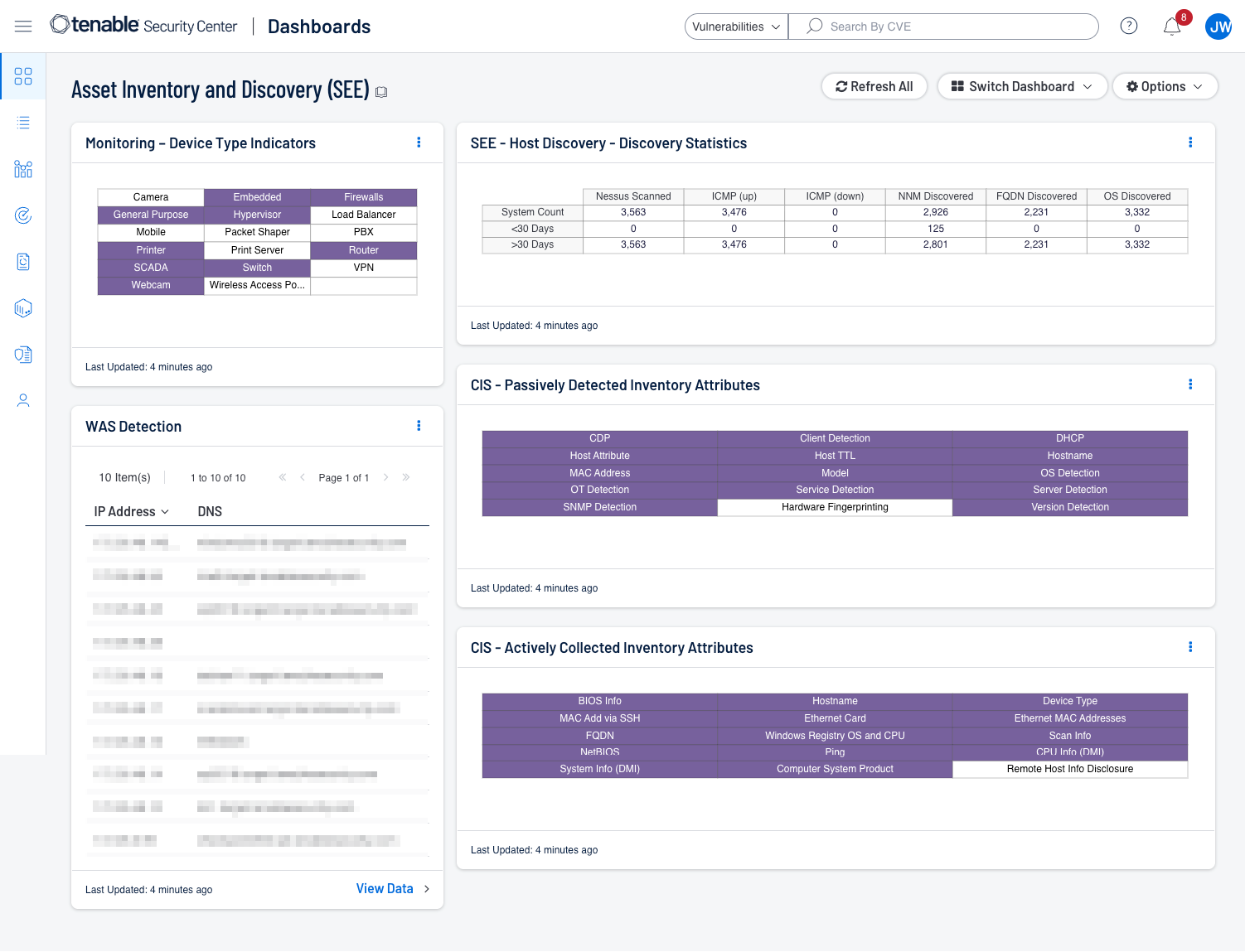
The Asset Inventory & Discovery (SEE) Tenable Vulnerability Management dashboard and the Asset Inventory & Discovery (SEE) Tenable.sc dashboard displayed the following provides guidance to establish an asset discovery, including:
-
Actively and passively detected assets
-
Asset discovery statistics
-
Detected web applications
-
Indications for device types (printers, cameras, routers, firewalls, WAPs)
For more information on Asset Discovery and Classification see the Asset Inventory and Discovery Cyber Exposure Study.
Tenable One (Exposure Management Platform)
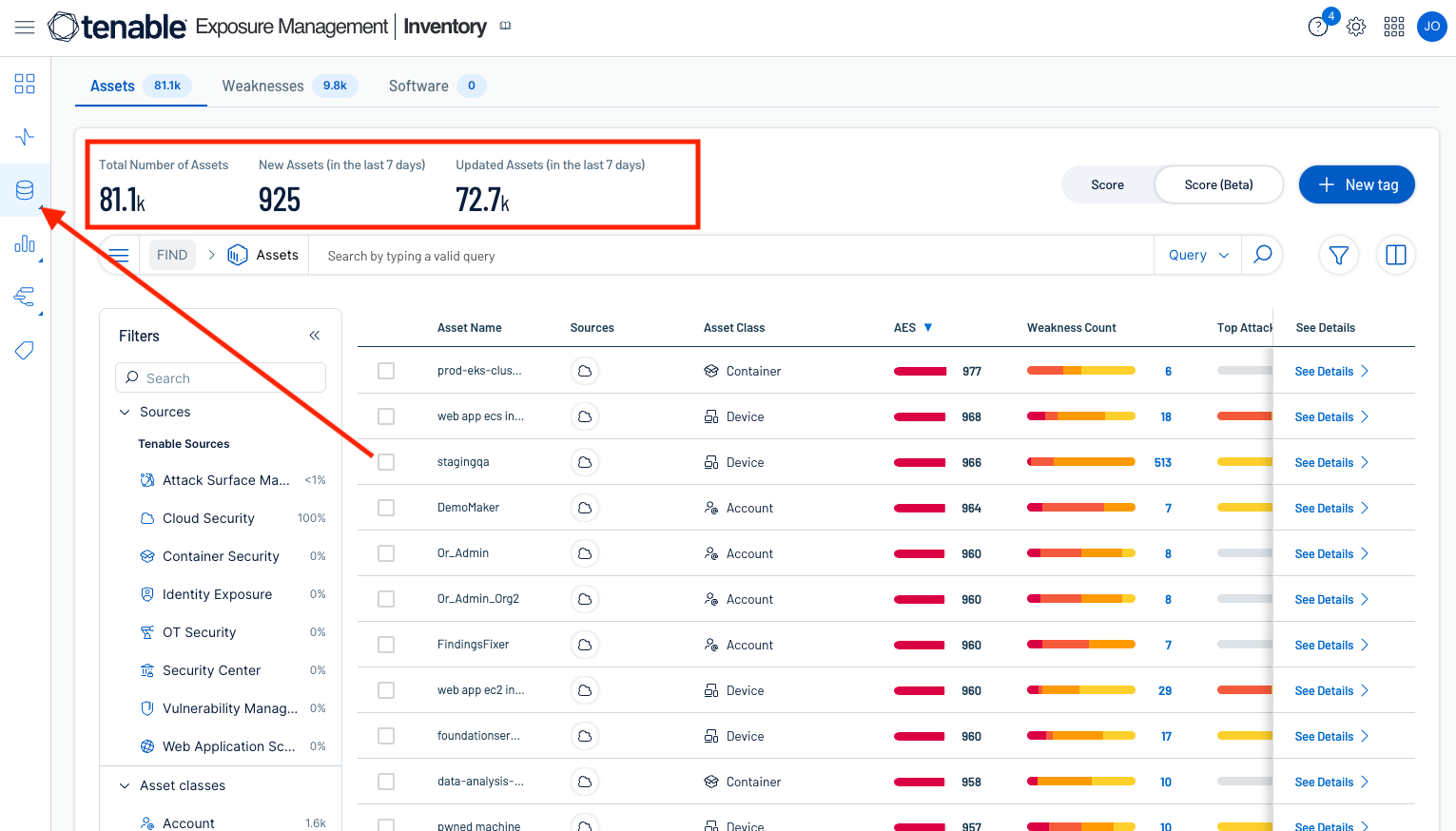
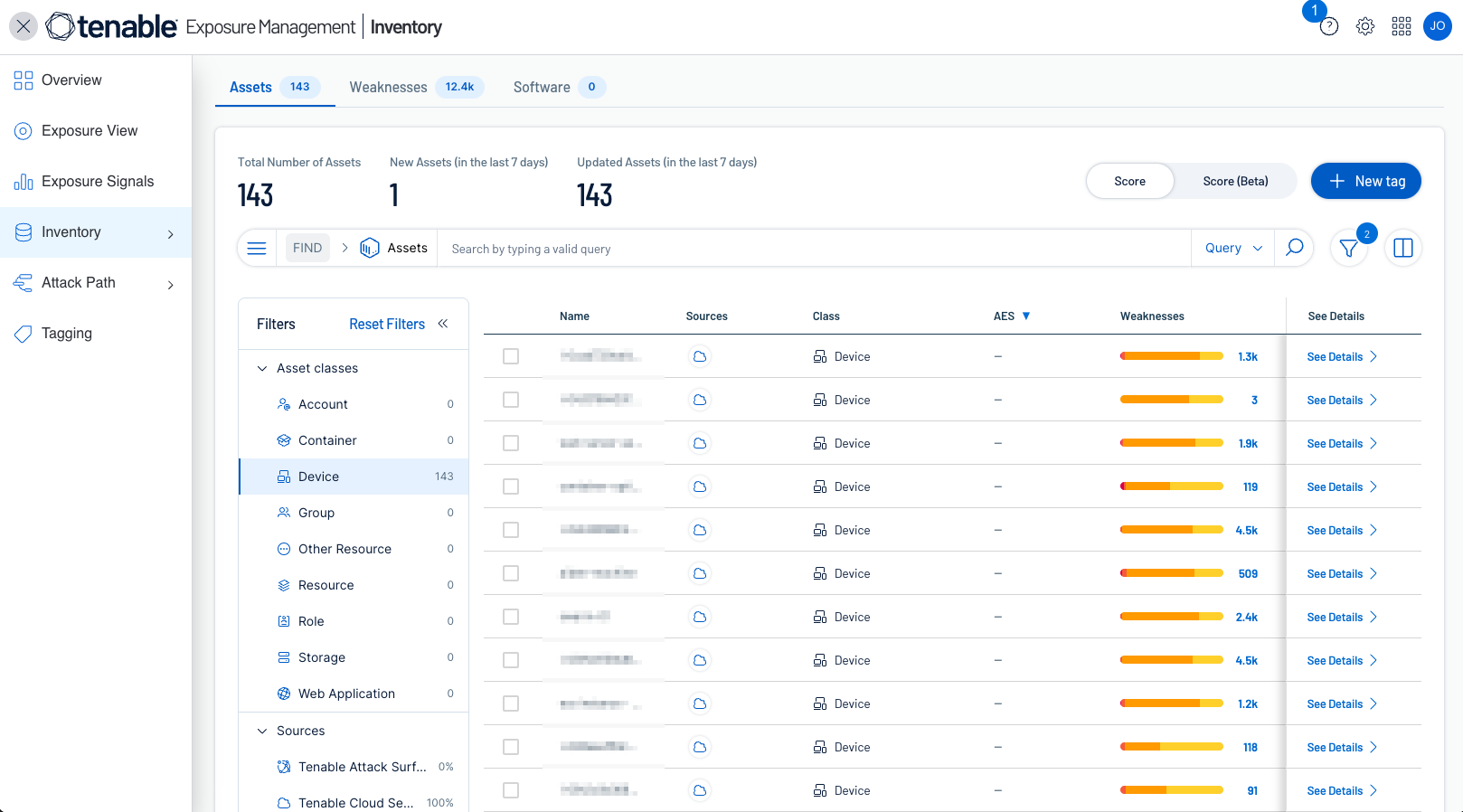
Products such as Tenable Exposure Manage can provide asset inventory details. The Inventory Page on Tenable Exposure Management aggregates all assets and their associated entities to unify and operationalise the data. It focuses on your organization's ability to maintain an accurate inventory for all of your cyber-enabled technologies while providing data analytics and a comprehensive inventory across various sources. While asset management highlights processes and people that can be affected, Tenable Exposure Management takes this one step further by digging into the technologies that can be hacked and allowing you to gain insight into these exposures.
The Inventory page is the central repository of all cyber assets across an organization's attack surface by providing:
-
A comprehensive list of all digital assets
-
A complete view of risks using enriched context
-
Built-in control, monitoring, and alerting
-
Unified asset analysis to drive prioritization
To access the inventory page first select the Inventory icon from the left navigation window, the Assets tab will display automatically, displaying asset counts on the top section.
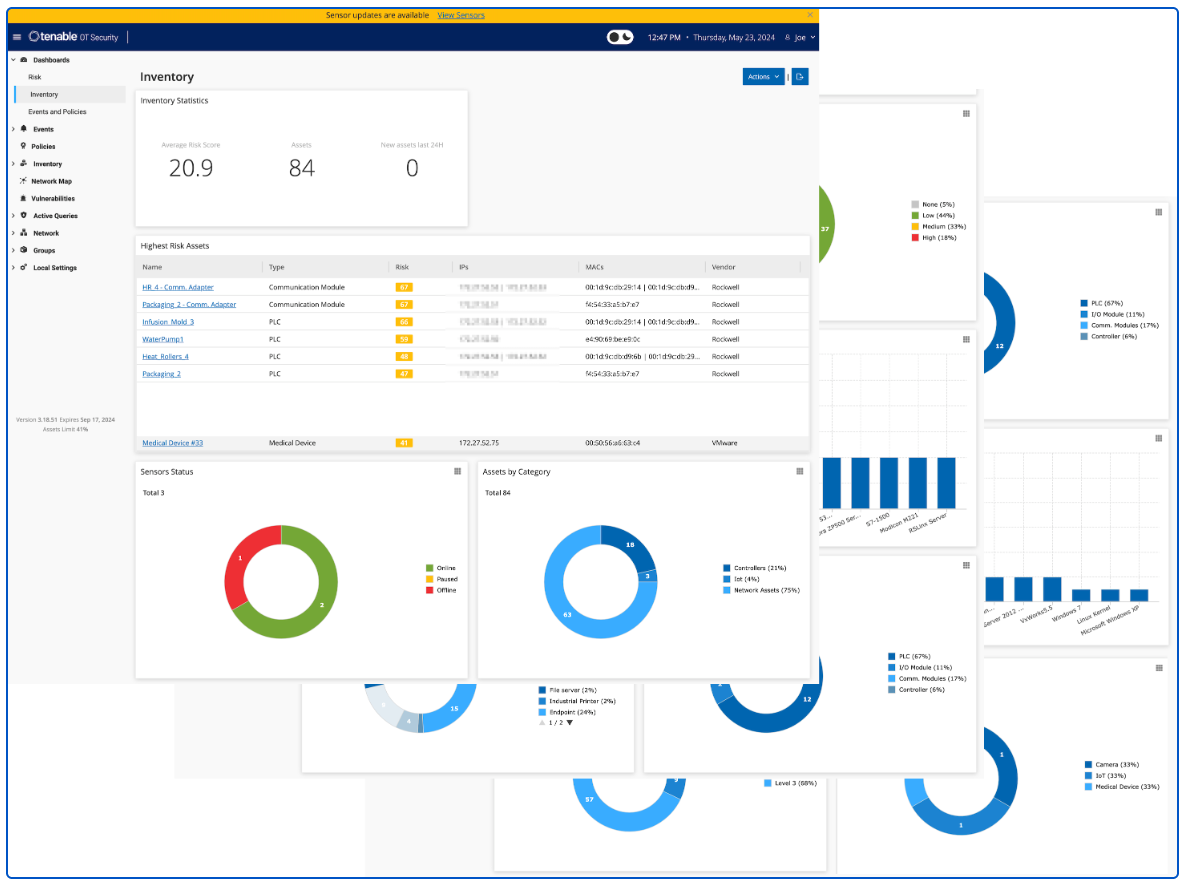
Tenable OT
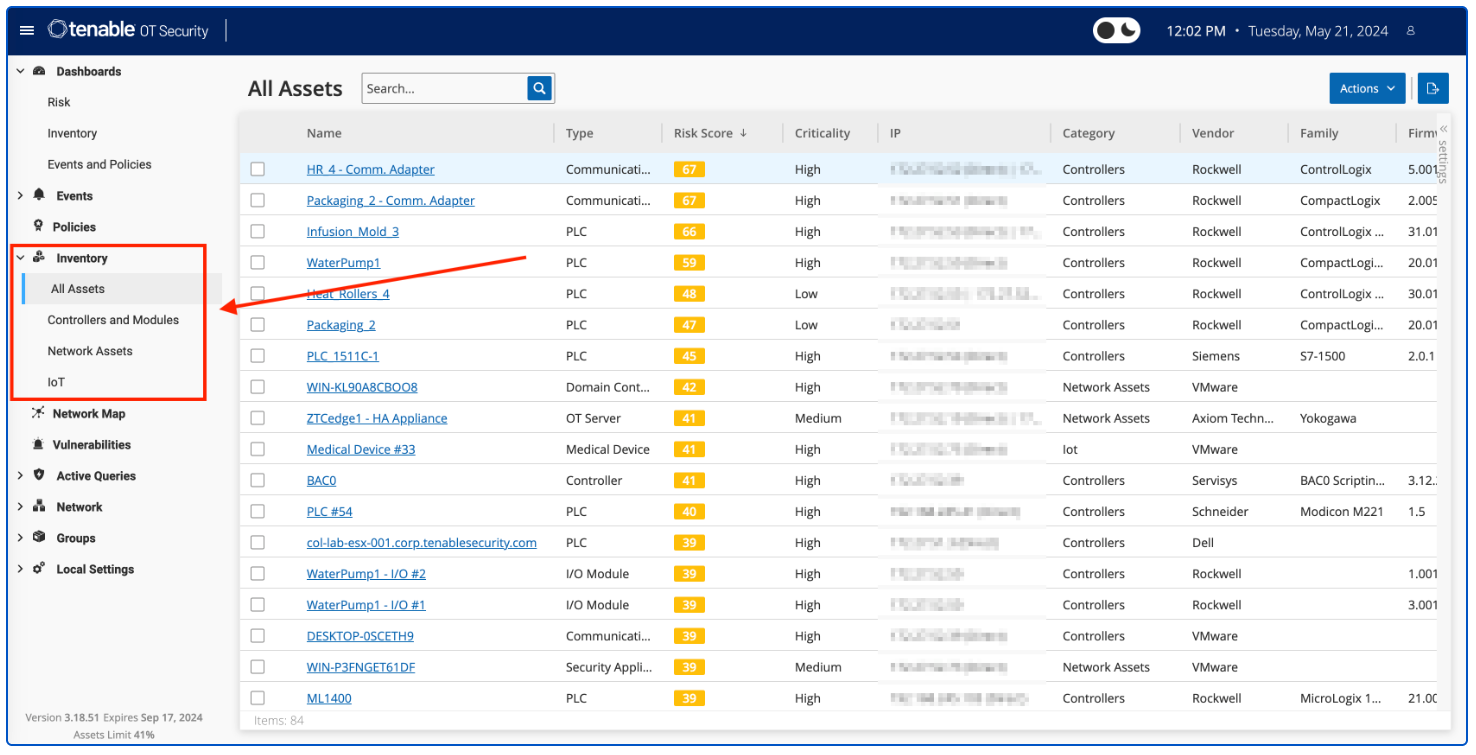
For organisations with industrial controls devices that are in scope, identification of IoT assets is accomplished with Tenable OT Security. Native communication protocols are used to query both Information Technology (IT) and Operational Technology (OT) devices in your Industrial Control Systems (ICS) environment in order to identify all of the activities and actions occurring across your network. All the assets in the network appear on the Inventory page. The Inventory page includes details about the asset that enables comprehensive asset management as well as monitoring of the status of each asset and its related events. OT Security collects this data using the Network Detection and Active Query capabilities.
The All Assets page shows data for all types of assets. Subsets of assets are shown on separate screens for each of the following asset types: Controllers and Modules, Network Assets, and IoT.
Tenable OT provides three in product dashboards that display assets in groupings such as by Category, Vendor, Module Type, Purdue Level, and more, facilitating asset management and tracking. Tenable OT Security provides a complete visibility of assets across the environment (IT and OT). A service called "Asset Gateway" receives asset information and tries to consolidate assets that have matching identifiers. In the case of an IT laptop, for example, we show "Sources" of Nessus, Agent, and Tenable OT Security all together. In the case of OT assets, they will not be merged into existing assets.
Tenable One is an exposure management platform, designed to allow customers to gain visibility across the entire modern attack surface. Tenable One focuses efforts to prevent likely attacks, and accurately communicate cyber risk to optimise business performance.
Tenable One Asset Inventory provides a comprehensive view of all assets across the entire attach surface. Sensors pull data from multiple applications across the platform, providing details on all known systems. At the highest level on the Asset Inventory page is shown the Number of Assets identified, New Assets identified in the last 7 days, and assets that have been updated in the last 7 days. Tenable One also integrates with third-party security tools to consolidate asset and vulnerability data, these integrations called Tenable One Connectors, allow organizations to ingest data from multiple sources, enriching asset inventory and enabling more effective risk assessment.
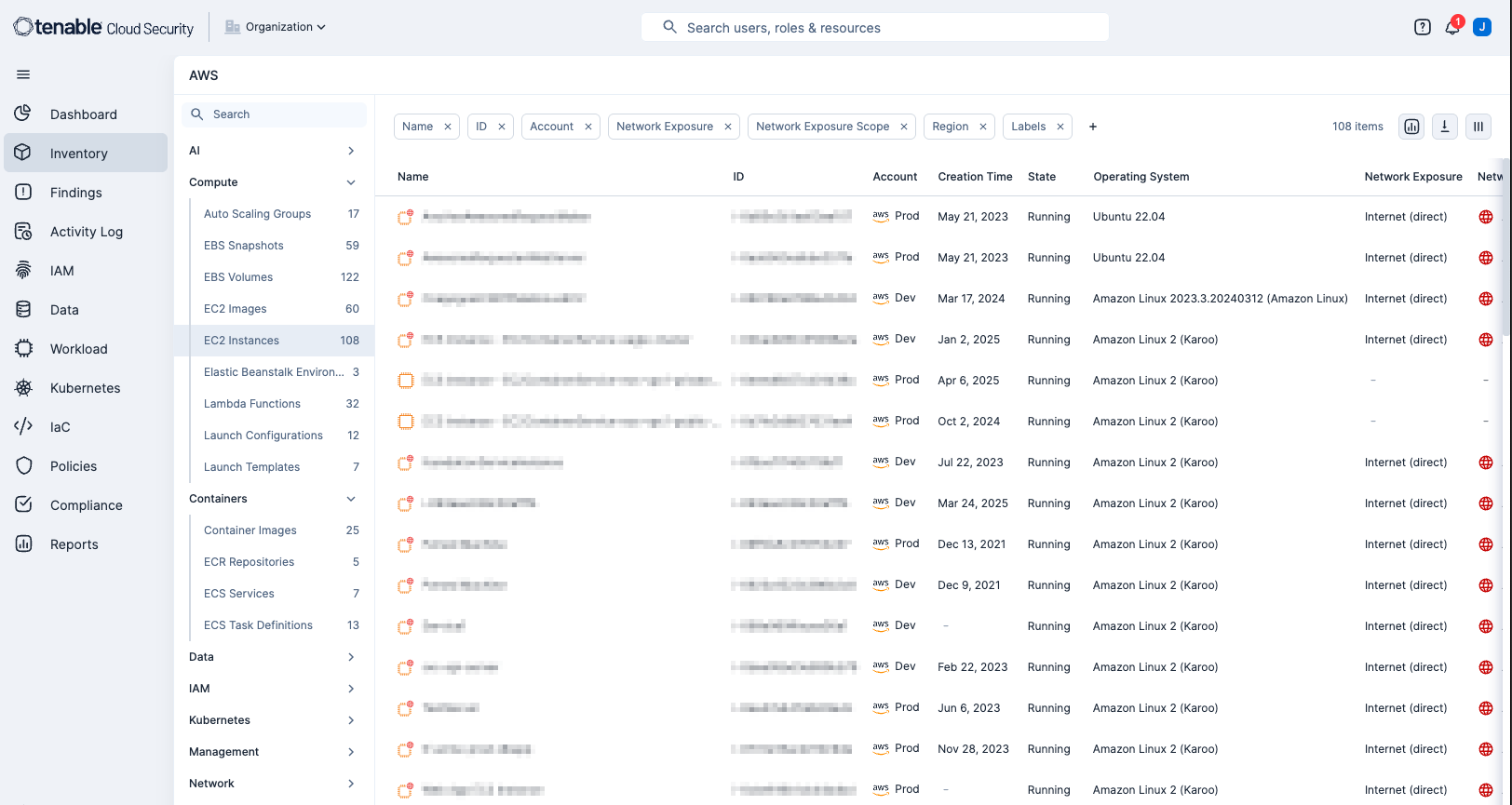
Tenable Cloud Security
Tenable Cloud Security is a Cloud Native Application Protection Platform (CNAPP) that assists organisations secure cloud environments. A few of Tenable Cloud Security’s benefits include automated asset discovery, assessing and prioritising risks, and detecting threats in real-time. Cloud assets can be easily and quickly identified by navigating to the Inventory page where assets are listed by categories, such as AI, Compute, Containers, and more. In the example displayed below, Compute Assets, specifically EC2 instances are displayed.
See Also