Outpost24 Connector
The following is not supported in Tenable FedRAMP Moderate environments. For more information, see the Tenable FedRAMP Product Offering.
The following steps allow you to configure this connector for use with Tenable Exposure Management from start to finish.
Connector Details
| Details | Description |
|---|---|
|
Supported products |
|
|
Category |
Endpoint Security |
|
Ingested data |
Assets and Findings |
|
Ingested Asset Classes |
Device Web Application |
|
Integration type |
UNI directional (data is transferred from the Connector to Tenable Exposure Management in one direction) |
|
Supported version and type |
SaaS (latest) |
Prerequisites and User Permissions
Before you begin configuring the connector, make sure to:
-
Identify your Outpost Outscan Server URL (e.g., https://outscan.outpost24.com)
-
Generate Outpost credentials (username and password).
Generate Outpost Credentials
-
Log in to the Outpost24 platform.
-
Click your account name in the upper-right corner, then select IAM.
-
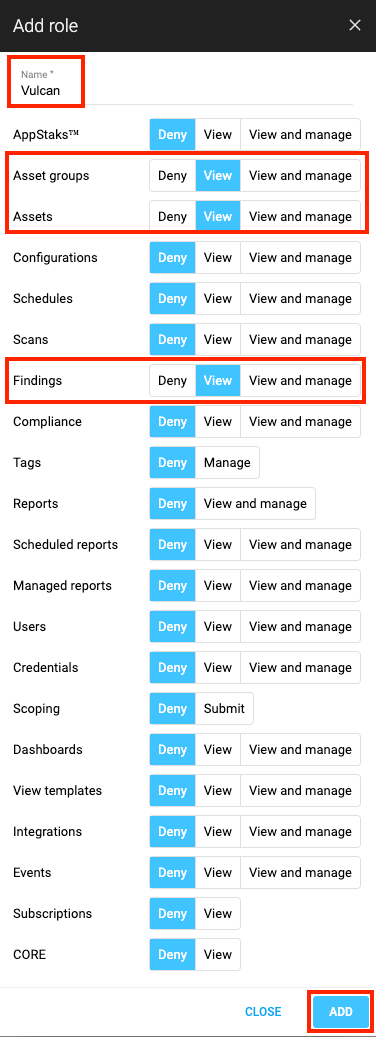
In the Roles tab, click + Add role.
-
Name the role Exposure Management or Tenable (or another preferred name).
-
Grant View permissions to Asset groups, Assets, and Findings.
-
Click Add to create the role.
-
In the Users tab, click + Add user.
-
Fill in the required details:
-
Provide a unique username.
-
Use a valid email address (a temporary password will be sent here).
-
-
Click Add.
-
Retrieve the password from the email. (Optional: log in and update the password.)
Assign the Role and Resource Groups
-
Log in ti the Outpost24 platform.
-
In the Users tab, select the checkbox of the newly created user.
-
Click Assign roles and check the role you created earlier.
-
Click Assign.
-
Click Assign resource groups, select the relevant resource groups, and click Assign.
Configure NetSec Permissions (Read only)
-
Log in ti the Outpost24 platform.
-
In the left navigation panel, click NetSec.
-
In the bottom-left, click the target icon, then Navigate to: NetSec > Settings > Manage Users.
-
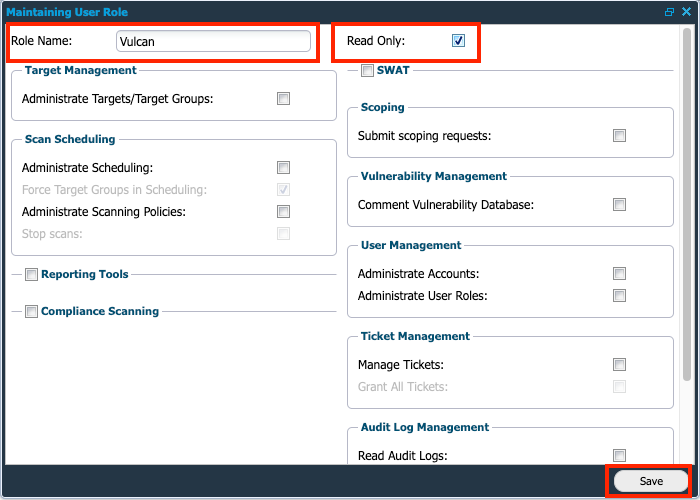
In Manage User Accounts, navigate to the User Roles tab and click + New.
-
Enter the role name you greated earlier, check Read Only, and click Save.
-
In the User Accounts tab, right-click the same user and select Edit.
-
In the Account Settings tab:
-
Navigate to the Granted Targets tab and uncheck Not all Targets Granted.
-
Navigate to the Attributes tab.
-
In the Uri field, enter a unique string.
-
Click Save.
Add a Connector
To add a new connector:
-
In the left navigation menu, click Connectors.
The Connectors page appears.
-
In the upper-right corner, click
 Add new connector.
Add new connector.The Connector Library page appears.
-
In the search box, type the name of the connector.
-
On the tile for the connector, click Connect.
The connector configuration options appear.
Configure the Connector
To configure the connector:
-
(Optional) In the Connector's Name text box, type a descriptive name for the connector.
-
(Optional) To use a preconfigured on-prem connector to connect to this connector, from the Gateway drop-down, select the on-prem connector you want to use for the connector. Otherwise, select Don't use gateway.
Note: For information about configuring a gateway, see Tenable On-Prem Connector. -
In the Server URL section, type the URL for your Outpost24 server.
-
In the Username and Password text boxes, paste the user credentials you generated in Outpost24.
-
In the Data pulling configuration section, you can configure dynamic settings specific to the connector.
-
(Optional) To fetch NetSec assets and vulnerabilities from Outpost24, select the Fetch NetSec assets and vulnerabilities check box.
-
In the Asset Retention text box, type the number of days after which you want assets to be removed from Tenable Exposure Management. If an asset has not been detected or updated within the specified number of days, it is automatically removed from the application, ensuring your asset inventory is current and relevant.
Tip: For more information, see Asset Retention.
-
-
In the Test connectivity section, click the Test Connectivity button to verify that Tenable Exposure Management can connect to your connector instance.
-
A successful connectivity test confirms that the platform can connect to the connector instance. It does not, however, guarantee that the synchronization process will succeed, as additional syncing or processing issues may arise.
-
If the connectivity test fails, an error message with details about the issue appears. Click Show tests for more information about the exact error.
-
-
In the Connector scheduling section, configure the time and day(s) on which you want connector syncs to occur.
Tip: For more information, see Connector Scheduling. -
Click Create. Tenable Exposure Management begins syncing the connector. The sync can take some time to complete.
-
To confirm the sync is complete, do the following:
-
Navigate to the Connectors page and monitor the connector's status. Sync is complete once the connector status is Connected.
-
View the sync logs for the connector to monitor the logs for a successful connection.
-
Outpost 24 in Tenable Exposure Management
Locate Connector Assets in Tenable Exposure Management
As the connector discovers assets, Tenable Exposure Management ingests those devices for reporting.
To view assets by connector:
-
In Tenable Exposure Management, navigate to the Assets page.
-
In the Filters section, under 3rd Party Connectors, click the connector name for which you want to view assets.
The asset list updates to show only assets from the selected connector.
-
Click on any asset to view Asset Details.
Locate Connector Weaknesses in Tenable Exposure Management
As the connector discovers weaknesses, Tenable Exposure Management ingests those weaknesses for reporting.
To view weaknesses by connector:
-
In Tenable Exposure Management, navigate to the Weaknesses page.
-
In the Filters section, under 3rd Party Connectors, click the connector name for which you want to view weaknesses.
The weaknesses list updates to show only weaknesses from the selected connector.
-
Click on any weakness to view Weakness Details.
Locate Connector Findings in Tenable Exposure Management
As the connector discovers individual findings, Tenable Exposure Management ingests those findings for reporting.
To view findings by connector:
-
In Tenable Exposure Management, navigate to the Findings page.
-
In the Filters section, under 3rd Party Connectors, click the connector name for which you want to view findings
The findings list updates to show only assets from the selected connector.
-
Click on any asset to view Finding Details.
Data Mapping
Exposure Management integrates with the connector via API to retrieve relevant weakness and asset data, which is then mapped into the Exposure Management system. The following tables outline how fields and their values are mapped from the connector to Exposure Management.
Device Mapping
| Tenable Exposure Management UI Field |
Outpost24 Field |
|---|---|
| Unique Identifier |
id |
| Asset - Name |
hostname or name |
| Asset - Operating Systems |
os |
| Asset - First Observation Date | firstSeen or created |
| Asset - Last Observed At |
lastSeen or updated |
|
Asset - External Tags |
source businessCriticality exposed assetIdentifiers |
| Asset Custom Attributes |
tags groups |
Finding Mapping (for Device)
| Tenable Exposure Management UI Field |
Outpost24 Field |
|---|---|
| Unique Identifier |
asset id + id + Unique Vulnerability id |
| Finding Name |
name |
| CVEs |
cve |
| CWEs | cwe |
| Severity Driver |
nvdCvssV3Score or cvssV3Severity or nvdCvssV2Score |
| Description |
description |
| Port | port |
| Protocol | protocol |
| First Seen |
firstSeen or created |
| Last seen (Observed) |
lastSeen |
| Finding Custom Attributes |
packageName or presentableName vulnId or id softwareComponent cyrating hasExploits exploitProbability nvdCvssV3Vector |
Web Application Mapping
| Tenable Exposure Management Value |
Outpost24 Value |
|---|---|
| Unique Identifier |
id |
| Asset - Name |
name |
| Asset - First Observation Date |
firstSeen or created |
| Asset - Last Observed At |
lastSeen or updated |
|
Asset - External Tags |
tags groups |
| Asset Custom Attributes |
source asset_identifiers |
Finding Mapping (for Web Application)
| Tenable Exposure Management UI Field |
Outpost24 Field |
|---|---|
| Unique Identifier |
asset id + match id + Unique Vulnerability id |
| Finding Name |
name |
| CVEs |
cve |
| CWEs | cwe |
| Severity Driver |
nvdCvssV3Score or cvssV3Severity or nvdCvssV2Score |
| Description |
description |
| First Seen |
firstSeen or created |
| Last seen (Observed) |
lastSeen |
| Finding Custom Attributes |
url source port protocol id softwareComponent cyrating hasExploits exploitProbability nvdCvssV3Vector |
Finding Status Mapping
|
Tenable Exposure Management Status |
[Connector] Status |
|---|---|
|
Active |
PRESENT isAccepted:false (for NetSec) FALSE_POSITIVE IRREPRODUCIBLE REJECTED ACCEPTED isAccepted:true (for NetSec) TO_PUSH TO_QA PENDING_VERIFICATION TO_REVIEW TO_VERIFY |
|
Fixed |
FIXED |
Note:For Outpost24, Tenable Exposure Management uses the findings_status field to determine finding status.
Finding Severity Mapping
|
Tenable Exposure Management Severity |
[Connector] Score |
|---|---|
|
Critical |
CVSS: 9.0 - 10.0 Severity: Critical |
|
High |
CVSS: 7.0 - 8.9 Severity: High |
|
Medium |
CVSS: 4.0 - 6.9 Severity: Medium |
|
Low |
CVSS: 1-3.9 Severity:Low |
|
None |
CVSS:0 Severtity: empty |
Note:For Outpost24, Tenable Exposure Management uses the nvdCvssV3Score or cvssV3Severity or nvdCvssV2Score field to determine severity.
Status Update Mechanisms
Every day, Tenable Exposure Management syncs with the vendor's platform to receive updates on existing findings and assets and to retrieve new ones (if any were added).
The table below describes how the status update mechanism works in the connector for findings and assets ingested into Tenable Exposure Management.
|
Update Type in Tenable Exposure Management |
Mechanism (When?) |
|---|---|
|
Archiving Assets |
|
|
Change a Finding status from "Active" to "Fixed" |
|
Uniqueness Criteria
Tenable Exposure Management uses defined uniqueness criteria to determine whether an ingested asset or finding should be recognized as a distinct record. These criteria help define how assets and findings are identified and counted from each connector.
Tip: Read all about Third-Party Data Deduplication in Tenable Exposure Management
The uniqueness criteria for this connector are as follows:
|
Data |
Uniqueness Criteria |
|---|---|
|
Asset |
id |
|
Finding |
asset id + id + Unique Vulnerability id |
| Detection |
Website / cloud resource: checkId Host: vulnId |
| Solution | solutionUuid |
Support Limitations and Expected Behavior
This section outlines any irregularities, expected behaviors, or limitations related to integration of the connector and Exposure Management. It also highlights details about ingested and non-ingested data to clarify data handling and functionality within this integration.
Some customers use the NetSec module in Outpost24, which includes host data collected from agents running on machines. In these cases, certain hosts may appear in NetSec but not in the Outpost24 Portal interface.
The Exposure Management connector ingests data from both the Portal and NetSec, which may result in assets appearing in Exposure Management that are not visible in the Outpost24 Portal.
Outpost24 does not differentiate between asset types (e.g., devices vs. web applications). As a result, it may represent multiple asset types as a single entity.
Exposure Management, however, distinguishes between asset types. This difference may lead to apparent duplication of assets in Exposure Management.
Example:
If an Outpost24 agent is installed on a machine that also hosts a web application:
-
Outpost24 displays this as a single asset.
-
Exposure Management displays two distinct assets: one as a device, and another as a Web Application.
This behavior is expected and results from Exposure Management granular asset classification model.
API Endpoints in Use
API version: v1.0
|
API |
Use in Tenable Exposure Management |
Required Permissions |
|---|---|---|
|
/opi/rest/auth/login |
Token generation |
None |
|
/opi/rest/outscan/targets |
Assets (devices) |
Read Only for all targets |
|
/opi/rest/outscan/findings |
Findings, Assets enrichment |
Read Only for all targets |
| /opi/rest/checks | Detections | View Findings |
| /opi/rest/assets | Assets (Web applications) | View Assets |
| /opi/rest/findings | Findings | View Findings |
| /opi/rest/matches | Findings | View Findings |
| /opi/rest/checks | Detections | View Findings |
| /opi/rest/asset-groups | Asset enrichment (tags) | View Asset Groups |
Data Validation
This section outlines how to validate and compare data between Tenable Exposure Management and the Outpost24 platform.
Asset Data Validation
Objective: Ensure that the number of assets in Outpost24 aligns with the number of assets displayed in Tenable Exposure Management.
In Outpost24:
-
Navigate to the Assets section and select the Assets tab.
-
Apply a filter on the Source column based on asset type:
-
Select NETSEC and VERIFY to view device assets.
-
Select CLOUDSEC to view resources.
-
Select all other sources (excluding the above) to view web applications.
-
-
At the top of the list, select the checkbox next to Name to highlight all items.
-
At the bottom of the screen, review the total number of filtered assets.
Note: Some customers use the NetSec module, which includes agents running on machines. These hosts may not appear in the Portal but are ingested into Tenable Exposure Management.Tenable Exposure Management displays all NetSec and Portal data sources, which may lead to a higher asset count.
In Tenable Exposure Management:
-
Compare the total number of assets between Outpost24 and Tenable Exposure Management.
Expected outcome: Asset counts may not align exactly due to Outpost24 grouping multiple asset types under a single entry, whereas Tenable Exposure Management separates these into distinct asset types (for example, device vs. web application).
If an asset is not visible in Tenable Exposure Management, check the following conditions:
-
The asset was archived based on the last observed date (last seen).
-
The asset was archived because it did not return in the connector's next sync.
Tip: To learn more on how assets and findings change status, see Status Update Mechanisms.
Finding Data Validation
Objective: Ensure that the number of findings in Outpost24 aligns with the number of findings displayed in Tenable Exposure Management.
In Outpost24 Portal:
-
Navigate to the Assets section and select the Assets tab.
-
Apply a filter on the Source column based on asset type:
-
Select NETSEC and VERIFY to view device assets.
-
Select CLOUDSEC to view resources.
-
Select all other sources (excluding the above) to view web applications.
-
-
Select the checkbox next to Name for all applicable assets.
-
At the bottom of the screen, click Generate Report.
-
In the wizard:
-
Select the Vulnerabilities report type.
-
Choose Detailed.
-
Uncheck PDF and select Excel format.
-
Choose Custom date range from 1999-01-01 to the current date.
-
-
Download the generated Excel file from the cloud icon.
-
Open the Risk Details sheet to view all findings.
In Outpost24 NetSec:
-
Navigate to NetSec > Reporting Tools.
-
Select the relevant Target Group (e.g., All Targets).
-
Click Export Report.
-
Set:
-
Format: Excel
-
Report Type: Vulnerability
-
Target Summary: All Selected Targets
-
-
Download and open the file.
-
Review the Vulnerability Details sheet to see all findings.
In Tenable Exposure Management:
-
Compare the total number of findings between Outpost24 and Tenable Exposure Management.
Expected outcome: Finding counts may differ slightly due to data granularity or filtering differences. Outpost24 may present one asset with multiple findings collapsed, whereas Tenable Exposure Management separates them per asset and source.
If a finding is missing from Tenable Exposure Management or no longer active, check the following conditions:
-
The finding is marked as Fixed and appears under the Fixed state on the Findings screen
-
The finding no longer appears because its related asset was archived.
Tip: To learn more on how assets and findings are archived or change status, see Status Update Mechanisms.