Qualys Connector
The following is not supported in Tenable FedRAMP Moderate environments. For more information, see the Tenable FedRAMP Product Offering.
The following steps allow you to configure this connector for use with Tenable Exposure Management from start to finish.
Connector Details
| Details | Description |
|---|---|
|
Supported products |
|
|
Category |
Endpoint Security |
|
Ingested data |
Assets and Findings |
|
Ingested Asset Classes |
Device |
|
Integration type |
UNI directional (data is transferred from the Connector to Tenable Exposure Management in one direction) |
|
Supported version and type |
SaaS (latest) |
Prerequisites and User Permissions
Before you begin configuring the connector, make sure to:
-
Identify your Qualys API Server URL.
-
Create a Qualys user with the Scanner role and API access enabled.
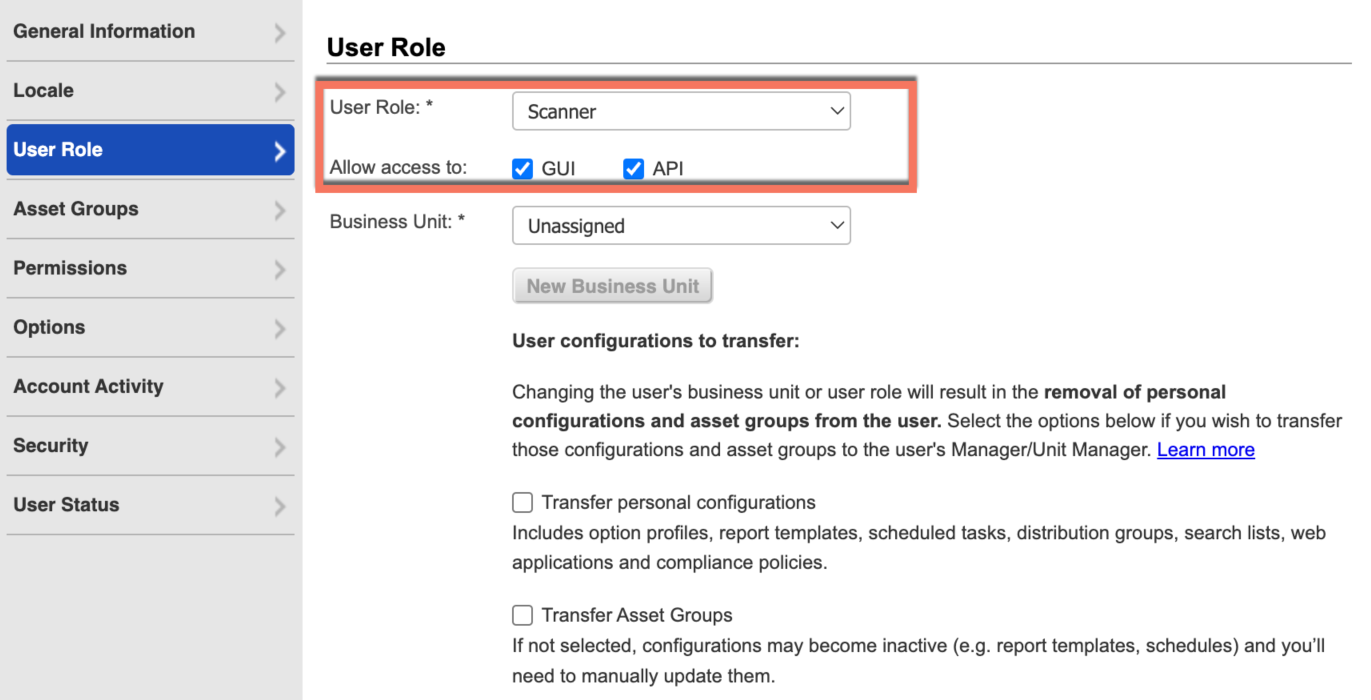
Create a Qualys User with the Scanner Role and API Access Enabled
-
Log in to the Qualys platform.
-
Click User Role, and assign the Scanner role to the user.
-
Enable access to GUI and API.
-
Click Asset Groups and assign the relevant asset groups to the user.
-
Click Save to create the user.
-
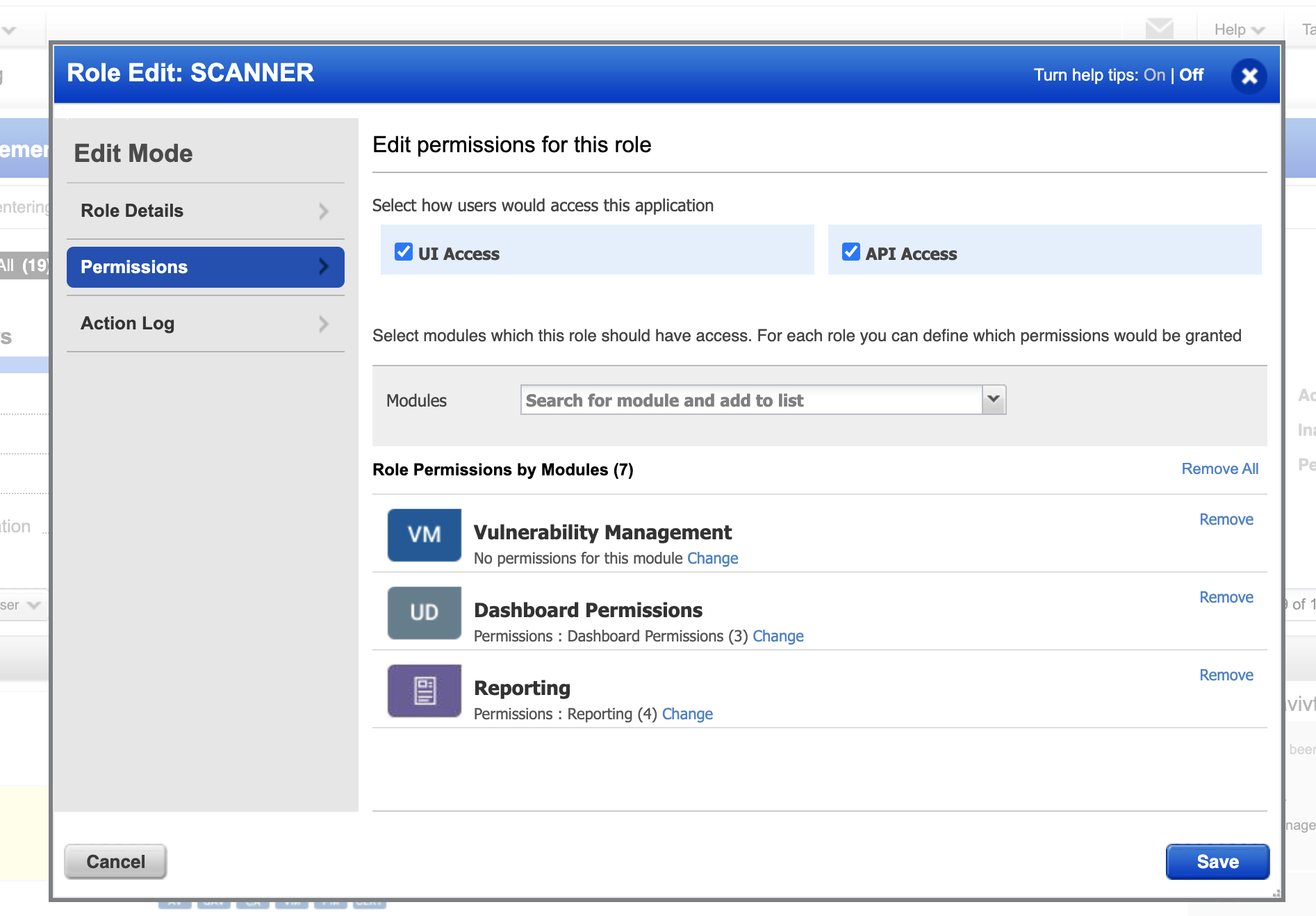
Once the user appears in the user list, click the user entry to open their details.
-
Under the Scanner role, ensure that both API access and GUI access permissions are selected.
-
In the Modules drop-down, select Manage PC Module and enable the following permissions:
-
Manage VM Module
-
Manage PC Module
-
-
Click Save to add the module to the user permissions.
-
Complete the user and copy the Username and Password to a safe location. You need them to configure the connector.
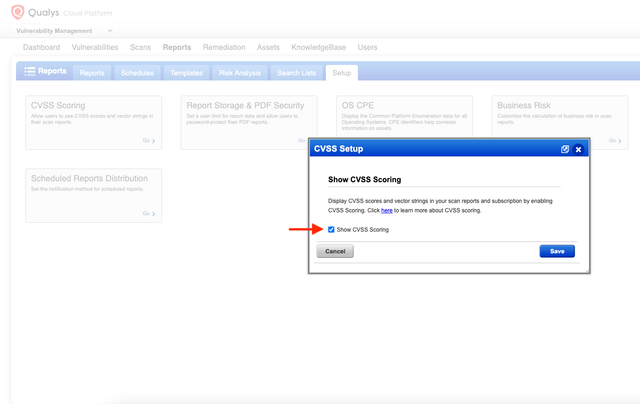
Enable CVSS Scoring in Your Qualys Account
CVSS scoring is not enabled by default in Qualys. To ensure vulnerability scores are available in Exposure Management, you must enable this feature in your Qualys environment.
-
Log in to the Qualys platform.
-
Navigate to the Reports tab.
-
Select the Setup tab.
-
Click CVSS Scoring.
-
Check the box labeled Show CVSS Scoring.
-
Click Save.
Add a Connector
To add a new connector:
-
In the left navigation menu, click Connectors.
The Connectors page appears.
-
In the upper-right corner, click
 Add new connector.
Add new connector.The Connector Library page appears.
-
In the search box, type the name of the connector.
-
On the tile for the connector, click Connect.
The connector configuration options appear.
Configure the Connector
To configure the connector:
-
(Optional) In the Connector's Name text box, type a descriptive name for the connector.
-
(Optional) To use a preconfigured on-prem connector to connect to this connector, from the Gateway drop-down, select the on-prem connector you want to use for the connector. Otherwise, select Don't use gateway.
Note: For information about configuring a gateway, see Tenable On-Prem Connector. -
In the API Server Url drop-down, select the appropriate server URL to use for API configuration.
-
In the Username and Password text boxes, paste your Qualys client credentials.
-
In the Data pulling configuration section, you can configure dynamic settings specific to the connector.
-
Use the ark_kernel_filter drop-down to filter vulnerabilities related to the system kernel. This filter helps exclude vulnerabilities that may have already been remediated but are still linked to outdated kernel versions that remain installed.
Note:Tenable Exposure Management disregards this filter when importing fixed vulnerabilities. This is intentional—Exposure Management continues tracking when a vulnerability was resolved, even if the vulnerable kernel is no longer active.
Select one of the following options:
-
Vulnerabilities related to the kernel are not filtered based on kernel activity. This matches the default configuration in Qualys, meaning vulnerabilities related to the kernel are not filtered based on kernel activity.
-
Exclude kernel-related vulnerabilities that are not exploitable (found on non-running kernels).
-
Include only kernel-related vulnerabilities that are not exploitable (found on non-running kernels).
-
Include only kernel-related vulnerabilities that are exploitable (found on running kernels).
-
-
From the Subscription type drop-down, select the subscription type of your Qualys account.
-
(Optional) Enable the Fetch Potential vulnerabilities option to ingest potential vulnerabilities identified by Qualys. Select this option if your organization wants broader visibility into possibly vulnerable systems, even if the vulnerability hasn't been confirmed through direct detection.
Note: Potential vulnerabilities are detections based on indirect evidence (e.g., version-based or inferred) rather than confirmed exploit presence. Enabling this setting increases visibility but may introduce additional noise in the findings.
-
(Optional) Enable the Fetch Superseded QIDS to ingest superseded QIDs (Qualys IDs). Enable if your organization wants to track historical detection coverage or if you're working with legacy remediation workflows where superseded QIDs are still relevant.
Note:Superseded QIDs are older detections that have been replaced by newer signatures in Qualys. Enabling this setting includes them in the findings ingested into Exposure Management.
-
(Optional) In the Tags text box, type a list of comma separated tags to apply to the ingested Qualys data.
-
In the Asset Retention text box, type the number of days after which you want assets to be removed from Tenable Exposure Management. If an asset has not been detected or updated within the specified number of days, it is automatically removed from the application, ensuring your asset inventory is current and relevant.
Tip: For more information, see Asset Retention. -
(Optional) From the drop-down menu, you can choose to automatically remove assets that reach a certain asset status, for example, TERMINATED.
-
-
In the Test connectivity section, click the Test Connectivity button to verify that Tenable Exposure Management can connect to your connector instance.
-
A successful connectivity test confirms that the platform can connect to the connector instance. It does not, however, guarantee that the synchronization process will succeed, as additional syncing or processing issues may arise.
-
If the connectivity test fails, an error message with details about the issue appears. Click Show tests for more information about the exact error.
-
-
In the Connector scheduling section, configure the time and day(s) on which you want connector syncs to occur.
Tip: For more information, see Connector Scheduling. -
Click Create. Tenable Exposure Management begins syncing the connector. The sync can take some time to complete.
-
To confirm the sync is complete, do the following:
-
Navigate to the Connectors page and monitor the connector's status. Sync is complete once the connector status is Connected.
-
View the sync logs for the connector to monitor the logs for a successful connection.
-
Qualys in Tenable Exposure Management
Locate Connector Assets in Tenable Exposure Management
As the connector discovers assets, Tenable Exposure Management ingests those devices for reporting.
To view assets by connector:
-
In Tenable Exposure Management, navigate to the Assets page.
-
In the Filters section, under 3rd Party Connectors, click the connector name for which you want to view assets.
The asset list updates to show only assets from the selected connector.
-
Click on any asset to view Asset Details.
Locate Connector Weaknesses in Tenable Exposure Management
As the connector discovers weaknesses, Tenable Exposure Management ingests those weaknesses for reporting.
To view weaknesses by connector:
-
In Tenable Exposure Management, navigate to the Weaknesses page.
-
In the Filters section, under 3rd Party Connectors, click the connector name for which you want to view weaknesses.
The weaknesses list updates to show only weaknesses from the selected connector.
-
Click on any weakness to view Weakness Details.
Locate Connector Findings in Tenable Exposure Management
As the connector discovers individual findings, Tenable Exposure Management ingests those findings for reporting.
To view findings by connector:
-
In Tenable Exposure Management, navigate to the Findings page.
-
In the Filters section, under 3rd Party Connectors, click the connector name for which you want to view findings
The findings list updates to show only assets from the selected connector.
-
Click on any asset to view Finding Details.
Device Mapping
| Tenable Exposure Management UI Field |
Qualys Field |
|---|---|
| Unique Identifier | id |
|
Asset - External Identifier or Asset - Provider Identifier |
CLOUD_RESOURCE_ID |
| Asset - Name | data.name or DNS or METADATA.VALUE or NAME for 'hostname'
|
| Asset - Operating Systems | OS or data.os |
|
Asset - IPv4 Adresses Asset - IPv6 Adresses |
IP |
| Asset - MAC Addresses | data.networkInterface.list.HostAssetInterface.[*].mac_address |
| Asset - First Observation Date | data.created or FIRST_FOUND_DATE |
| Asset - Last Observed At | LAST_VM_SCANNED_DATE or data.lastVulnScan |
|
Asset - External Tags |
TAGS METADATA CLOUD_PROVIDER_TAGS |
| Asset Custom Attributes |
Host ID Cloud Resource ID Hostname qualys_id Account ID Region Instance ID Image ID Instance State Tracking Method QG Host ID Last VM Scanned Date Last VM Auth Scanned Date |
Finding Mapping
| Tenable Exposure Management UI Field |
Qualys Field |
|---|---|
| Unique Identifier | Host ID + QID + UNIQUE_VULN_ID |
| Finding Name | data.TITLE |
| CVEs | data.CVE_LIST.CVE |
| Severity Driver | data.CVSS_V3.BASE |
| Description | data.DIAGNOSIS |
| Finding Custom Attributes |
RESULTS.Package.Installed Version data.openPort.list.HostAssetOpenPort |
| First Seen | FIRST_FOUND_DATETIME |
| Last seen (Observed) | LAST_FOUND_DATETIME |
Finding Status Mapping
|
Tenable Exposure Management Status |
Qualys Status |
|---|---|
|
Active |
All other statuses |
|
Fixed |
Fixed Ignored Disabled |
Note:For Qualys, Tenable Exposure Management uses the report_item_status field for.
Finding Severity Mapping
|
Tenable Exposure Management Severity |
Qualys Score |
|---|---|
|
Critical |
CVSS: 9.0 - 10.0 |
|
High |
CVSS: 7.0 - 8.9 |
|
Medium |
CVSS: 4.0 - 6.9 |
|
Low |
CVSS: 1-3.9 |
|
None |
CVSS:0 |
Note:For Qualys, Tenable uses the cvss3/cvss score field to determine severity.
Status Update Mechanisms
Every day, Tenable Exposure Management syncs with the vendor's platform to receive updates on existing findings and assets and to retrieve new ones (if any were added).
The table below describes how the status update mechanism works in the connector for findings and assets ingested into Tenable Exposure Management.
|
Update Type in Tenable Exposure Management |
Mechanism (When?) |
|---|---|
|
Archiving Assets |
|
|
Change a Finding status from "Active" to "Fixed" |
|
Uniqueness Criteria
Tenable Exposure Management uses defined uniqueness criteria to determine whether an ingested asset or finding should be recognized as a distinct record. These criteria help define how assets and findings are identified and counted from each connector.
Tip: Read all about Third-Party Data Deduplication in Tenable Exposure Management .
The uniqueness criteria for this connector are as follows:
|
Data |
Uniqueness Criteria |
|---|---|
|
Asset |
id |
|
Finding |
ID + QID + UNIQUE_VULN_ID |
API Endpoints in Use
List Hosts version: 4.0 List Agents version: 2.0 Asset Groups version: 3.0 Host List Detection version: 3.0
|
API |
Use in Tenable Exposure Management |
Requested Permissions |
|---|---|---|
|
qualysapi.{{ server_url_postfix }}/api/4.0/fo/asset/host |
Fetch Devices - Assets |
Managers view all scanned hosts within the subscription. Auditors view all scanned compliance hosts within the subscription. Unit Managers view scanned hosts assigned to the user’s business unit. Scanners and Readers view scanned hosts assigned to the user’s account.
Note: This API returns host information based on the user’s role and assigned asset groups in VM/VMDR and PC modules. Access is restricted according to role-based permissions. For Unit Managers, Scanners, and Readers to view compliance hosts, the Manage Compliance permission must be enabled in the user’s account settings.
|
|
qualysapi.{{ server_url_postfix }}/qps/rest/2.0/search/am/hostasset |
Devices enrichment |
Managers with full scope can access the API without additional permissions. All other users must have the following permissions assigned:
|
|
qualysapi.{{ server_url_postfix }}/api/3.0/fo/asset/group |
Devices enrichment |
Managers view all asset groups in the subscription. Unit Managers view asset groups assigned to their business unit, including groups owned by any user within that unit. Scanners and Readers view asset groups assigned to their account, including those they own. |
|
qualysapi.{{ server_url_postfix }}/api/3.0/fo/asset/host/vm/detection |
Fetch Detections - Findings |
Managers view all VM scanned hosts in the subscription. Auditors do not have permission to view VM scanned hosts. Unit Managers view VM scanned hosts assigned to their business unit. Scanners and Readers view VM scanned hosts assigned to their account.
Note: This API only returns information for hosts assigned to each user through asset groups in VM/VMDR. |
|
qualysapi.{{ server_url_postfix }}/api/3.0/fo/knowledge_base/vuln |
Fetch Solutions Detections enrichment |
Your subscription must include permission to run this API function. Auditors do not have permission to download vulnerability data from the Knowledge Base. |
Support Limitations and Expected Behavior
This section outlines any irregularities, expected behaviors, or limitations related to integration of the connector and Exposure Management. It also highlights details about ingested and non-ingested data to clarify data handling and functionality within this integration.
The selected Subscription Type in the connector configuration directly affects sync behavior and performance.
-
Lower-than-actual subscription tier: The sync may still succeed, but performance can degrade significantly. Extended sync times may lead to timeouts and eventual sync failure.
-
Higher-than-actual subscription tier: This can result in API permission errors and cause the sync to fail immediately.
To ensure optimal performance and a successful sync:
-
Confirm the correct subscription tier is selected in the connector configuration.
-
If multiple connectors share the same subscription, consider staggering their sync schedules to avoid API contention.
-
You may lower the configured subscription tier in Vulcan to throttle the sync rate in environments with shared API usage.
To use TruRisk (Qualys Detection Score - QDS) within the Exposure Management integration, you must have VMDR (Vulnerability Management, Detection, and Response) enabled on your Qualys subscription.
If the subscription includes only VM (Vulnerability Management) without VMDR, TruRisk scoring will not be available.
Data Validation
This section shows how to validate and compare data between Tenable Exposure Management and the Qualys platform.
Asset Data Validation
Objective: Ensure the number of endpoints (devices) in Qualys aligns with the number of devices displayed in Tenable Exposure Management.
In Qualys:
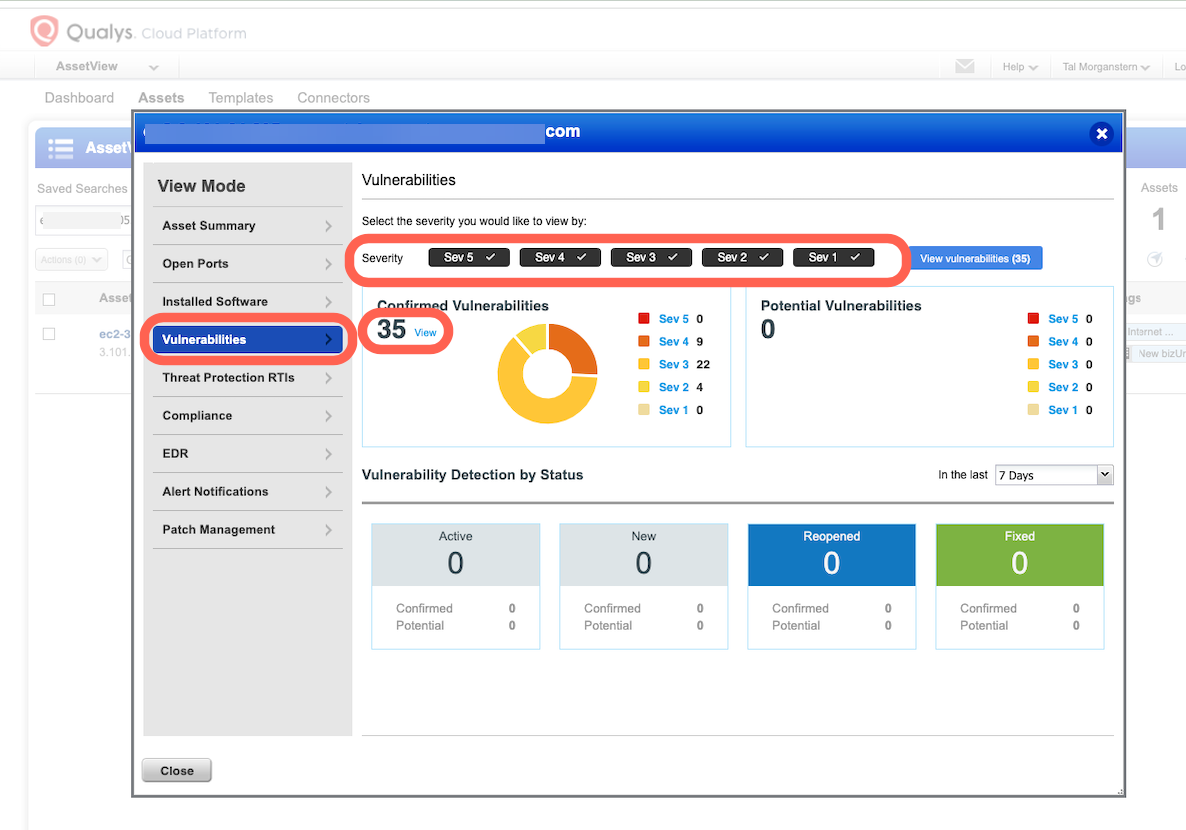
The Qualys UI does not provide a direct filter to view all assets returned by the hosts endpoint. However, you can validate a subset of these assets through the UI:
-
In the Asset View tab, navigate to Assets, then search using the filter activatedForModules:"VM".
-
In this example, the filtered view in Qualys shows 47 assets.
In Tenable Exposure Management:
-
Compare the total number of assets between Qualys and Tenable Exposure Management.
Expected outcome: The total numbers returned in Qualys and Tenable Exposure Management should match.
If an asset is not visible in Tenable Exposure Management, check the following conditions:
-
The asset was archived based on its last observed date (last_seen field).
-
Asset that returns from the Qualys connector with the state “TERMINATED" (This is the default, but configurable by the user) is archived.
-
The asset was archived because it did not return in the connector's last sync.
Tip: To learn more on how assets are archived and findings change status, see Status Update Mechanisms.
Findings Data Validation
Objective: Ensure the number of findings in Qualys aligns with the number of findings in Tenable Exposure Management.
In Qualys:
-
Navigate to the Assets view.
-
Click on the asset you want to validate.
-
Navigate to the Vulnerabilities tab.
-
Ensure all severities are selected in the filter options.
Tip: Only vulnerabilities that are active and not superseded are synced. Apply filters to exclude information, fixed, disabled, and ignored vulnerabilities (if applicable). For accurate comparison, make sure filters in both platforms align by severity, status, and time of sync.
In Tenable Exposure Management:
-
Compare the total number of findings in Tenable Exposure Management to the number from Crowdstrike.
Expected outcome: The total numbers returned in Qualys and Tenable Exposure Management should match.
If a finding is missing from Tenable Exposure Management or no longer active, check the following conditions:
-
The finding is marked as Fixed and appears under the Fixed state on the Findings screen.
-
The finding no longer appears because its related asset was archived.
Tip: To learn more on how assets are archived and findings change status, see Status Update Mechanisms.