CIS Control 5: Secure Configuration for Hardware and Software on Mobile Devices, Laptops, Workstations and Servers
The focus of this control is to maintain documented security configuration standards for all authorized operating systems and software. Organizations must establish a baseline security configuration, implement a configuration management and change control process, and actively be able to report on the security configuration of all endpoint devices such as:
- Mobile devices
- Laptops
- Servers
- Workstations
The CIS states this Control is critical:
“As delivered by manufacturers and resellers, the default configurations for operating systems and applications are normally geared towards ease-of-deployment and ease-of-use – not security. Basic controls, open services and ports, default accounts or passwords, older (vulnerable) protocols, and pre-installation of unneeded software can be exploitable in their default state.
Developing configuration settings with good security properties is a complex task beyond the ability of individual users, requiring analysis of potentially hundreds or thousands of options in order to make good choices (the Procedures and Tools section below provides resources for secure configurations). Even if a strong initial configuration is developed and installed, it must be continually managed to avoid security “decay” as software is updated or patched, new security vulnerabilities are reported, and configurations are “tweaked” to allow the installation of new software or support new operational requirements. If not, attackers will find opportunities to exploit both network accessible services and client software.”
The journey of implementing the CIS Controls continues with the Secure Configuration for Hardware and Software on Mobile Devices, Laptops, Workstations, and Servers. Organizations are directed to develop strong, secure baseline configurations for each deployed software system. Organizations are also directed to maintain documented security configuration standards for all authorized operating systems and software. The specific sub-controls that are part of Implementation Group 1 (IG1) are:
Oftentimes organizations struggle to get started. Small organizations purchase devices that arrive pre-configured or pre-loaded with an operating system and applications. Large organizations typically struggle with large numbers of devices which become harder to manage over time. Creating a secure baseline is challenging at best, and involves a great deal of resources and expertise. Why recreate the wheel developing a secure baseline? CIS and NIST have developed publicly available security benchmarks, security guides, and checklists that have been thoroughly vetted. Excellent resources include:
Organizations can save a great deal of time and effort by starting with these publicly available resources, then augmenting or adjusting these baselines to satisfy local policies and requirements. Because these resources are trusted industry standards, any deviations should be documented to facilitate later reviews or audits. For example, complex enterprises may find that a single security baseline configuration is impractical. Many organizations may find they need to support different configurations, such as those for web servers, database servers, etc,. If this is the case, the number of baseline variations should be kept to a minimum and should be well documented.
For CIS Control 5, Tenable products allow security operations teams to use Tenable Security Center Continuous View to analyze endpoint operating systems and software configurations. Using the CIS Benchmarks and Tenable Security Center, the organization can verify that established configuration policies are followed.
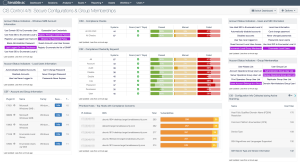
A vital step in vulnerability management is assessing the configuration of systems within the network. The CIS Control 4/5 Secure Configurations and Group Memberships Dashboard provides useful information to assist organizations with this control.
For more information about the CIS Control 4/5 dashboard, see CIS Control 4/5: Secure Configurations & Group Memberships.