Log Collection and Management
Questions that this section may help solve:
-
How do I ensure Logs are capturing when confidential information is being read/updated (ex. Passwords)?
-
Do my logs show who or what performed the action on my system?
-
The changing of access rights (revocation/Grants/modifying) should be logged. Which audits will help me identify this compliance?
-
Apps startup/shutdown/restart/abort/failure/or abnormal end should also be logged. How can this be verified with compliance scanning?
-
Logs should be sent via syslog, syslog-ng, or syslog-reliable network protocols to a centralized log management system. Which audits will verify the presence of these protocols?
Ensuring logging is appropriately set up and operating correctly is important when securing enterprise assets, as this helps identify potential attacks. In some instances, analyzing the logs may be the only way to prove an attack was carried out successfully. In many cases an attacker is aware that most enterprises may be logging activities, though most do not analyze the logs in a regular enough frequency. This irregular log analysis can allow an attacker to be exploiting the system for weeks, months, or more without detection.
There are two common types of logs; Audit Logs and system logs. Audit logs usually include user-level events, while system logs have system-level events. System logs are usually easier to enable as they may require less configuration, while audit logs take more configuration, as they involve collecting information on when users access certain files, logged in, etc.
Search Examples
When attempting to focus on Audit log compliance results one thing that can be helpful is to have specific controls or audit checks in mind to query within Tenable Vulnerability Management or Tenable Security Center. Refer to the Search Overview Section for a refresher on audit file format and structure. Focusing on Audit Log management and confirming the enterprise’s compliance can be done more efficiently if common keywords for audit checks are used to query through the compliance scan results. In the Keyword table are some common keywords that can be found as audit checks related to audit log management.
| Keyword | Common Windows Audit Name | Common Unix Audit Name |
|---|---|---|
| Audit Log | "17.5.3 Ensure 'Audit Logoff' is set to include 'Success'" | "4.1.1.1 Ensure audit log storage size is configured" |
| System Logs |
N/A |
"4.1 (L1) Host must configure a persistent log location for all locally stored system logs" |
| Logging |
"Turn on PowerShell Script Block Logging - EnableScriptBlockInvocationLogging" |
"5.3 Ensure that logging captures as much information as possible" |
| Logs |
"Windows Defender Firewall: Allow logging - LogSuccessfulConnections" |
"3.1.7 Secure permissions for all diagnostic logs" |
Note: When searching a keyword in Tenable Security Center (Plugin Name filter), the plugin type compliance filter should be used along with a cross reference filter to eliminate any false positives in the query.
Related Controls: 800-53r5 AU-9*, 800-171 3.3.*, CIS CSC v7 6.4, 6.5/ CIS CSC v8 8.3, 8.9, CSF PR.DS-4, PR.PT-1, ISO-27001 A.6.1.2,A.9.4.1,A.9.4.5
Tenable Vulnerability Management
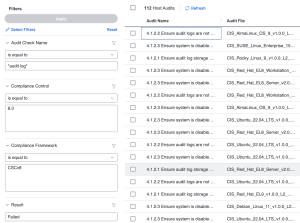
In Tenable Vulnerability Management the user can navigate to the Findings page and Host Audits section to query results from the Policy Compliance scan that was run. Once there, the filters that are most useful to use are the Compliance Framework, Compliance Control, and Audit Check Name filters. An additional filter that can be useful in conjunction with the others is the Results filter, as the filter allows the user to focus on different states of compliance for the assets.
For example, the focus may be tracking the state of compliance and more specifically grabbing a list of failed checks involving audit logs in Windows and Unix assets. For this scenario the user will want to focus on Failed Result types using the Result Filter. In Tenable Vulnerability Management the user could use the Compliance Control filter equal to 8.3, Compliance Framework filter equal to “CSCv8”, Result set to Failed, and Audit Check Name filter equal to *audit log*. One important note is that the asterisks need to be in the Audit Check Name filter value so the filter acts as a contains rather than a straight match.
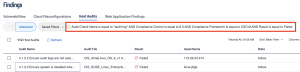
This query can be replicated by selecting the “Advanced” button within the Host Audits section of the findings page and inputting the following queries:
-
Audit Check Name is equal to *audit log* AND Compliance Control is equal to 8.3 AND Compliance Framework is equal to CSCv8 AND Result is equal to Failed
-
Audit Check Name is equal to *System Logs* AND Compliance Control is equal to 8 AND Compliance Framework is equal to CSCv8 AND Result is equal to Failed
-
Audit Check Name is equal to *Logging* AND Compliance Control is equal to 8 AND Compliance Framework is equal to CSCv8 AND Result is equal to Failed
Tenable Security Center
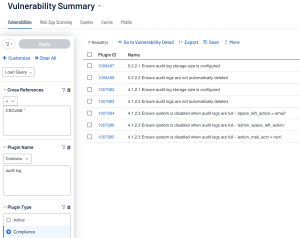
In Tenable Security Center the user needs to navigate to the Analysis page and use the Plugin Type filter, Plugin Name Filter, and Cross Reference Filter. The Plugin Type filter needs to be set to ‘Compliance’ to focus only on compliance plugins and results. The Plugin Name filter can be set to contains and whatever keyword the user may need; like in the previous example the keywords can be “Audit log” so the query looks at audit checks that have “audit log” in the name. Lastly, the Cross Reference filter allows the user to further filter the results by Compliance Framework and Compliance Control.
Following the previous scenario covered in the Tenable Vulnerability Management section, the user will want to focus on Failed Result types which can be achieved by using the Severity filter set to High. The next filters the user will use are Plugin type set to compliance, cross reference equal to “CSCv8|8.*”, and Plugin Name contains “audit log”. Be aware that the asterisk in the Cross Reference filter is used to cover any check that is related to control 8.