Developing and Maintaining a Software Inventory
Developing and maintaining a software inventory is a proactive investment in time and resources to gather and analyze information about software assets before a security incident occurs. This process identifies installed software, determines software authorization, groups assets, verifies patches and detects running services. Tenable solutions simplify the task of gathering and analyzing systems to develop and maintain a software inventory.
Identifying Installed Software
Identifying the authorized software assets is an important step to ensure critical assets are protected. The larger the organization, the more difficult the inventory process becomes. Tenable Vulnerability Management and Tenable Security Center help organizations build a software inventory. There are several software discovery plugins that run by default in the following scan templates:
- Basic and Advanced Agent Scans
- Basic and Advanced [Network] Scans
- Credentialed Patch Audit
- Internal PCI Network Scan
- Collect Inventory Agent Scan (see below)
Inventory Agent Scanning in Tenable Vulnerability Management is part of the Frictionless Agent. This new scanning capability leverages Tenable’s frictionless assessment capabilities to provide more efficient vulnerability detection, minimizing the Nessus Agent load and installed footprint on the endpoint. Leveraging this new scan policy ensures the agent only runs an inventory collection plugin locally and sends results to Tenable Vulnerability Management for processing in the Frictionless Assessment pipeline. Scan results are presented in the same format as traditional scans. While there is a coverage differential compared to using a traditional agent, the Inventory Agent provides a great option for host-based scanning on hosts with limited resources.
Inventory Agent Scanning is supported on the following platforms:
- Tenable Vulnerability Management Agent scans
- Tenable Security Center imports of Tenable Vulnerability Management cloud agent scans
Performing Authenticated Scans
Authenticated scans are required to enumerate software since software enumerations are considered “Local Checks.” More than 120,000 Tenable plugins require successful authentication to occur via a Nessus Agent or a Nessus Scanner before these plugins can run on an asset. These plugins are of the plugin type “Local” rather than “Remote.” The Tenable Plugins page allows you to search for Local Plugins and Remote Plugins to determine which plugins require successful authentication.
Nessus scanners used with Tenable Vulnerability Management and Tenable Security Center support the use of credentials to log in to a system to provide information about configuration settings that would not be visible from the network. For example, a credentialed scan can get information about the type of hardware that is running. Hardware drivers have life cycles just like any other type of software, and are subject to the same security issues. The Center for Internet Security (CIS) provides consensus benchmarks that set security hardening standards. A credentialed scan can verify that systems are configured in accordance with a known “gold standard.”
The most common software enumeration plugins are OS Identification (11936), Microsoft Windows Installed Software Enumeration (credentialed check) (20811), Software Enumeration (SSH) (22869), and List Installed Mac OS X Software (83991). There are several other software enumeration plugins that provide information that can help build a software inventory:
- OS Fingerprinting via DHCP (7120)
- Oracle Installed Software Enumeration (Linux / Unix) (71642)
- Oracle Installed Software Enumeration (Windows) (71643)
- OS Identification and Installed Software Enumeration over SSH v2 (Using New SSH Library) (97993)
- Unix Software Discovery Command Checks (152741)
- Unix Software Discovery Commands Available (152742)
- Unix Software Discovery Commands Not Available (152743)
The package installation date may not be displayed in the scan results for some systems, such as Debian.
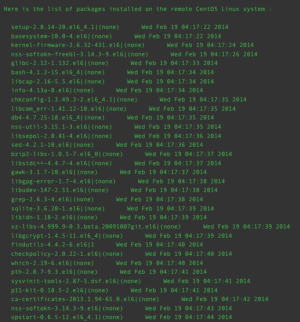
Tenable products will attempt to store a version of the package list that includes dates separately for all Tenable-supported Linux operating systems running RPM-based packaging. If available, the package installation date will be displayed in the "Software Enumeration (SSH)" plugin, 22869.
The following is a sample of the Plugin Output for Plugin 22869:
Common searches for Tenable software enumeration plugins and plugin results include:
- Plugin Name contains enumeration
- Plugin Name contains discovery
- Plugin Name contains list installed
- Plugin Name contains installed software
- Plugin ID equals 11936, 20811, 22869, 83991, 97993, 152741, 71642, 71643, 152742, 152743, 7120
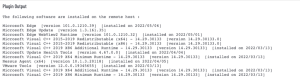
The following is a sample of the Plugin Output from Plugin 20811:
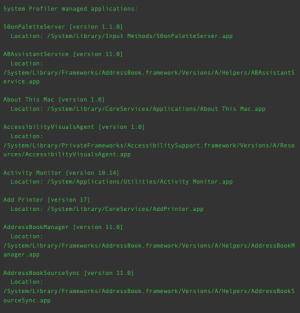
The following image displays the results of the software enumeration plugin for macOS, Plugin ID 83991: