Tenable Vulnerability Management 2024 Release Notes
Tip: You can subscribe to receive alerts for Tenable documentation updates.
These release notes are listed in reverse chronological order.
December 2, 2024
Tenable is pleased to announce a new Account Details tab in  Settings > License, which presents information about your relationship with Tenable and your licensed products. This admin-only tab is the same in all your Tenable containers and holds the following details:
Settings > License, which presents information about your relationship with Tenable and your licensed products. This admin-only tab is the same in all your Tenable containers and holds the following details:
-
Account Information — Your account name, Customer ID, and Tenable contact.
-
Tenable One Licenses — Any Tenable One license, including its version, allocated assets, and the license start and end dates.
-
Standalone Product Licenses — Standalone product license details including the license key, assets used, and assets purchased.
To learn more, see License Information in the Tenable Vulnerability Management User Guide.
November 19, 2024
Tenable is pleased to announce new fields and columns on the Findings and Assets workbenches and details pages. These new attributes surface information including when vulnerabilities and assets were last scanned, when Tenable Nessus last authenticated or signed in, and if workarounds exist for vulnerabilities.
The following table lists the new attributes and indicates where they appear in the user interface.
| Attribute | Description | Appear On... |
|---|---|---|
| Remediation Type |
The type of fix recommended, such as Patch or Workaround. |
Findings Details page |
| Workaround Type | If the Remediation Type is Workaround, the type. Possible values are Configuration Change or Disable Service. | Findings Details page |
| Workaround Published | The date a workaround for a vulnerability was published. | Findings Details page |
| Last Scan Target | The IP address or fully qualified domain name (FQDN) of the asset targeted in the last scan. | Findings Details page, Asset Details page, Findings workbench, Assets workbench |
| Last Authentication Attempt | The last time that Tenable Nessus attempted to sign in, either with SSH on Unix-based systems or SMB on Windows. | Asset Details page |
| Last Successful Authentication | The last time that Tenable Nessus authenticated successfully. | Asset Details page |
| Last Authentication Status | If the last authentication attempt by Tenable Nessus was successful. | Asset Details page |
| Network Device Serial ID | The unique identifier of the asset as assigned by the manufacturer. This property is only available for network devices. | Findings Details page, Asset Details page |
To learn more, see Host Asset Details and Vulnerability Details in the Tenable Vulnerability Management User Guide.
November 12, 2024
Agents that are installed on Linux hosts and linked to Tenable Vulnerability Management now support the continuous assessment scanning feature. Continuous assessment scanning enables continuous software inventory monitoring on the host.
You can configure continuous assessment scanning at the agent profile level. To enable continuous assessment scanning, select the Enable Continuous Assessment module option in the Agent Profile menu and configure the profile's Baseline scan frequency. Once you enable the setting, configure the baseline scan frequency, and save the agent profile changes, the agents assigned to that profile begin to perform continuous assessment scanning.
For more information, see Continuous Assessment Scanning and Agent Profiles in the Tenable Vulnerability Management User Guide.
November 7, 2024
You can now track and filter for zero day CVEs in Vulnerability Intelligence. This release contains the following updates:
-
Filter and Column — On the Vulnerability Intelligence Overview page, use a new Zero Day filter to view zero day vulnerabilities. In addition, view that information in a table column.
-
Vulnerability Profile field — On the Vulnerability Profile page, in the Risk Profile section, a new field indicates if a vulnerability is a zero day vulnerability.
To learn more, see Identify Your Exposure and View Vulnerability Profiles in the Tenable Vulnerability Management User Guide.
October 21, 2024
Tenable is pleased to announce new fields and filters that you can use to better understand the history of a finding.
-
Resurfaced Date — On the Findings workbench, in a new filter and column, track the most recent date that a scan detected a Resurfaced vulnerability. This information also appears on the Findings Details page.
-
Vulnerability Age — On the Findings Details page, under Discovery, view the age of a vulnerability based on its State.
To learn more, see Findings Filters and Vulnerability Details in the Tenable Vulnerability Management User Guide.
October 16, 2024
Tenable is pleased to announce enhancements to the Vulnerability Intelligence section as follows:
-
View only relevant CVEs — On the CVEs tab, with a new checkbox, filter for only the vulnerabilities present on your assets.
-
View CVEs by asset — On the CVEs tab in any row, click the dropdown > to view assets containing that vulnerability.
To learn more, see CVEs in the Tenable Vulnerability Management User Guide.
Note: This feature is available to a limited pilot group and will be rolled out to a wider audience in the future.
Agents that are installed on Linux hosts and linked to Tenable Vulnerability Management now support the continuous assessment scanning feature. Continuous assessment scanning enables continuous software inventory monitoring on the host.
You can configure continuous assessment scanning at the agent profile level. To enable continuous assessment scanning, select the Enable Continuous Assessment module option in the Agent Profile menu and configure the profile's Baseline scan frequency. Once you enable the setting, configure the baseline scan frequency, and save the agent profile changes, the agents assigned to that profile begin to perform continuous assessment scanning.
For more information, see Continuous Assessment Scanning and Agent Profiles in the Tenable Vulnerability Management Early Access User Guide.
October 8, 2024
Tenable is pleased to announce a redesigned License Information page which presents a complete breakdown of your products and their license usage, including any ratios.
On the enhanced License Information page, you can:
-
View information about your Tenable products, including the licenses they are using, the number of licenses assigned, and more.
-
View your license usage over time to spot trends such as product misconfigurations or temporary usage spikes.
-
(Tenable One-only) Get a snapshot of license usage by component.
To learn more, see License Information in the Tenable Vulnerability Management User Guide.
October 3, 2024
Tenable MSSP Portal now includes an Exposure Response Summary page to view high-level vulnerability information about all your Tenable Vulnerability Management child containers. For more information, see Exposure Response in the Tenable MSSP Portal User Guide.
October 2, 2024
Tenable Vulnerability Management's left navigation bar has a new look and feel. It also holds shortcuts to frequently used items and menus to open specific pages with one click.
For example, to open the Host Audits tab on the Assets workbench, in the left navigation, hover on Assets and then click Host Audits in the menu that appears.
The new navigation bar contains the following items.
| Sidebar Item | Description |
|---|---|
 Dashboards Dashboards
|
View information about your environment with configurable indicators and widgets. Renamed from My Dashboards. |
 Vulnerability Intelligence Vulnerability Intelligence
|
Review vulnerabilities from Tenable's database and compare them to findings in your environment. |
 Exposure Response Exposure Response
|
Create and manage projects to address vulnerabilities in your environment. |
 Assets Assets
|
View all your assets in Tenable Vulnerability Management, broken down by type. Before this release, this item was under Explore. |
 Findings Findings
|
View all your findings in Tenable Vulnerability Management, broken down by type. Before this release, this item was under Explore. |
 Solutions Solutions
|
Review Tenable-recommended solutions for vulnerabilities in your environment. Before this release, this item was under Act. |
 Scans Scans
|
Create, configure, and manage scans. |
 Sensors Sensors
|
Manage sensors, such as cloud sensors or linked sensors from Tenable Nessus. Shortcut to  Settings > Settings >  Sensors. Sensors. |
 Reports Reports
|
Create, manage, and run reports. Before this release, this item was under Act. |
 Exports Exports
|
Manage scheduled exports and download files from past exports. Shortcut to  Settings > Settings >  Exports. Exports. |
 Remediation Remediation
|
Track and manage remediation projects. Before this release, this item was under Act. |
 Container Security Legacy Container Security Legacy
|
Manage containers, images and image repositories. End of Life on September 30, 2024. |
 Settings Settings
|
Manage Tenable Vulnerability Management's settings. |
October 1, 2024
Tenable has standardized operating system (OS) name values for macOS and some Linux and Unix distributions that appear in the Tenable Vulnerability Management asset attribute list. OS values now show the distribution and its version consistently.
Before this update, OS name values have appeared with variations based on whether Tenable Nessus scanners or Tenable Agents generated the data.
If you have built filters, saved searches, and tags that are filtered on expected variations of specific OS values (for example, Linux Kernel 4.4 on Ubuntu 16.04 (xenial)), Tenable recommends updating these saved filters.
Note: This update only applies to Linux, Unix, and macOS data in the English user interface.
For more information, see the Tenable Linux/UNIX/macOS Host Data Normalization FAQ.
Note: This feature is available to a limited pilot group and will be rolled out to a wider audience in the future.
Tenable is pleased to announce the early access release of Tenable Data Stream, with which you can stream Tenable Vulnerability Management to your own AWS S3 bucket. This feature is an alternative to exporting your data with the Tenable APIs.
Once configured in the user interface, Tenable Data Stream continuously sends the following files types to your AWS bucket:
| File Type | Description |
|---|---|
| Assets payload |
New, updated, or deleted assets. |
| Findings payload |
New or updated findings. |
| Tags payload | New, updated, or deleted asset tags. |
| Manifest | Event logs for the payload files sent to your AWS S3 bucket. |
To learn more, see Tenable Data Stream in the Early Access version of the Tenable Vulnerability Management User Guide.
September 10, 2024
Tenable has added features to help you monitor your artificial intelligence applications and services. Data is drawn from your scans and installed agents and then shown on the Findings workbench, in reports, and on a custom dashboard.
This release contains:
-
AI Inventory — On the Findings workbench, in the Vulnerabilities and Web Application Scanning tabs, use the new AI Inventory button to filter for AI-related findings. These informational findings are not vulnerabilities.
-
AI findings details — On Findings Details pages for AI-related findings, a new AI Inventory section appears.
-
AI/LLM dashboard — On a new custom dashboard, view your environment's top AI-related browser extensions or plugins, the most used AI applications in your environment, and more.
Tip: To use the new dashboard, in the left-hand navigation, click My Dashboard. Then, on the right side, click Dashboards. On the Dashboards page that appears, click New Dashboard > Template Library and in the search box, search for AI/LLM Dashboard.
Dashboards. On the Dashboards page that appears, click New Dashboard > Template Library and in the search box, search for AI/LLM Dashboard. -
AI/LLM reports — In Tenable Vulnerability Management's Reports section, run three new reports about AI/LLM-related findings.
To learn more, see Use the Findings Workbench in the Tenable Vulnerability Management User Guide. Also, on the Tenable blog, see AI/LLM Findings Report Templates and AI/LLM Dashboard.
September 3, 2024
Tenable is pleased to announce new recast rule types with which you can modify the results of host audit findings or hide them from the Findings workbench.
You can manage the new rules in  Settings >
Settings >  Recast or directly from the
Recast or directly from the  Findings workbench. The following table lists all rule types now supported in Tenable Vulnerability Management.
Findings workbench. The following table lists all rule types now supported in Tenable Vulnerability Management.
| Rule | New? | Description |
|---|---|---|
| Recast | No | Change the severity of vulnerability findings based on their Plugin ID. |
| Accept (for host vulnerabilities) | No | Accept the risk of vulnerability findings without modifying severity and hide them from the Findings workbench. |
| Change Result | Yes | Modify the Result of host audit findings, for example by changing Failed results to Passed. |
| Accept (for host audits) | Yes | Accept the Result of host audit findings and hide them from the the Findings workbench. |
To learn more, see Recast Rules in the Tenable Vulnerability Management User Guide.
August 21, 2024
Tenable is pleased to announce that you can now define the email domains to send export results to (for example, mycompany.com). Once you add domains, users can only send exports to to those domains. Set this option in Settings > General.
To learn more, see General Settings.
August 14, 2024
Tenable has added a new Agent Health Events tab to the agent details page. This tab provides a health status and a record of health events that have occurred on a linked agent.
The health events tab records the following events:
-
Available disk space on the asset the agent is installed on
-
Agent disk space used by plugins
-
Plugin update failures
-
Plugin integrity check failures
-
Plugin compilation failures
Also, the Linked Agents page has been updated with a new Health column. This column allows you to quickly identify agents that have recently experienced negative health events.
You can use the agent health information to troubleshoot agent issues, or you can forward agent health information to Tenable support for further investigation.
For more information, see View Linked Agent Health Events.
August 13, 2024
Tenable is pleased to announce the availability of Tenable Web App Scanning Scan Management support within Tenable Vulnerability Management Custom Roles. This capability enables more granular controls for customer role users to access, modify, and execute Tenable Web App Scanning scans, closing a significant gap in our custom role capabilities for our Tenable Vulnerability Management customers.
August 8, 2024
Tenable is pleased to announce updates to the Plugin Output filter on the Findings workbench. The updates make this resource-intensive filter easier to use by prompting you to refine the search results with other filters:
-
Top plugins — When you search for plugin output, the system now lists the top ten Plugin IDs from the results.
-
Search prompt — When you search for plugin output, the system suggests adding the Plugin ID and Last Seen filters.
August 6, 2024
Tenable is pleased to announce the availability of the following Cloud Sensor IP ranges for Tenable FedRAMP Moderate Cloud Based Network Scans:
-
2600:1f12:98d:c900::/56
Additionally, beginning on September 3, 2024, the following IP ranges will be available for Internal Scanner or Agent Communications:
-
172.65.64.208
-
172.65.64.209
-
172.65.64.210
-
172.65.64.211
-
2606:4700:78::120:0:1200
-
2606:4700:78::120:0:1201
-
2606:4700:78::120:0:1202
-
2606:4700:78::120:0:1203
For more information, see Cloud Sensors in the Tenable Vulnerability Management User Guide.
August 1, 2024
Tenable is pleased to announce Exposure Response, a new main section in Tenable Vulnerability Management. Use this section to create initiatives, which track which track the identification of critical exposures and your response to them.
As an administrator, you’ll use these new tools to create, assign, and report on initiatives. As a initiative owner, you’ll only work with your initiatives.
In the Exposure Response section, you can:
- Create initiatives — Add and assign initiatives; apply SLAs, target specific vulnerabilities.
- Manage initiatives — Review initiatives on customizable dashboards.
- Custom query builder — Drill down to specific findings or assets.
- Export initiative data —Export and share lists of findings or assets.
- Use report cards — View and export visual reports of your remediation progress.
To learn more, see Exposure Response in the Tenable Vulnerability Management User Guide.
July 24, 2024
Tenable is pleased to announce Exposure Response, a new main section in Tenable Vulnerability Management. Use this section to create initiatives, which track your remediation projects.
As an administrator, you’ll use these new tools to create, assign, and report on initiatives. As a initiative owner, you’ll only work with your initiatives.
In the Exposure Response section, you can:
- Create initiatives — Add and assign initiatives, apply SLAs, and target specific vulnerabilities using combinations of queries.
- Manage initiatives — Review your initiatives on customizable dashboards.
- Custom query builder — Drill down to specific resources and save your searches.
- Export initiative data — Export and share lists of findings or affected assets.
- Use report cards — View and export visual reports about remediation progress.
To learn more, see Exposure Response in the Tenable Vulnerability Management User Guide or contact your Tenable representative.
July 22, 2024
Tenable is pleased to announce new plugin update options for Tenable Agent in Tenable Vulnerability Management. You can set these options before deploying Agents to your environment.
This release contains the following:
-
New plugin update options — Delay Agent plugin updates by a certain number of days or substitute a plugin set from the past 30 days.
-
New options when editing Agents — Change the profile description, the agent version, the Open Agent Port, or the setting for Configure Plugin Update Plan.
To learn more, see Agent Profiles in the Tenable Vulnerability Management User Guide.
July 10, 2024
Tenable is pleased to announce key features and content that enhance how you work with compliance findings in Tenable FedRAMP Moderate. This release includes hundreds of new compliance-focused report templates, dashboards, and widgets as well as new findings filters.
-
Report template categories — In a previous release, Tenable introduced report template categories. On the Reports page, new categories now contain new templates. Review the categories in Create a Report.
-
Dashboard templates — On the Dashboards page, click New Dashboard > Template Library to choose from new dashboards in categories under Host Audits. Review the categories in Create a Dashboard.
-
Dashboard widgets — On the Dashboards page, click Widget Library to add new widgets from categories under Host Audits.
-
Findings filters — On the Findings workbench in the Host Audits tab, new benchmarking and compliance filters now appear, as described in Findings Filters.
July 9, 2024
You can now edit scheduled exports from the Tenable Vulnerability Management settings and assign them to different users.
This release includes the following:
-
Edit scheduled exports — In Settings > Exports, click
 and then click Edit to open a pane of export options.
and then click Edit to open a pane of export options. -
Reassign scheduled exports — When deleting a user, the system assigns their scheduled exports to the new object owner.
To learn more, see Edit a Scheduled Export and Delete a User Account.
July 1, 2024
Note: This feature is available to a limited pilot group and will be rolled out to a wider audience in the future.
Tenable has added the Configure Plugin Update Plan setting to the Agent Profiles menu. The setting allows you to determine what plugins Tenable Vulnerability Management installs on the selected profile's agents during the daily plugin update and has three possible configurations:
-
Auto update to latest — Update agents with the latest plugin set. This is the default selection.
-
Delay plugin updates by days — Update agents with a delayed plugin set. The plugin set can be delayed by a minimum of one day and a maximum of 30 days. If multiple plugin sets were published on the configured day, Tenable Vulnerability Management installs the latest set of that day.
-
Select plugin set from the last 30 days — Update agents with a specific plugin set from the last 30 days. Tenable Vulnerability Management uses this plugin set until you choose another plugin set or update plan setting.
You can now designate different plugin sets to different agent profiles according to your business needs. For example, you could keep one profile on the latest plugin set for testing and a second profile on a delayed update plan of fourteen days.
For more information, see Agent Profiles in the Tenable Vulnerability Management Early Access User Guide.
June 5, 2024
Tenable now supports API access security where users can define the IPv4 and IPv6 addresses from which Tenable Vulnerability Management public APIs can be accessed. Users can add discrete, range, or CIDR IPv4 or IPv6 addresses to add an extra layer of security to their container. Administrators can manage this setting in the Access Control section of the user interface.
June 4, 2024
Tenable is pleased to announce Vulnerability Intelligence, a new main section in Tenable Vulnerability Management. Use this section to compare vulnerabilities known by Tenable to your own exposure. Review vulnerabilities across Tenable's entire database, a subset of that data, or in curated categories that surface crucial vulnerability types.
Where the Findings and Assets workbenches simply show scan results, Vulnerability Intelligence provides context. For example, you can view vulnerabilities being leveraged by threat actors in ransomware—and then check which of your own assets are affected.
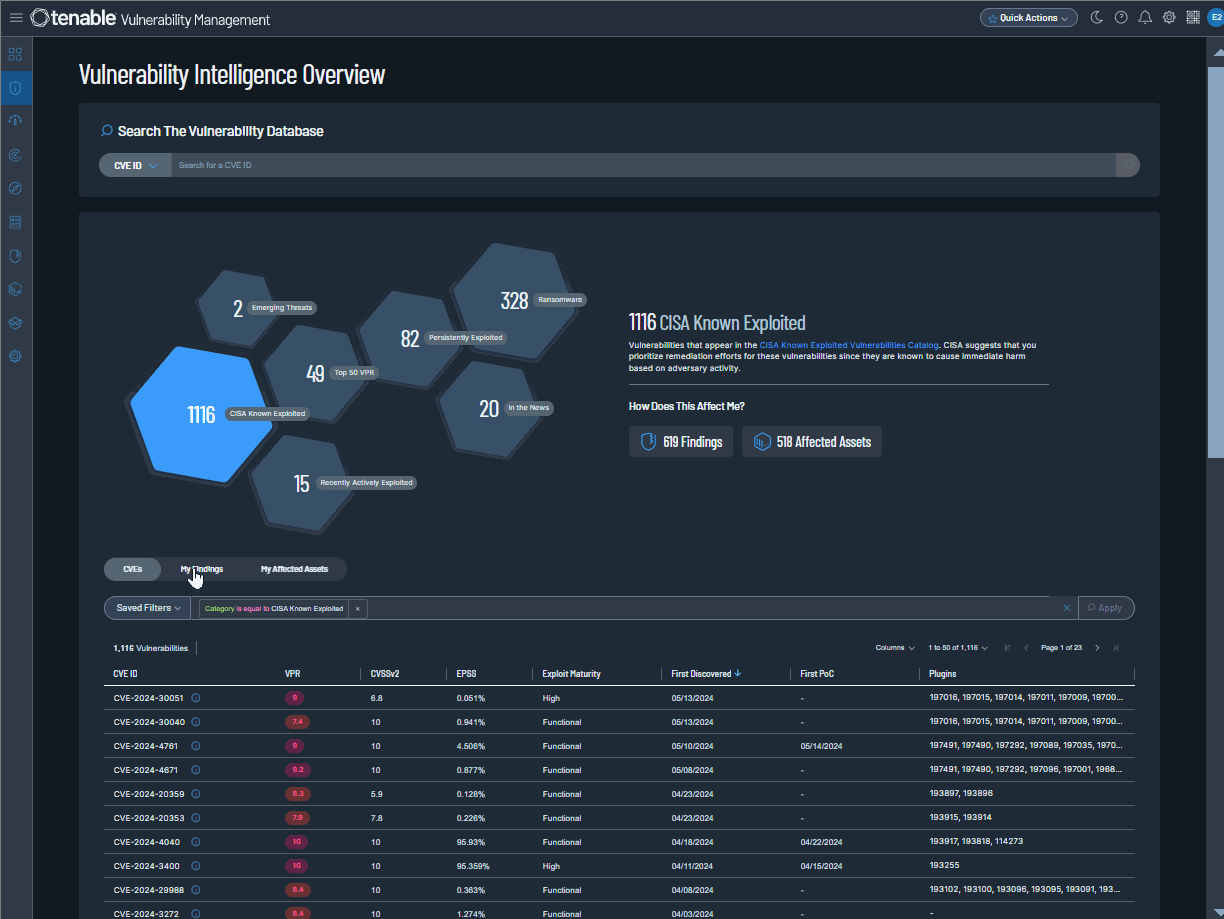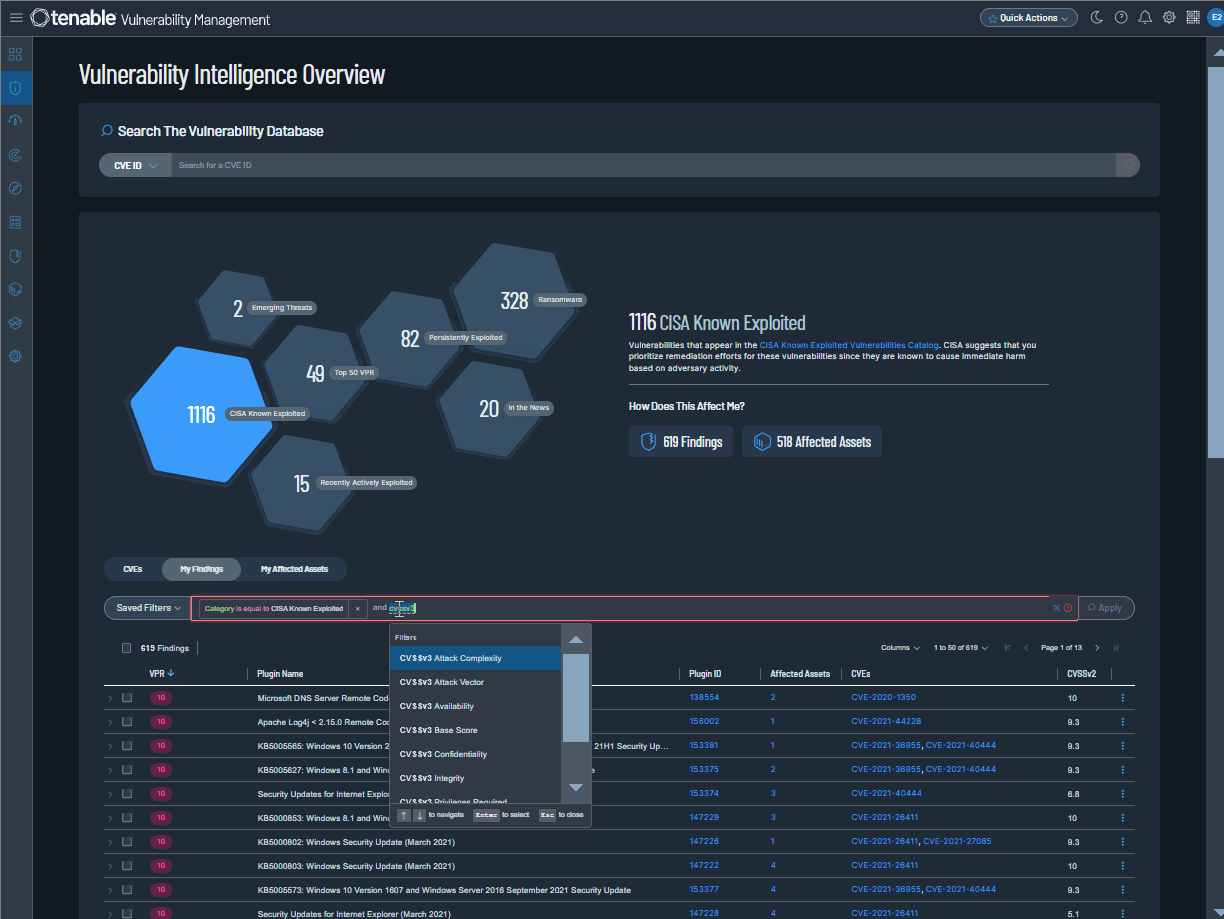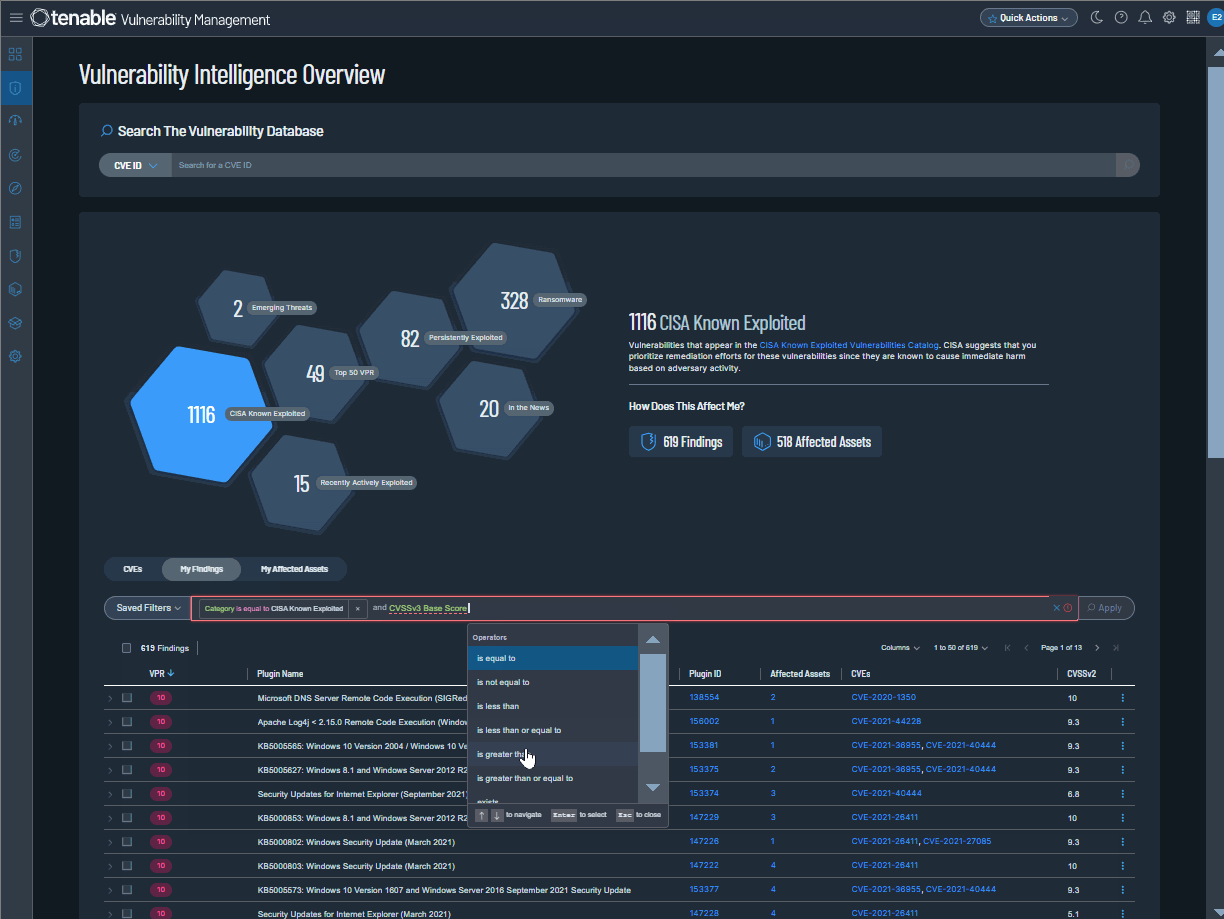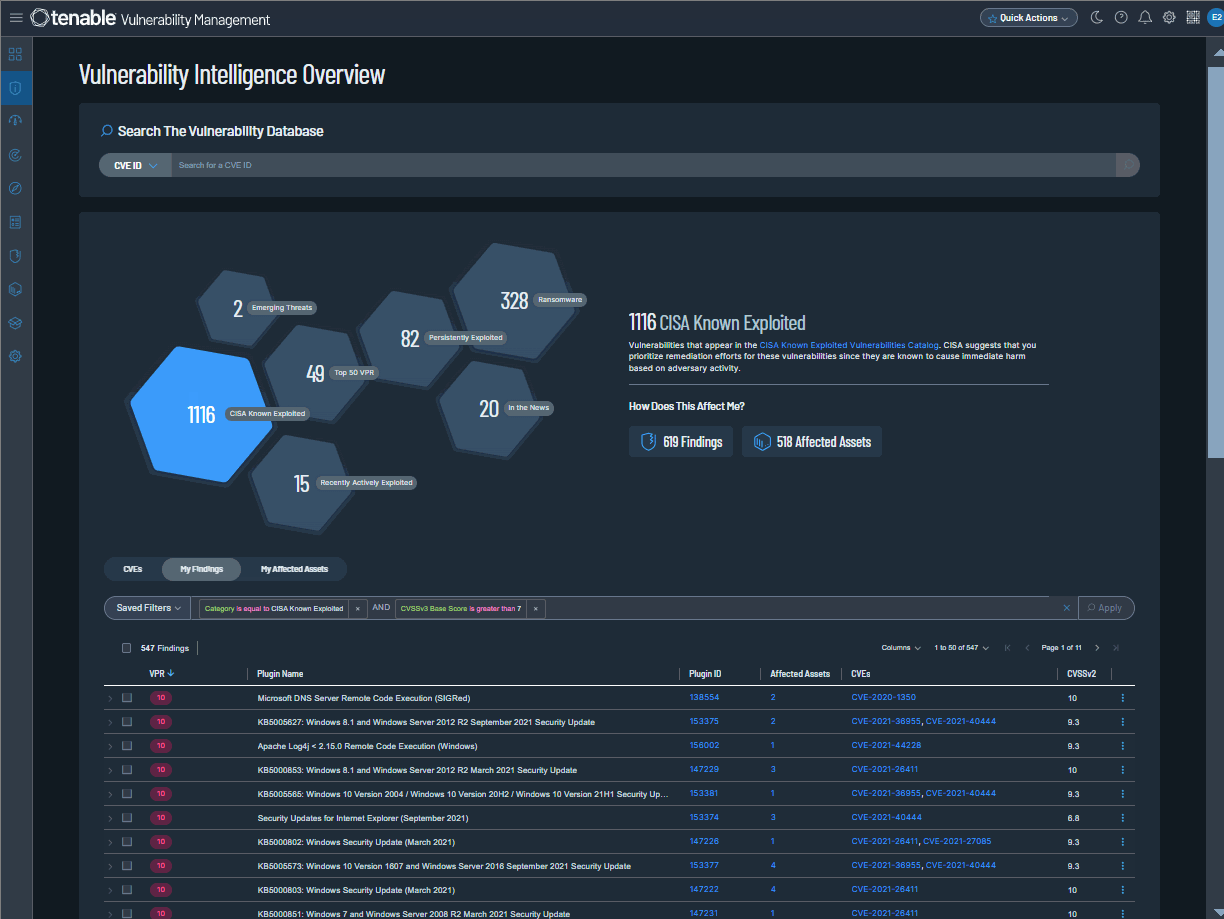
In the Vulnerability Intelligence section, you can:
-
Search Tenable’s database — Search for any vulnerability known to Tenable and view its complete details.
-
Curated categories — Review seven key vulnerability categories built on known risk indicators and Tenable research insights.
-
Custom query builder — Drill down to specific vulnerabilities, findings, or assets with a new custom query builder.
-
Export findings and assets — Export your findings or affected assets to CSV or JSON.
To learn more, see Vulnerability Intelligence in the Tenable Vulnerability Management User Guide or contact your Tenable representative.
-
In the Query Builder, the less than or equal to, exists, and does not exist filter operators may return incorrect results when used with AES and ACR.
-
In CSV exports of your findings or affected assets, the Asset ID, ACR, and AES columns do not appear.
May 22, 2024
Tenable has made the following updates to the Explore workbenches:
-
Port filter — On the Assets workbench, the Open Ports and Port filters have been combined. Use the new Port filter to search host or domain inventory assets by specific ports or port ranges. To learn more, see Asset Filters.
-
Port Last Detected Open filter — On the Assets workbench, search for all assets with detected open ports as of a date or a date range, as described in Asset Filters.
-
Enhanced Findings workbench search — On the Findings workbench, search by asset name, IPv4 address or range, or Classless Inter-Domain Routing (CIDR) block, as described in View the Findings Workbench.
May 13, 2024
You can now configure scanners to identify the existence of a Tenable Agent on a target host via the Open Agent Port setting in Tenable Vulnerability Management. This ensures that the host is recorded as a single asset in Tenable Vulnerability Management, regardless of whether they are the target of a scanner's network scan or are generating agent scans.
For more information about automatic asset merging and the Open Agent Port setting, see Configure Agent Profiles to Avoid Asset Duplication in Tenable Vulnerability Management in the Tenable Agent User Guide.
For information on how to configure the Open Agent Port for an agent profile, see Agent Profiles in the Tenable Vulnerability Management User Guide.
April 23, 2024
The following is not supported in Tenable FedRAMP Moderate environments. For more information, see the Tenable FedRAMP Product Offering.
Tenable is pleased to announce key features and content that enhance how you work with compliance findings in Tenable Vulnerability Management. This release includes hundreds of new compliance-focused report templates, dashboards, and widgets as well as new findings filters.
-
Report template categories — In a previous release, Tenable introduced report template categories. On the Reports page, new categories now contain new templates. Review the categories in Create a Report.
-
Dashboard templates — On the Dashboards page, click New Dashboard > Template Library to choose from new dashboards in categories under Host Audits. Review the categories in Create a Dashboard.
-
Dashboard widgets — On the Dashboards page, click Widget Library to add new widgets from categories under Host Audits.
-
Custom widgets — When adding a custom widget, you can now include host audit data, as described in Create a Custom Widget.
-
Findings filters — On the Findings workbench in the Host Audits tab, new benchmarking and compliance filters now appear, as described in Findings Filters.
April 3, 2024
Tenable has added the new Info-level Reporting scan setting to Nessus Agent vulnerability scan templates. Configuring this setting can help minimize your scan processing times by decreasing the number of unchanged Info-severity findings that Tenable Vulnerability Management processes after every agent scan.
For more information, see Info-level Reporting and Basic Settings in the Tenable Vulnerability Management User Guide.
April 2, 2024
Tenable has updated the Findings workbench and Findings Details page with two new fields that enable you to run more accurate findings reports and measure SLA compliance for scanned vulnerabilities.
The new fields are:
-
Time Taken to Fix — How long it took to fix a vulnerability found on a scan, in hours or days. Only applicable to Fixed vulnerabilities. Now appears as a Findings Details field, a Findings workbench filter, and a Findings workbench column.
-
Last Fixed — The last time a previously detected vulnerability was scanned and noted as no longer present on an asset. Now appears as a Findings workbench column and a Findings Details field. Tenable added the filter in a previous release.
To learn more, see Vulnerability Details and Findings Filters.
March 20, 2024
Tenable has updated Findings workbench reports and templates in the Act > Reports section as follows:
-
Password protection for Findings reports — When you generate a report on the Findings workbench, add a password that uses AES 128-bit encryption. To learn more, see Generate a Findings Report.
-
Report categories in the Reports section — When you create a report in the Act > Reports section, choose a template from new categories that better organize Tenable Vulnerability Management's many templates. Tenable will add new categories in the coming days. To learn more, see Create a Report.
March 14, 2024
In Tenable Vulnerability Management's Remediation section, use a new Asset Tags filter and Asset Tags column to identify which tags are associated with your remediation projects and goals.
For more information, see Remediation.
March 6, 2024
On the License Information page, the Cloud Security section now shows your licensed Tenable cloud assets instead of your billable cloud resources so you can easily see how much of your license you are using.
Tip: In the new version of Tenable Cloud Security, your licensed asset count may be calculated by multiplying your Compute, Serverless, and Container Repository assets against a ratio and then adding your Container Images (if you use Tenable Container Security). If a ratio is applied, it now appears in the Cloud Security section, in the new License Ratio field. To learn more, contact your Tenable representative.
Tenable has made the following updates to the License Information page:
-
Cloud Security section — A new tooltip explains how your licensed cloud assets are calculated. Your ratio, if any, appears in the new License Ratio field. If you have no ratio, 1 appears.
-
Compute — Now shows your licensed cloud computing assets. Hover on the number to view your billable resources (the number of resources before any ratio is applied).
-
Serverless — Now shows your licensed serverless assets. Hover on the number to view your billable resources.
-
Container Repositories — Now shows your licensed container repositories. Hover on the number to view your billable resources.
-
Container Images (Legacy Container Security) — This field’s new name clarifies that Tenable Container Security is a legacy application.
To learn more, see License Information.
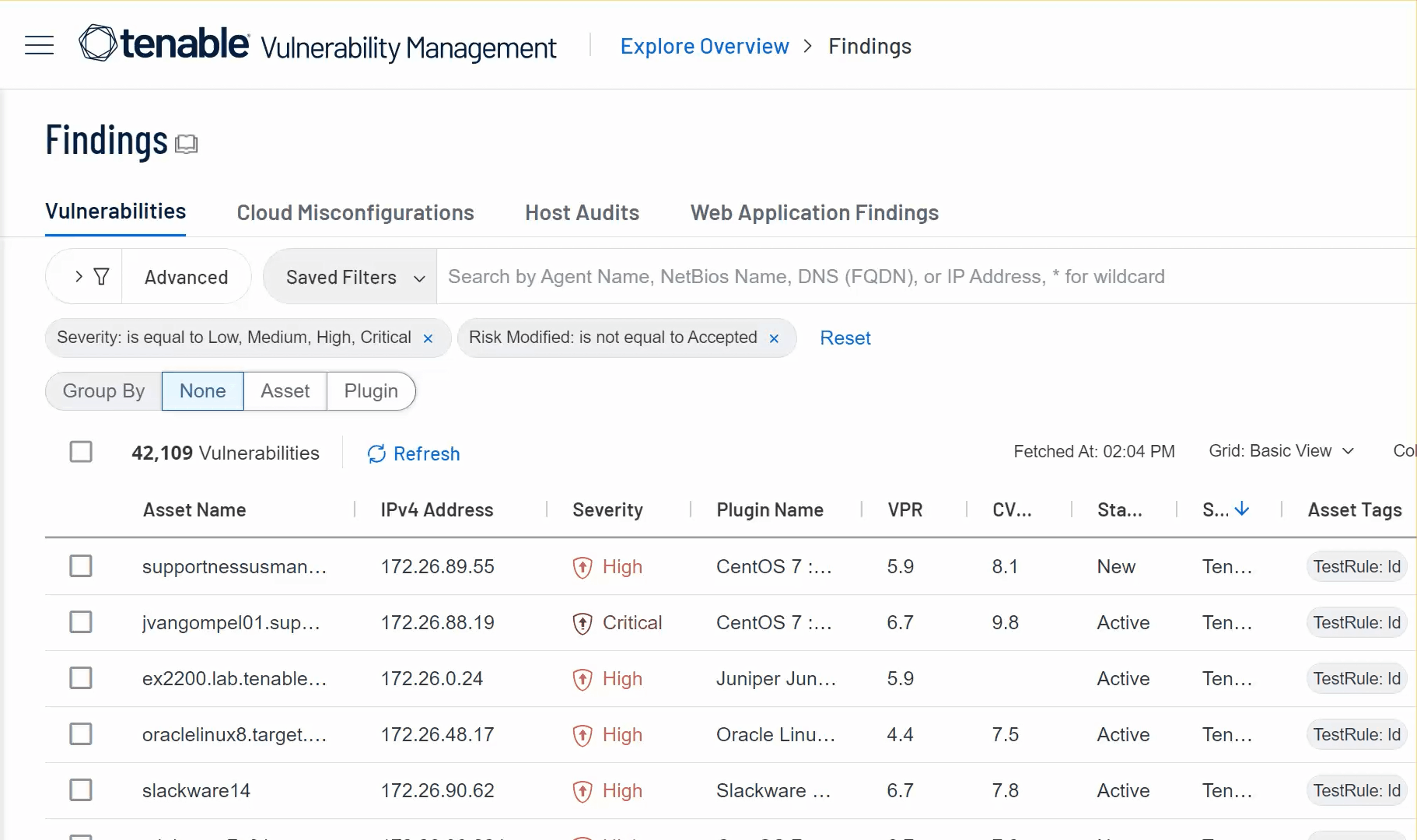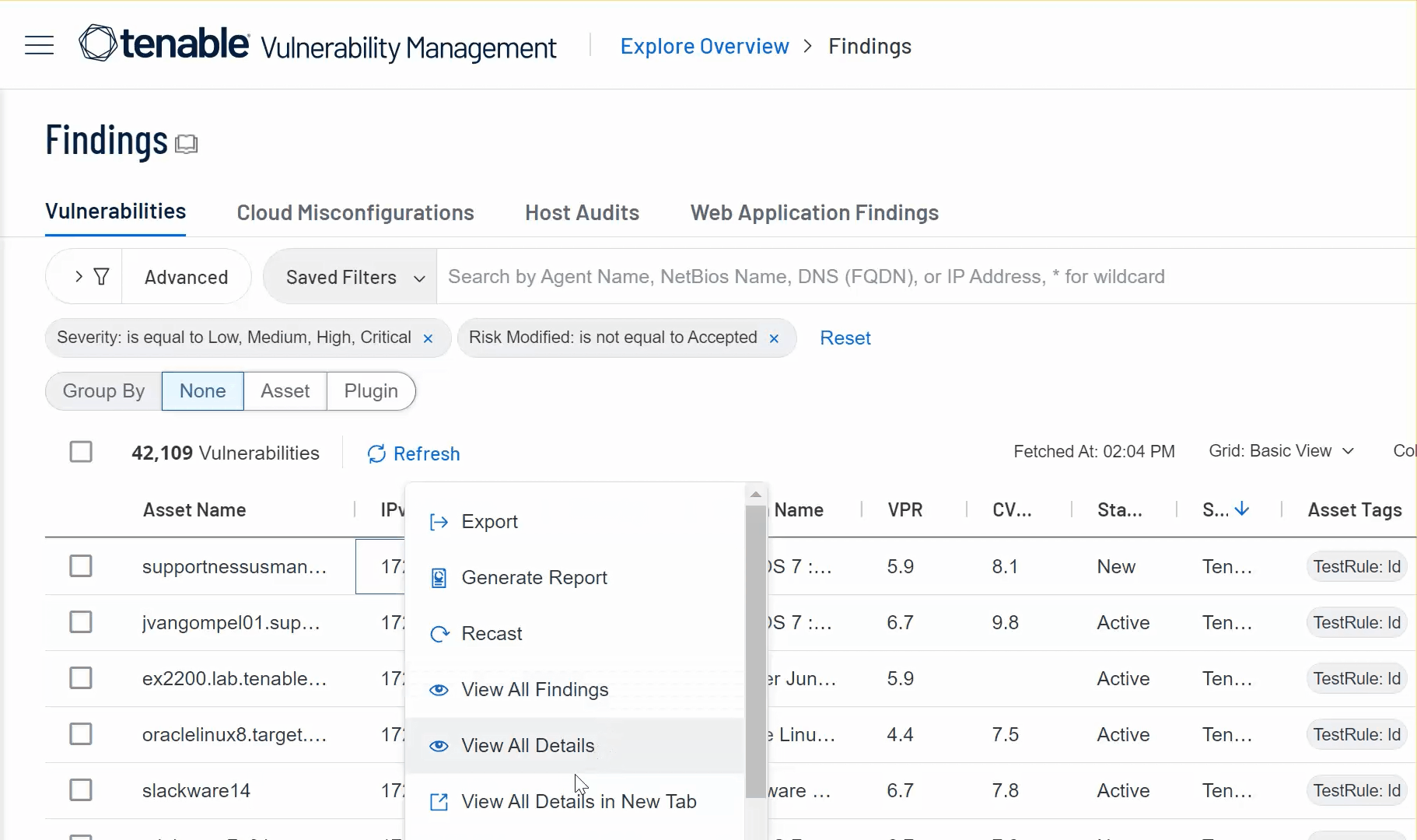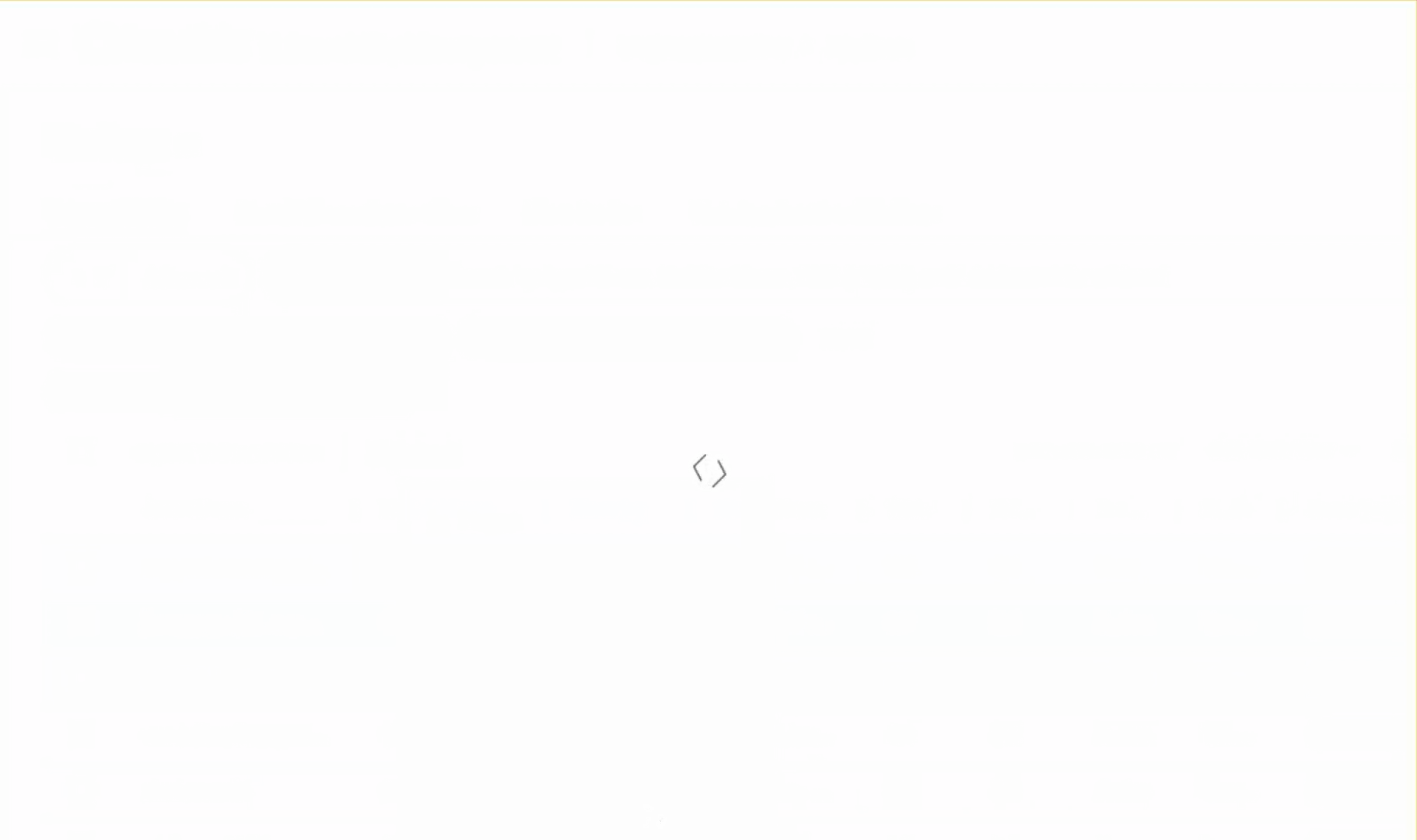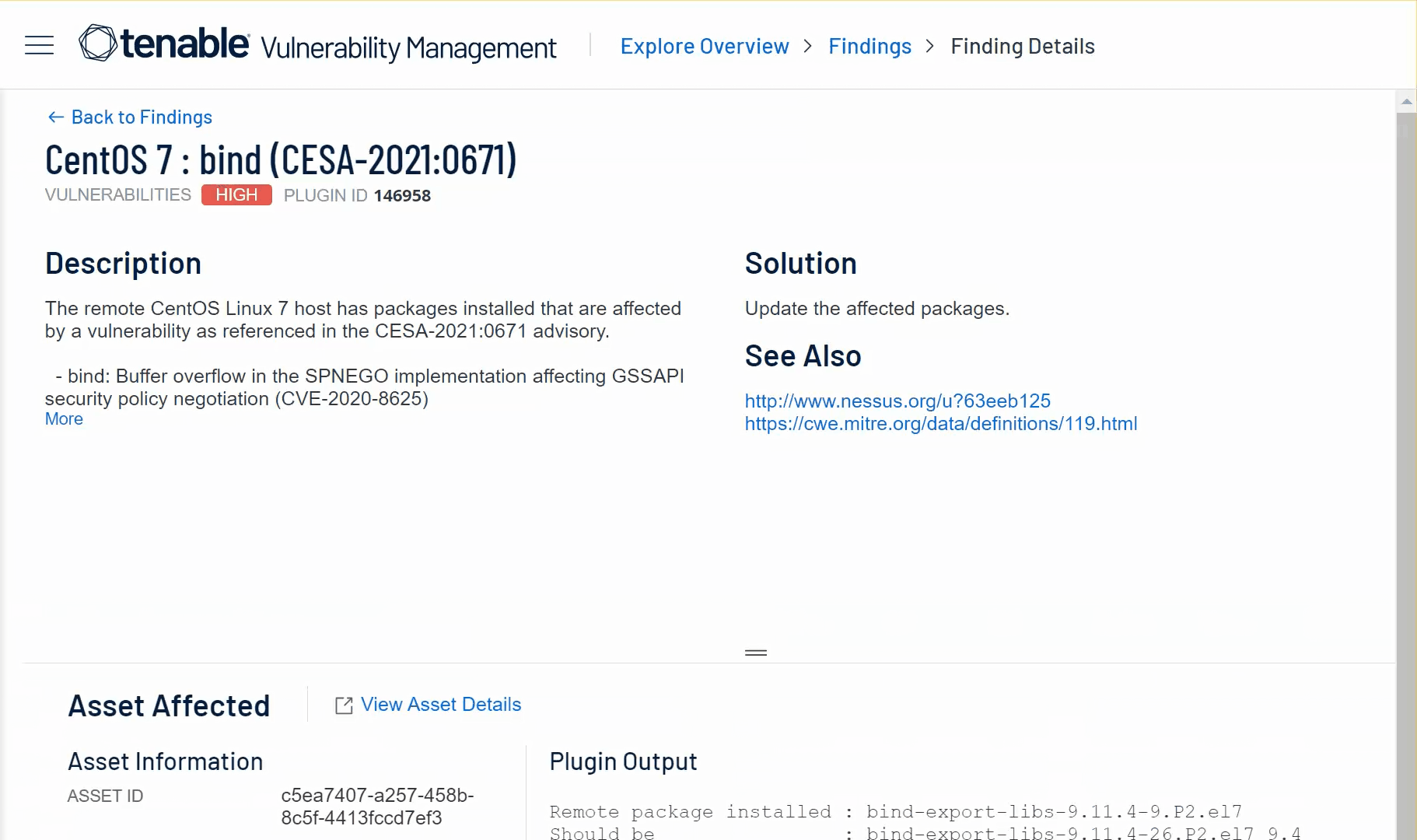
The Findings and Assets workbenches now support multiple browser tabs.
The following enhancements support this change:
-
Findings workbench tabs — Right-click a tab (for example, Cloud Misconfigurations) to open it in a new browser tab, active filters included.
-
Details panes — On the findings or assets details panes, in the upper right corner, right-click See All Details to open the corresponding details page in a new browser tab.
-
Workbench context menus — On the Findings or Assets workbenches, right-click a row and then click View All Details or View all Details in New Tab to open the corresponding details page in the current tab or a new one.
-
Grouped findings — On the Findings workbench, right-click a finding grouped by Plugin and then click View Plugin Details or View Plugin Details in New Tab to review the plugin on Tenable's website.
-
Workbench action menus — On the Findings or Assets workbenches, in the (
 ) menu, click View All Details or View all Details in New Tab to open the corresponding details page in the current tab or a new one.
) menu, click View All Details or View all Details in New Tab to open the corresponding details page in the current tab or a new one.
To learn more, see Use the Context Menu in the Explore section of the Tenable Vulnerability Management User Guide.
February 28, 2024
|
Bug Fix |
Defect ID |
|---|---|
|
Fixed an issue in the Scans section where web application scans failed with an Insufficient scope error. |
01769832, 01769765, 01768766, 01768764, 01769400, 01770252, 01769478, 01769538, 01770915, 01769177, 01771942, 01772182, 01772321 |
|
Fixed an issue where some assets were automatically added to tag exclusion lists. |
01728823, 01739470, 01735561, 01731375, 01756024 |
|
Fixed an issue on the Findings workbench where searches with the CVE filter did not return new results. |
01779775, 01780299, 01778390, 01782808, 01784618 |
| Fixed an issue where scans using plugin 84239 did not generate output | 01518718, 01757216 |
February 12, 2024
This update enables custom role users to access Tenable Vulnerability Management Scan Management. It also enables administrators to leverage custom roles to manage access to Tenable Vulnerability Management Scan Management tasks, such as viewing and managing scans, exclusions, scan templates, managed credentials, and target groups.
January 30, 2024
|
Bug Fix |
Defect ID |
|---|---|
|
Fixed an issue on the Assets workbench where using the CISA KEV Due Date filter caused an error to appear. |
01761164, 01761011, 01761653, 01760891 |
|
Fixed an issue on both the Findings and Assets workbenches where exporting findings or assets intermittently failed with an error. |
01730886, 01739220, 01730892 |
|
Fixed an issue on the Findings workbench where two users saw different findings when using the same filters. |
01763398, 01762034, 01763507 |
| Fixed an issue on the Findings workbench where the Host Audits tab failed to load. | 01730539 |
January 23, 2024
Tenable is pleased to announce the redesigned License Information page, which streamlines how you view cloud license details on the Tenable platform.
On the License Information page, you can:
-
In Tenable One only, use visual overviews by product or time period to spot trends.
-
View license information for all Tenable products in your cloud container.
-
View license usage snapshots, such as total assets or available assets.
-
View license resource counts for all your cloud products.
The License Information page is available to all users. To learn more, see License Information.
January 18, 2024
Tenable's redesigned License Information page now supports the new version of Tenable Cloud Security.
If your organization has upgraded to this version, the following new fields appear under Cloud Security:
-
Compute — Non function-like cloud resources, such as virtual machines or cloud storage.
-
Serverless — Function-like cloud resources such as AWS Lambda or Azure Functions.
In these fields, view your organization's scanned cloud resources. To learn more, see License Information.
January 16, 2024
The Tenable Vulnerability Management header has been restyled to better align with Tenable’s latest branding and visual design guidelines. It also makes it much easier for users to access their personal profile and product and platform settings from any page in Tenable Vulnerability Management.
For more information, see Navigate Tenable Vulnerability Management.
January 12, 2024
Tenable Vulnerability Management now supports a single-line command installation and linking method for Tenable Nessus scanners and Tenable Agents. You can specify the sensor name and group assignment within the single-line command.
For more information, see Link a Sensor in the Tenable Vulnerability Management User Guide.
January 4, 2024
Tenable Vulnerability Management changed how it processes fully qualified domain names (FQDNs) for assets. All FQDNs will be normalized to lowercase and then the duplicates will be merged.
For example, where asset1 would previously have three FQDNs: ["VeryImportantAsset.local", "veryimportantasset.local", "externalimportantasset.local"], after the change asset1 will have two FQDNs: ["veryimportantasset.local", "externalimportantasset.local"].
This change streamlines the Host Assets view in the Assets Workbench in the user interface, prevents assets from registering as duplicates, and enables users to better focus on the assets that need their attention.